Embed presentation
Download as PDF, PPTX




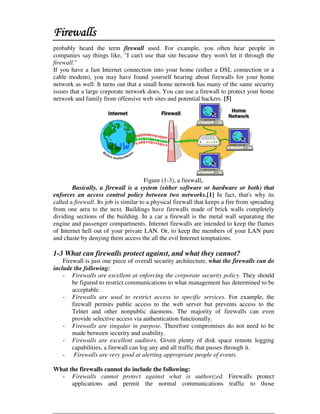


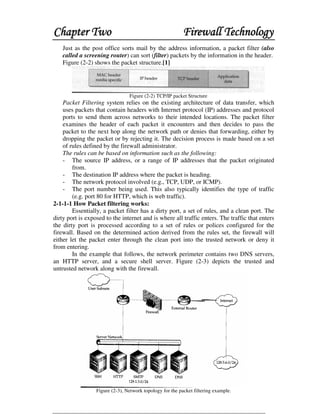
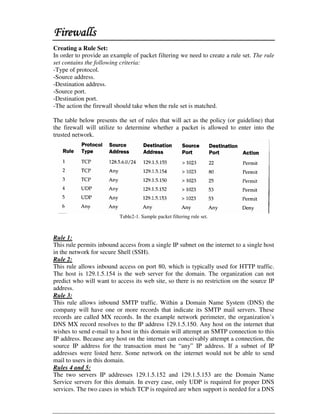
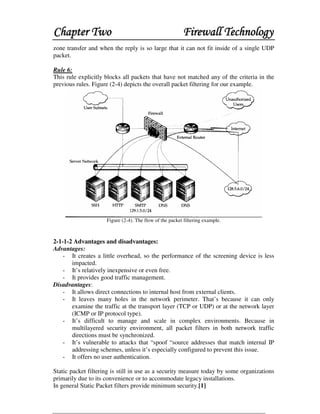
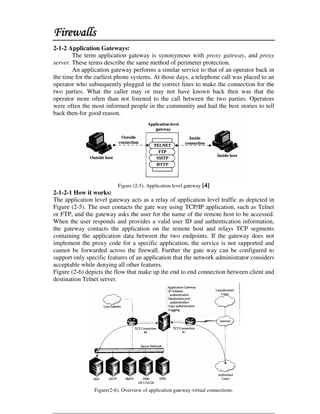

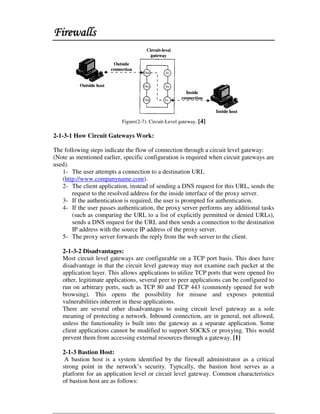



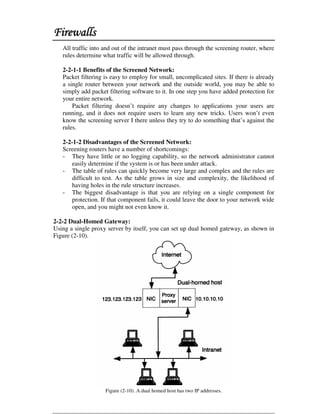
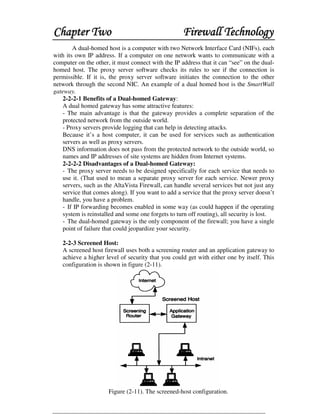
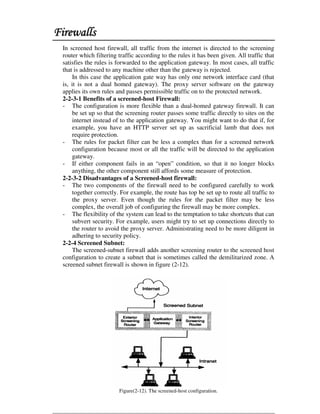

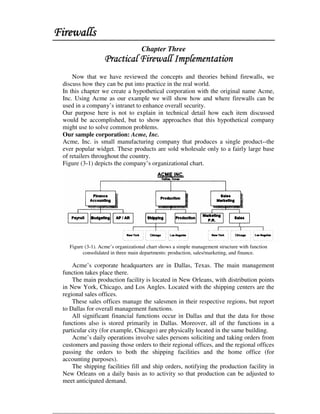

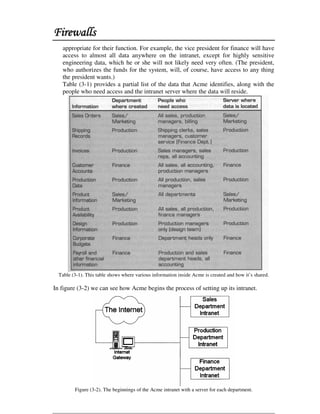

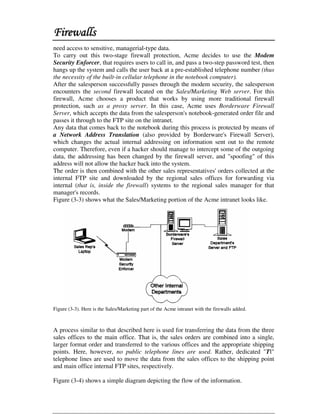
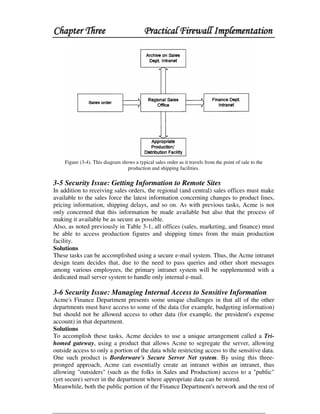
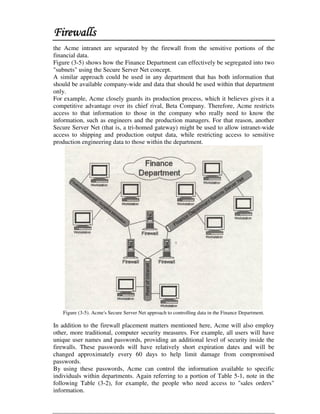

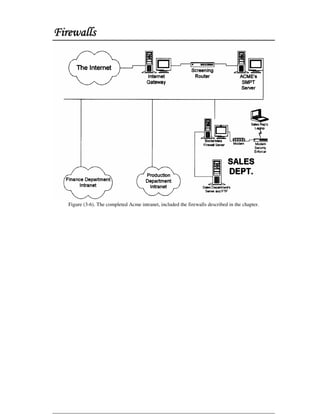


This document discusses firewall technology and architectures. It describes how packet filtering firewalls work by examining packet headers and applying rules to determine whether to allow or block packets from entering the network. Specifically, it provides an example of a packet filtering rule set that allows inbound access for secure shell, HTTP, SMTP, and DNS traffic from specified source IP addresses and ports to designated firewall-protected servers. The document also outlines some of the advantages and disadvantages of different firewall architectures like packet filtering, application gateways, and stateful packet inspection.






























