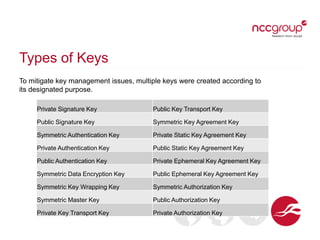
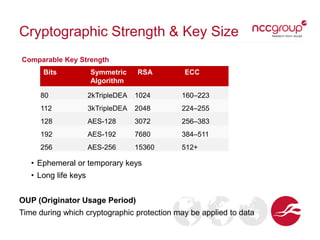
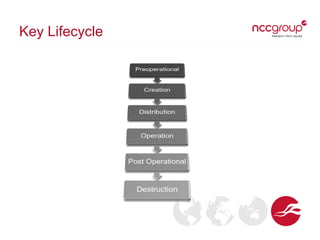
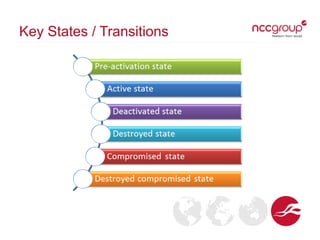
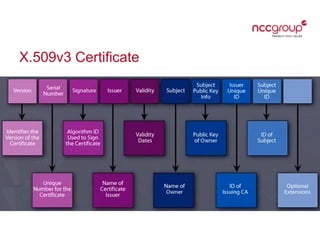
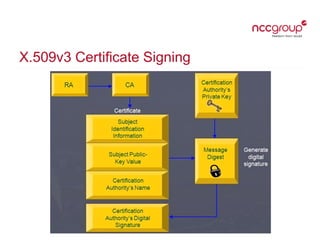
This document provides an overview of key management concepts and the key lifecycle in a PKI system. It discusses the different types of keys used in cryptography, including symmetric, asymmetric, and hashing keys. It describes each stage of the key lifecycle from pre-operational tasks like key registration through creation, distribution, operation, post-operation, and destruction. It also examines digital certificates based on the X.509 standard and provides an example of an SSL certificate.