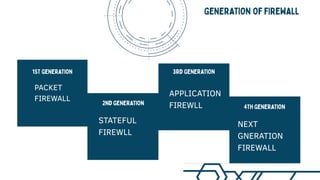
The document provides an overview of information technology and firewalls. It discusses what a firewall is, the history and types of firewalls, how firewalls work, the need for firewalls, advantages and disadvantages of firewalls, and real-time applications of firewalls. The types of firewalls discussed include packet filtering firewalls, stateful firewalls, application firewalls, and next generation firewalls. Examples are given of how firewalls can protect corporate networks, government organizations, service providers, small enterprises, home networks, and industrial control systems.