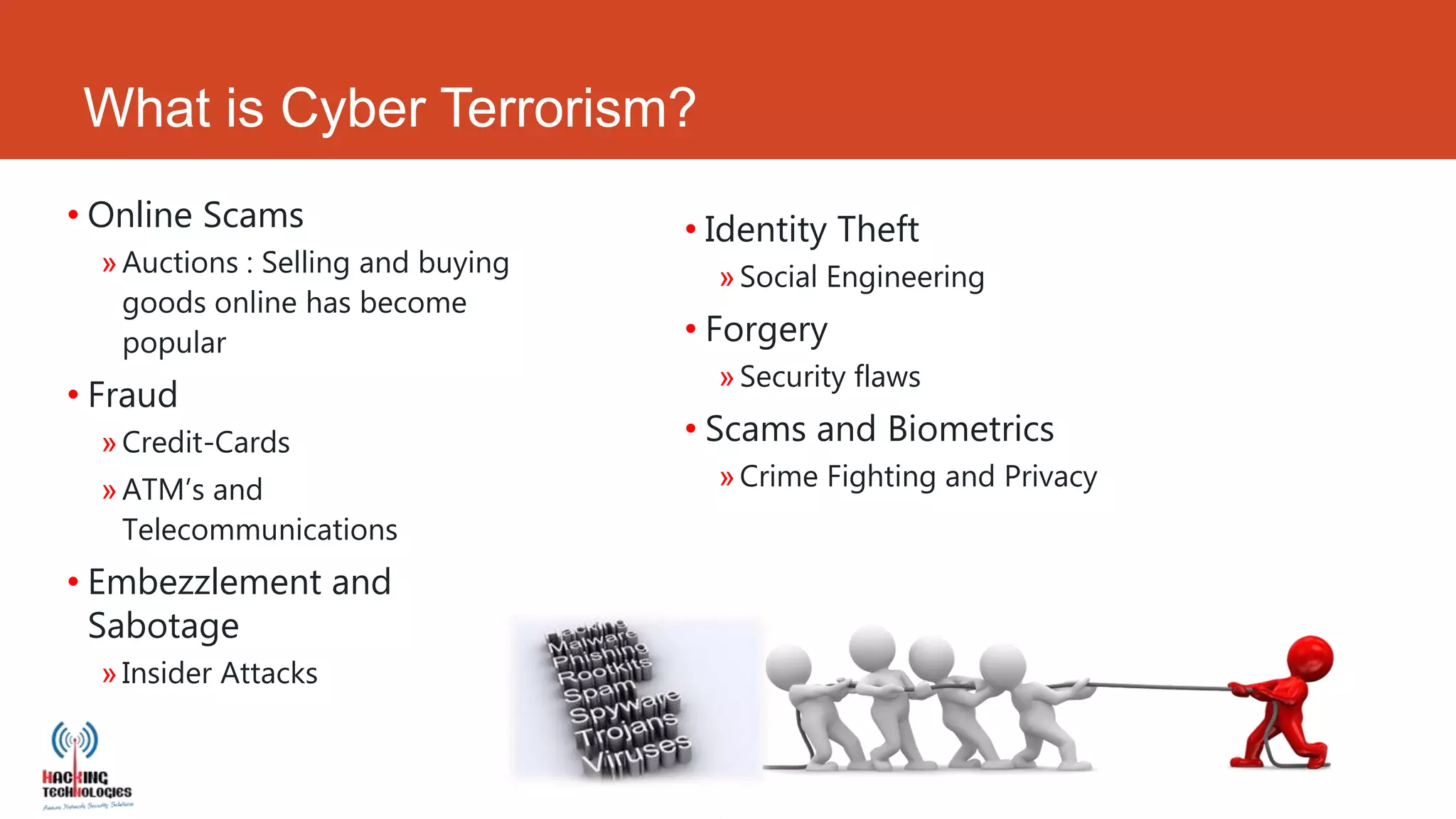
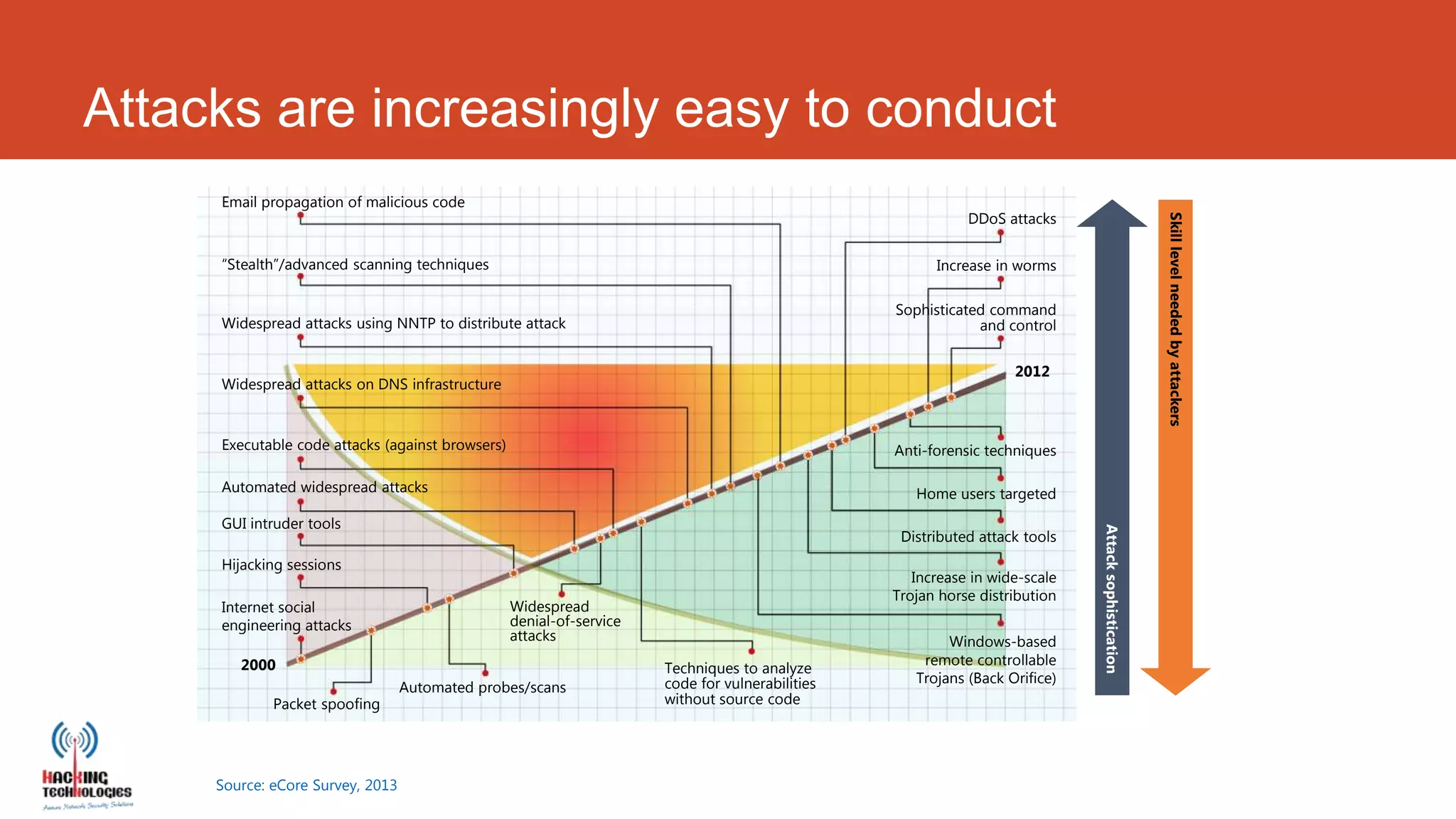
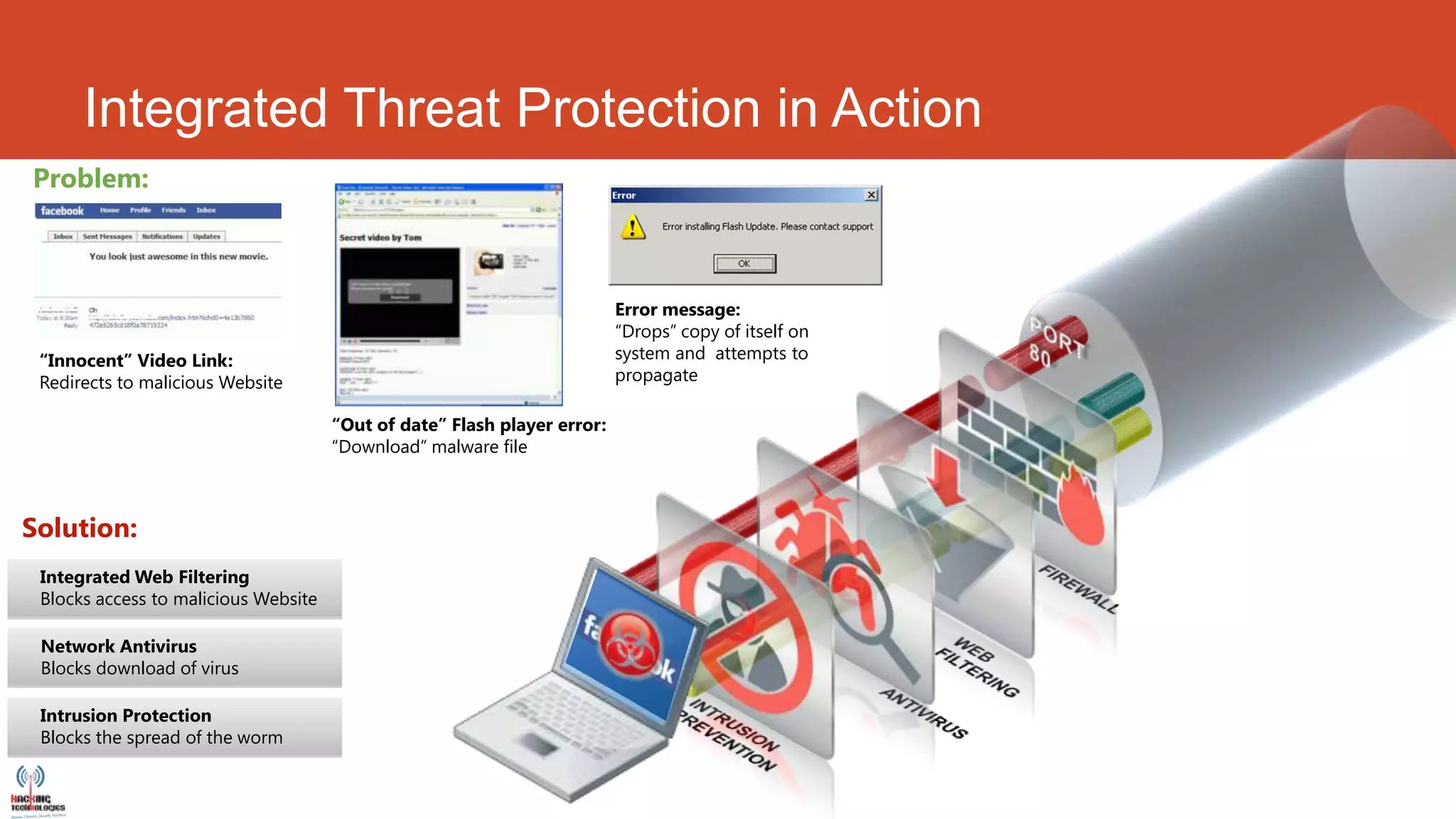
This document discusses cyber crime trends in 2013 and cyber security solutions. It begins with an introduction of the author and their background. It then defines various types of cyber crimes like online scams, identity theft, fraud, and embezzlement. International cyber crime trends are discussed along with increasing sophistication of attacks. Solutions discussed include integrated threat protection through application control, intrusion prevention, web filtering, vulnerability management, antispam, and antivirus technologies. The document concludes with information about the author's company and resources.