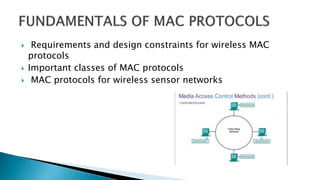
This document discusses medium access control (MAC) protocols, which regulate access to a shared wireless medium between nodes. It covers key requirements for MAC protocols including throughput efficiency, fairness, and low overhead. It also describes challenges like the hidden terminal problem, exposed terminal problem, and sources of overhead from collisions, overhearing, and idle listening. Finally, it categorizes common MAC protocols as fixed assignment, demand assignment, and random access and notes additional energy conservation requirements for wireless sensor networks.