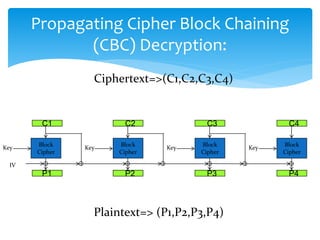
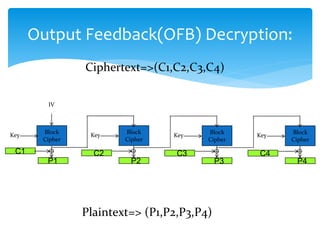
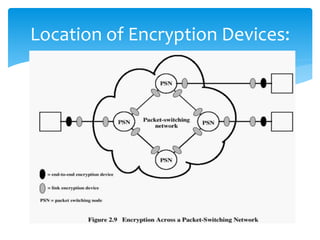
The document discusses various cryptographic techniques including symmetric and asymmetric encryption, stream and block ciphers, and algorithms like Caesar cipher, ROT13, Four Square cipher, Running Key cipher, Vigenere cipher, Playfair cipher, Hill cipher, and One Time Pad. It provides code examples and explanations of how the encryption and decryption processes work for different algorithms. Key concepts covered include plain text, cipher text, encryption/decryption keys, and using mathematical operations like modulo for cipher substitution.











![#include <stdio.h>
int main()
{
char array[100], cipher[100];
int c=0, x=0, y=0;
int z;
printf("This Program will encrypt according to your needsn");
printf("Enter the cipher keyn");
scanf("%d",&z);
printf("Enter the sentence");
while((c=getchar()) != 'n')
{
array[x++]=(char)c;
cipher[y++]=(char)(c+z); //for decription need to do (c-z)
}
array[x]=0;
cipher[y]=0;
printf("%sn",cipher);
return 0;
}](https://image.slidesharecdn.com/cybersecuritypart-2-220815061843-b5b9d03d/85/Cyber-Security-Part-2-pptx-12-320.jpg)