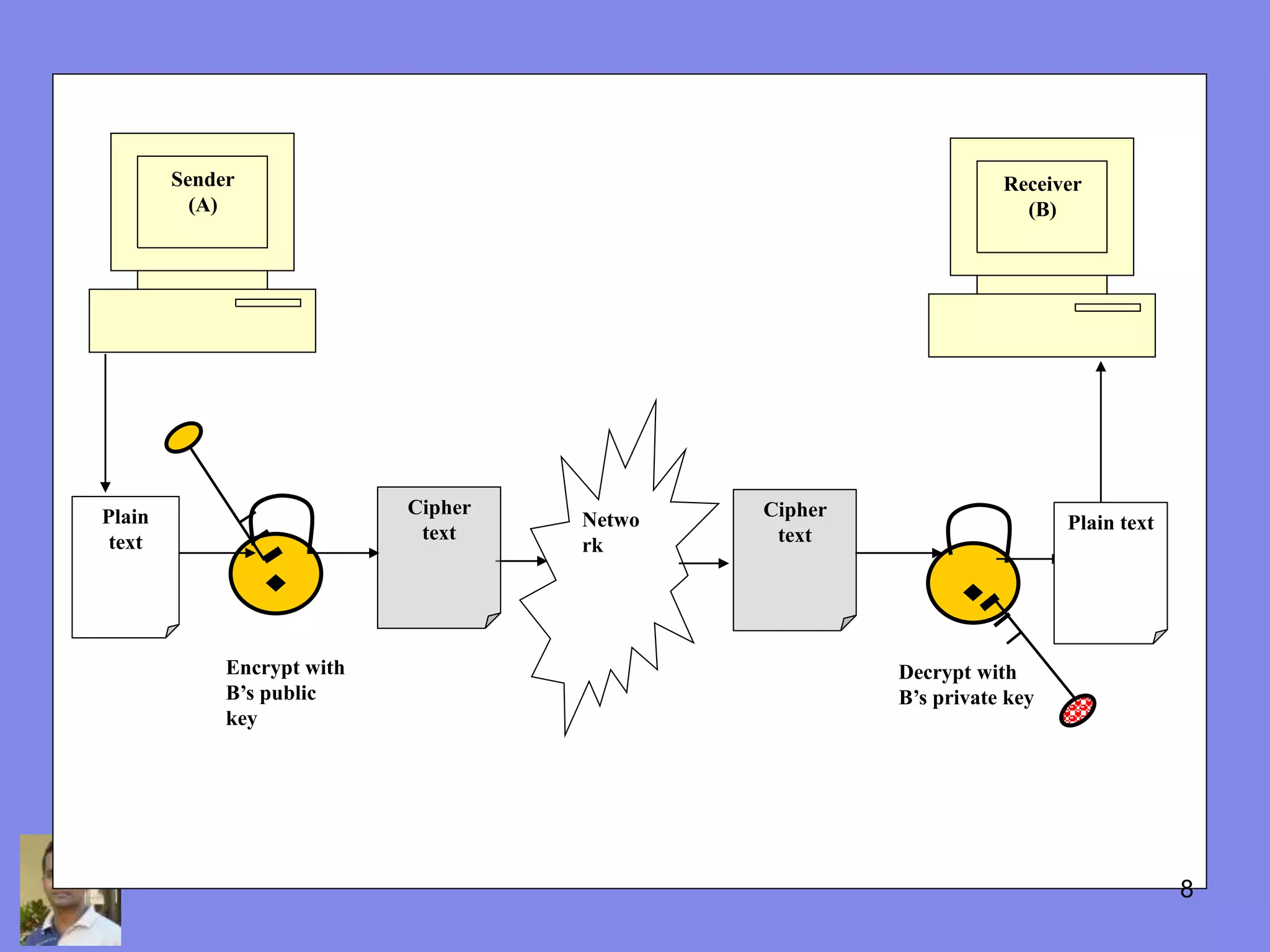
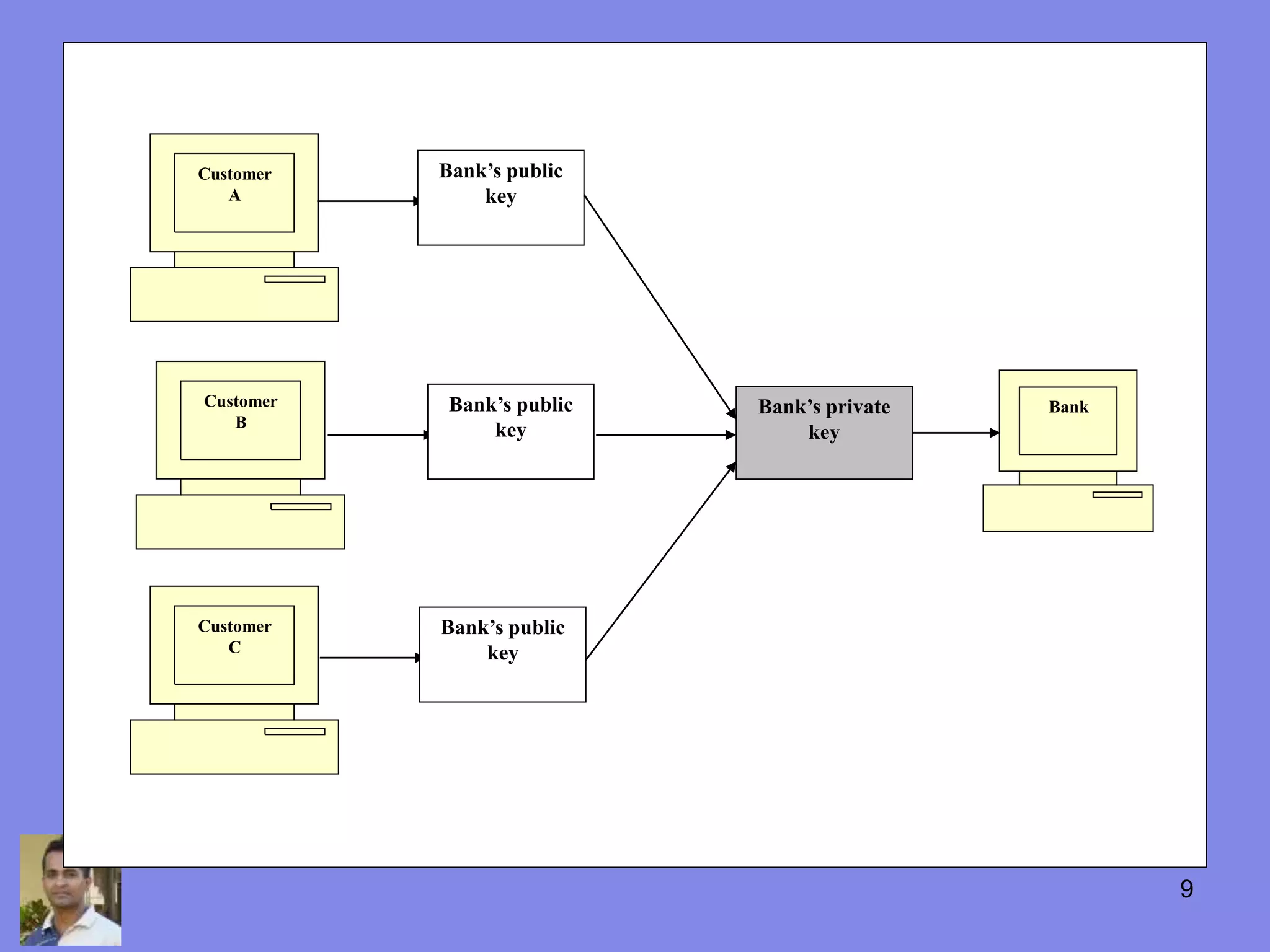
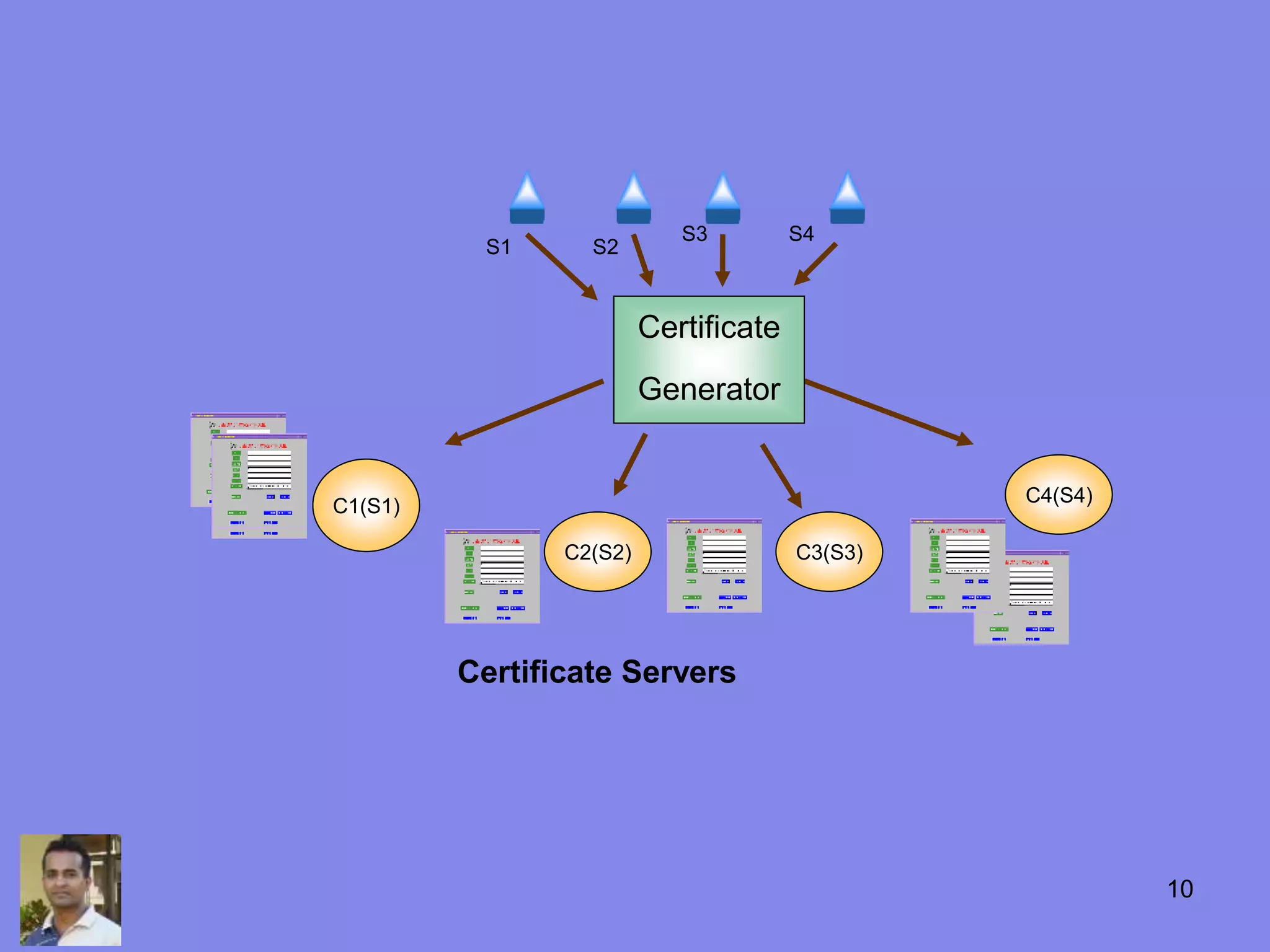
This document discusses the history and uses of cryptography and digital certificates. It provides an overview of how public key infrastructure (PKI) uses public and private key pairs to securely exchange information over networks. A certification authority (CA) is responsible for issuing digital certificates which contain a public key and verify identity. PKI and digital certificates are used for applications like encryption, digital signatures, authentication, and secure communication protocols.