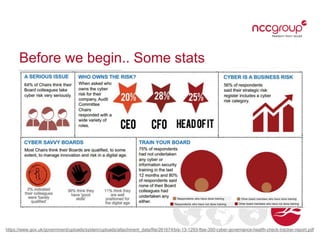
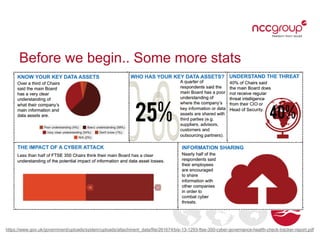
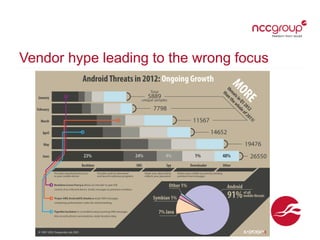
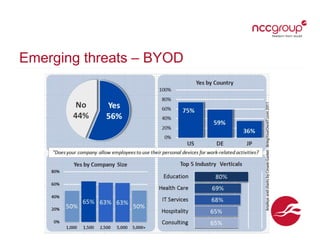
The document outlines current and emerging cyber security threats. It discusses threat actors, primary threats like poor software design and lack of network security, and common attack vectors. Current threats include accidental data loss, deliberate exfiltration, and targeted attacks. Emerging threats involve issues from bring your own device (BYOD) use, large data volumes, fast-paced technology evolution, and increased consumer coding and internet of things devices. The document emphasizes that perimeter security is not enough and that cyber risk responsibility cannot be outsourced.