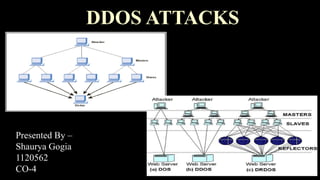
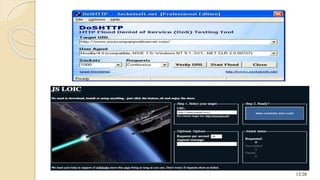
This document discusses distributed denial of service (DDoS) attacks. It begins with an introduction that defines DDoS attacks as attempts to make an online service unavailable by overwhelming it with traffic from multiple compromised sources. The document then covers the basics of DDoS attacks, common symptoms, how they work by exploiting vulnerabilities in systems to create botnets for launching attacks, and various methods like ICMP floods and SYN floods. It also discusses ways to handle DDoS attacks through defenses like firewalls, switches, and routers. The document concludes with preventative and reactive defense mechanisms to detect and respond to attacks.