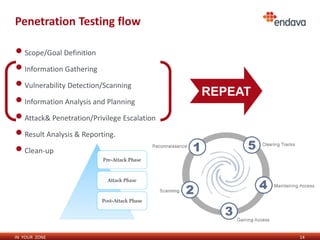
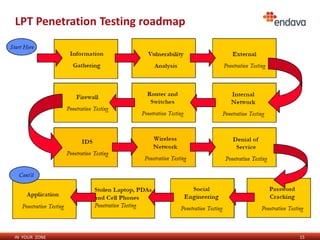
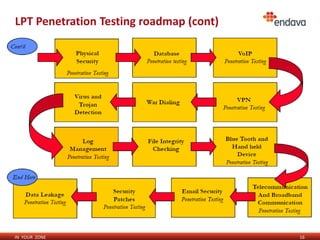
This document discusses penetration testing and ethical hacking. It provides an overview of penetration testing methodology and the services offered by Endava, including regular vulnerability scans, penetration tests, PCI assessments, security trainings, audits, and intrusion monitoring solutions. The presenter, Maxim Catanoi, is an IT security consultant at Endava with over 9 years of experience and multiple security certifications.