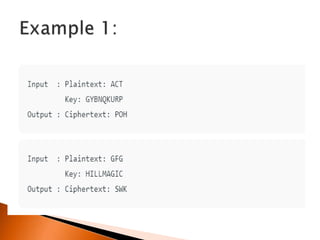
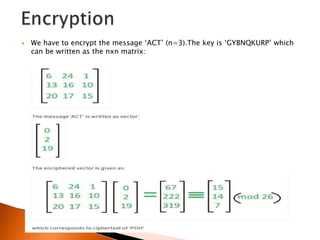
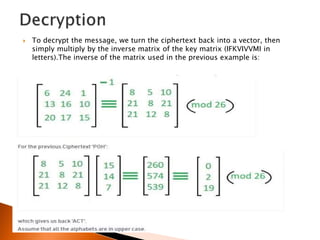
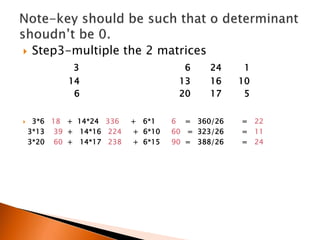
The document discusses polygraphic substitution ciphers and the Hill cipher. The Hill cipher is a polygraphic cipher that represents letters as numbers and encrypts blocks of text by multiplying them by a random key matrix. To decrypt, the cipher text is multiplied by the inverse of the key matrix. An example is given showing how a 3x3 key matrix is used to encrypt the plaintext "ACT" into ciphertext and then decrypt it back by multiplying the ciphertext by the inverse key matrix. The steps of encrypting a message using a Hill cipher are outlined.