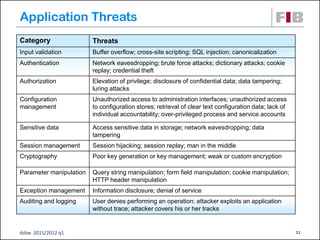
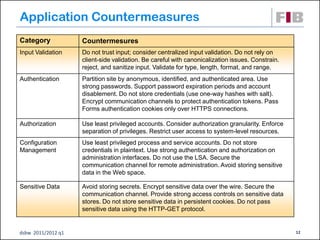
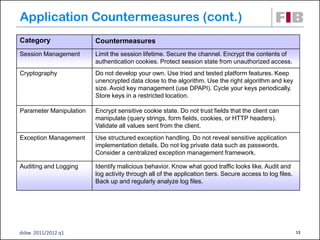
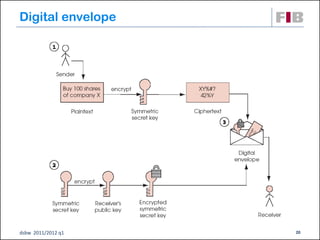
The document discusses security principles for web applications, including identifying threats like spoofing and tampering, vulnerabilities, and attacks. It emphasizes authenticating and authorizing users, implementing measures like encryption to ensure confidentiality and integrity of data, and making systems available through techniques such as throttling. The document also provides examples of network, host, and application level threats and corresponding countermeasures.