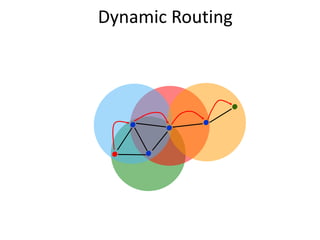
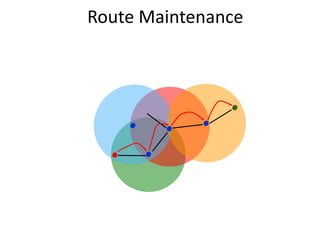
This document discusses network management for wireless sensor networks. It begins with an introduction to traditional network management models and then discusses key design issues for network management in WSNs including power efficiency, scalability, and simplicity. It provides MANNA as an example management architecture for WSNs and discusses other related issues like naming, localization, and fault tolerance. The document also outlines applications of WSNs such as habitat monitoring, structural monitoring, and smart roads.