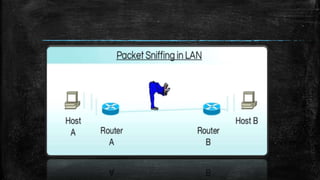
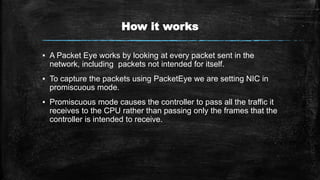
This document describes PacketEye, a Java-based packet sniffer application. PacketEye uses the jpcap library and WinPcap to monitor network traffic in promiscuous mode and capture packet data including protocol, time, source/destination IP addresses, ports, and data. It has a graphical user interface and allows network administrators to store, retrieve, filter, and examine captured packets to detect security breaches and intruders. The tool provides platform-independent network monitoring and troubleshooting capabilities.