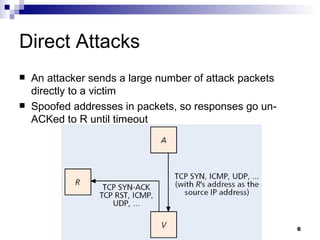
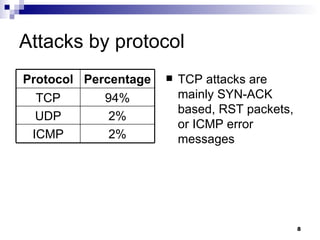
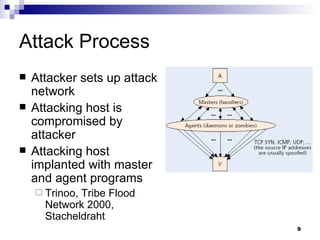
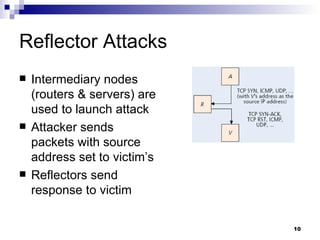
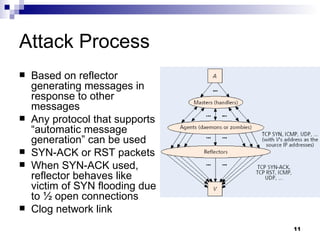
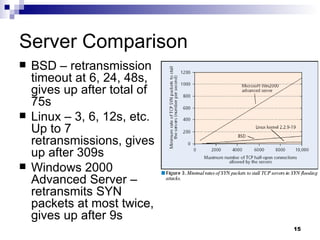
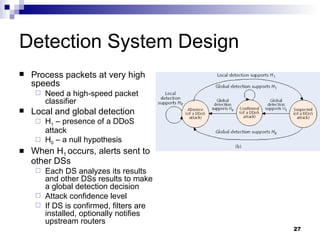
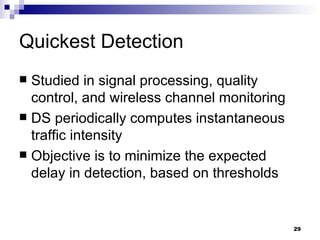
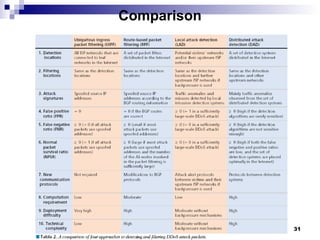
The document discusses defending against distributed denial-of-service (DDoS) attacks and proposes solutions. It describes types of DDoS attacks like SYN flooding and reflector attacks. It then analyzes solutions like route-based packet filtering and a distributed attack detection system using detection systems to identify attacks and install filters. The document concludes current defenses are inadequate and more effective detection-and-filtering approaches need to be developed.