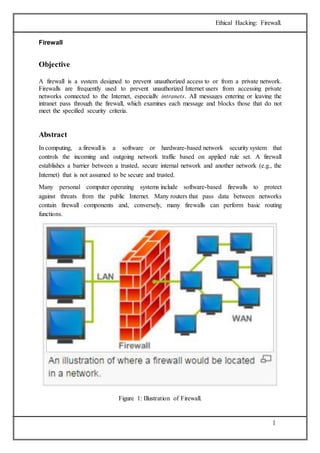
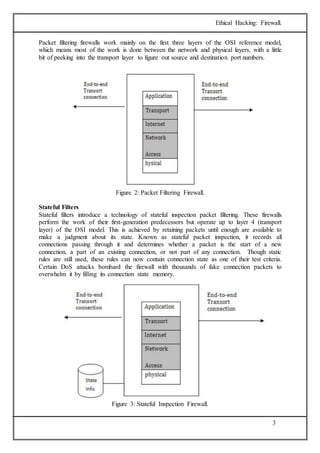
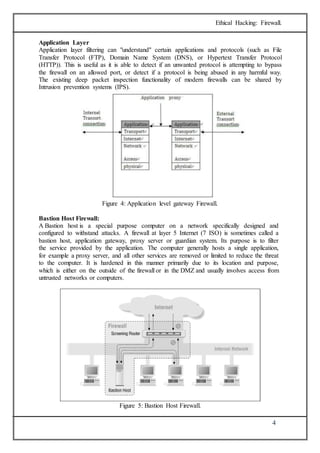
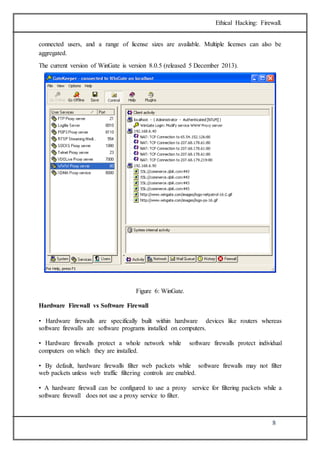
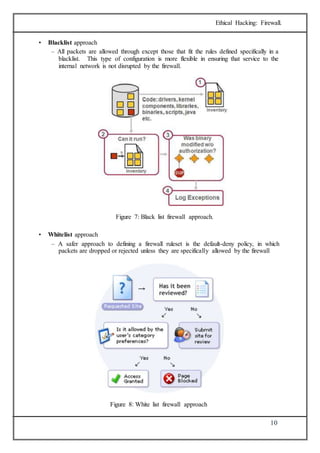
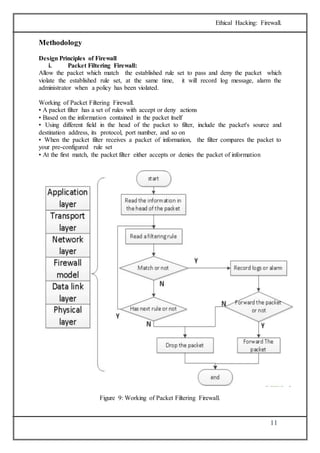
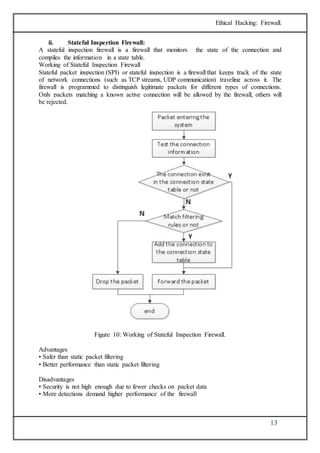
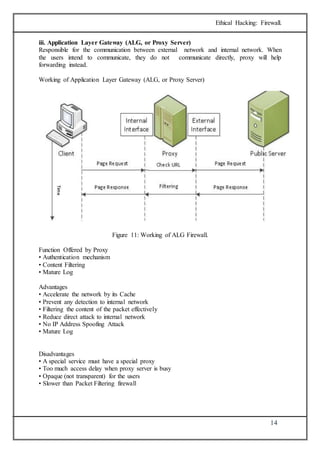
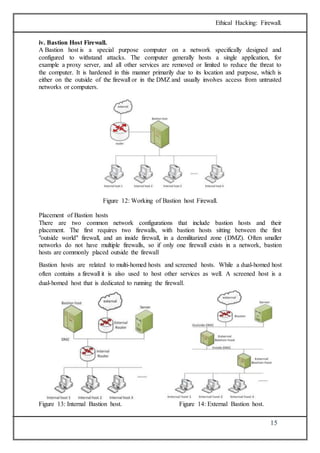
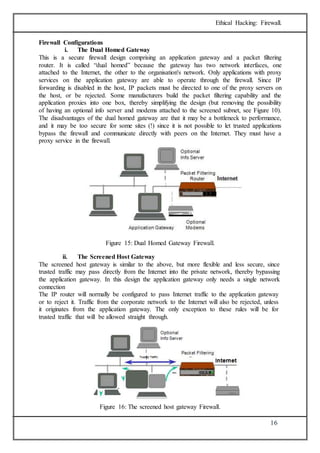
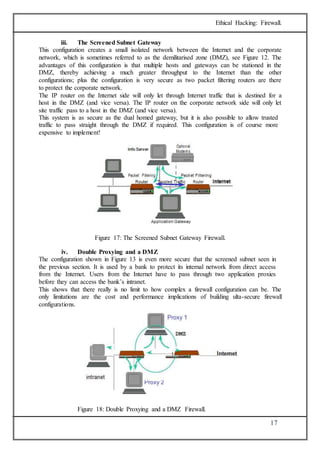
The document discusses firewalls, which are systems designed to prevent unauthorized access to private networks, explaining their components, types (packet filtering, stateful filters, application layer, and bastion hosts), and their roles in cybersecurity. It reviews the evolution of firewalls, starting from first-generation packet filters to advanced application-layer firewalls, detailing the attacks they defend against and the methodologies for implementing firewall policies. Additionally, it highlights the differences between hardware and software firewalls, and provides insights into firewall analysis and configuration challenges.