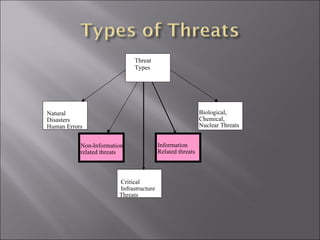
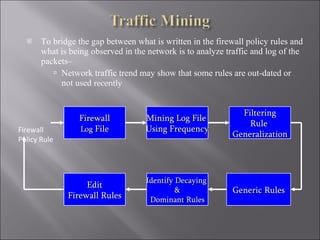
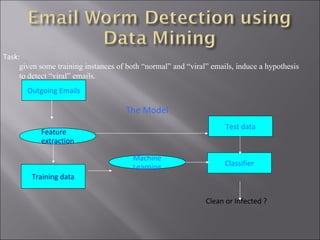
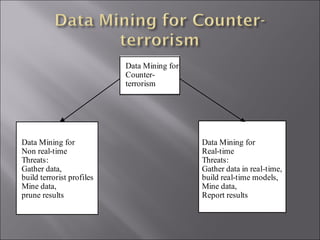
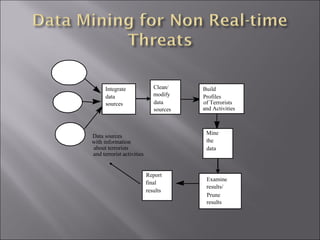
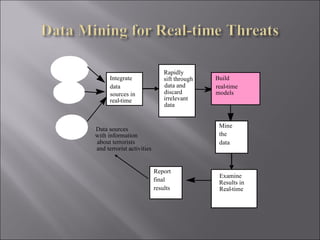
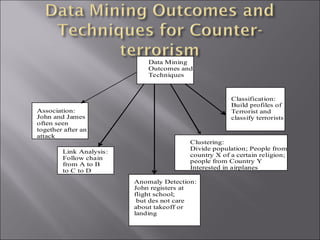
The document discusses various ways that data mining can be applied for security applications such as intrusion detection, firewall policy management, worm detection, and counter-terrorism surveillance. It describes techniques like anomaly detection, link analysis, classification, and prediction that can help detect cyber attacks, trace malware authors, and predict future threats. It also addresses challenges of working with real-time streaming data from sensors for critical applications.


![Data Mining - Extraction of interesting ( non-trivial, implicit, previously unknown and potentially useful) information or patterns from data in large databases [Han and Kamber 2005]. Data mining is used to sort through the tremendous amounts of data stored by automated data collection tools. Extracts rules, regularities, patterns, and constraints from databases.](https://image.slidesharecdn.com/p10co9823-110828073718-phpapp01/85/data-mining-for-security-application-3-320.jpg)