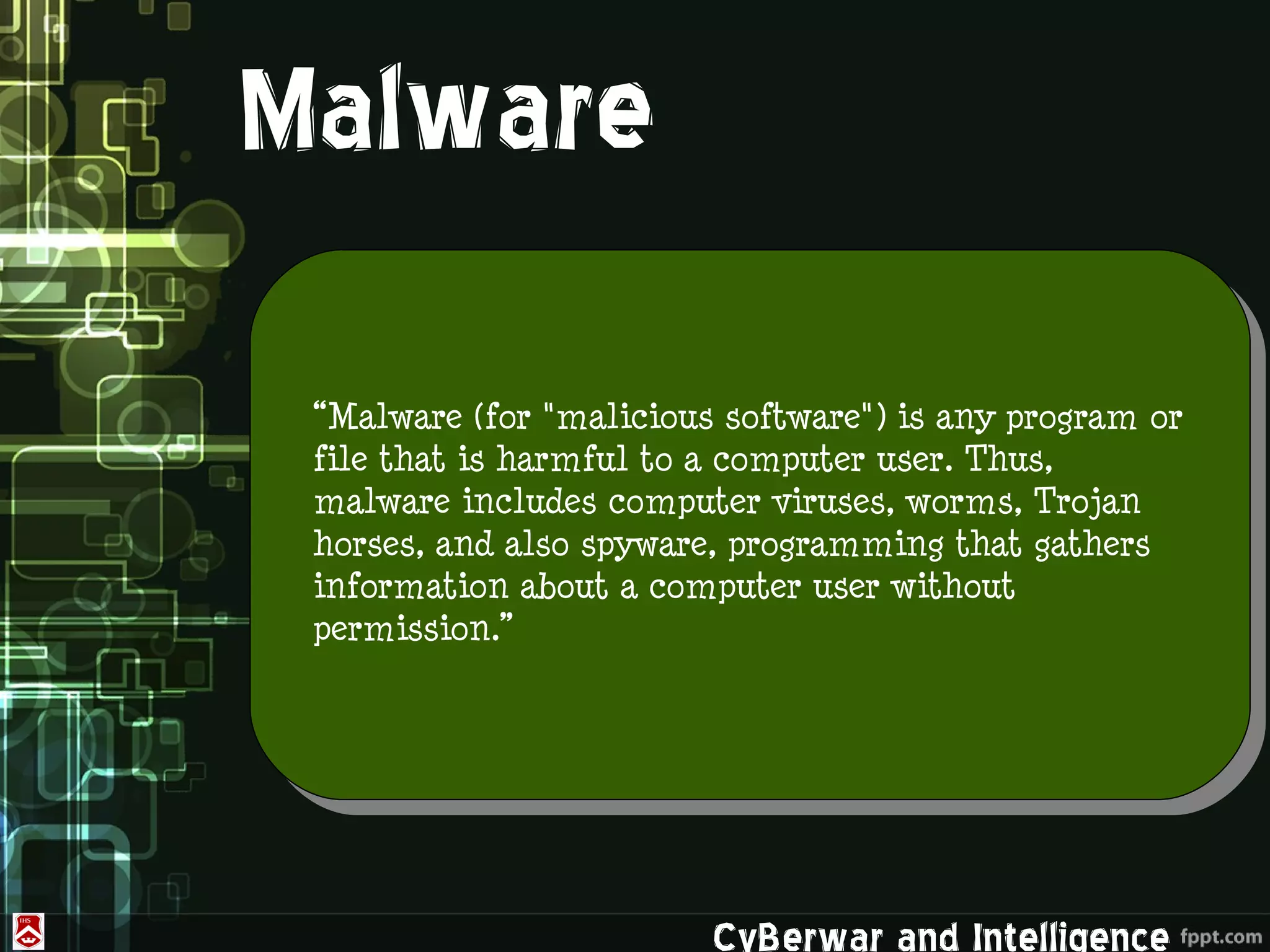
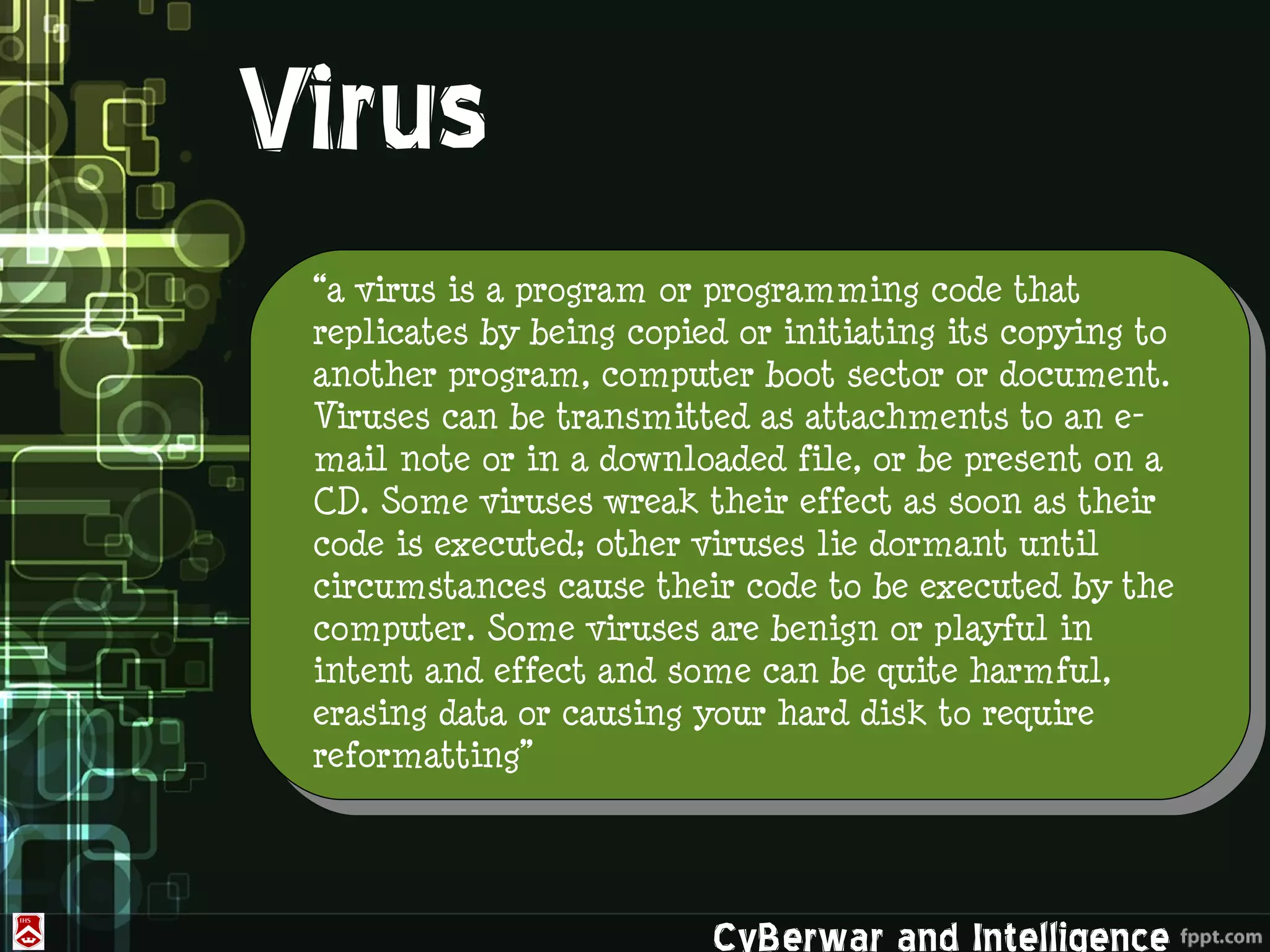
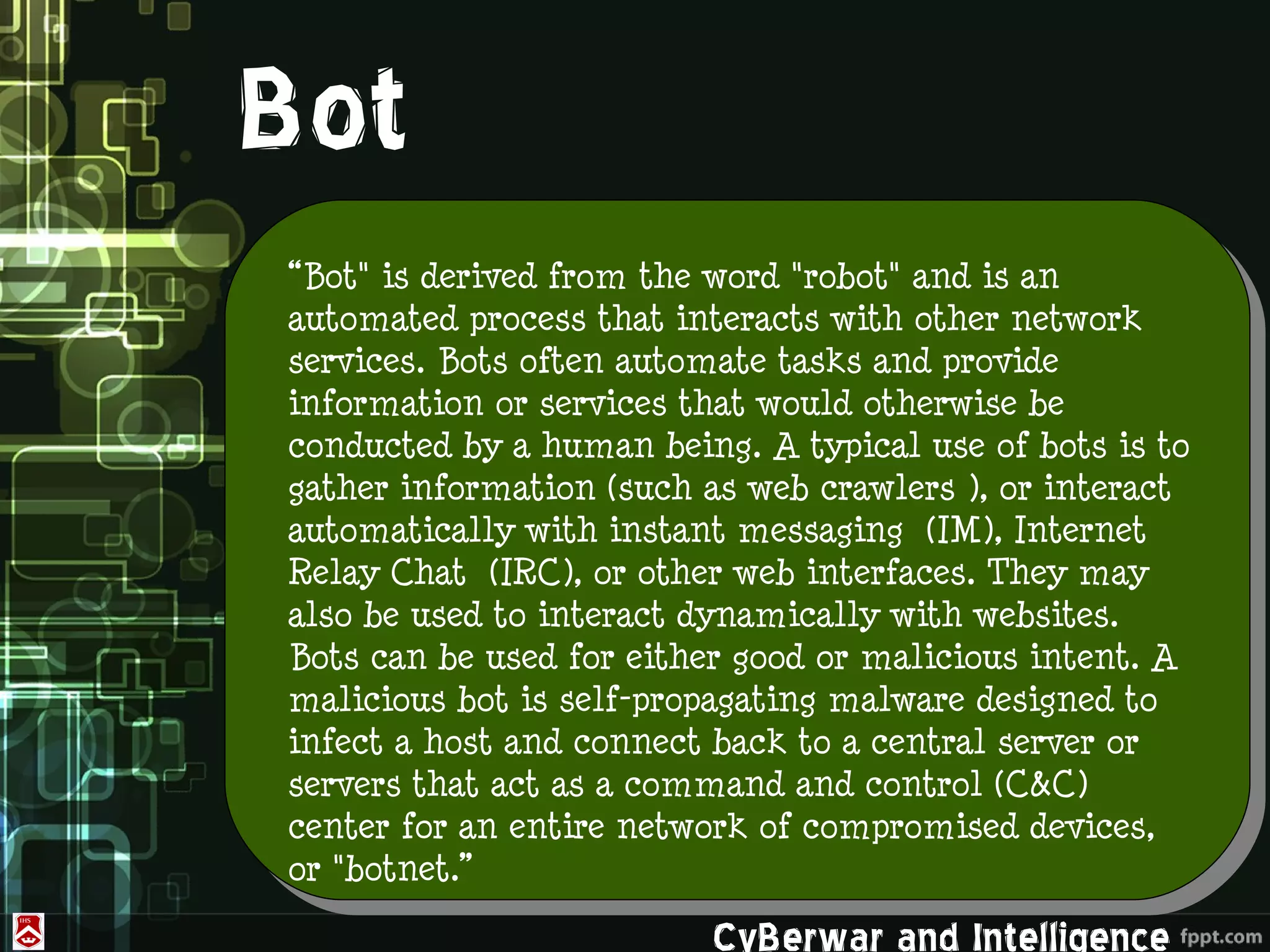
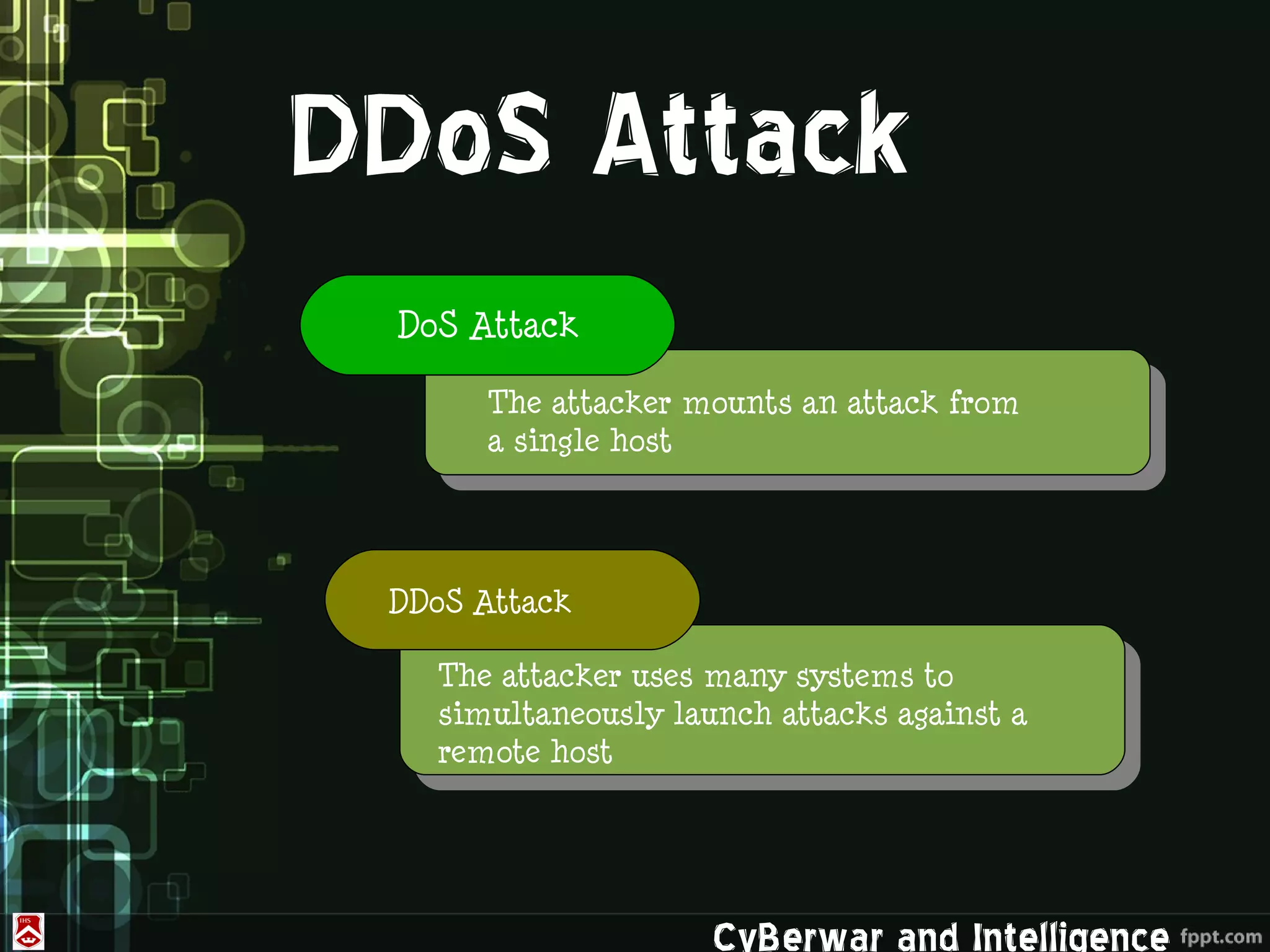
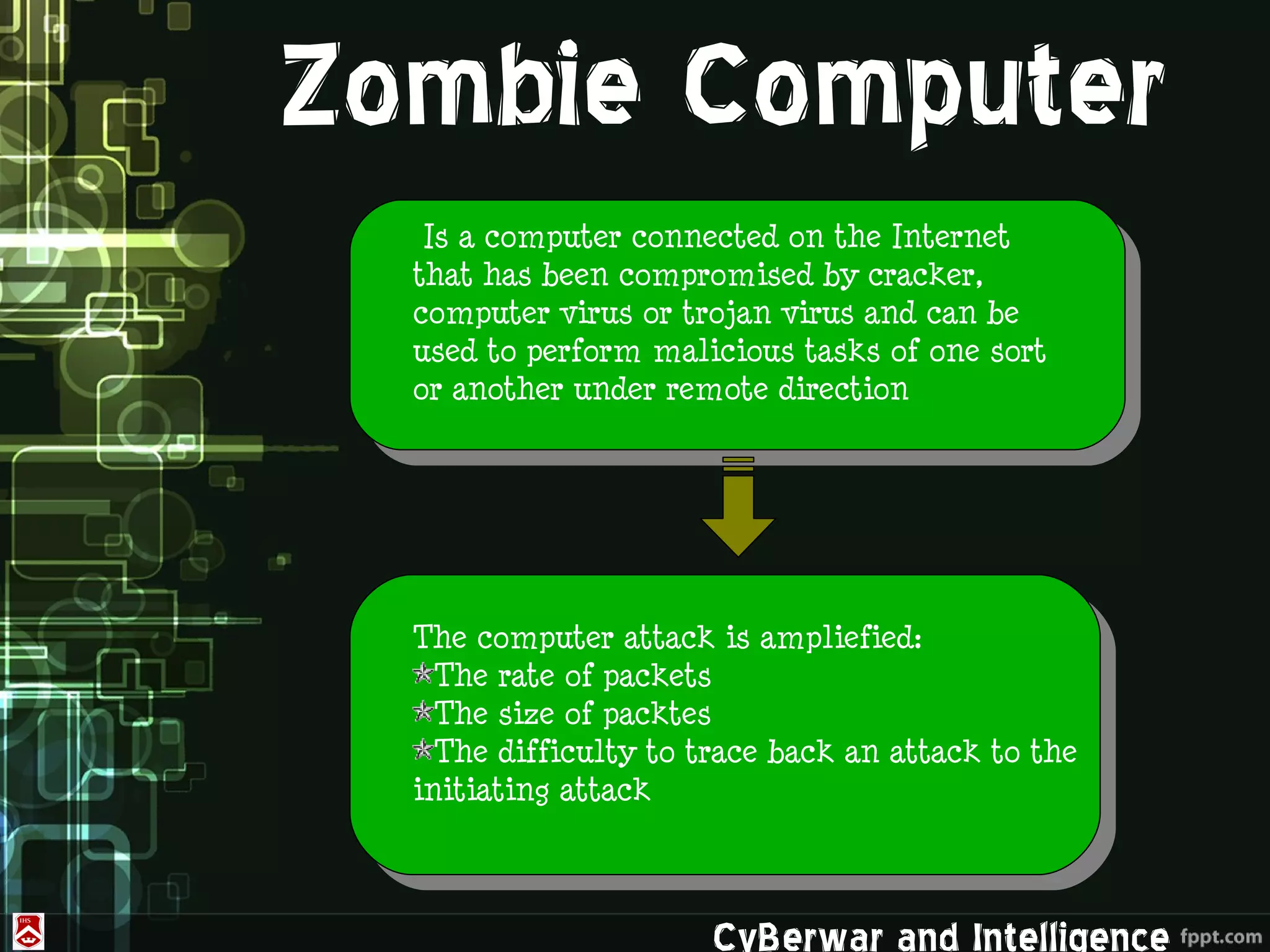
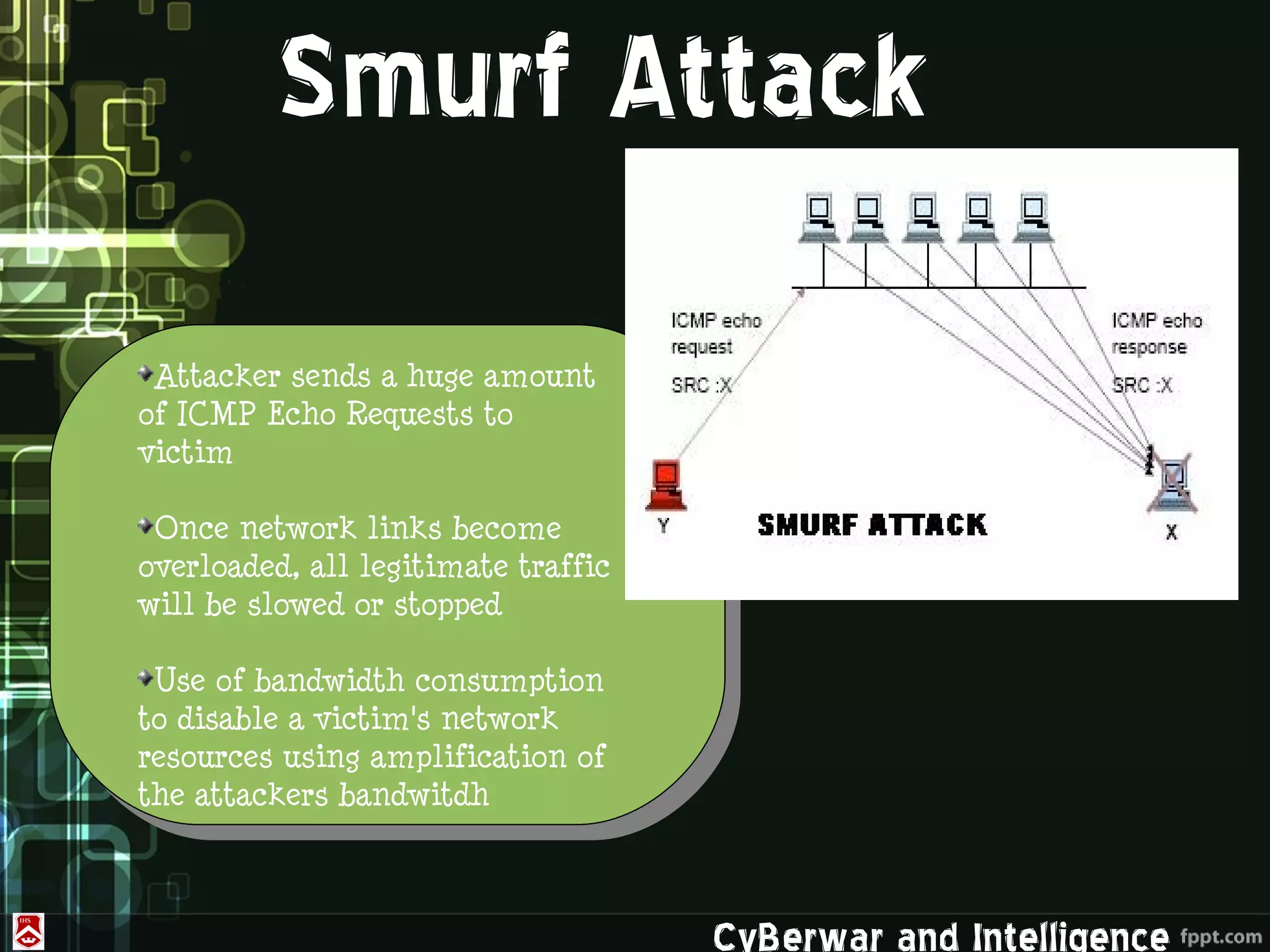
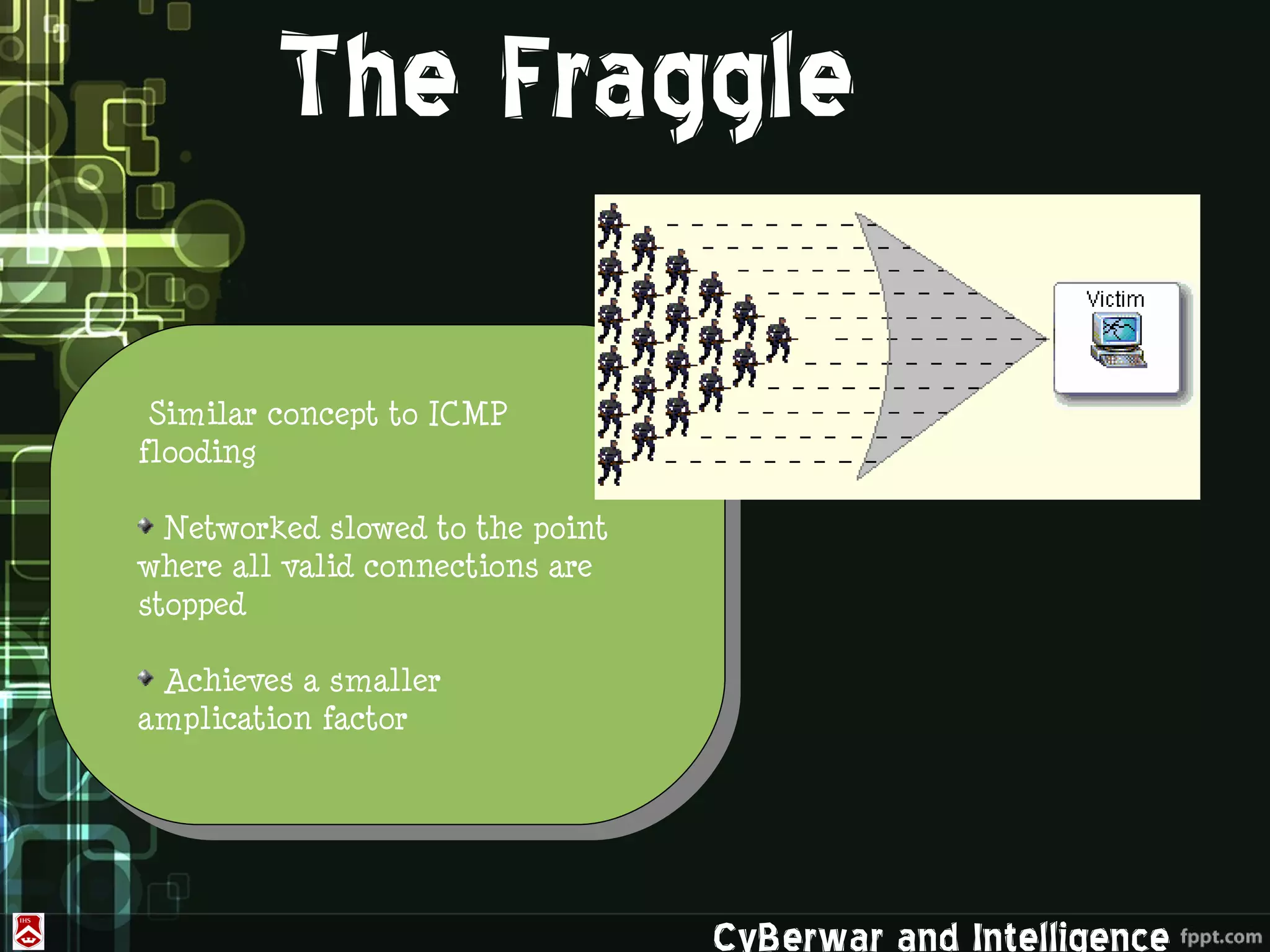
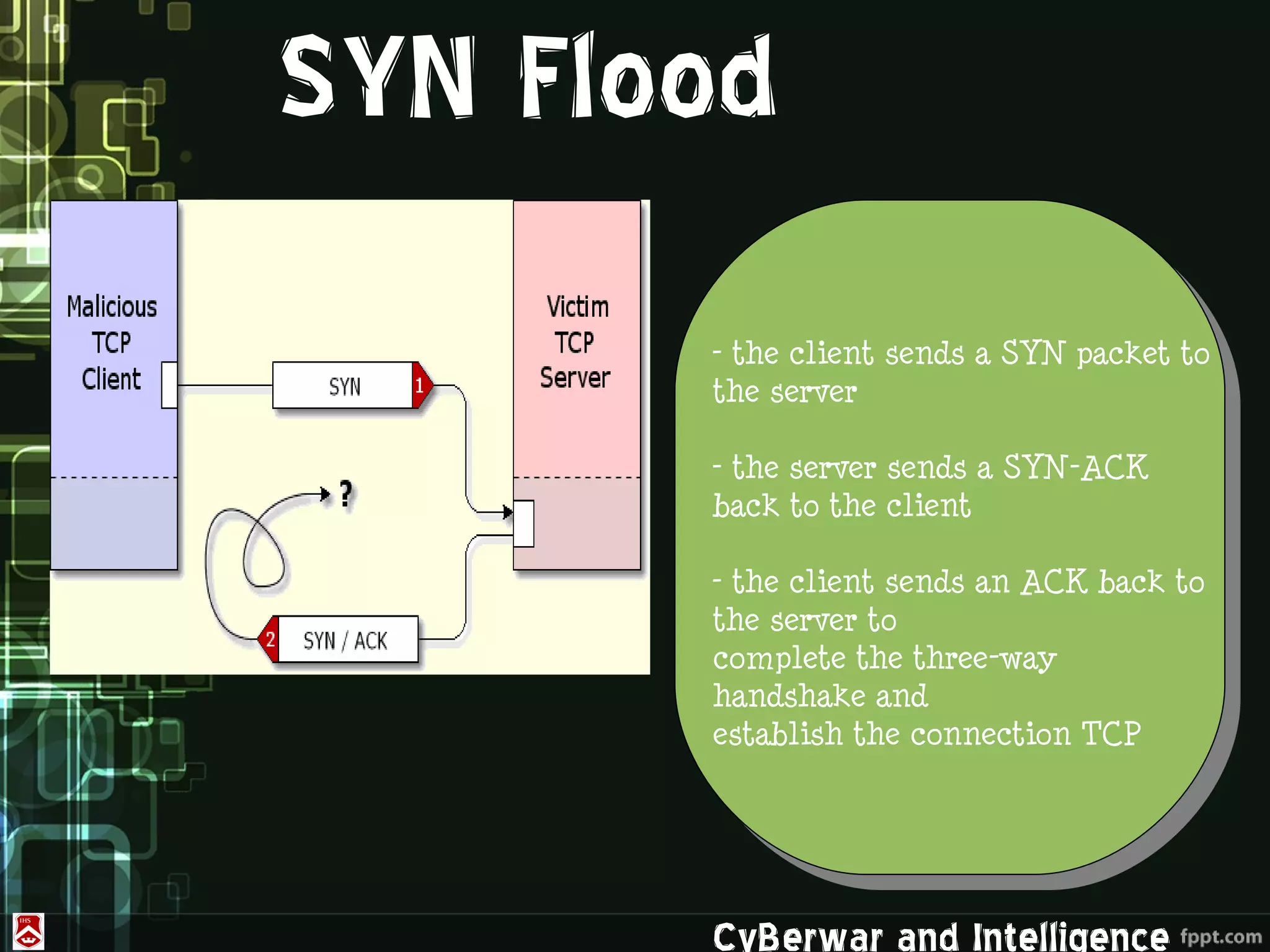
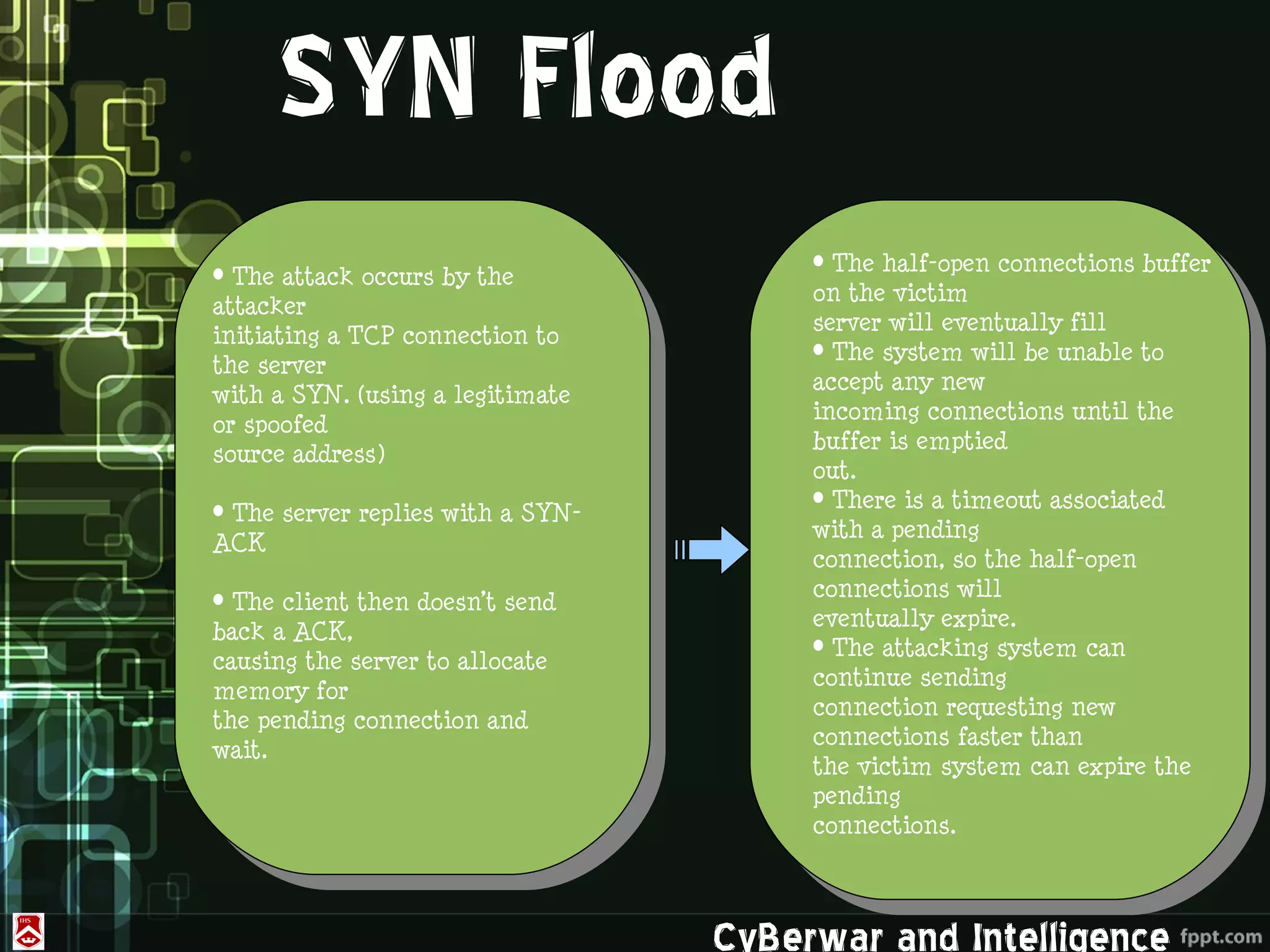
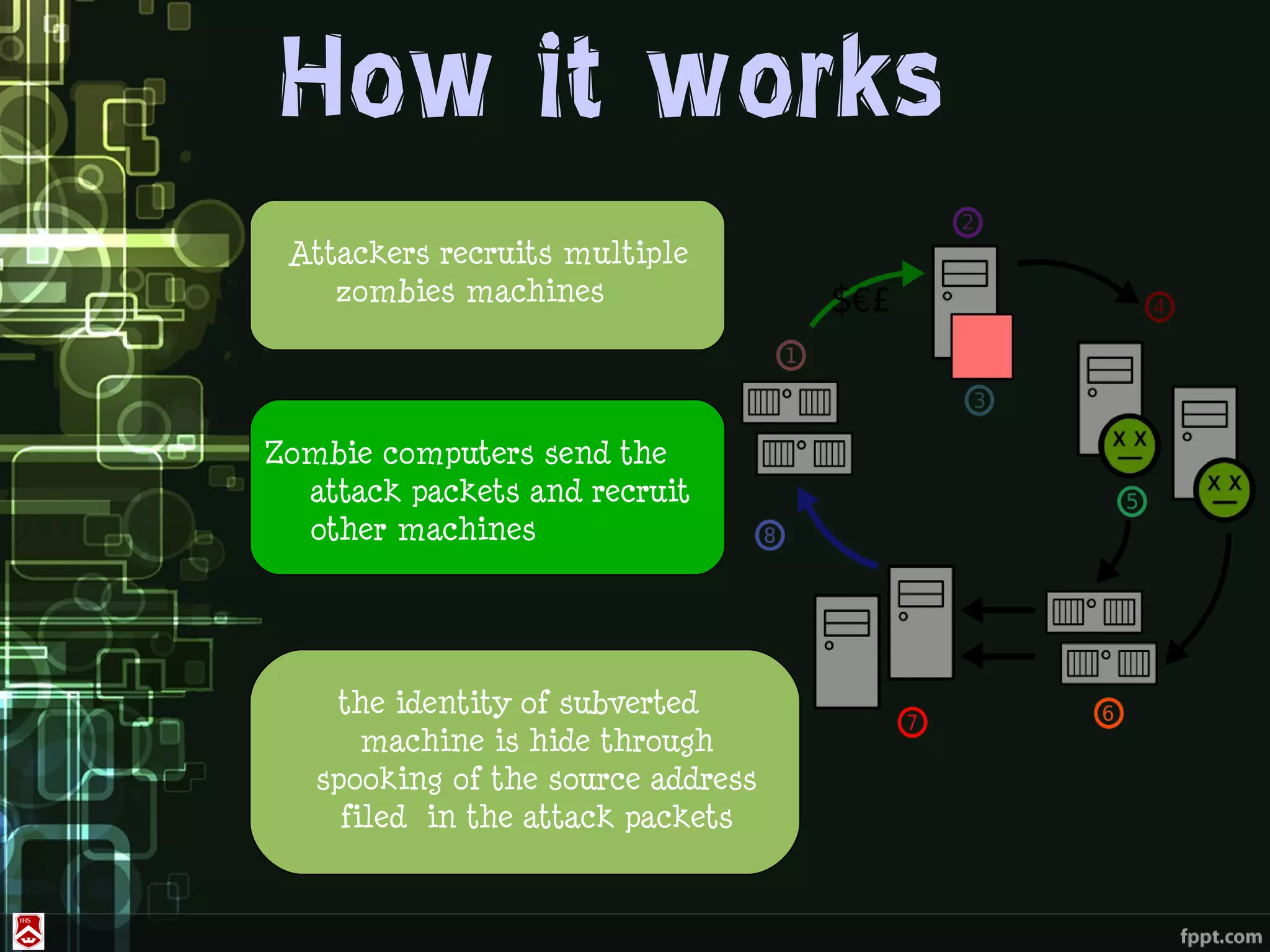
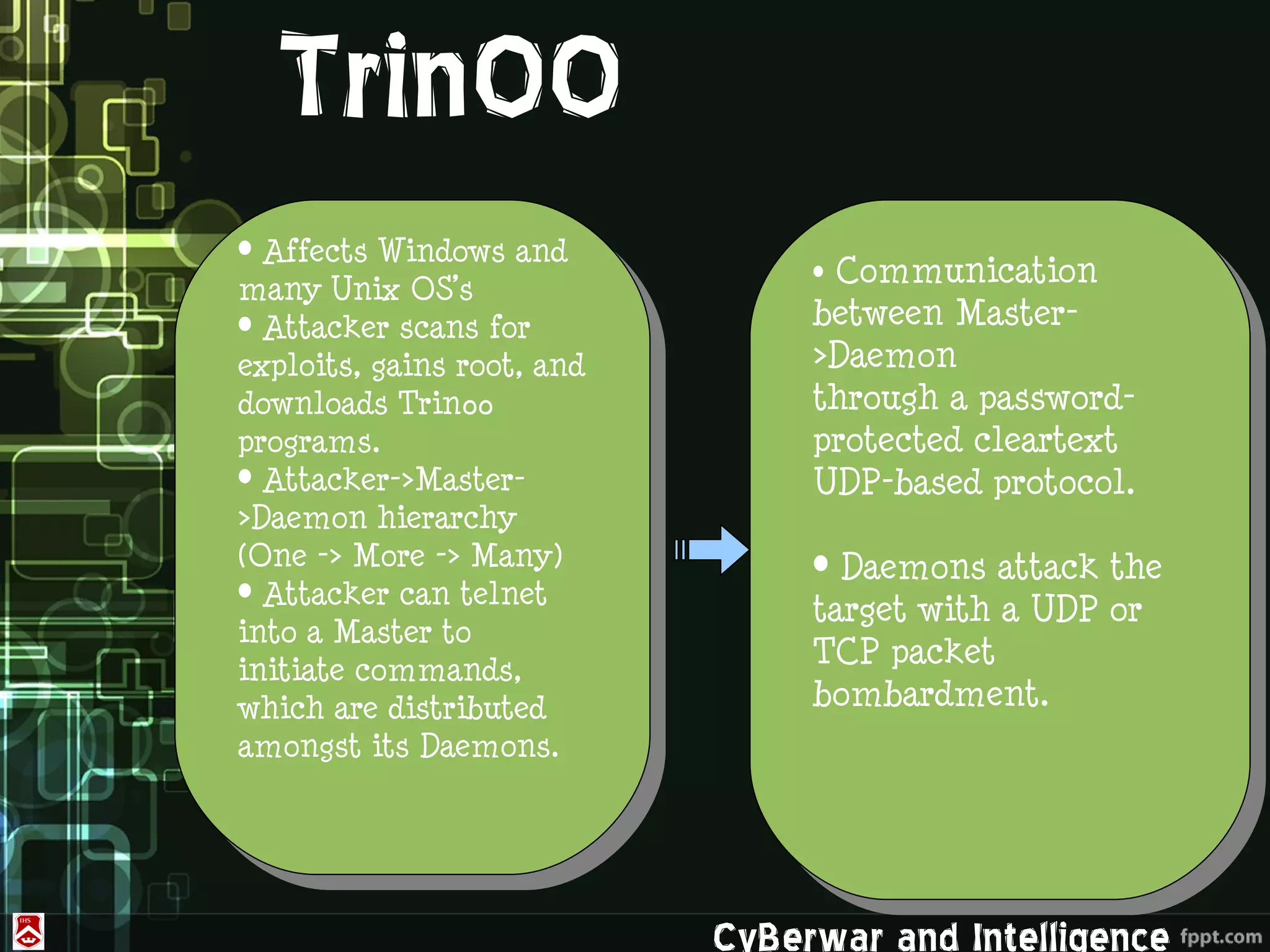
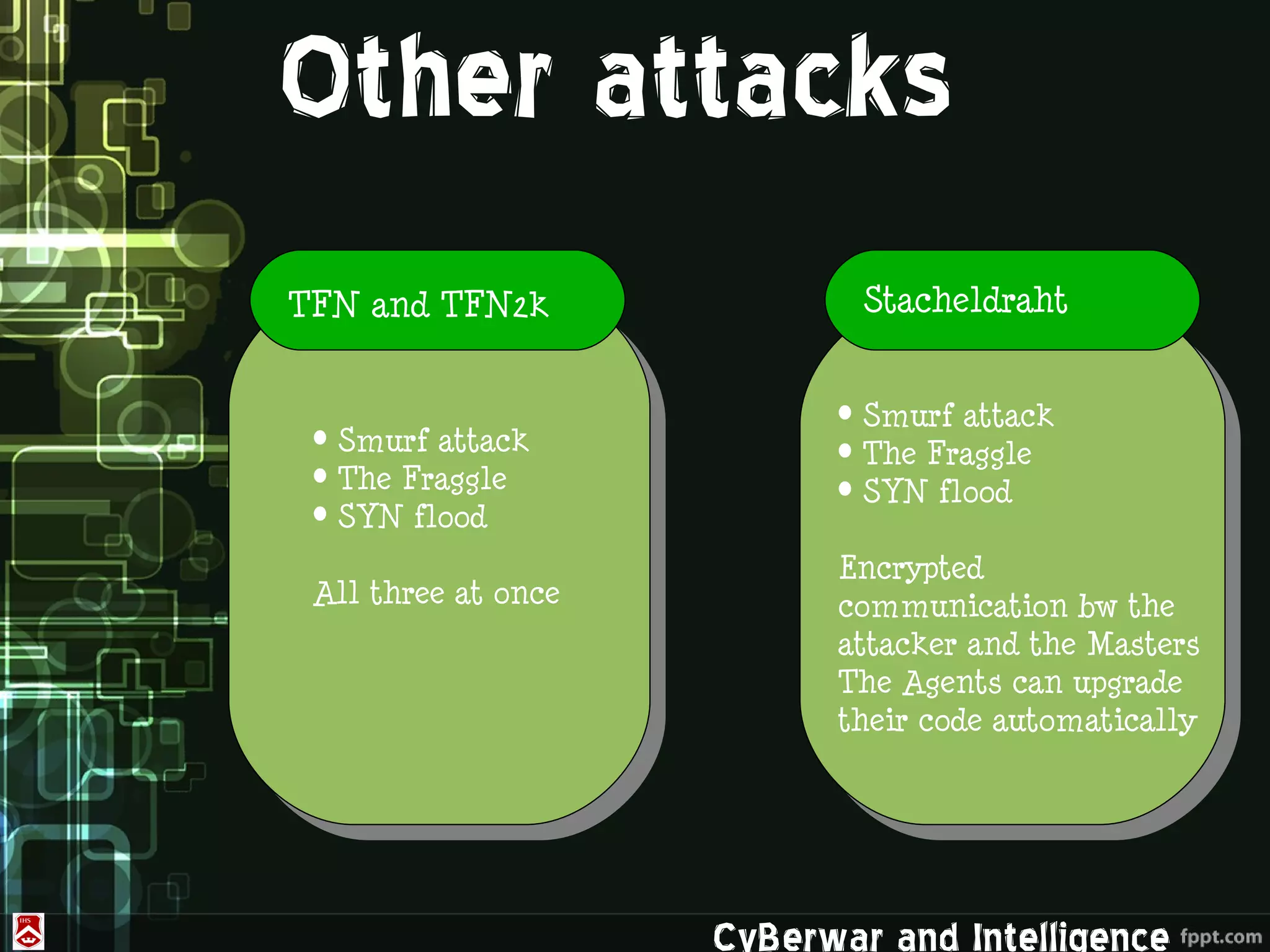
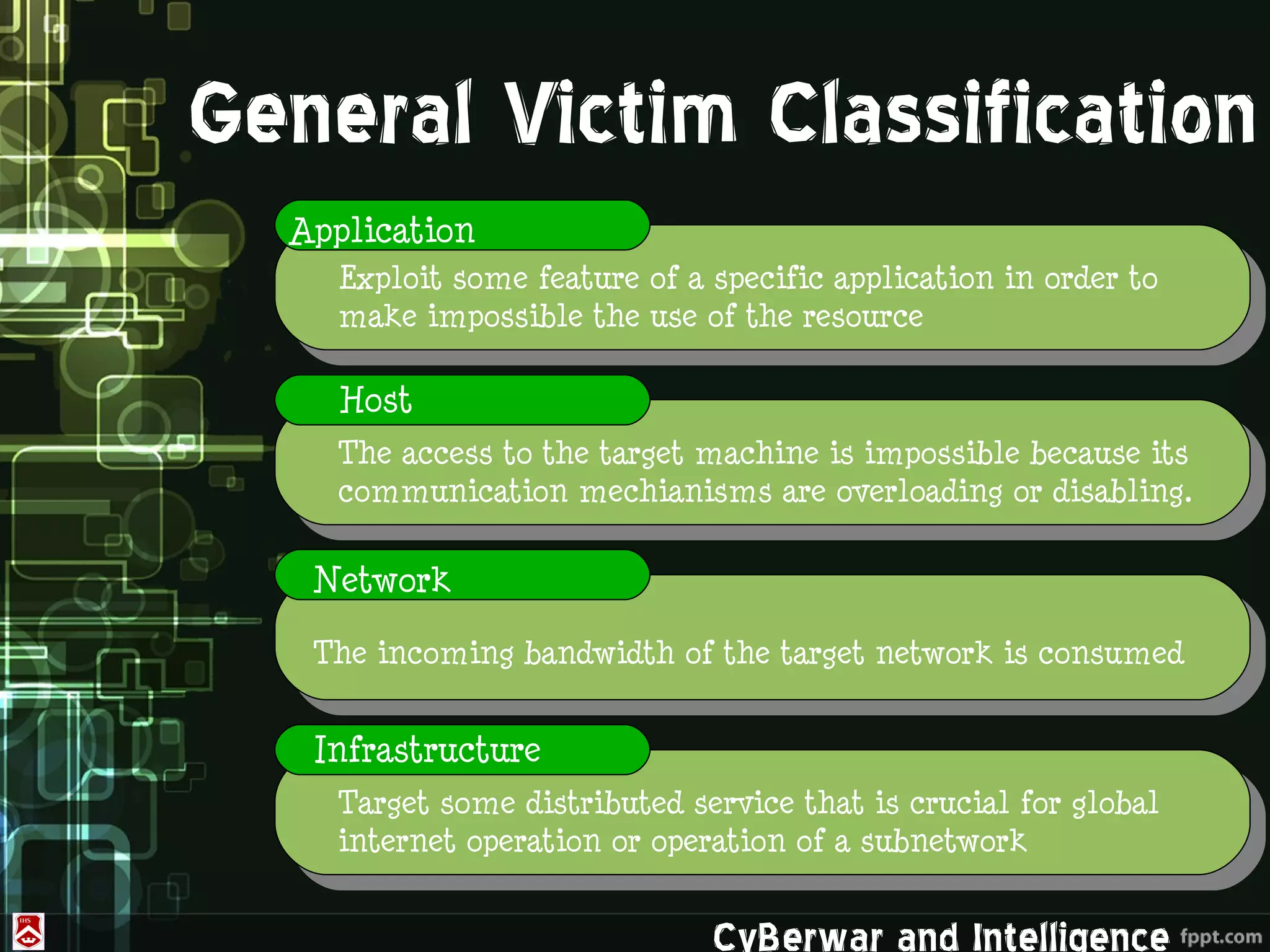
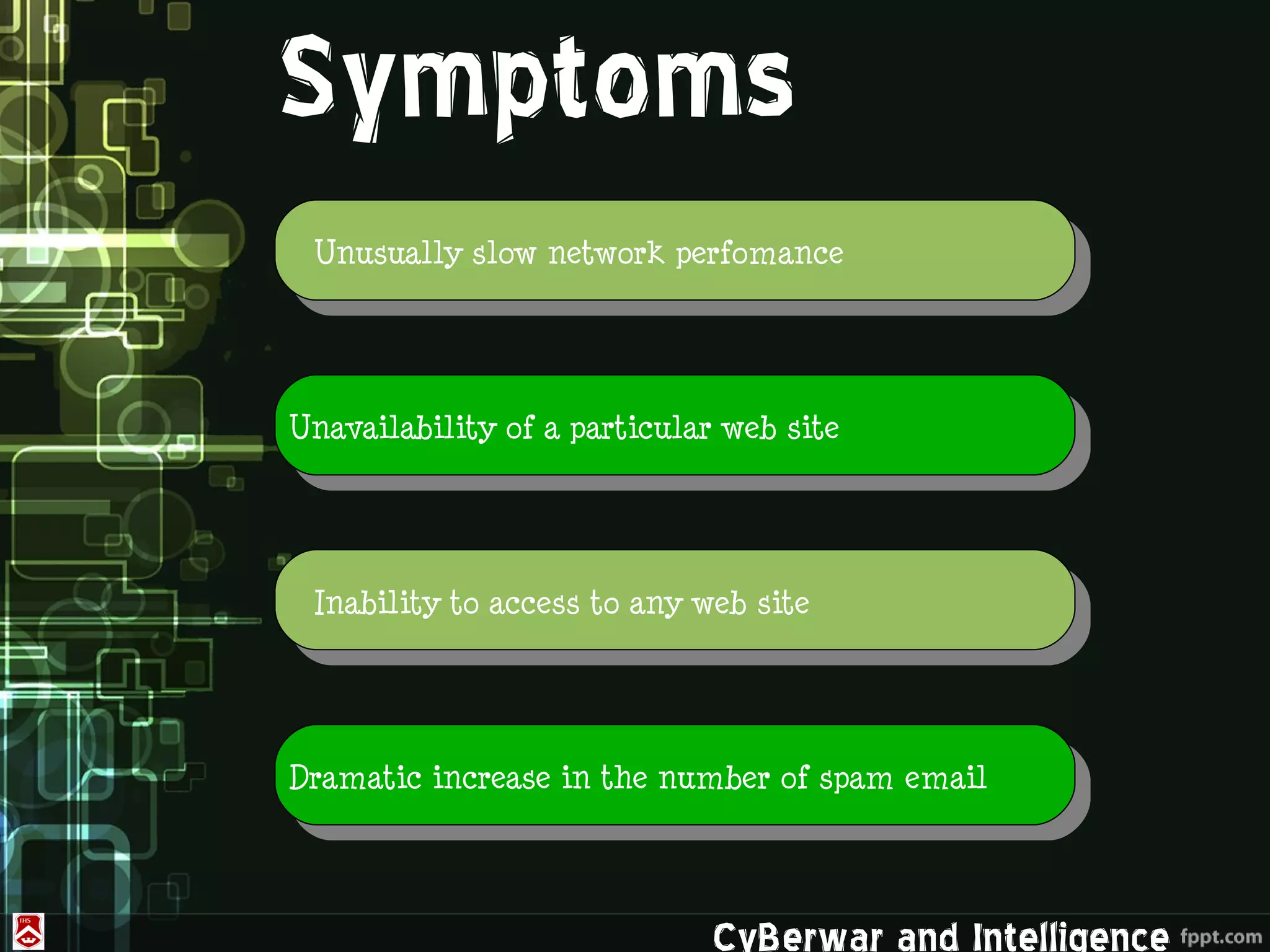
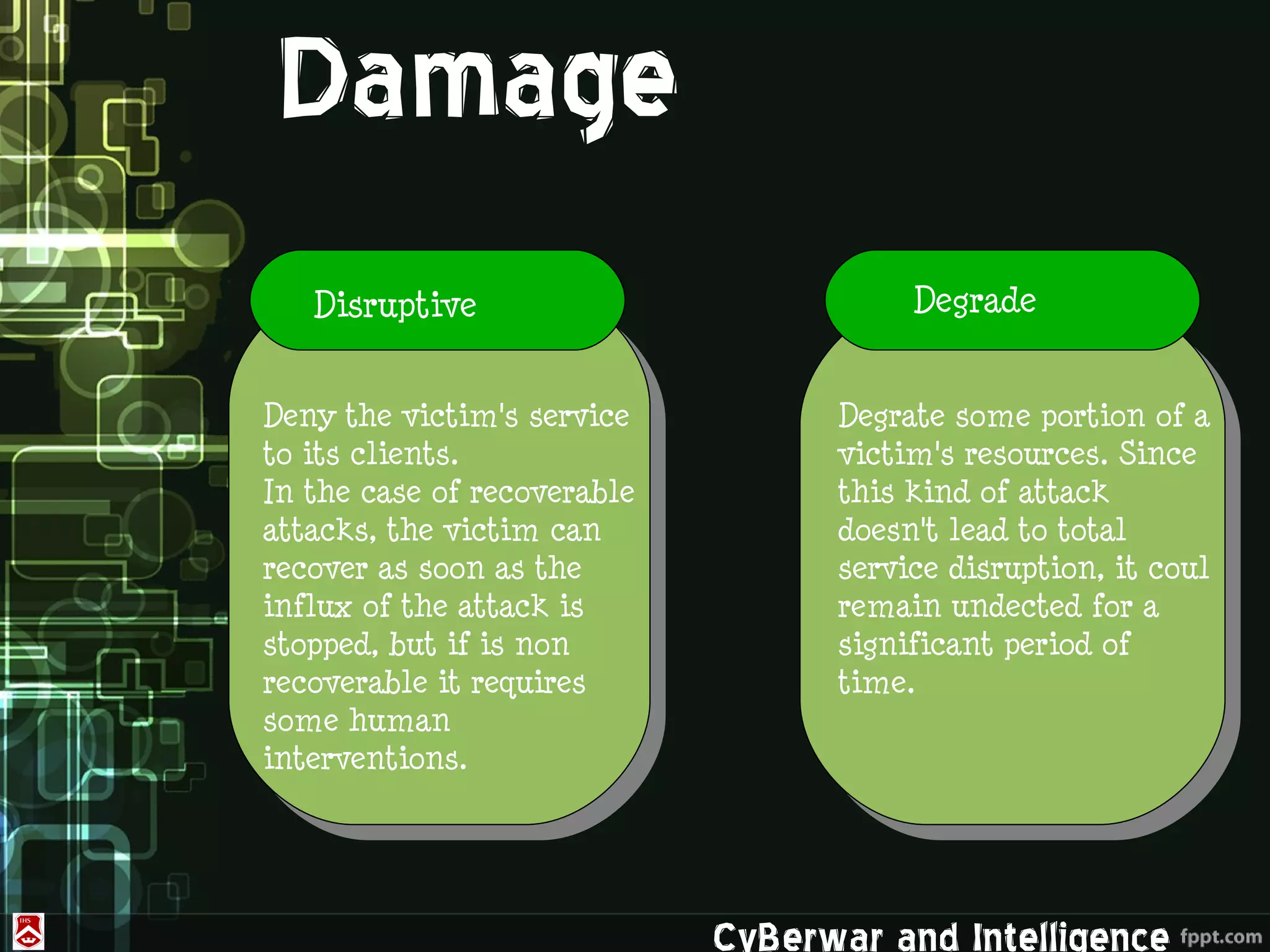
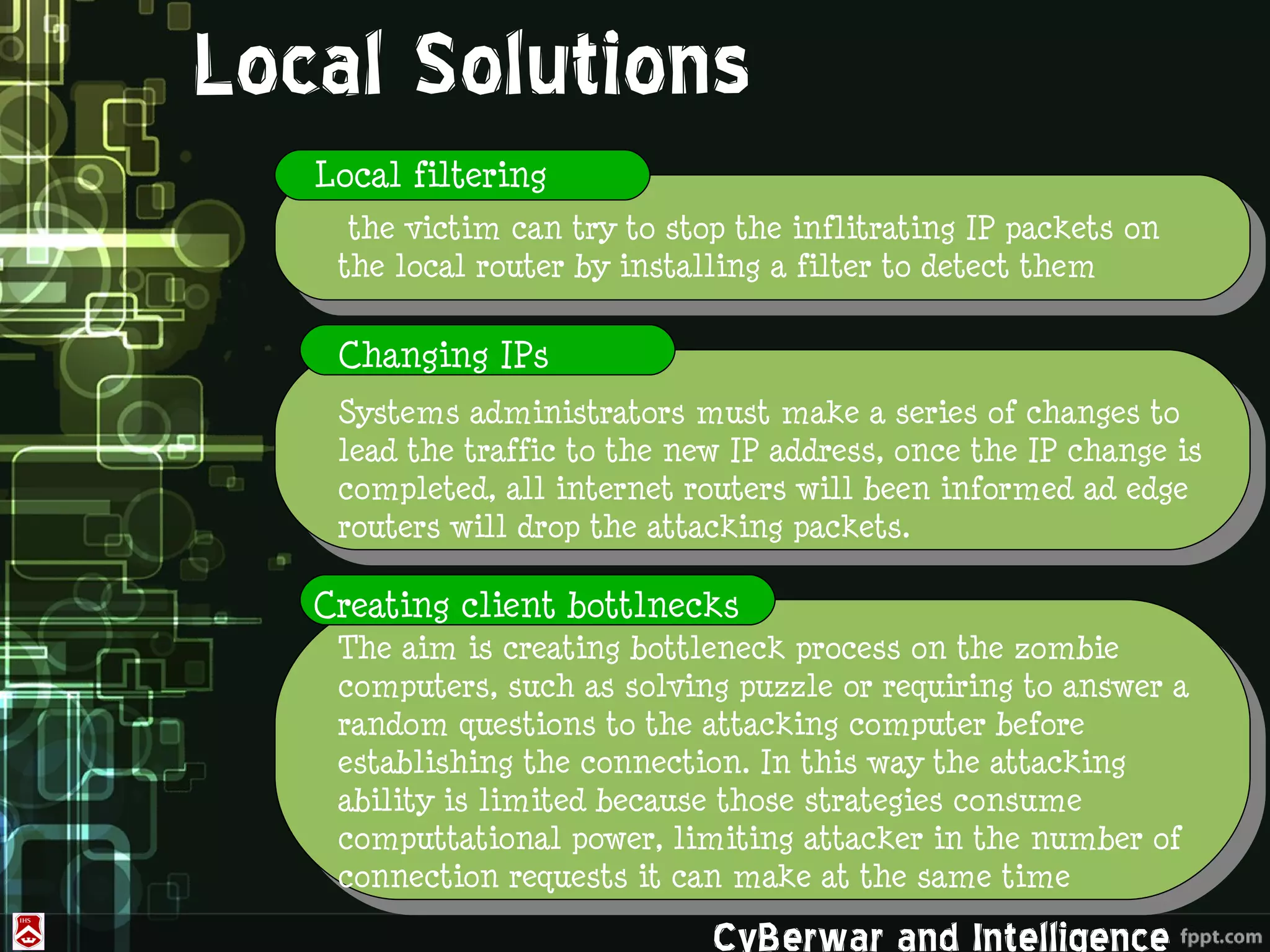
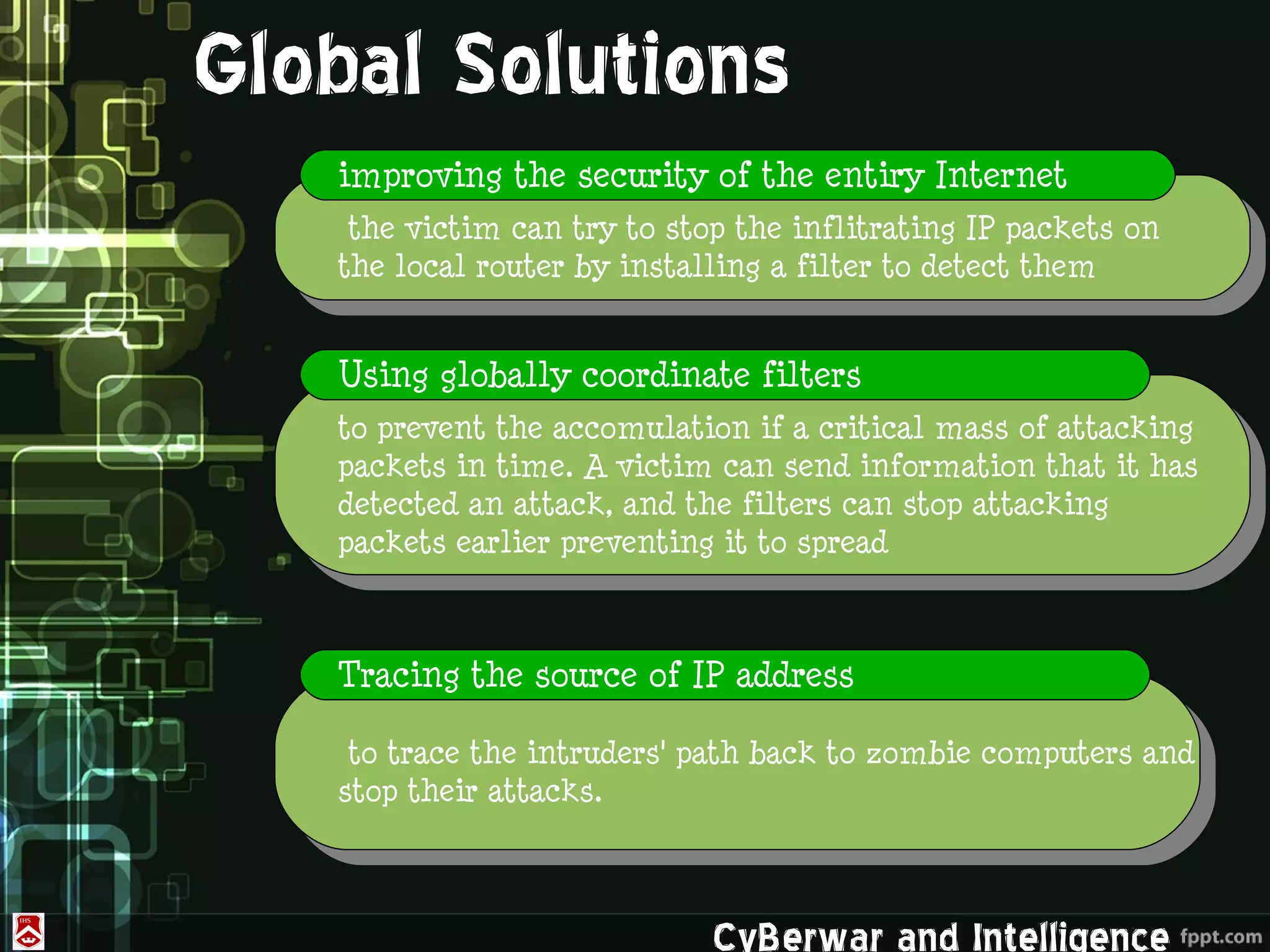
This document discusses denial of service (DoS) and distributed denial of service (DDoS) attacks. It defines various types of malware used in such attacks like viruses, worms, Trojans, and bots. It explains how DDoS attacks work using multiple compromised systems or "zombie computers" controlled by an attacker. The document outlines different DDoS attack methods and provides examples of DDoS attacks against Estonia and Georgia. It discusses challenges in preventing such attacks and potential solutions like improving overall internet security, using coordinated filters, and tracing attacks back to their source.