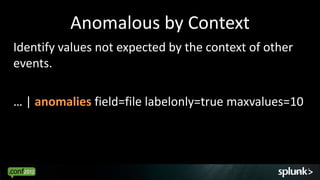
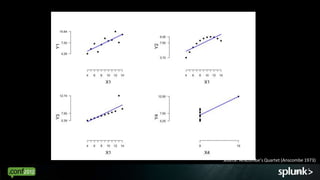
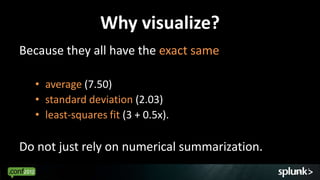
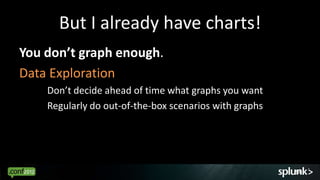
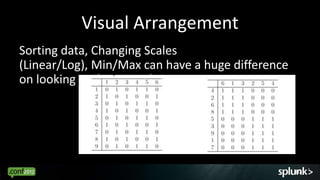
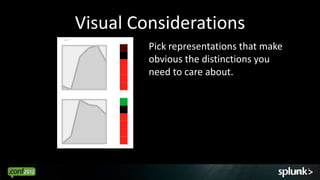
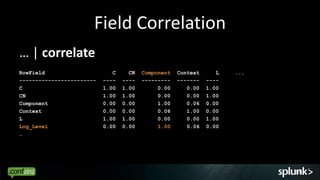
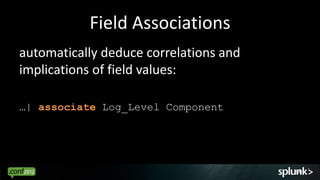
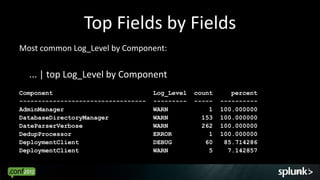
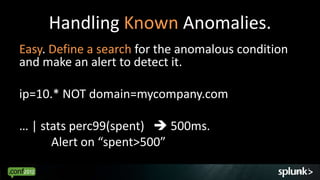
Look for events that are anomalous given their context, such as:
- Time of day (e.g. activity at 3am)
- Source/destination (e.g. traffic from unknown IP)
- Associated events (e.g. login without subsequent activity)
- Normal volume patterns (e.g. spike in requests)
Analyze events in context to identify deviations from normal patterns.







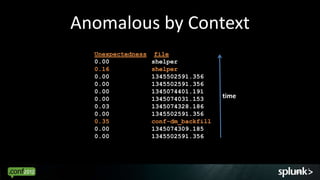
![Preparing the data
You've been thrown data you aren't familiar with…
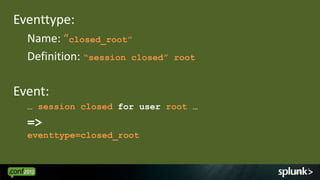
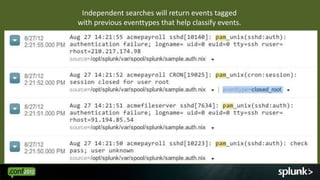
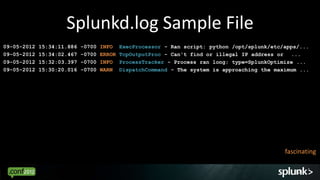
Mar 7 12:40:01 willLaptop crond(pam_unix)[10696]: session opened for user root by (uid=0)
Mar 7 12:40:01 willLaptop crond(pam_unix)[10695]: session closed for user root
Mar 7 12:40:02 willLaptop crond(pam_unix)[10696]: session closed for user root
Mar 7 12:44:47 willLaptop gconfd (root-10750): starting (version 2.10.0), pid 10750 user
'root'
Mar 7 12:44:47 willLaptop gconfd (root-10750): Resolved address
"xml:readonly:/etc/gconf/gconf.xml.mandatory" to a read-only config...
Mar 7 12:44:47 willLaptop gconfd (root-10750): Resolved address "xml:readwrite:/root/.gconf”…
Mar 7 12:45:01 willLaptop crond(pam_unix)[10754]: session opened for user root by (uid=0)
Mar 7 12:45:02 willLaptop crond(pam_unix)[10754]: session closed for user root
....
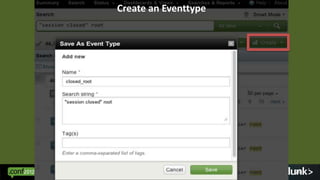
Eventtypes Fields Transactions Anomalies
(closed sessions) (pid) (open-close) (unexpected
address)
9](https://image.slidesharecdn.com/datamining5-120914141941-phpapp01/85/Data-Mining-with-Splunk-9-320.jpg)

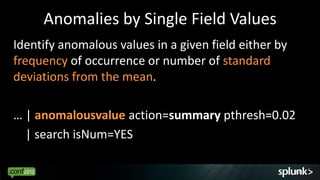
![Given Some Unknown Data
Mar 7 12:40:01 willLaptop crond(pam_unix)[10696]: session opened for user root by (uid=0)
Mar 7 12:40:01 willLaptop crond(pam_unix)[10695]: session closed for user root
Mar 7 12:40:02 willLaptop crond(pam_unix)[10696]: session closed for user root
Mar 7 12:44:47 willLaptop gconfd (root-10750): starting (version 2.10.0), pid 10750 user
'root'
Mar 7 12:44:47 willLaptop gconfd (root-10750): Resolved address
"xml:readonly:/etc/gconf/gconf.xml.mandatory" to a read-only config...
Mar 7 12:44:47 willLaptop gconfd (root-10750): Resolved address "xml:readwrite:/root/.gconf”…
Mar 7 12:44:47 willLaptop gconfd (root-10750): Resolved address
"xml:readonly:/etc/gconf/gconf.xml.defaults" to a read-only configuration ...
Mar 7 12:45:01 willLaptop crond(pam_unix)[10754]: session opened for user root by (uid=0)
Mar 7 12:45:02 willLaptop crond(pam_unix)[10754]: session closed for user root
....
12](https://image.slidesharecdn.com/datamining5-120914141941-phpapp01/85/Data-Mining-with-Splunk-12-320.jpg)


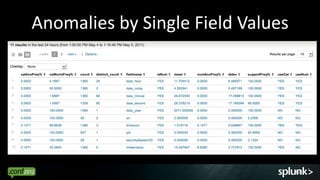
![Events By Content
count label _raw
--------------------------------------------------------------------------------------------------------
-
1339 3 Mar 7 11:05:01 willLaptop crond(pam_unix)[6785]: session opened for user root by…
1339 3 Mar 7 11:10:01 willLaptop crond(pam_unix)[1769]: session opened for user root by …
1339 3 Mar 7 11:10:01 willLaptop crond(pam_unix)[1766]: session opened for user root by …
1324 2 Mar 7 11:05:02 willLaptop crond(pam_unix)[6785]: session closed for user root
1324 2 Mar 7 11:10:01 willLaptop crond(pam_unix)[1766]: session closed for user root
1324 2 Mar 7 11:10:02 willLaptop crond(pam_unix)[1769]: session closed for user root
136 13 Mar 7 20:05:08 willLaptop kernel: SELinux: initialized (dev selinuxfs, type
selinuxfs)…
136 13 Mar 7 20:05:09 willLaptop kernel: SELinux: initialized (dev usbfs, type usbfs), uses …
136 13 Mar 7 20:05:09 willLaptop kernel: SELinux: initialized (dev sysfs, type sysfs), uses …
15](https://image.slidesharecdn.com/datamining5-120914141941-phpapp01/85/Data-Mining-with-Splunk-15-320.jpg)
![Events by Format
count smallpunct raw
------------------------------------------------------------------------------------------------
637 __::__( Mar 10 16:50:02 willLaptop crond(pam_unix)[9639]: session closed for user root
637 __::__( Mar 10 16:50:01 willLaptop crond(pam_unix)[9638]: session closed for user root
637 __::__( Mar 10 16:50:01 willLaptop crond(pam_unix)[9639]: session opened for user root by …
367 __::__: Mar 10 15:30:25 willLaptop dhclient: bound to 10.1.1.194 -- renewal in 5788 seconds.
367 __::__: Mar 10 15:30:25 willLaptop dhclient: DHCPACK from 10.1.1.50
367 __::__: Mar 10 15:30:25 willLaptop dhclient: DHCPREQUEST on eth0 to 10.1.1.50 port 67
57 __::__[ Mar 10 16:46:32 willLaptop ntpd[2544]: synchronized to 138.23.180.126, stratum 2
57 __::__[ Mar 10 16:46:27 willLaptop ntpd[2544]: synchronized to LOCAL(0), stratum 10
57 __::__[ Mar 10 16:42:09 willLaptop ntpd[2544]: time reset -0.236567 s
17](https://image.slidesharecdn.com/datamining5-120914141941-phpapp01/85/Data-Mining-with-Splunk-17-320.jpg)
![Group by Time Bursts
… | transaction maxpause=2s
| search eventcount>1
Mar 10 16:50:01 willLaptop crond(pam_unix)[9638]: session opened for user root by (uid=0)
Mar 10 16:50:01 willLaptop crond(pam_unix)[9639]: session opened for user root by (uid=0)
Mar 10 16:50:01 willLaptop crond(pam_unix)[9638]: session closed for user root
Mar 10 16:50:02 willLaptop crond(pam_unix)[9639]: session closed for user root
Mar 10 15:30:25 willLaptop dhclient: DHCPREQUEST on eth0 to 10.1.1.50 port 67
Mar 10 15:30:25 willLaptop dhclient: DHCPACK from 10.1.1.50
Mar 10 15:30:25 willLaptop dhclient: bound to 10.1.1.194 -- renewal in 5788 seconds.
Mar 10 16:45:01 willLaptop crond(pam_unix)[9553]: session opened for user root by (uid=0)
Mar 10 16:45:02 willLaptop crond(pam_unix)[9553]: session closed for user root
19](https://image.slidesharecdn.com/datamining5-120914141941-phpapp01/85/Data-Mining-with-Splunk-19-320.jpg)








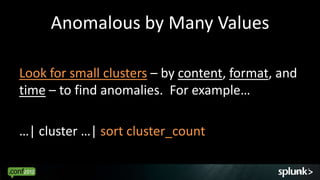
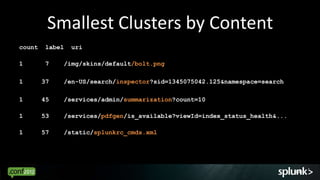
![Small Clusters: Bursts of One
Find bursts of just a single events where a pause of 2 seconds
occurred around it.
… |transaction maxpause=2s | search eventcount = 1
Mar 10 16:46:32 willLaptop ntpd[2544]: synchronized to 138.23.180.126…
Mar 10 16:46:27 willLaptop ntpd[2544]: synchronized to LOCAL(0), stratum…
Mar 10 16:42:09 willLaptop ntpd[2544]: time reset -0.236567…
45](https://image.slidesharecdn.com/datamining5-120914141941-phpapp01/85/Data-Mining-with-Splunk-45-320.jpg)
![Burst of One
Same idea, different data source: splunk
[11:58:08] "POST /services/search/jobs/export HTTP/1.1" 200 201630 …
[11:12:51] "POST /services/search/jobs/export HTTP/1.1" 200 459441 …
[10:00:58] "GET /servicesNS/nobody/SplunkDeploymentMonitor/backfill/…
46](https://image.slidesharecdn.com/datamining5-120914141941-phpapp01/85/Data-Mining-with-Splunk-46-320.jpg)