Firewall
•Download as PPTX, PDF•
1 like•457 views
Stateful Packet Inspection (SPI) keeps track of TCP and UDP connections through a state table containing details like source/destination IPs and ports, sequence numbers, and timestamps. It allows established connections from inside to outside but blocks new connections initiated from outside. SPI can detect replayed packets through unexpected sequence numbers or timestamps. By default, the firewall also filters anonymous internet requests, IDENT port 113 requests, and starts dropping connections initiated from outside.
Report
Share
Report
Share
Recommended
Anonymous Security Scanning and Browsing

It is for Information Security professionals, to perform anonymous scans and browsing. This presentation will guide to perform nmap and burp scans using TOR network.
Network scanning

A quick guide to describe the basic of Network and network scanning by oceanofwebs.com
How Microsoft will MiTM your network

A scenario on basic incident response and showing how Microsoft uses a service that automatically creates a Man in the Middle incident. It also covers an overview on some inherent tools and how to use them for security operations
Recommended
Anonymous Security Scanning and Browsing

It is for Information Security professionals, to perform anonymous scans and browsing. This presentation will guide to perform nmap and burp scans using TOR network.
Network scanning

A quick guide to describe the basic of Network and network scanning by oceanofwebs.com
How Microsoft will MiTM your network

A scenario on basic incident response and showing how Microsoft uses a service that automatically creates a Man in the Middle incident. It also covers an overview on some inherent tools and how to use them for security operations
Port scanning

About Port Scanning
Used Nmap and Shadow Security scanner for the best outputs.
A Detailed description on performing the port scanning mostly for the network administrators.
How to perform? Why to perform? Where to perform? The basic factors are taken into considerations and are provided in the presentation.
Darkweb + Python: discover, analyze and extract information from hidden services

Darkweb + Python: discover, analyze and extract information from hidden servicesJose Manuel Ortega Candel
The talk will start explaining how Tor project can help us to the research and development of tools for online anonymity and privacy of its users while surfing the Internet, by establishing virtual circuits between the different nodes that make up the Tor network. In addition, we will review how Tor works from anonymity point of view, preventing websites from tracking you. Python help us to automate the process to search an discover hidden services thanks to packages like requests,requesocks and sockspy,At this point we will review the crawling process and show tools in python ecosystem available for this task(https://github.com/jmortega/python_dark_web)
These could be the talking points:
-Introduction to Tor project and hidden services
-Discovering hidden services.
-Modules and packages we can use in python for connecting with Tor network
-Tools that allow search hidden services and atomate the crawling process in Tor networkTekTape - Audio Recorder for SIP Calls

TekTape is an audio recorder and call detail records (CDR) generator for Windows.
Barriers to TOR Research at UC Berkeley

A talk given by Joseph Lorenzo Hall at the UCB TRUST Privacy workshop on 10/05/2006 that describes the tensions between institutional requirements and technical abilities of the TOR network, which severly limits TOR research on the UCB campus.
Layer 8 and Why People are the Most Important Security Tool

People are the cause of many security problems, but people are also the most effective resource for combating them. Technology is critical, but without trained professionals, it is ineffective. In the context two case studies, the presenter will describe specific instances where human creativity and skill overcame technical deficiencies. The presenter believes this topic to be particularly relevant for the Packet Hacking Village, as many techniques used are the same that are pertinent for Capture the Packet and Packet Detective.
Technical details will include the specific tools used, screenshots of captured data, and analysis of the malware and the malicious user’s activity. The goal of the presentation is show the importance of technical ability and critical thinking, and to demonstrate that skilled people are the most important tool in an information security program.
Access control list [1]![Access control list [1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Access control list [1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Access list complete details for more details go to the netbis education on youtube or website
More Related Content
What's hot
Port scanning

About Port Scanning
Used Nmap and Shadow Security scanner for the best outputs.
A Detailed description on performing the port scanning mostly for the network administrators.
How to perform? Why to perform? Where to perform? The basic factors are taken into considerations and are provided in the presentation.
Darkweb + Python: discover, analyze and extract information from hidden services

Darkweb + Python: discover, analyze and extract information from hidden servicesJose Manuel Ortega Candel
The talk will start explaining how Tor project can help us to the research and development of tools for online anonymity and privacy of its users while surfing the Internet, by establishing virtual circuits between the different nodes that make up the Tor network. In addition, we will review how Tor works from anonymity point of view, preventing websites from tracking you. Python help us to automate the process to search an discover hidden services thanks to packages like requests,requesocks and sockspy,At this point we will review the crawling process and show tools in python ecosystem available for this task(https://github.com/jmortega/python_dark_web)
These could be the talking points:
-Introduction to Tor project and hidden services
-Discovering hidden services.
-Modules and packages we can use in python for connecting with Tor network
-Tools that allow search hidden services and atomate the crawling process in Tor networkTekTape - Audio Recorder for SIP Calls

TekTape is an audio recorder and call detail records (CDR) generator for Windows.
Barriers to TOR Research at UC Berkeley

A talk given by Joseph Lorenzo Hall at the UCB TRUST Privacy workshop on 10/05/2006 that describes the tensions between institutional requirements and technical abilities of the TOR network, which severly limits TOR research on the UCB campus.
Layer 8 and Why People are the Most Important Security Tool

People are the cause of many security problems, but people are also the most effective resource for combating them. Technology is critical, but without trained professionals, it is ineffective. In the context two case studies, the presenter will describe specific instances where human creativity and skill overcame technical deficiencies. The presenter believes this topic to be particularly relevant for the Packet Hacking Village, as many techniques used are the same that are pertinent for Capture the Packet and Packet Detective.
Technical details will include the specific tools used, screenshots of captured data, and analysis of the malware and the malicious user’s activity. The goal of the presentation is show the importance of technical ability and critical thinking, and to demonstrate that skilled people are the most important tool in an information security program.
Access control list [1]![Access control list [1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Access control list [1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Access list complete details for more details go to the netbis education on youtube or website
What's hot (20)
Darkweb + Python: discover, analyze and extract information from hidden services

Darkweb + Python: discover, analyze and extract information from hidden services
St Louis Linux Users Group Wireguard (for Fun and Networking)

St Louis Linux Users Group Wireguard (for Fun and Networking)
Layer 8 and Why People are the Most Important Security Tool

Layer 8 and Why People are the Most Important Security Tool
Router security-configuration-guide-executive-summary

Router security-configuration-guide-executive-summary
Viewers also liked
Firewall diapositivas (Stephanie Hernández ) ( Tercer grado de Secundaria)

Firewall diapositivas (Stephanie Hernández ) ( Tercer grado de Secundaria)Stephanie Alejandra Hernández Morales
Diapositivas de firewall. Proyecto de la clase de informática, impartida por el profesor: Freddy Cálcaneo Soberano.
La fecha de entrega es: Lunes 23 de Enero del 2017, pero está siendo entregada el Jueves 19 de Enero del 2017Data Value Creation in the Industrial IoT

A short overview and engagement strategy for data driven value for enterprise projects in the industrial internet of things,
Firewall Architecture 

This Presentation Related to Firewall Architecture And It's Components.I am also Includes definition of firewall and categories of firewall.
Tracxn Research — Industrial IoT Landscape, October 2016

By company formation, over 374 companies emerged in this space over the last three years, indicating a positive trend for this sector, going forward.
Firewall 

Hai...!! Here the powerpoint gives you a clear idea about Firewall and its types..
Make use of it..
Internet of Things & Hardware Industry Report 2016

Overview of industry trends and insights of Fortune 500 companies and startups' activities in the Internet of Things (IoT) and hardware space. We cover connected home, wearables, healthcare, robotics & drones, and industrial IoT.
Viewers also liked (12)
Firewall diapositivas (Stephanie Hernández ) ( Tercer grado de Secundaria)

Firewall diapositivas (Stephanie Hernández ) ( Tercer grado de Secundaria)
Tracxn Research — Industrial IoT Landscape, October 2016

Tracxn Research — Industrial IoT Landscape, October 2016
Internet of Things & Hardware Industry Report 2016

Internet of Things & Hardware Industry Report 2016
Similar to Firewall
Network tunneling techniques

Network Protocol Tunneling Techniques for Network Security Controls Bypass
TOR... ALL THE THINGS

The global Tor network and its routing protocols provide an excellent framework for online anonymity. However, the selection of Tor-friendly software for Windows is sub-par at best.
Want to anonymously browse the web? You’re stuck with Firefox, and don’t even think about trying to anonymously use Flash. Want to dynamically analyze malware without letting the C2 server know your home IP address? You’re outta luck. Want to anonymously use any program that doesn’t natively support SOCKS or HTTP proxying? Not gonna happen.
While some solutions currently exist for generically rerouting traffic through Tor, these solutions either don’t support Windows, or can be circumvented by malware, or require an additional network gateway device.
Missed the live session at Black Hat USA 2013? Check out the slides from Jason Geffner's standing room only presentation! Jason released a free new CrowdStrike community tool to securely, anonymously, and transparently route all TCP/IP and DNS traffic through Tor, regardless of the client software, and without relying on VPNs or additional hardware or virtual machines.
Network security

THREATS are possible attacks.
It includes
The spread of computer viruses
Infiltration and theft of data from external hackers
Engineered network overloads triggered by malicious mass e-mailing
Misuse of computer resources and confidential information by employees
Unauthorized financial transactions and other kinds of computer fraud conducted in the company's name
Electronic inspection of corporate computer data by outside parties
Damage from failure, fire, or natural disasters
Practical Malware Analysis Ch 14: Malware-Focused Network Signatures

Slides from a college course. More info: https://samsclass.info/126/126_S16.shtml
WIFI MODEM Part-22

Wi-Fi (or WiFi) is a local area wireless computer networking technology that allows electronic devices to network, mainly using the 2.4 gigahertz (12 cm) UHF and 5 gigahertz (6 cm) SHF ISM radio bands.
The Wi-Fi Alliance defines Wi-Fi as any "wireless local area network" (WLAN) product based on the Institute of Electrical and Electronics Engineers' (IEEE) 802.11 standards".[1] However, the term "Wi-Fi" is used in general English as a synonym for "WLAN" since most modern WLANs are based on these standards. "Wi-Fi" is a trademark of the Wi-Fi Alliance. The "Wi-Fi Certified" trademark can only be used by Wi-Fi products that successfully complete Wi-Fi Alliance interoperability certification testing.
Many devices can use Wi-Fi, e.g. personal computers, video-game consoles, smartphones, digital cameras, tablet computers and digital audio players. These can connect to a network resource such as the Internet via a wireless network access point. Such an access point (or hotspot) has a range of about 20 meters (66 feet) indoors and a greater range outdoors. Hotspot coverage can be as small as a single room with walls that block radio waves, or as large as many square kilometres achieved by using multiple overlapping access points.
Depiction of a device sending information wirelessly to another device, both connected to the local network, in order to print a document.
Wi-Fi can be less secure than wired connections, such as Ethernet, precisely because an intruder does not need a physical connection. Web pages that use TLS are secure, but unencrypted internet access can easily be detected by intruders. Because of this, Wi-Fi has adopted various encryption technologies. The early encryption WEP proved easy to break. Higher quality protocols (WPA, WPA2) were added later. An optional feature added in 2007, called Wi-Fi Protected Setup (WPS), had a serious flaw that allowed an attacker to recover the router's password.[2] The Wi-Fi Alliance has since updated its test plan and certification program to ensure all newly certified devices resist attacks .
Firewall and Types of firewall

In this PPT you can learn a firewall and types which help you a lot and you can able to understand. So, that you must read at once I sure that you are understand
Thank you!!!
I
osint + python: extracting information from tor network and darkweb 

The talk will start explaining how Tor project can help us to the research and development of tools for online anonymity and privacy of its users while surfing the Internet, by establishing virtual circuits between the different nodes that make up the Tor network. Later, we will review main tools for discover hidden services in tor network with osint tools. Finally we will use python for extracting information from tor network with specific modules like stem https://stem.torproject.org/
These could be the main points of the talk:
- Introduction to Tor project and hidden services
- Discovering hidden services with osint tools
- Extracting information from tor network with python
Similar to Firewall (20)
Practical Malware Analysis Ch 14: Malware-Focused Network Signatures

Practical Malware Analysis Ch 14: Malware-Focused Network Signatures
osint + python: extracting information from tor network and darkweb 

osint + python: extracting information from tor network and darkweb
More from lyndyv
More from lyndyv (16)
Firewall
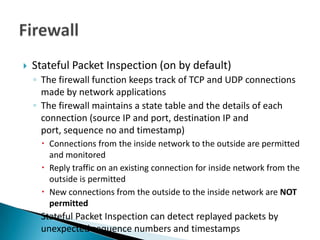
- 1. Stateful Packet Inspection (on by default) ◦ The firewall function keeps track of TCP and UDP connections made by network applications ◦ The firewall maintains a state table and the details of each connection (source IP and port, destination IP and port, sequence no and timestamp) Connections from the inside network to the outside are permitted and monitored Reply traffic on an existing connection for inside network from the outside is permitted New connections from the outside to the inside network are NOT permitted ◦ Stateful Packet Inspection can detect replayed packets by unexpected sequence numbers and timestamps
- 2. Filter anonymous Internet Requests (on by default) ◦ Drops pings from outside hosts and drops connection requests from the outside Filter Multicast (Off by default) ◦ Multicast traffic is sent to many hosts that are configured as part of a multicast group by registering with the multicast application ◦ Multicast is used to stream multimedia by allowing 1 stream to be sent to the router/switch and then the stream is copied to each registered host ◦ Disable filtering to permit multicast traffic ◦ Enable filtering to prevent multicast DOS attacks Filter Internet NAT Redirection (disabled) ◦ Block access to other local hosts from a local computer connection via the external NAT address Filter IDENT Port 113 (on by default) ◦ Drops IDENT requests which ask for info: local and remote ports, OS and username
- 3. SPI is Stateful Packet Inspection ◦ On by default By default ◦ Drop connections starting from the outside Drop request for identity info on Port 113 Web filter for proxy, java, activeX and cookies