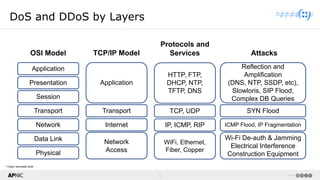
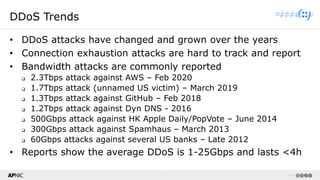
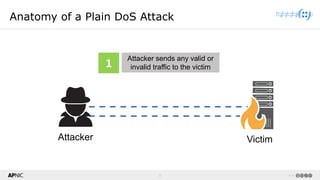
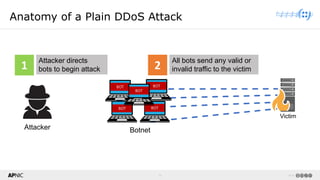
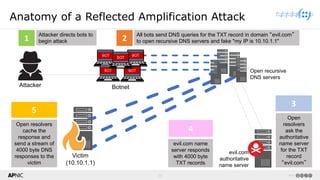
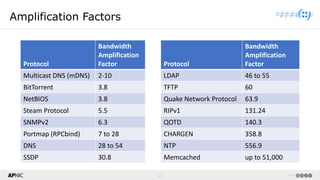
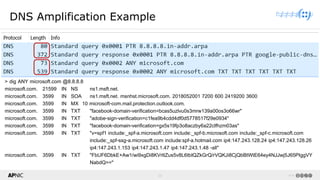
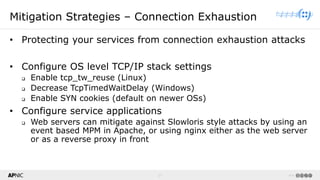
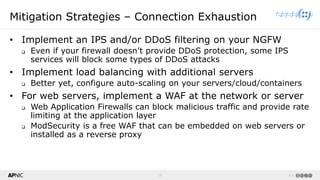
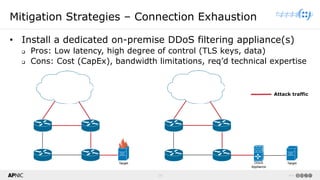
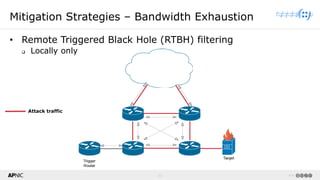
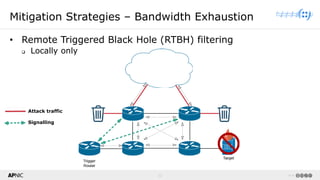
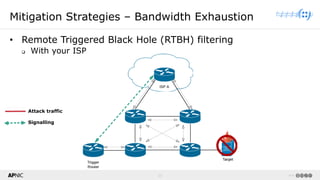
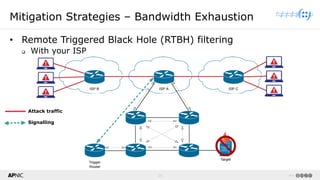
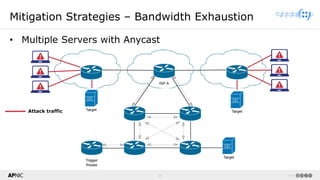
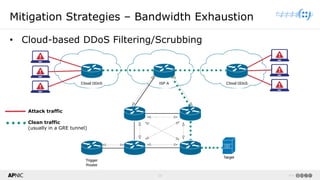
The document provides a comprehensive overview of Distributed Denial of Service (DDoS) attacks, detailing their types, impacts, and mitigation strategies. It discusses the technical anatomy of DDoS and traditional Denial of Service (DoS) attacks, including reflection and amplification tactics, as well as trends in attack traffic. Additionally, it outlines various mitigation strategies tailored to address both connection exhaustion and bandwidth exhaustion threats to services and networks.