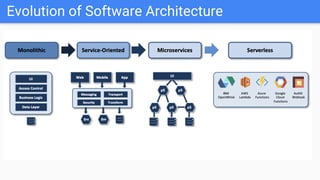
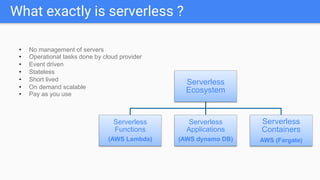
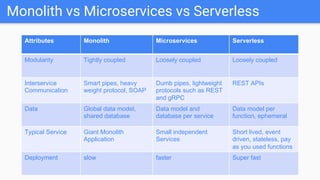
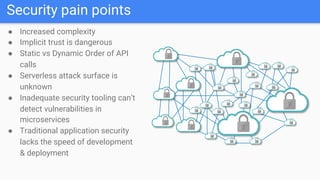
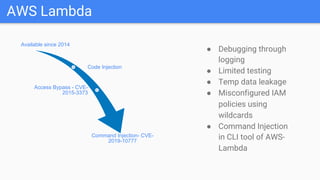
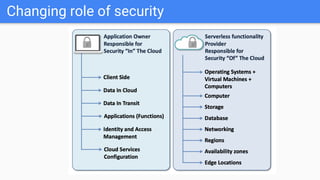
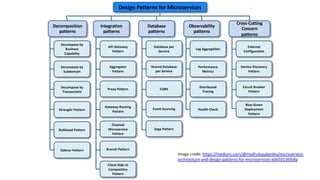
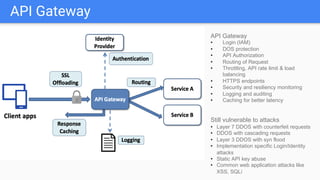
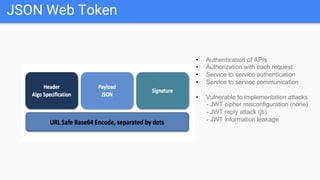
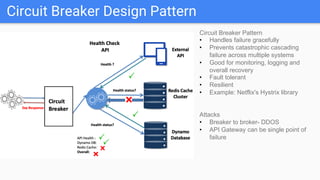
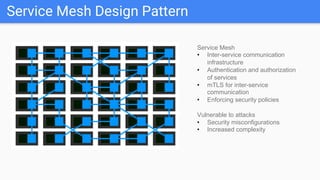
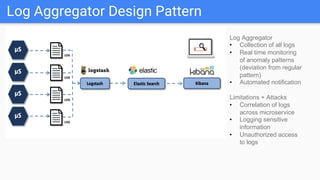
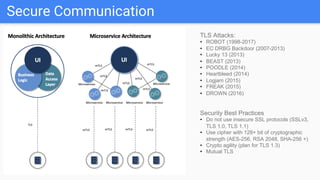
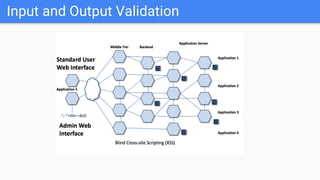
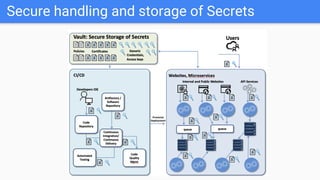
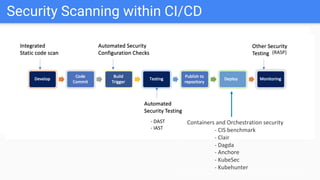
Trupti Shiralkar presented on securing serverless applications and microservices. She began with an overview of serverless architectures and microservices, noting the evolution from monoliths and increased security challenges from complexity and dynamic interactions. She then analyzed common microservices security design patterns like API gateways, JSON web tokens, circuit breakers, service meshes, and log aggregators. Finally, she discussed best practices for securing serverless applications, including zero trust, input/output validation, secret handling, security scanning in CI/CD, and conclusion security testing. The presentation provided context on serverless architectures and microservices before analyzing related security patterns and recommendations.