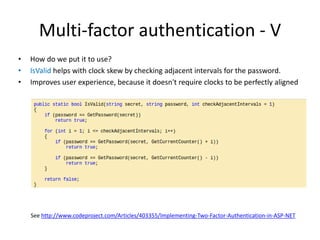
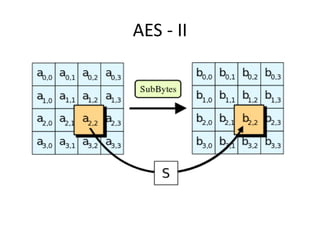
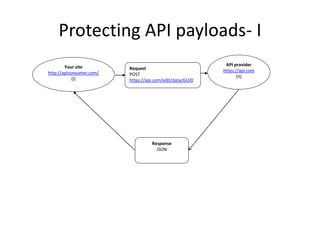
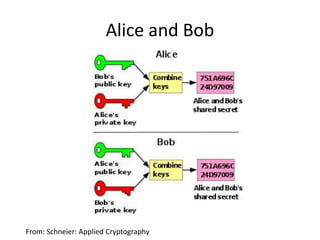
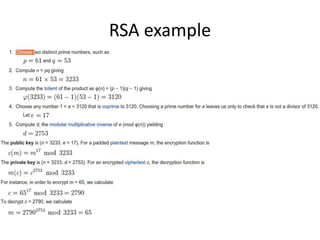
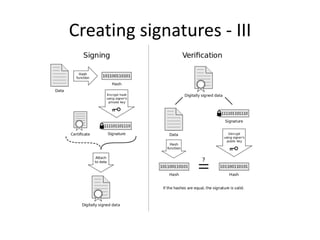
The document outlines a seminar on practical security for programmers, emphasizing topics such as access control, least privilege enforcement, cryptography, and security attacks. Key concepts include multi-factor authentication, password management, and the principles of symmetric and asymmetric encryption. The seminar aims to prepare participants for identifying and mitigating security vulnerabilities in software design and implementation.