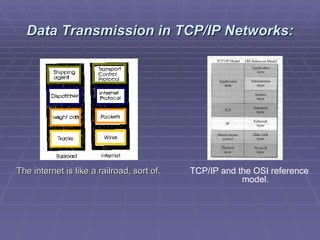
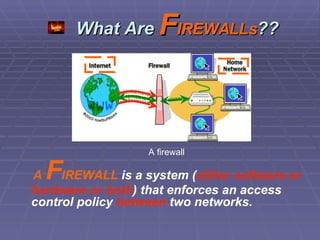
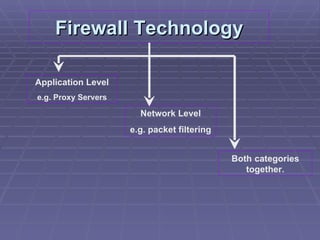
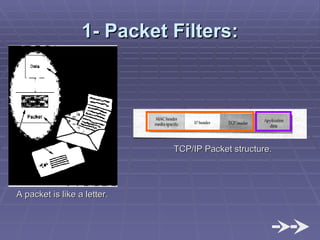
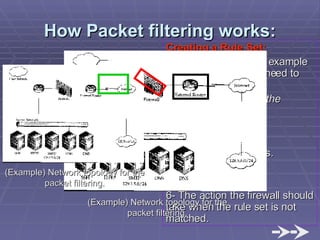
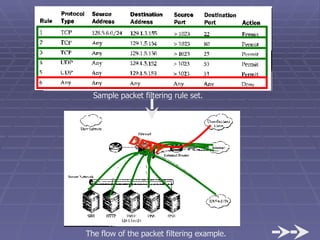
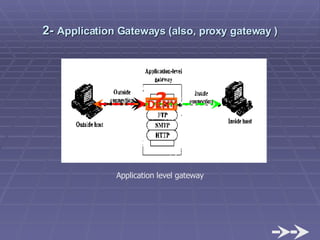
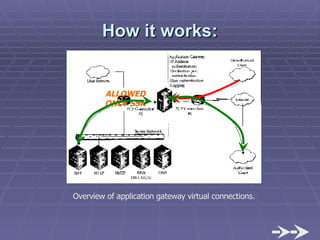
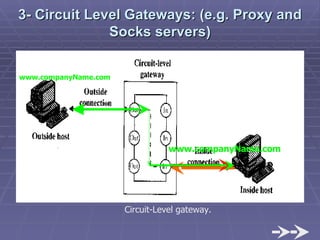
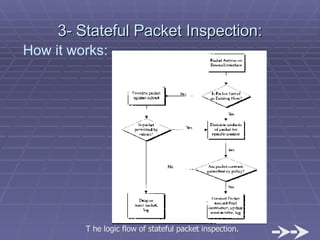
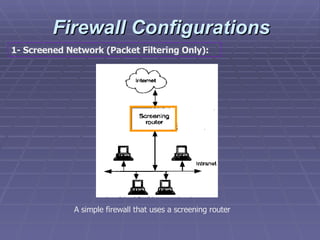
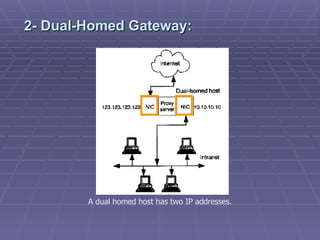
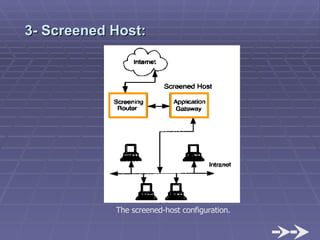
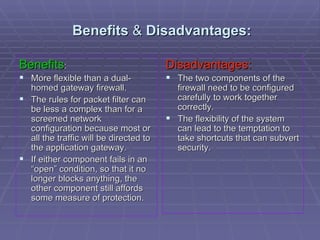
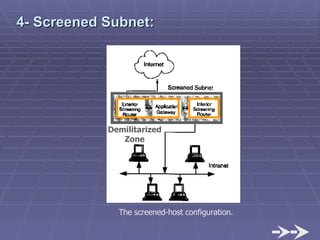
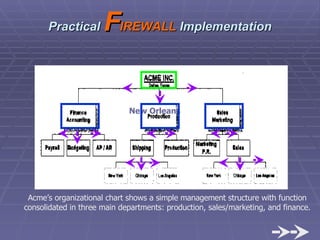
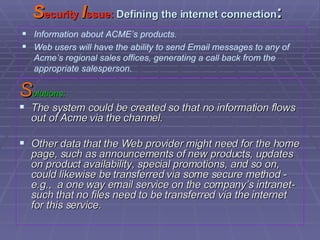
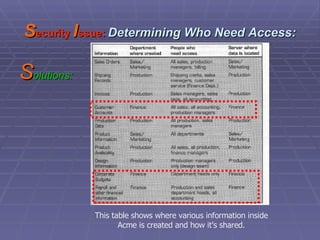
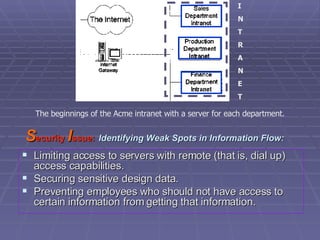
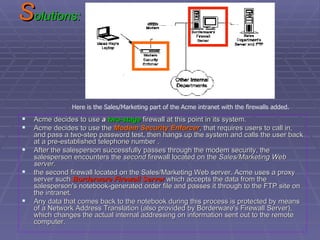
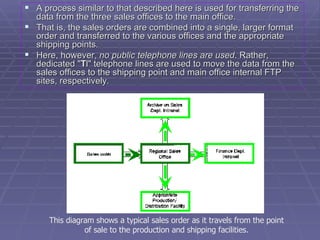
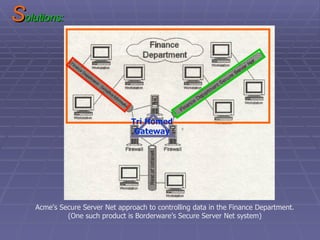
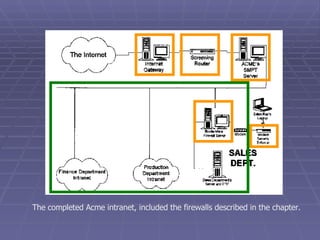
The document discusses firewall implementation for a company called Acme. It describes how Acme can set up firewalls to restrict access between internal and external networks and between different internal departments. Packet filtering, proxy servers, and demilitarized zones are implemented to enforce access controls and monitor network traffic flow while protecting sensitive data. The completed Acme intranet design includes multiple firewalls configured in screened subnets and dual-homed gateways to secure remote access and internal information flows.