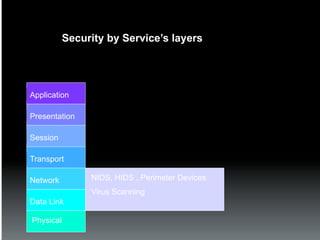
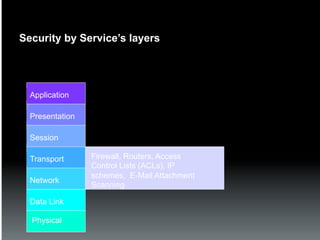
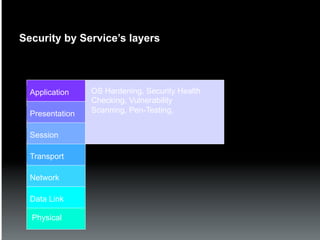
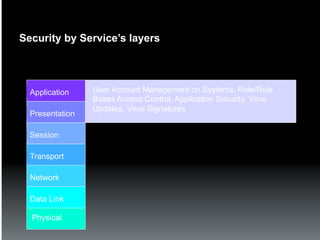
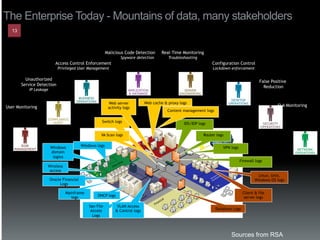
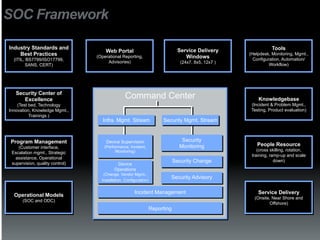
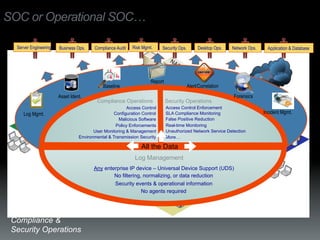
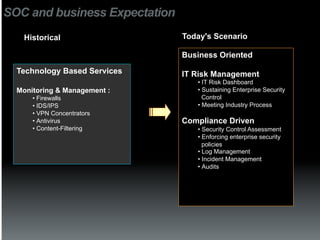
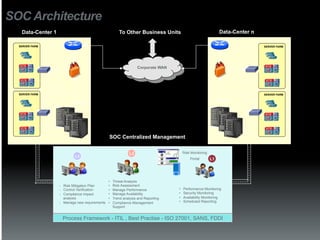
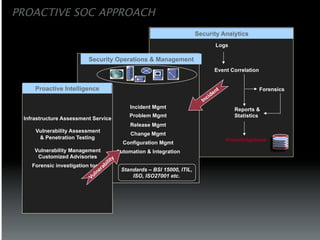
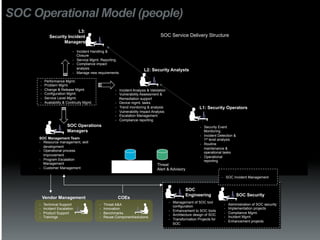
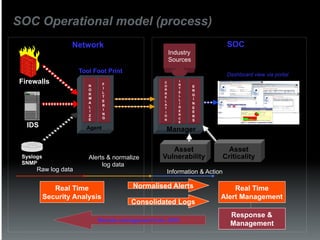
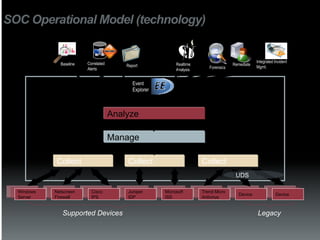
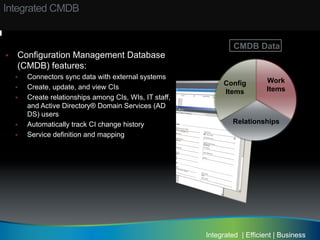
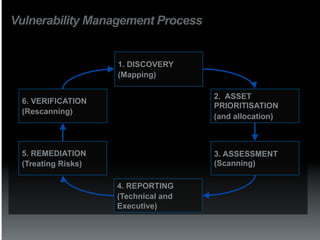
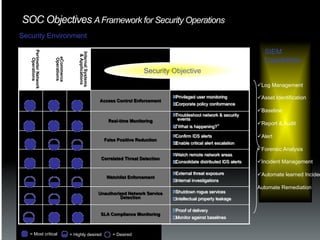
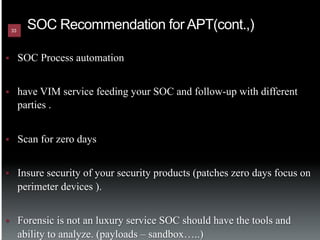
The document discusses the establishment and operation of a Security Operations Center (SOC), emphasizing its importance in mitigating risks and enhancing organizational security in a changing threat landscape. It highlights the key functions of an SOC such as real-time monitoring, incident management, and compliance enforcement, while addressing technological and operational challenges. Recommendations for improving SOC effectiveness include automating processes, conducting vulnerability assessments, and ensuring proactive threat investigation and remediation.