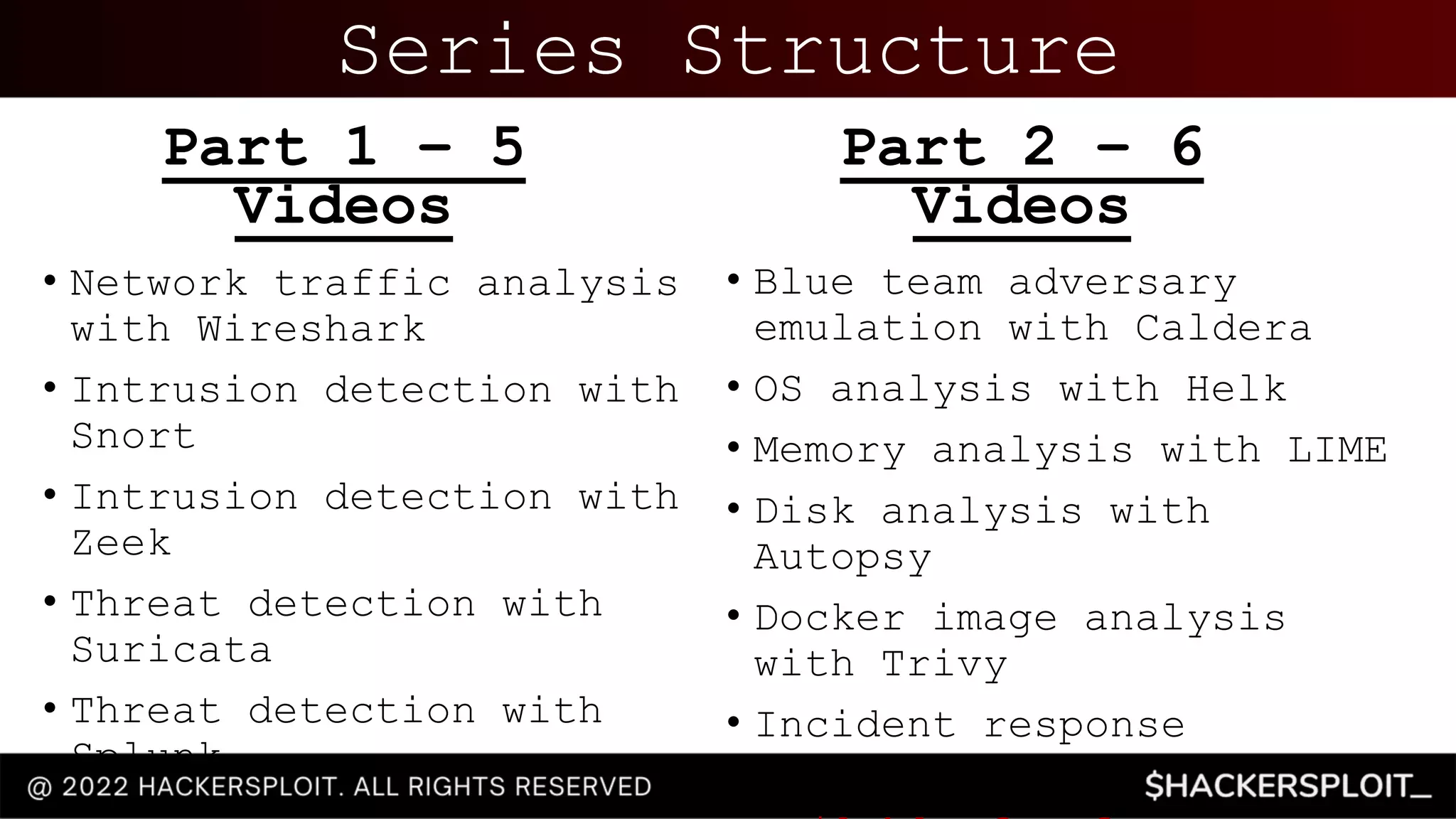
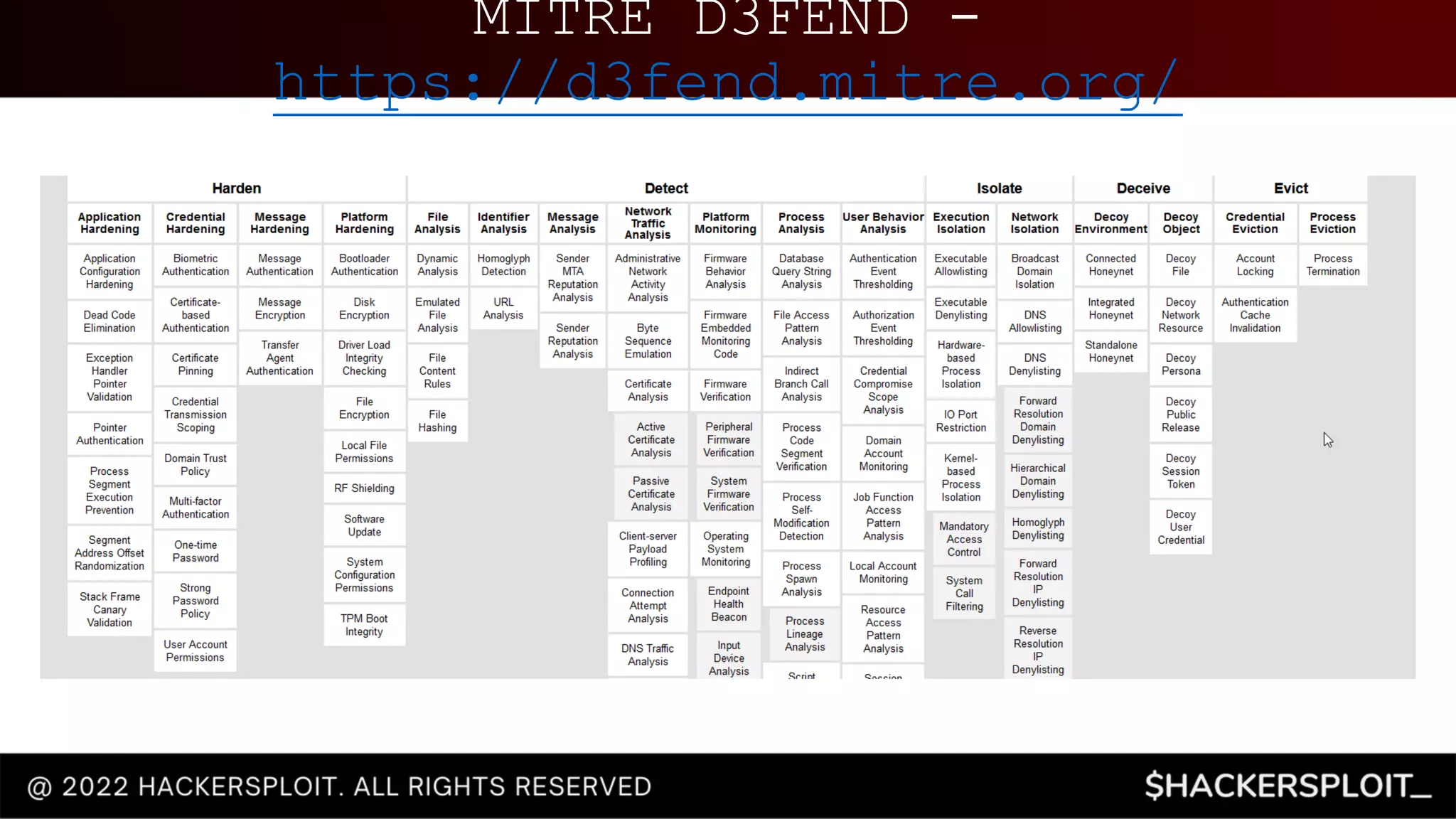
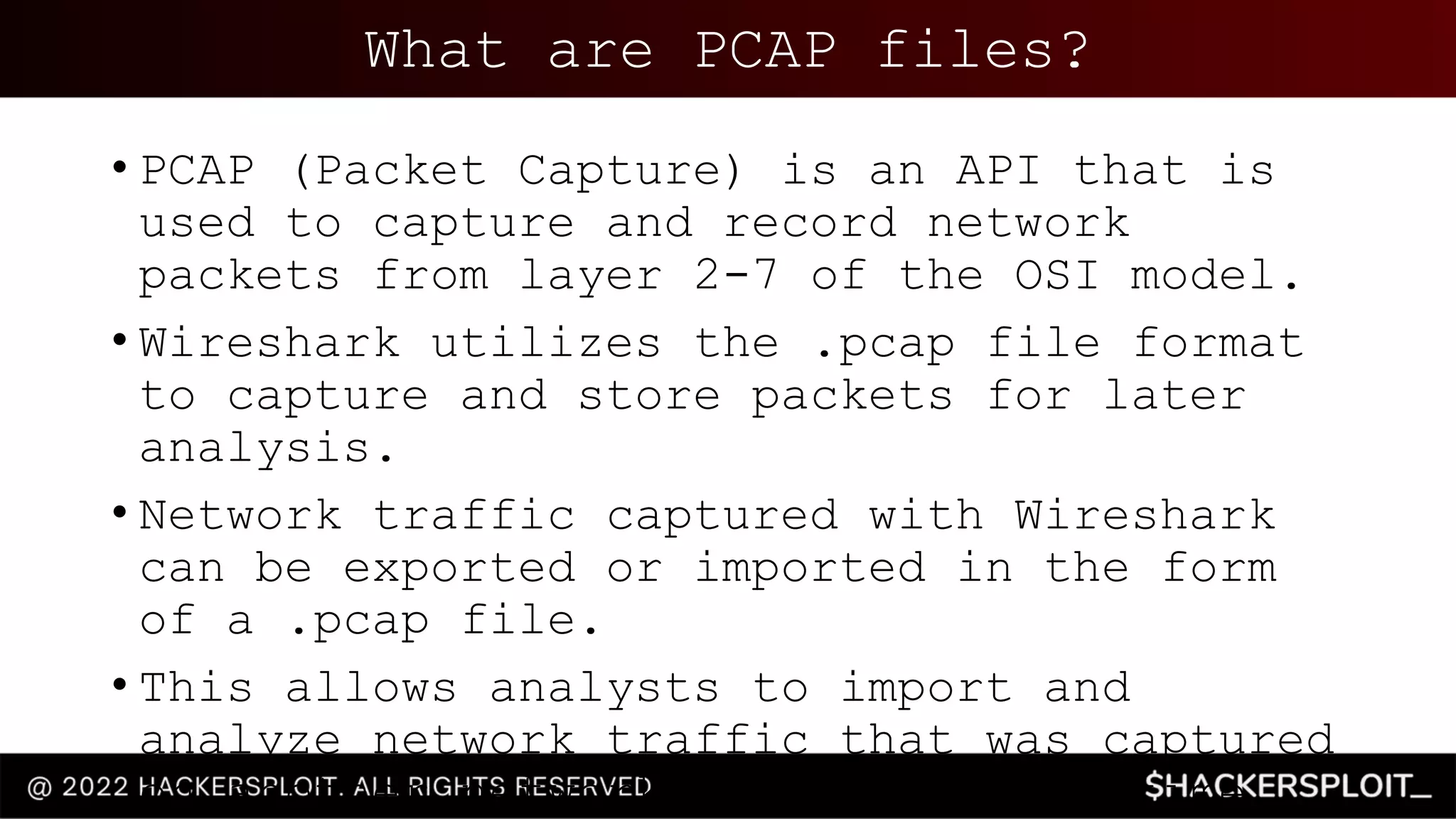
This document provides an introductory guide to blue team operations and security. It outlines a free training series on blue team techniques that is sponsored by Linode, a cloud hosting company. The series consists of 11 videos covering topics such as network traffic analysis with Wireshark, intrusion detection with Snort and Zeek, threat detection with Suricata and Splunk, and memory analysis and disk analysis tools. It defines the objectives of blue team operations such as incident response, network traffic analysis, and threat intelligence. Finally, it provides context on how tools like Wireshark can be used by blue teams to analyze network traffic captured in PCAP files and identify potential security threats and malicious activity.