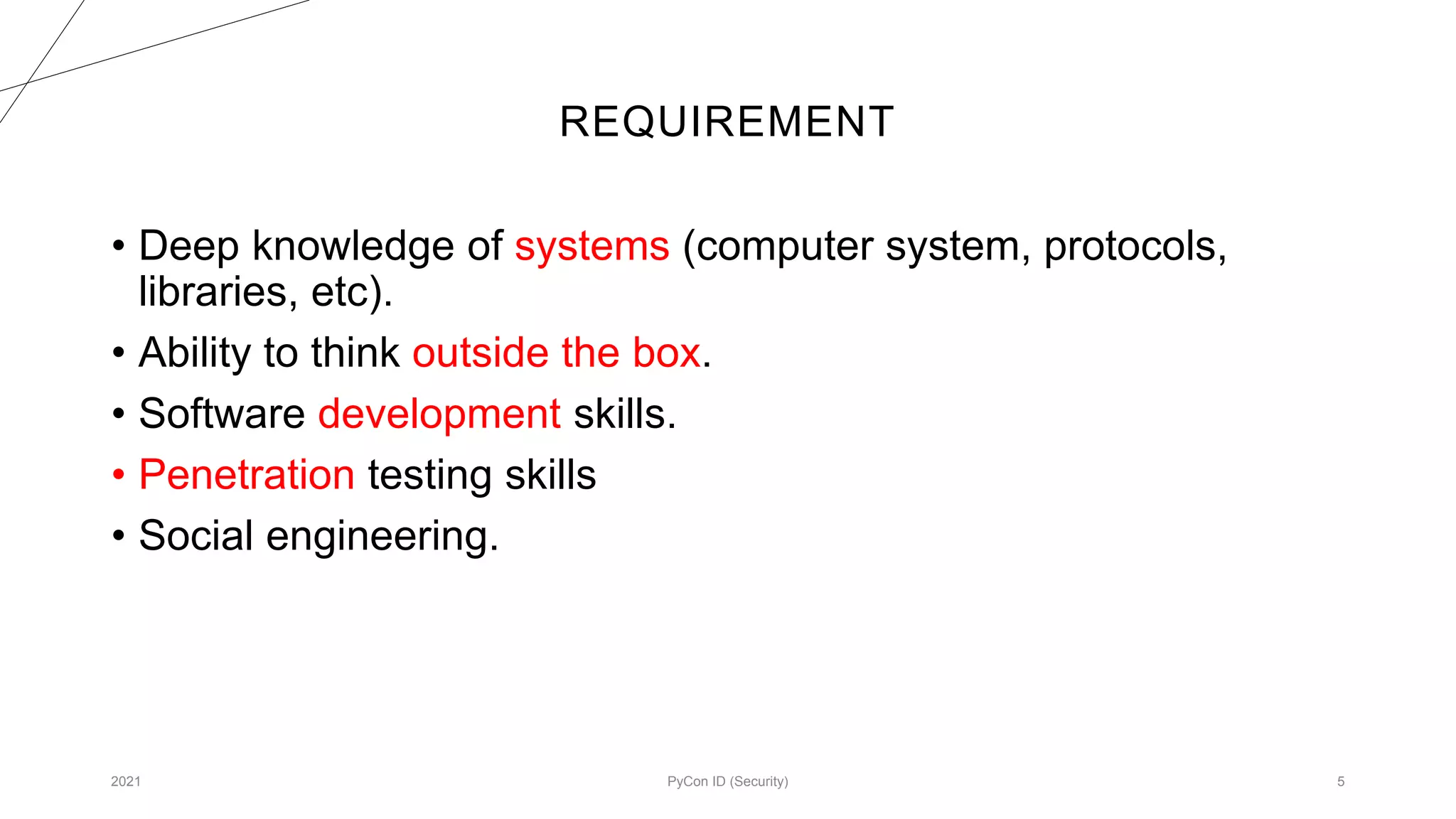
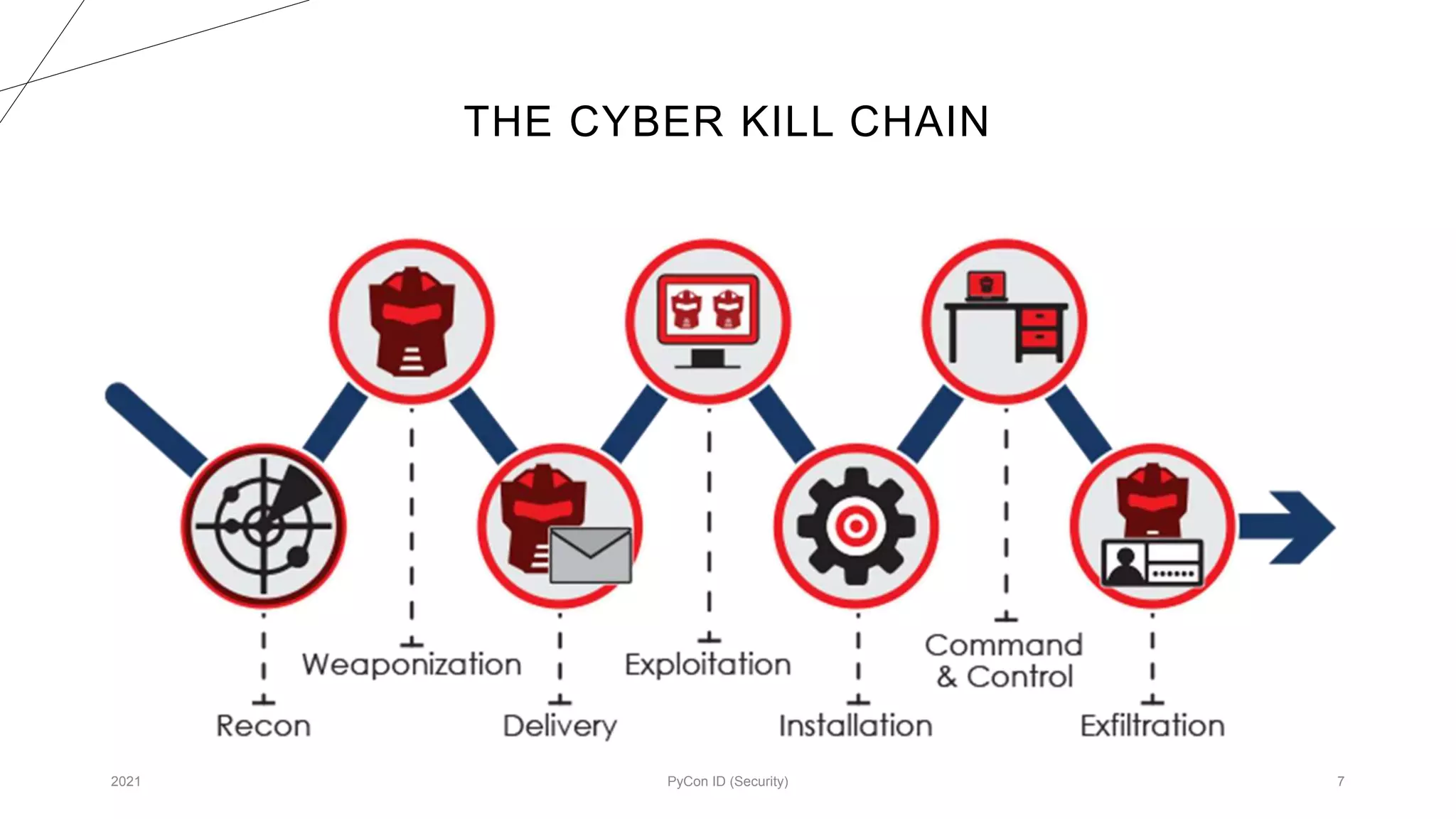
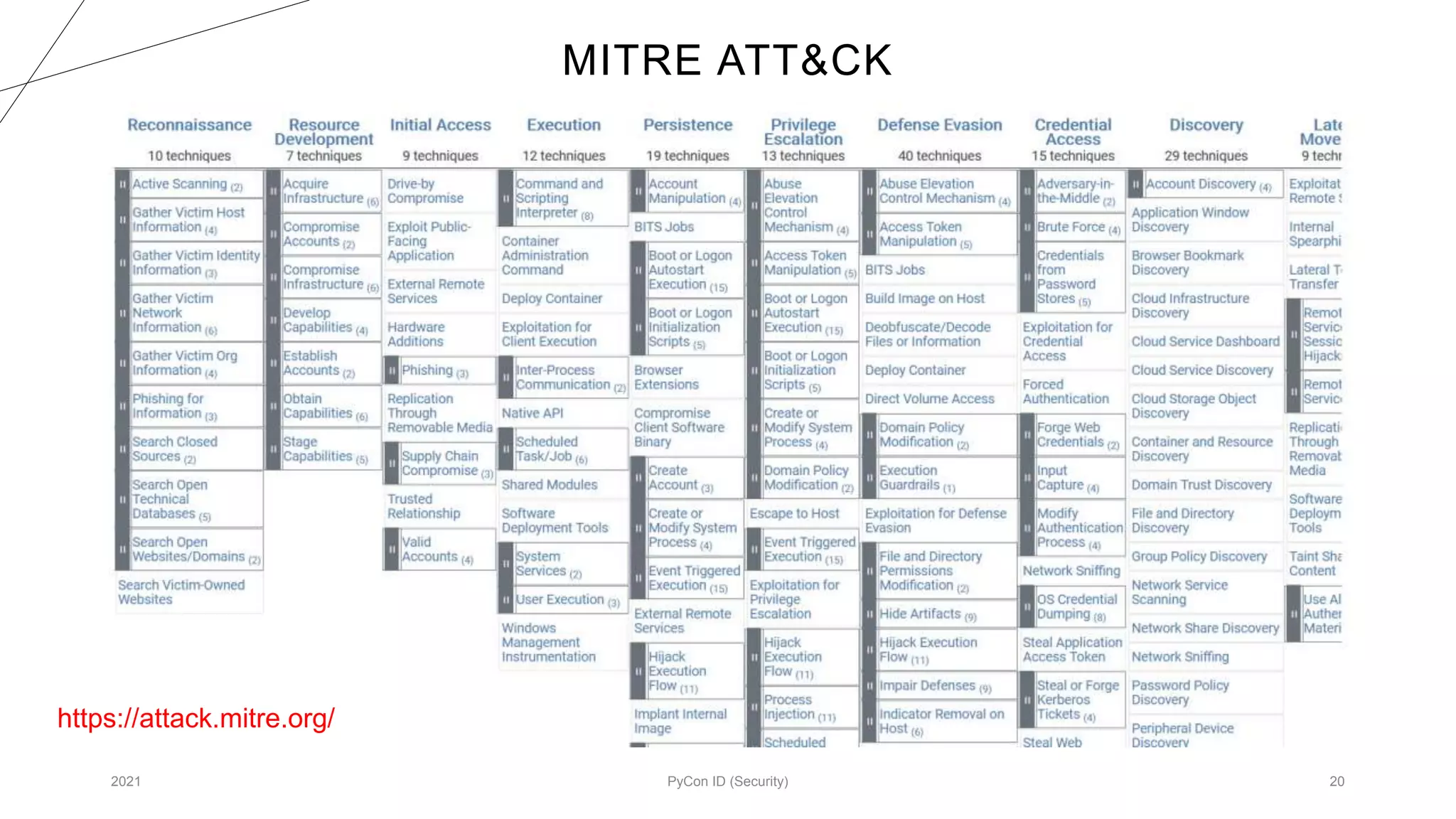
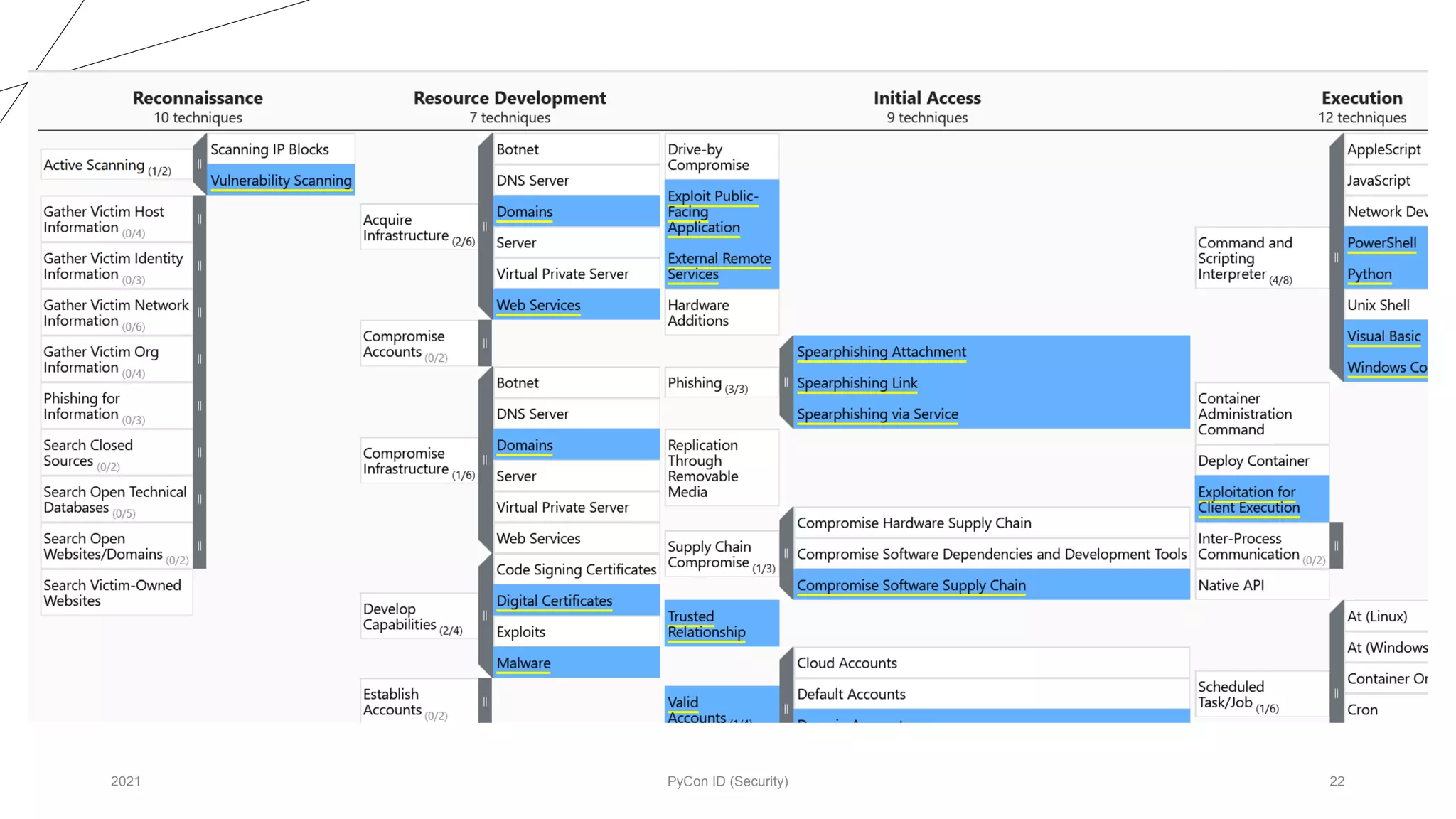
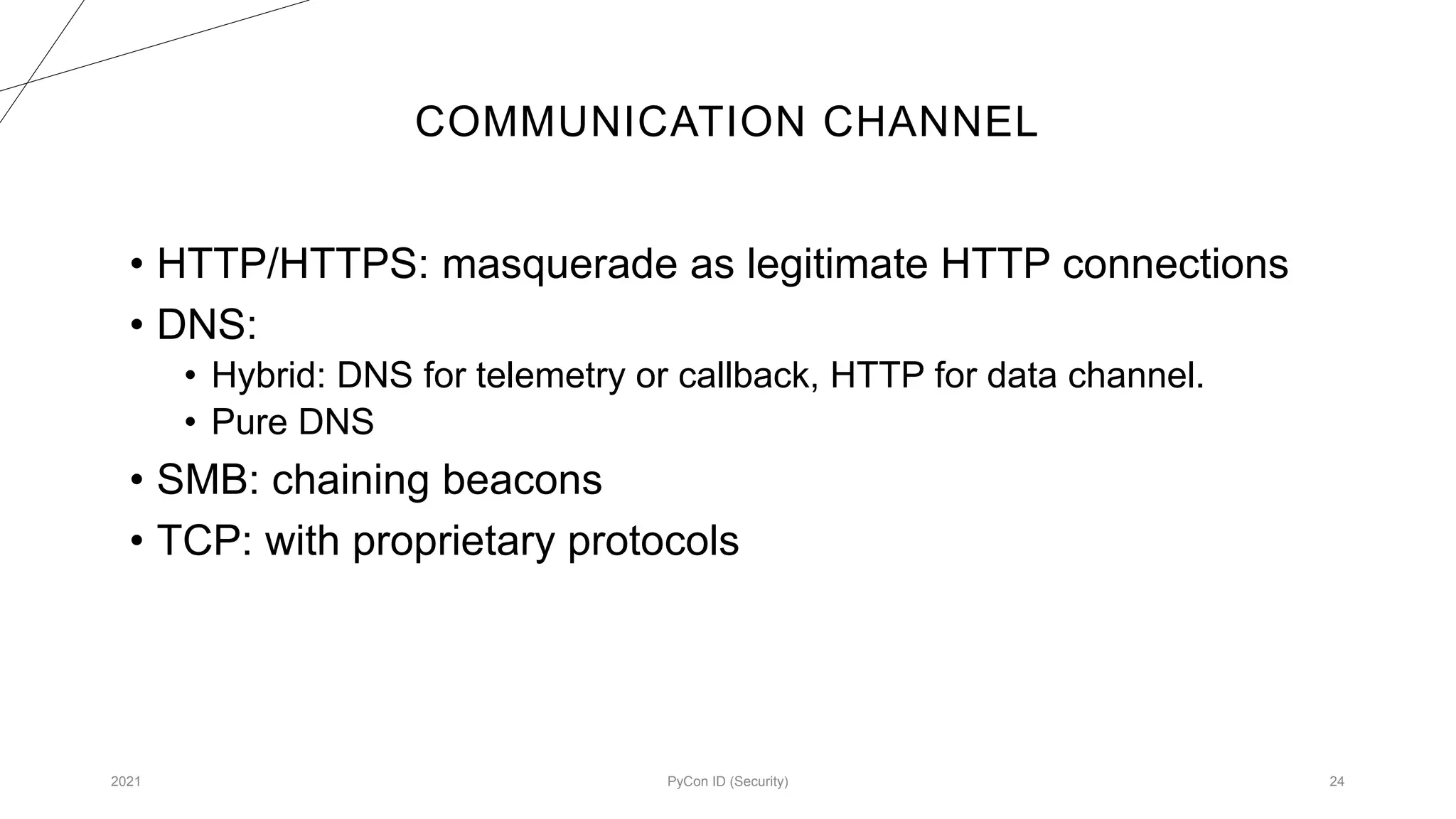
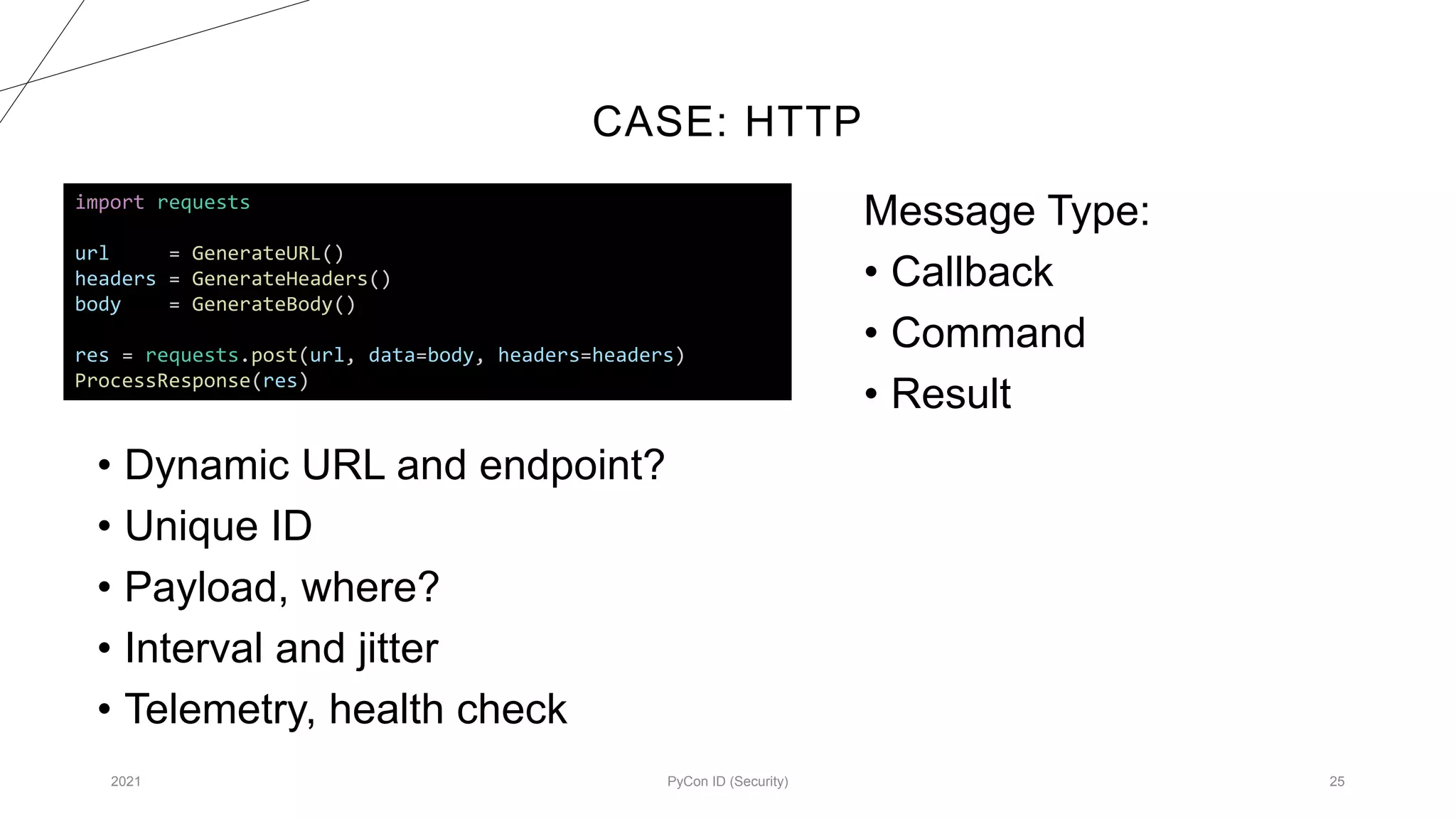
The document discusses methodologies for designing malware focused on red-teaming practices, emphasizing the need for deep system knowledge and penetration skills. It outlines the importance of command and control infrastructure, modular design, and various communication methods for maintaining presence and executing commands within target networks. Various commands and dynamic configurations to enhance malware functionality and operational security standards are also detailed.




















![THANK YOU
Satria Ady Pradana
satria.pradana [at] mii.co.id
@xathrya (telegram)
2021 PyCon ID (Security) 35](https://image.slidesharecdn.com/presentation-211205014558/75/Malware-for-Red-Team-35-2048.jpg)