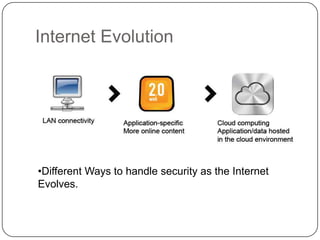
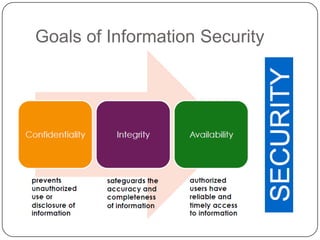
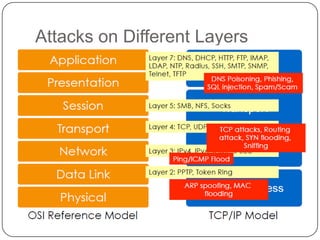
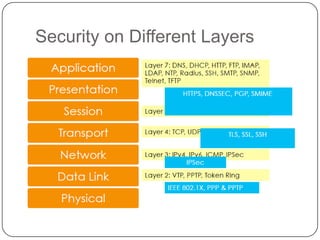
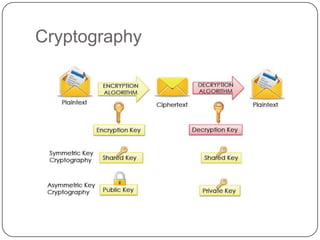
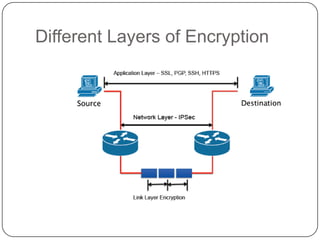
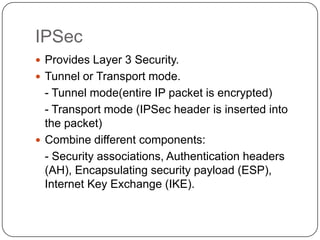
This document discusses network security. It covers topics such as why security is important given that the internet was initially designed for connectivity. It describes different types of security including computer, network, and internet security. It discusses security goals and common attacks targeting different layers such as IP, TCP, and DNS. The document also outlines security measures like firewalls, intrusion detection systems, access control, cryptography, public key infrastructure, and IPSec. It concludes with security management topics such as risk management and the Whois database.