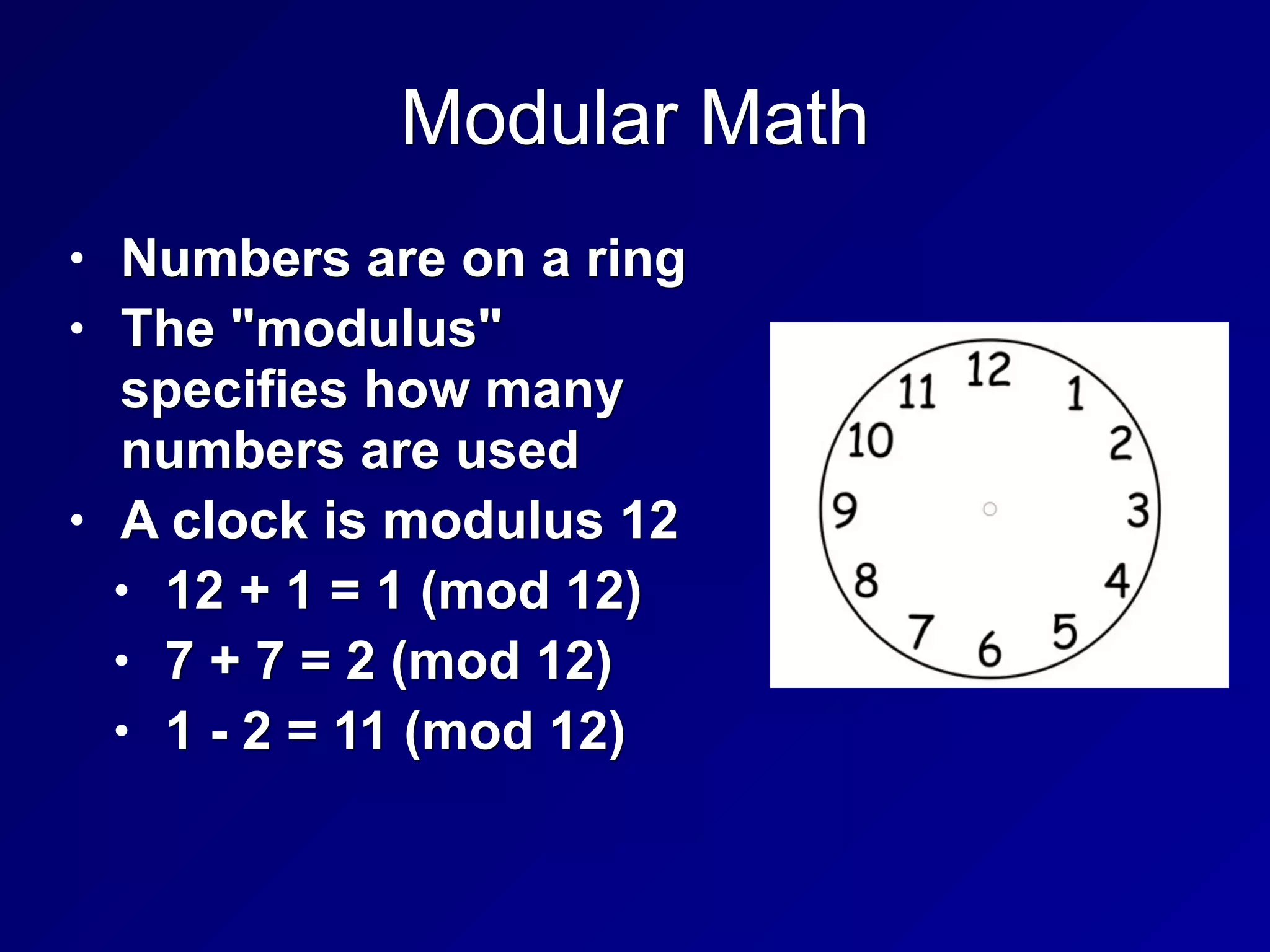
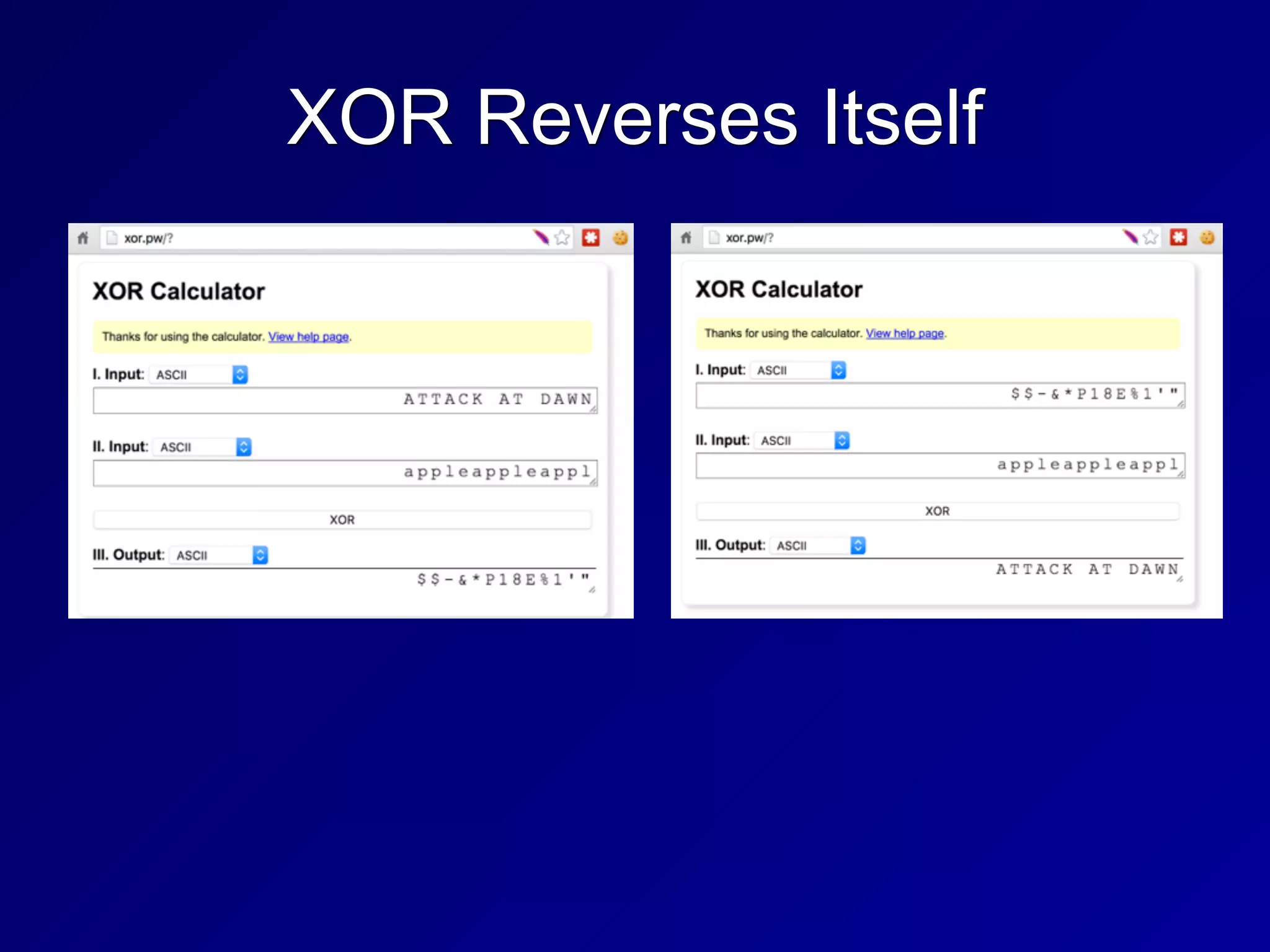
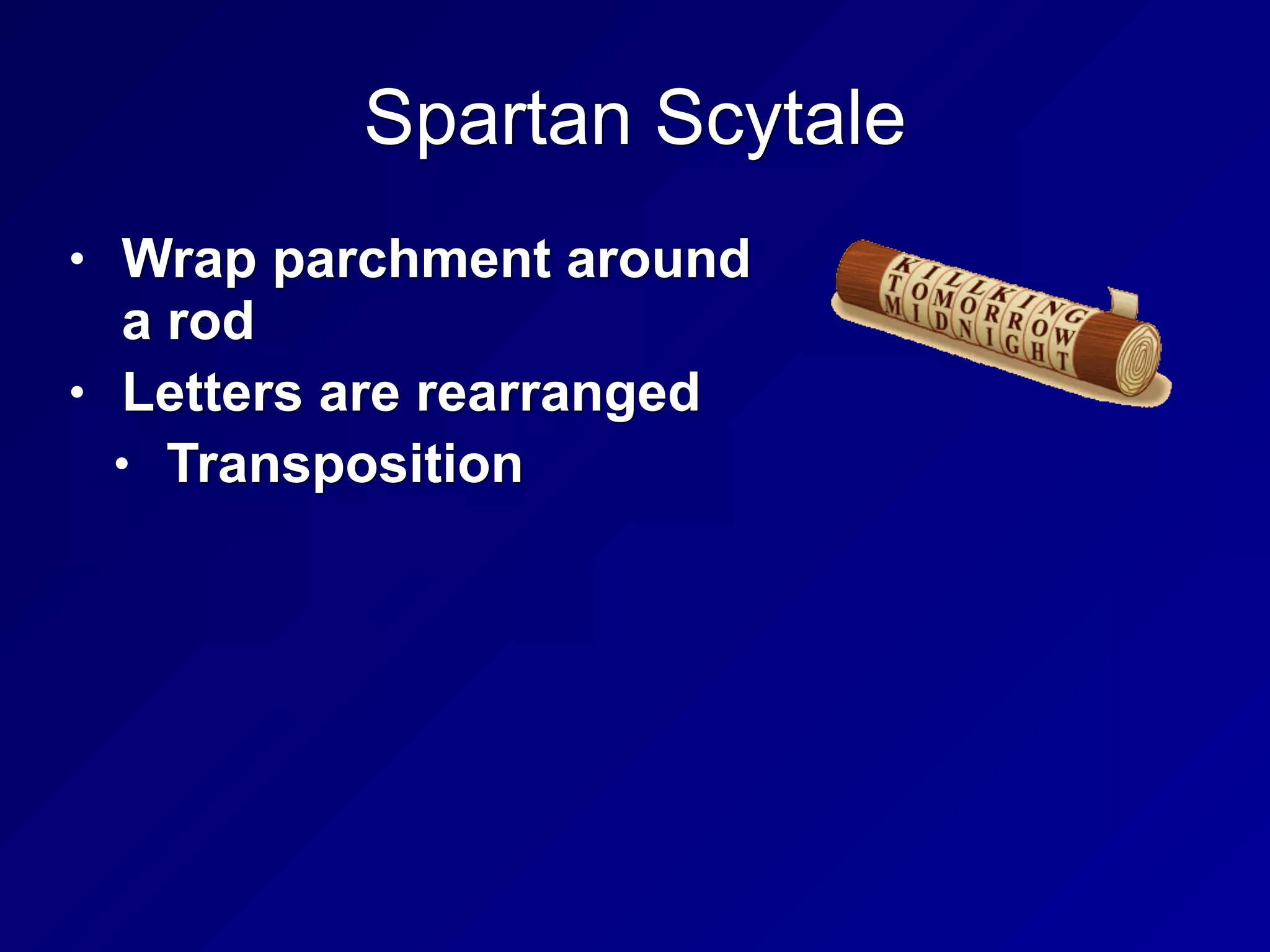
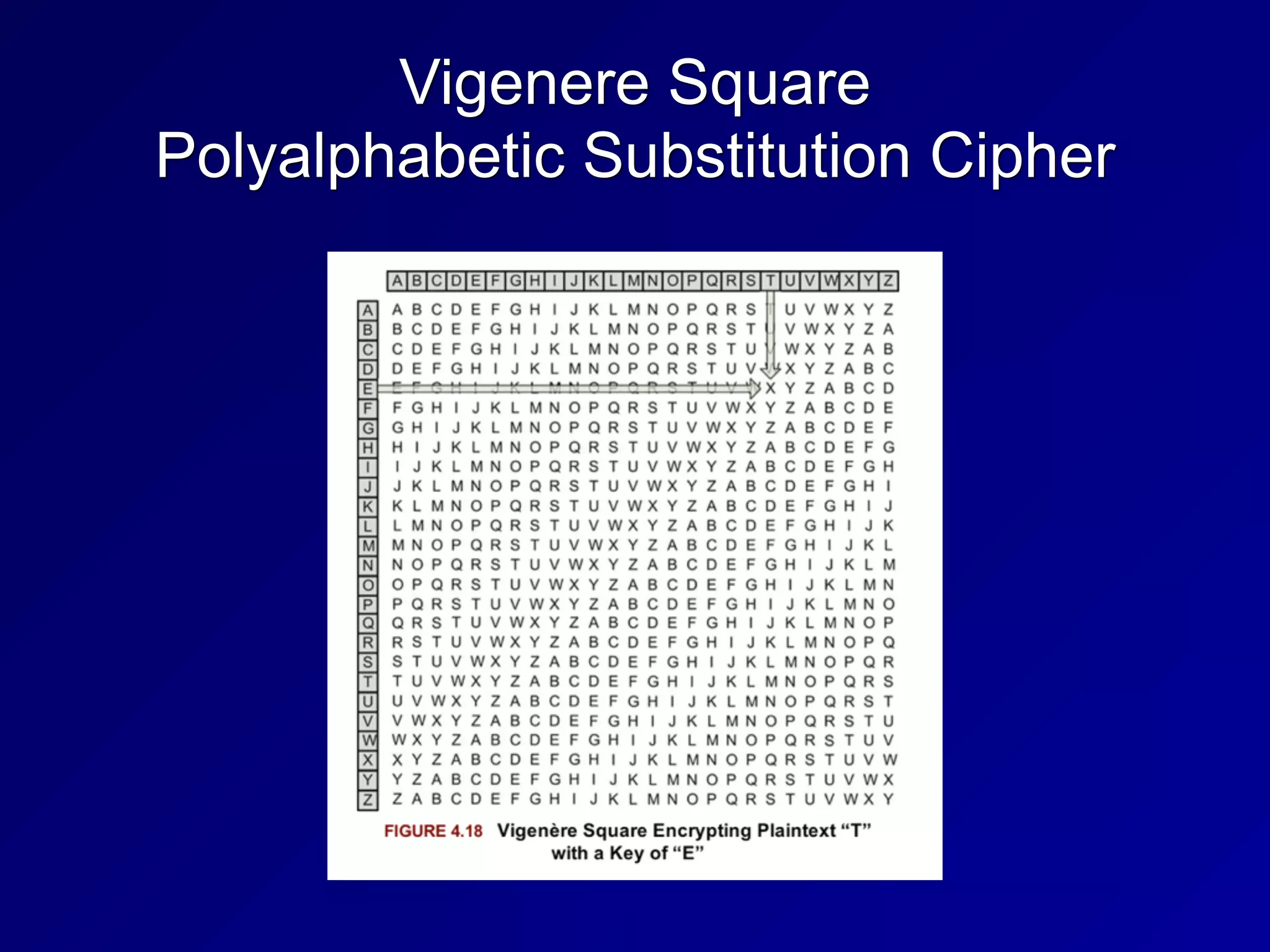
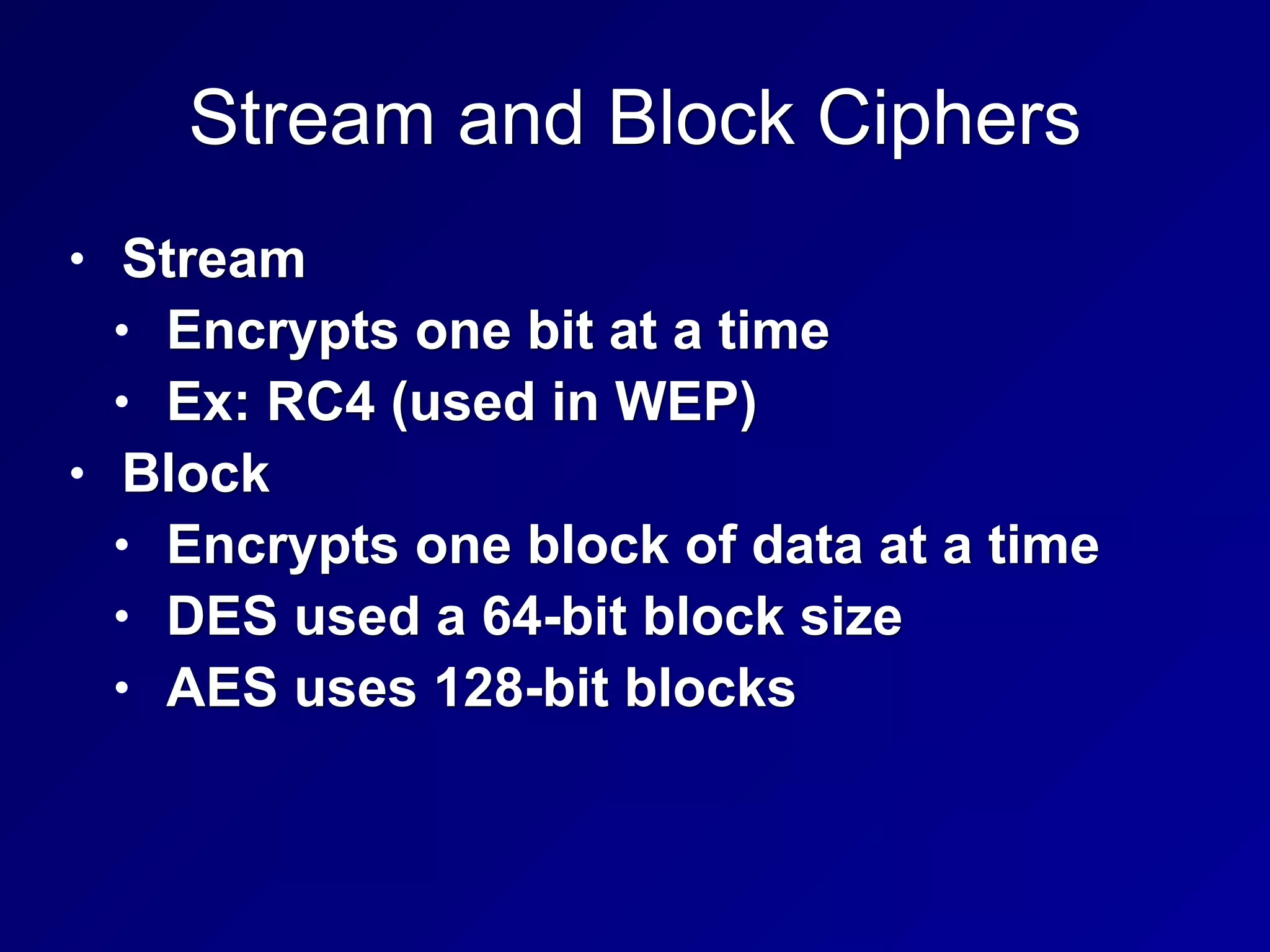
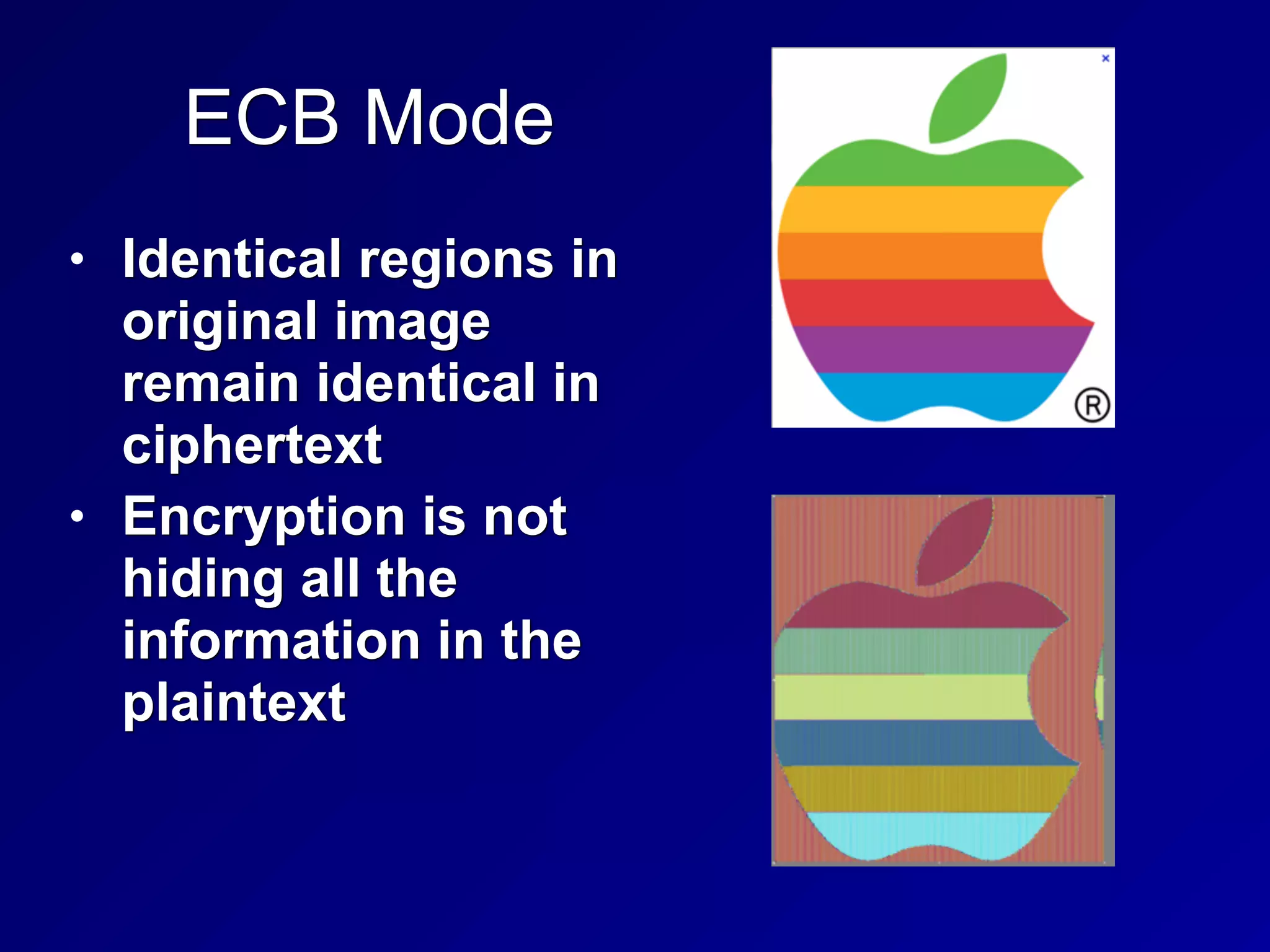
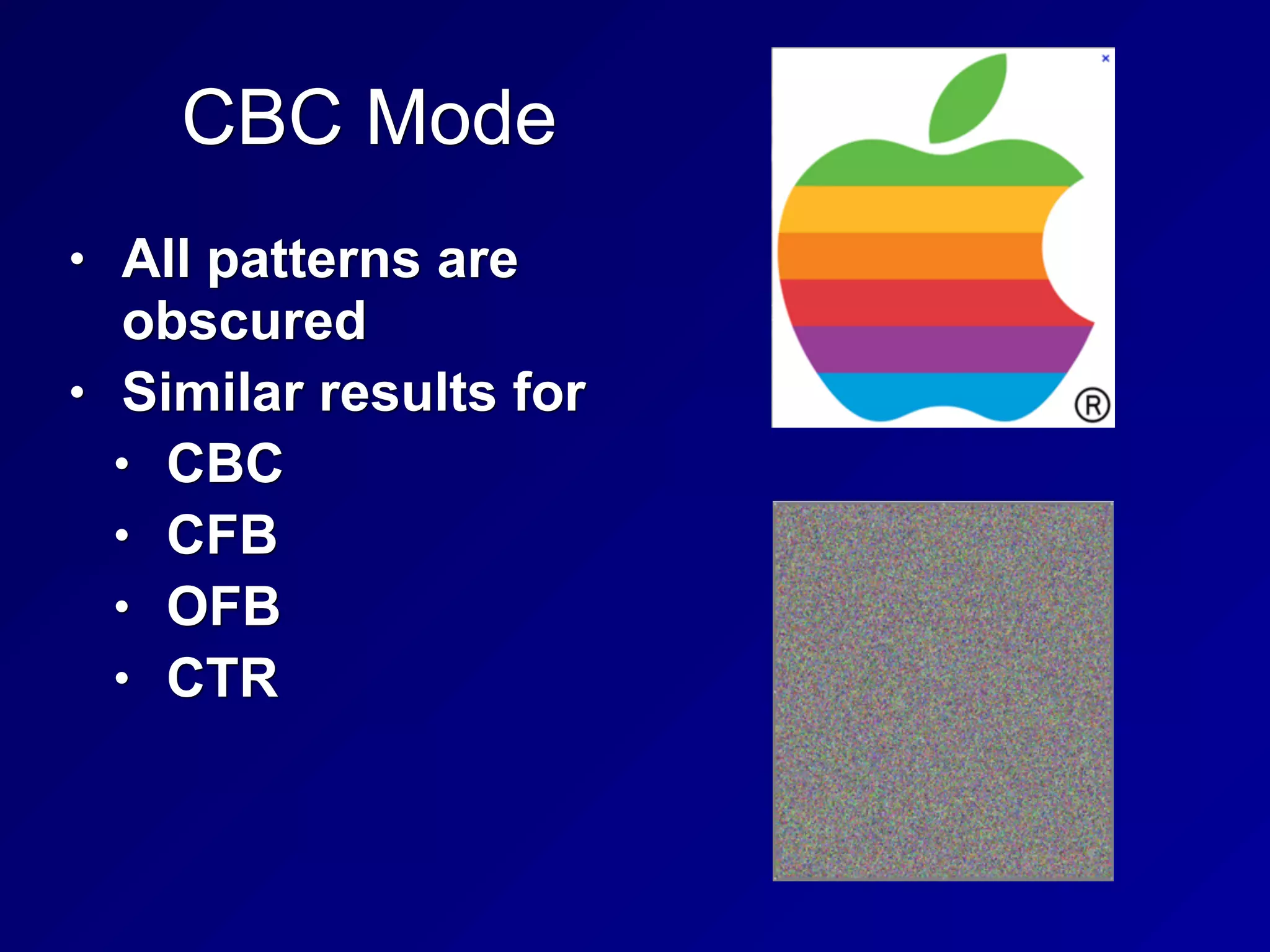
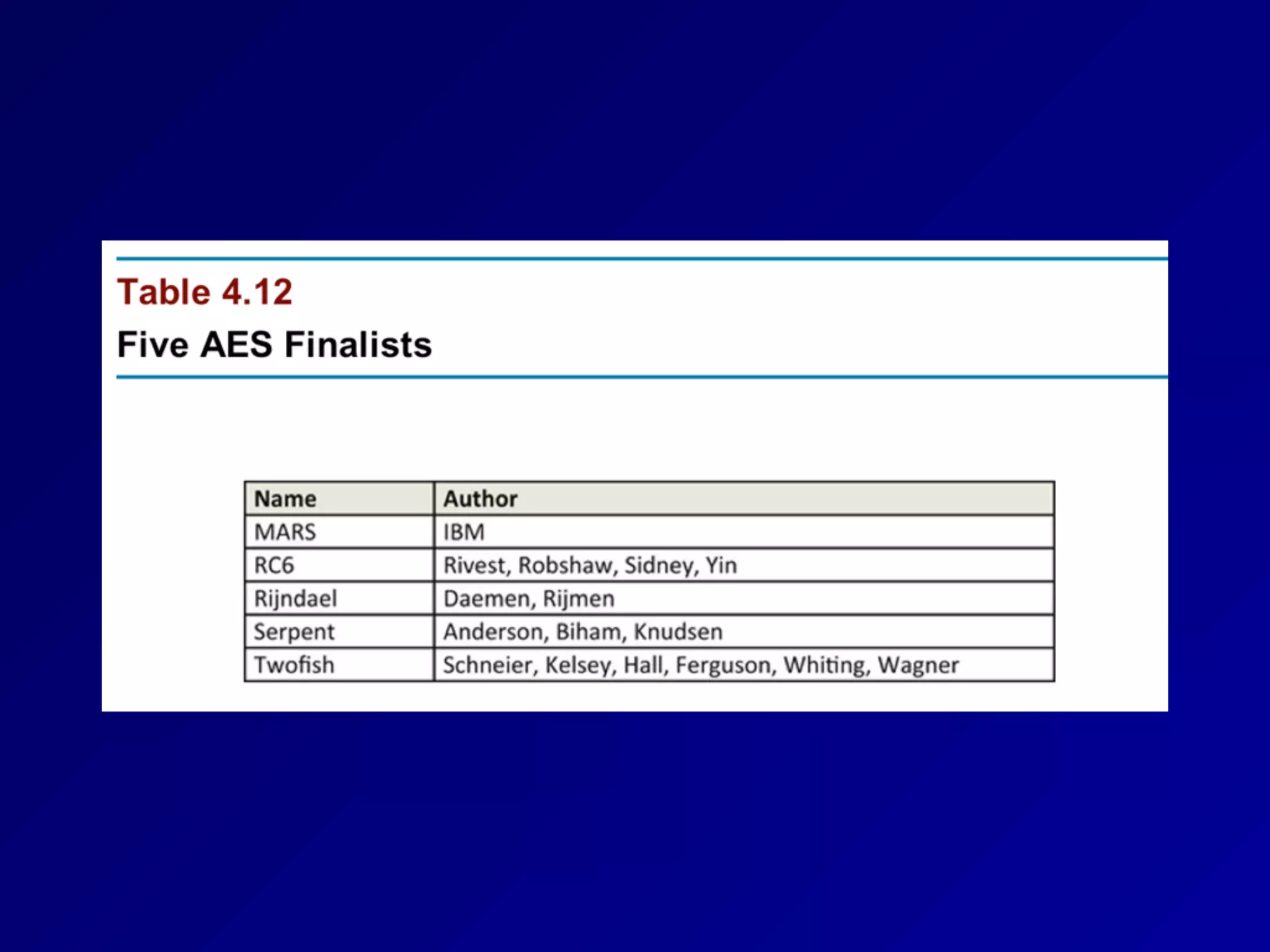
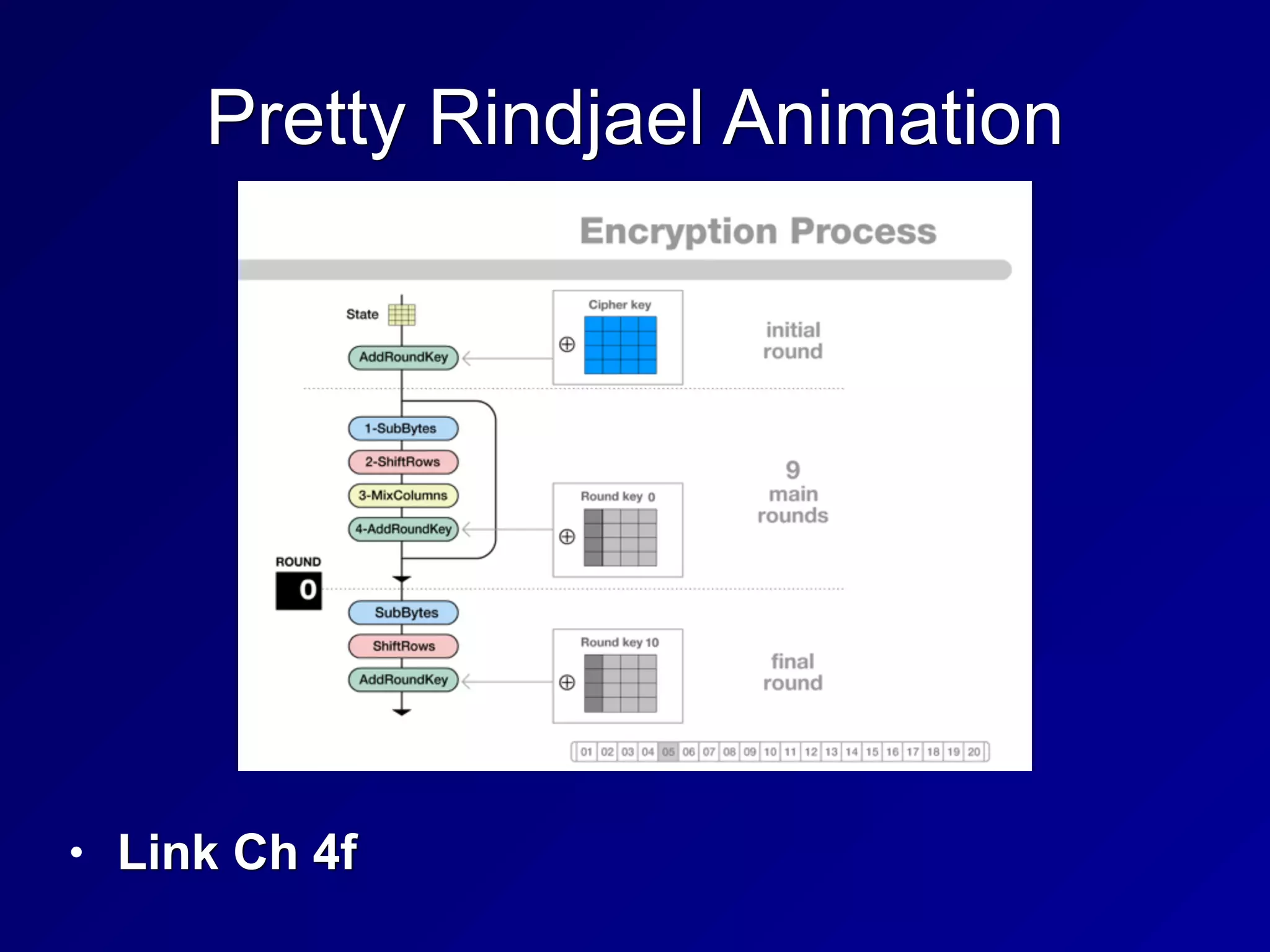
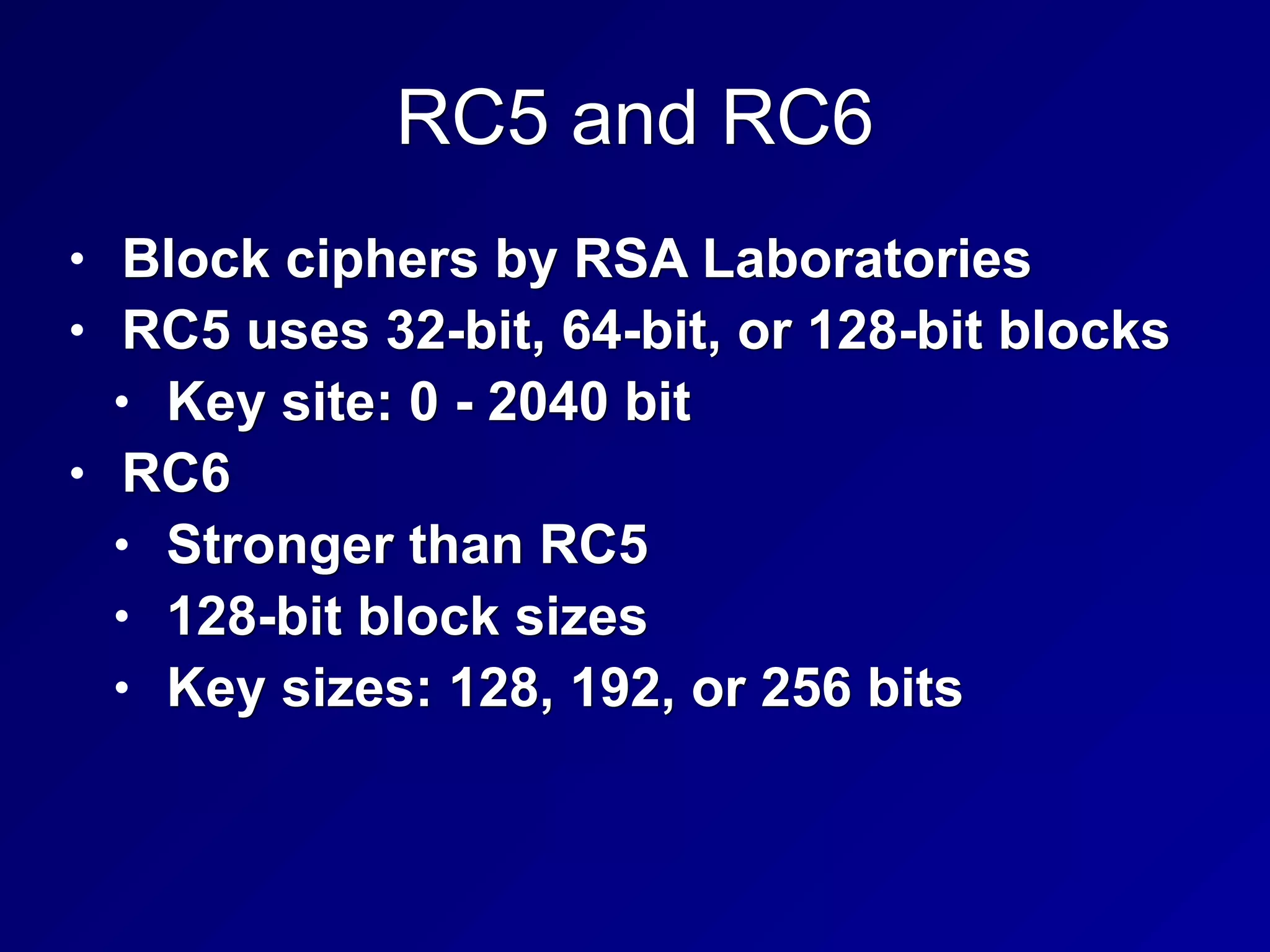
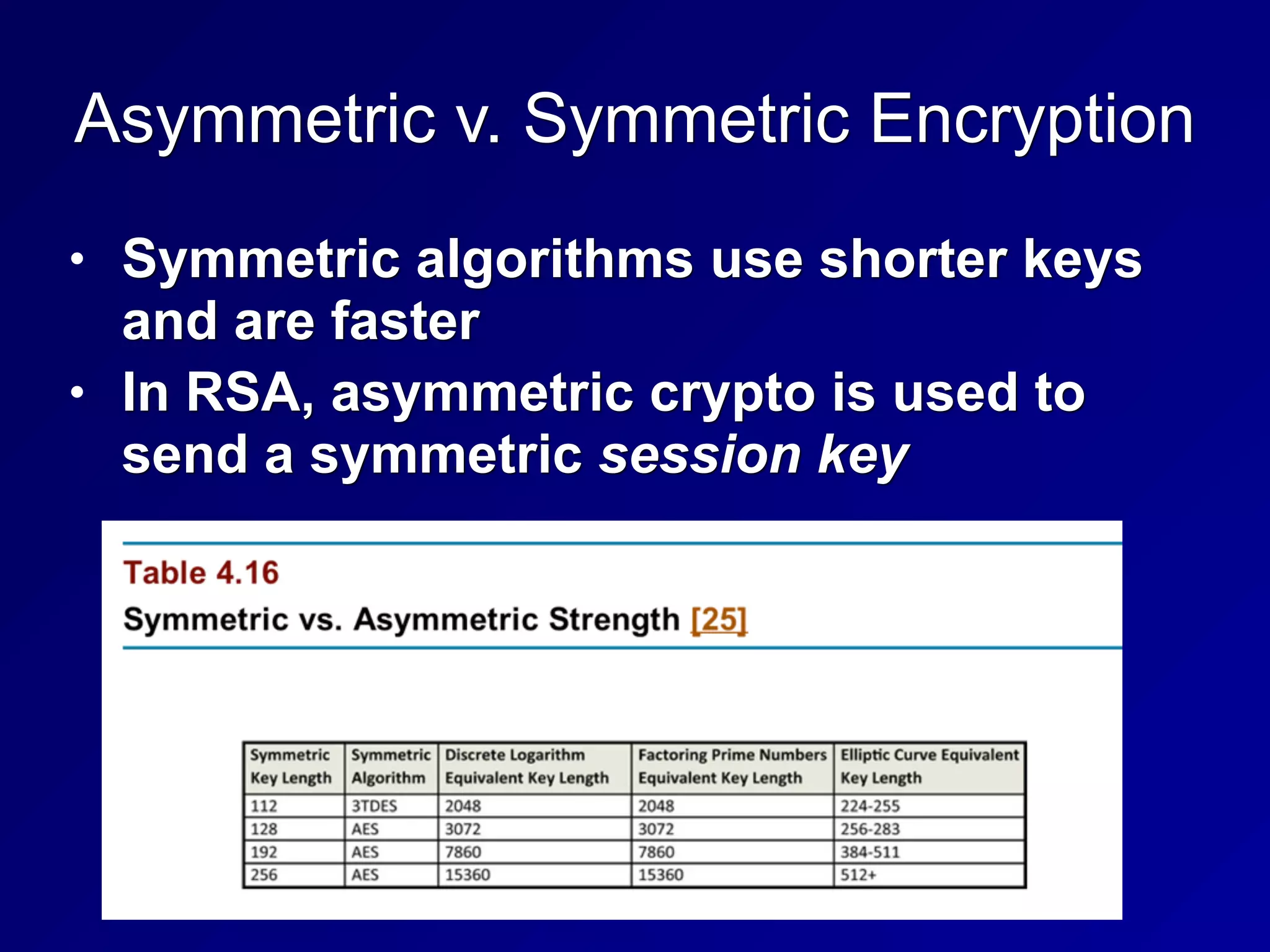
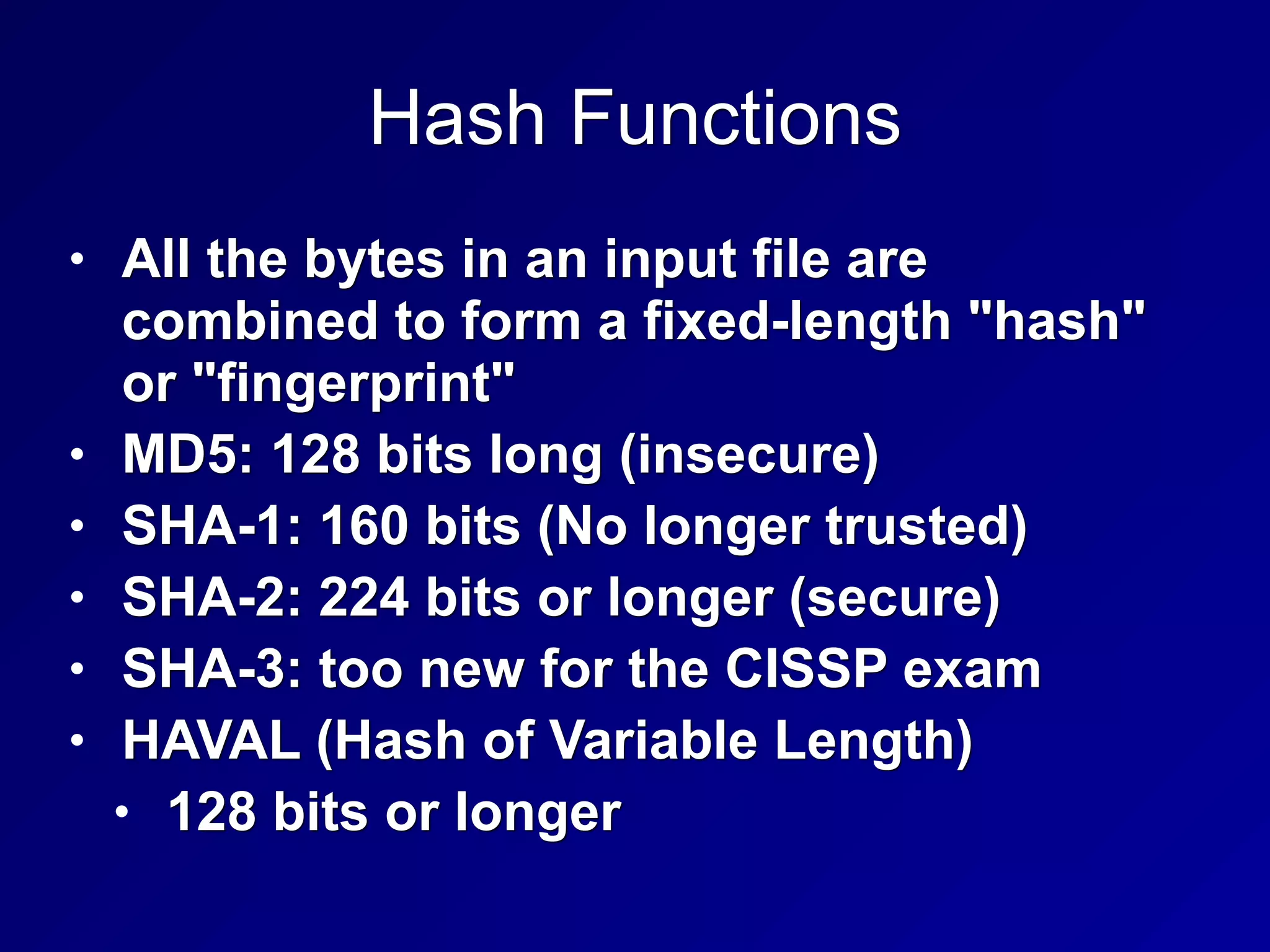
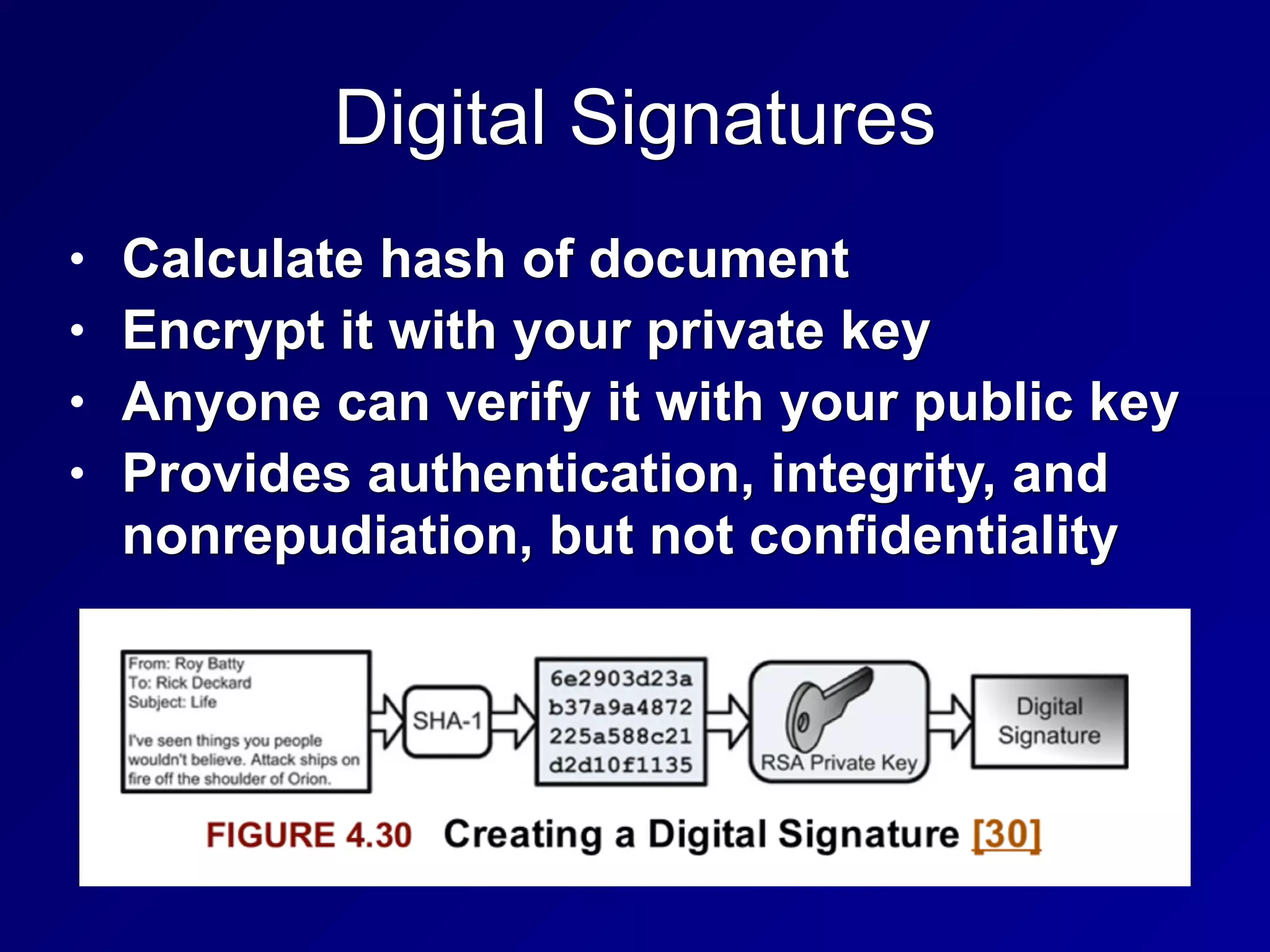
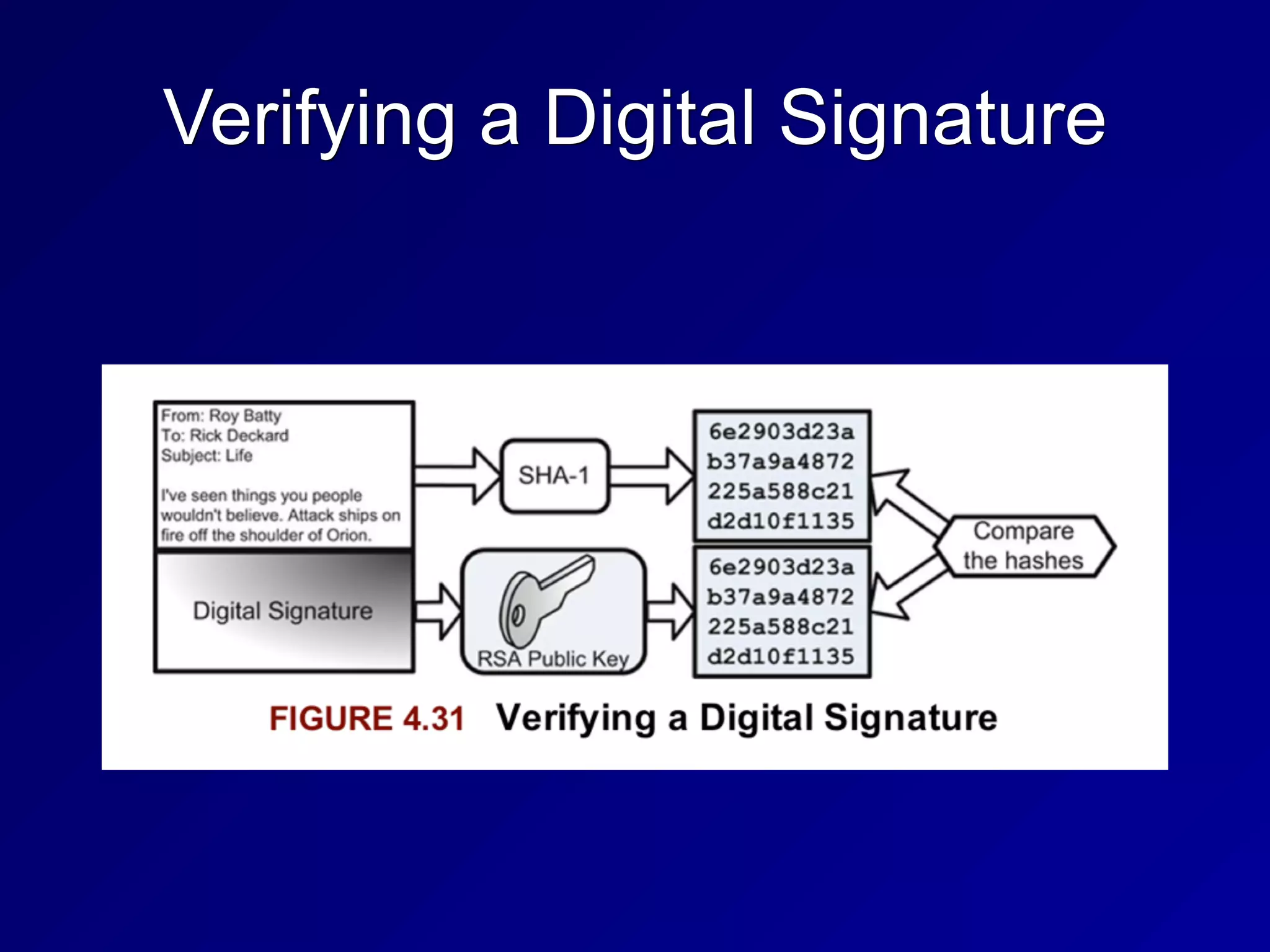
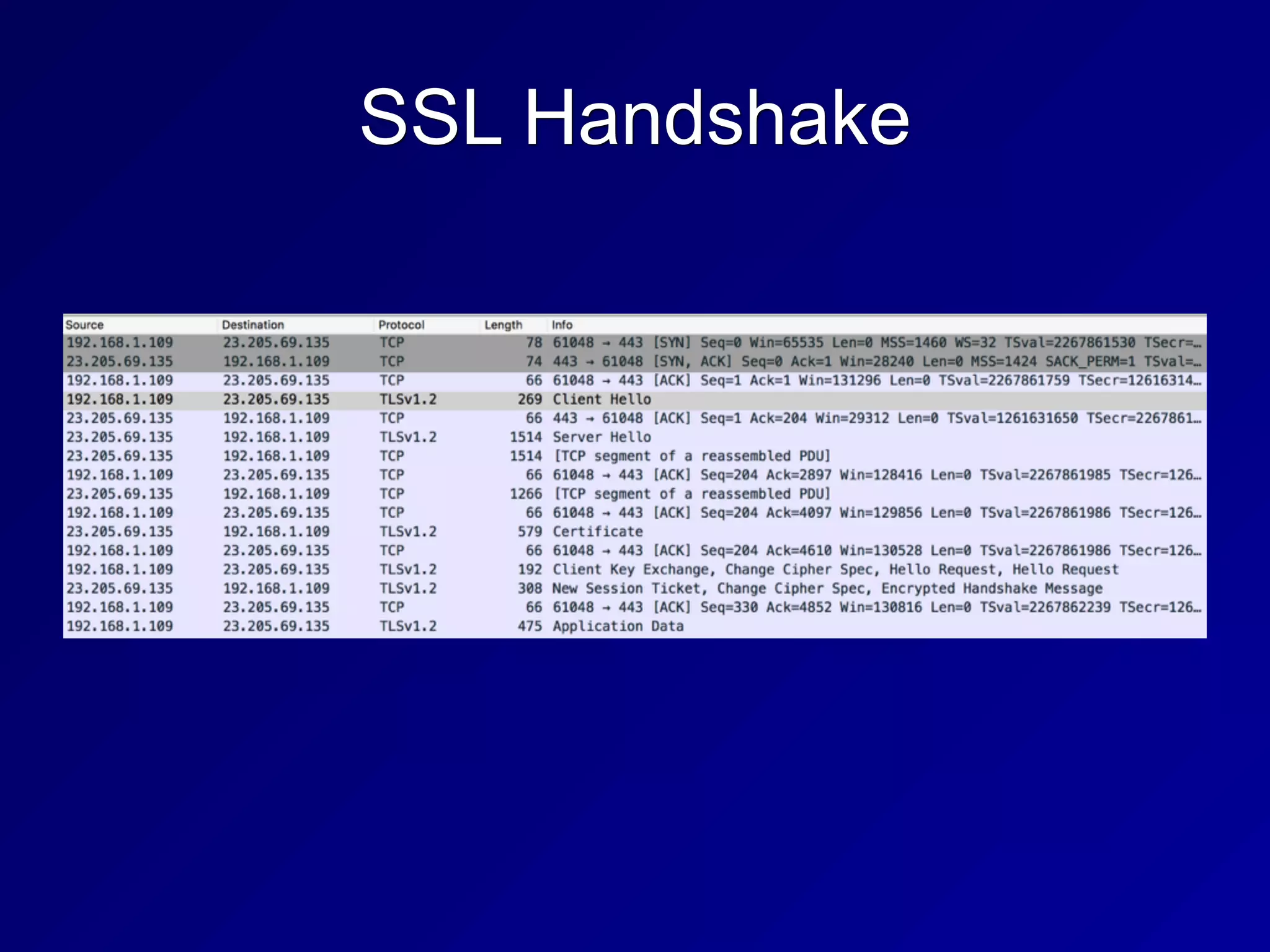
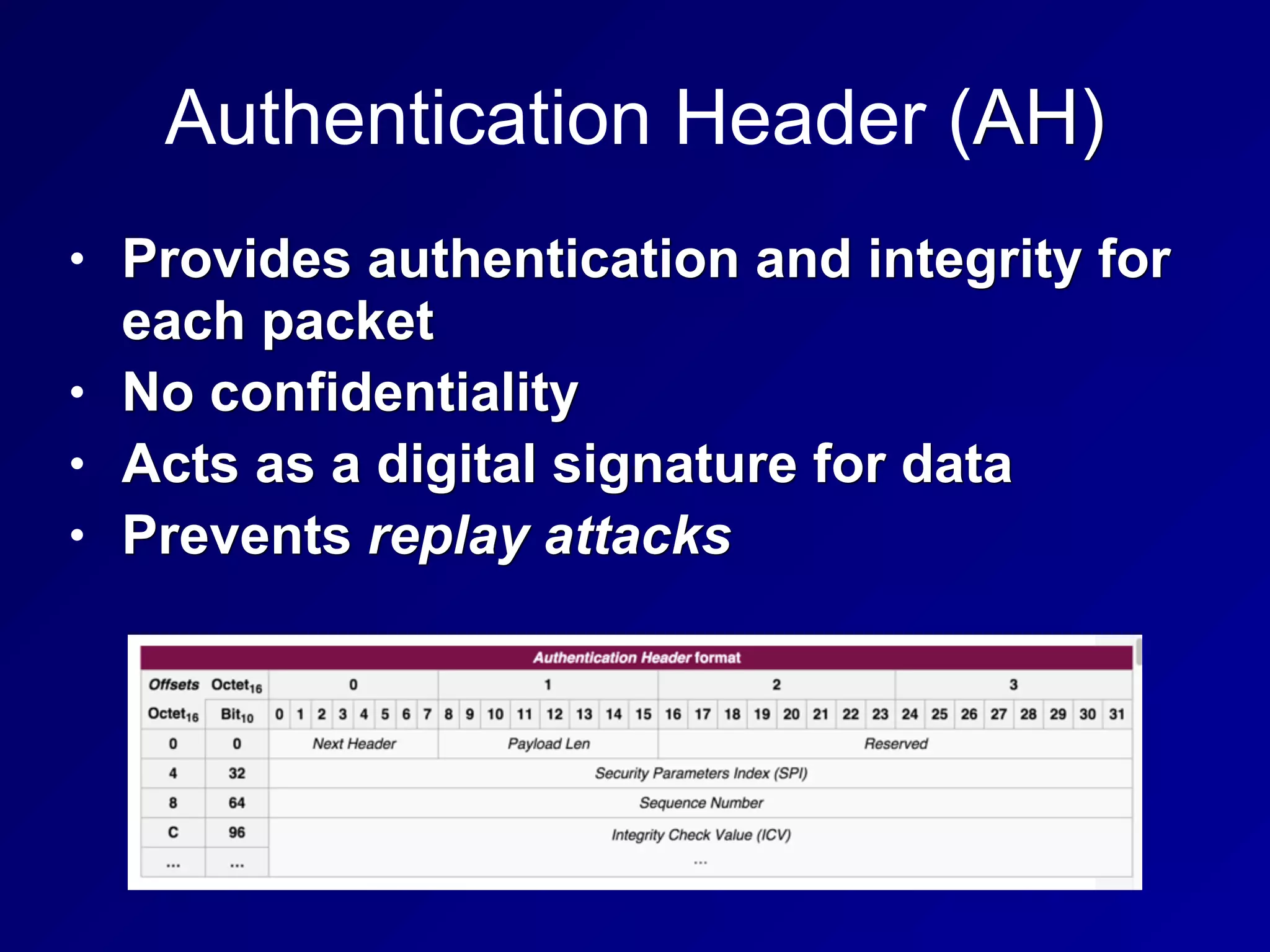
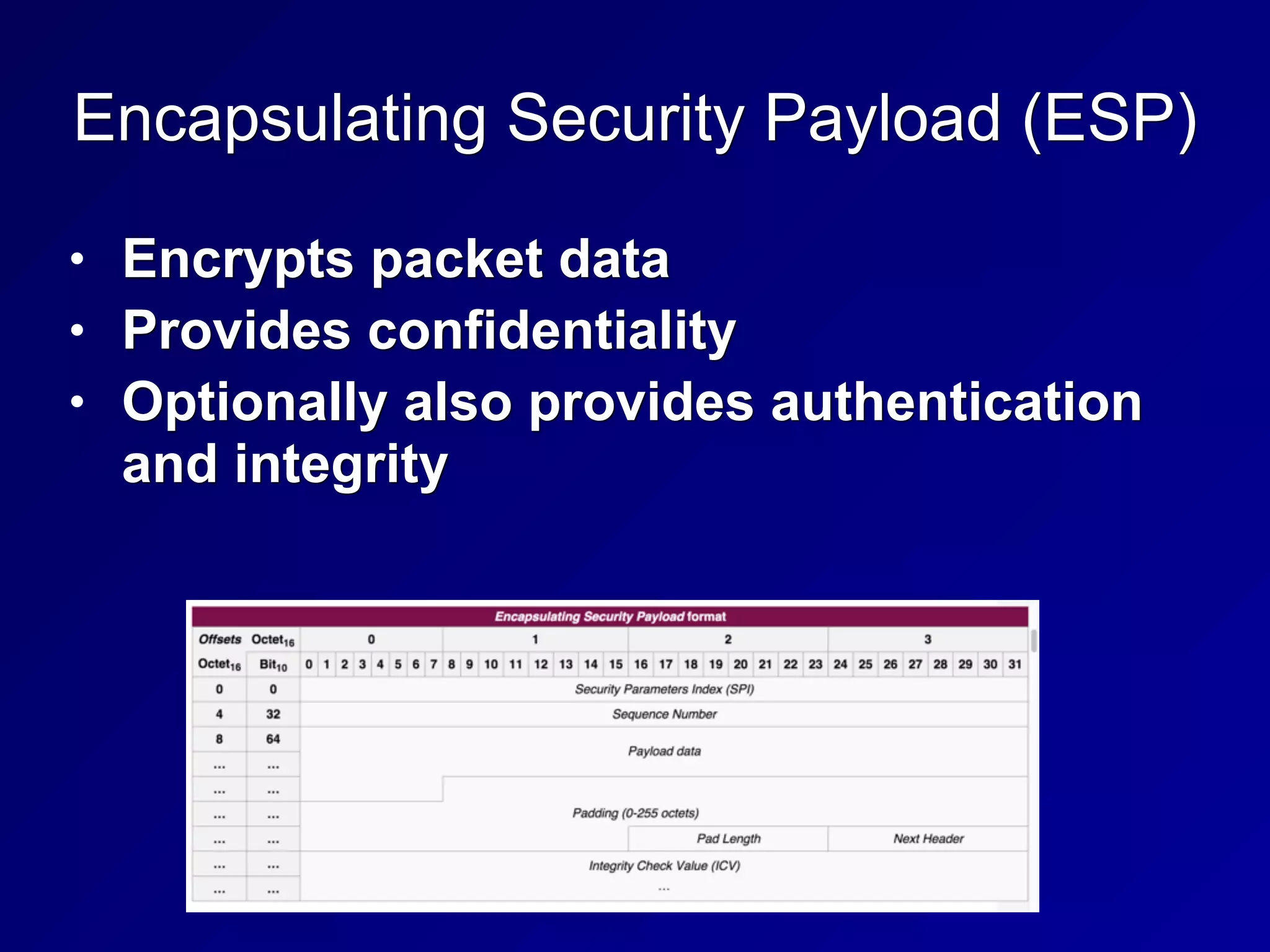
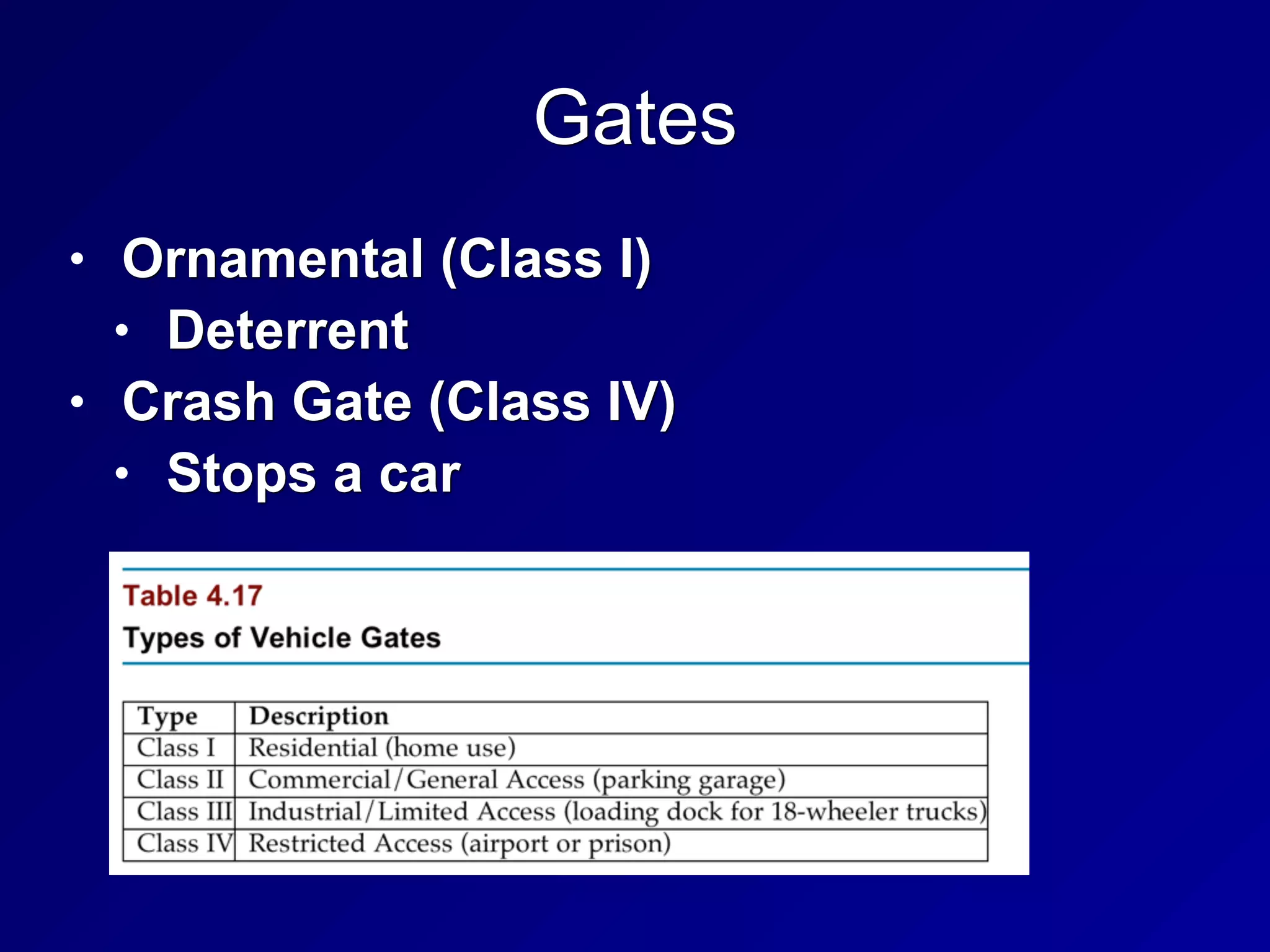
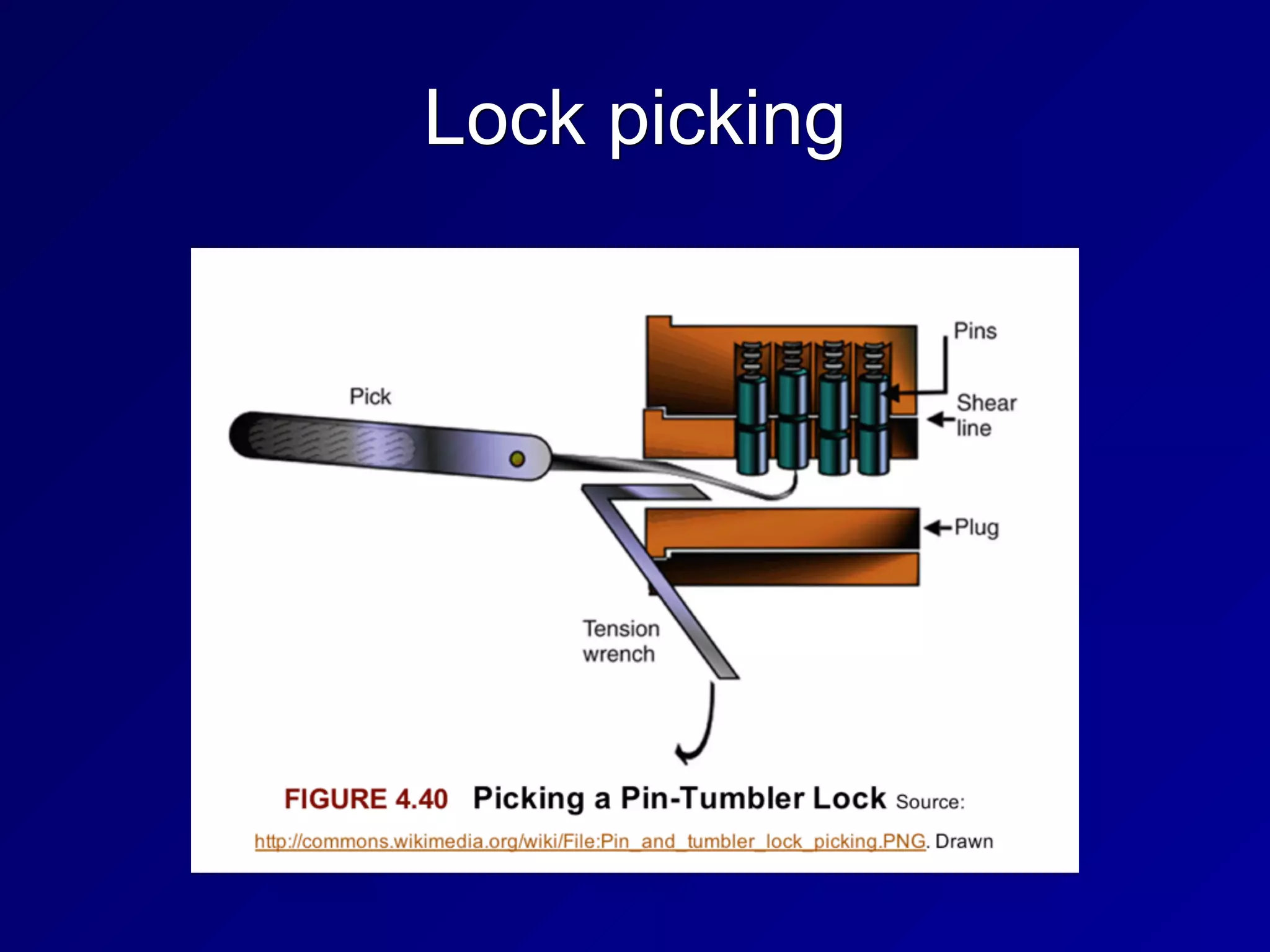
The document covers key concepts in information security, particularly focusing on cryptographic principles and practices. It discusses various encryption methods, types of cryptography, cryptographic attacks, and essential protocols like SSL/TLS, emphasizing the importance of key management and secure communication. Additionally, the text outlines protective measures in physical security and perimeter defenses to safeguard sensitive information.