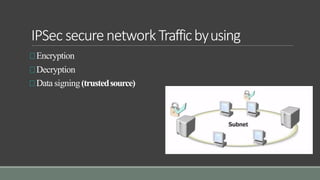
The document discusses Internet Protocol Security (IPSec). IPSec is a standard suite of protocols that provides data authentication, integrity, and confidentiality for IP packets. It defines encrypted, decrypted, and authenticated packets. IPSec uses encryption, decryption, and data signing to provide confidentiality, integrity, and authentication for securing network traffic. It has two encryption modes - tunnel mode and transport mode - that each have different uses depending on the network configuration.