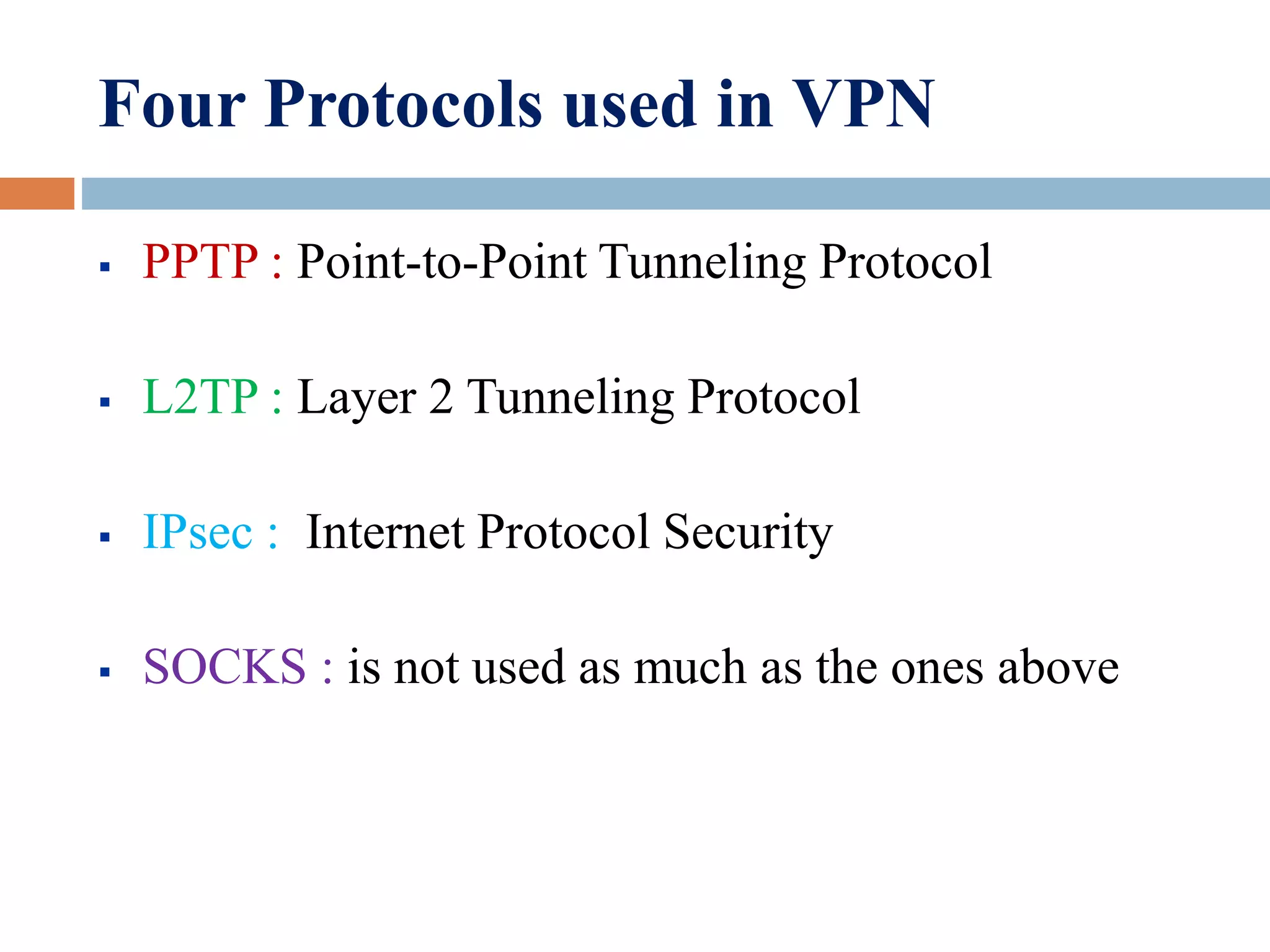
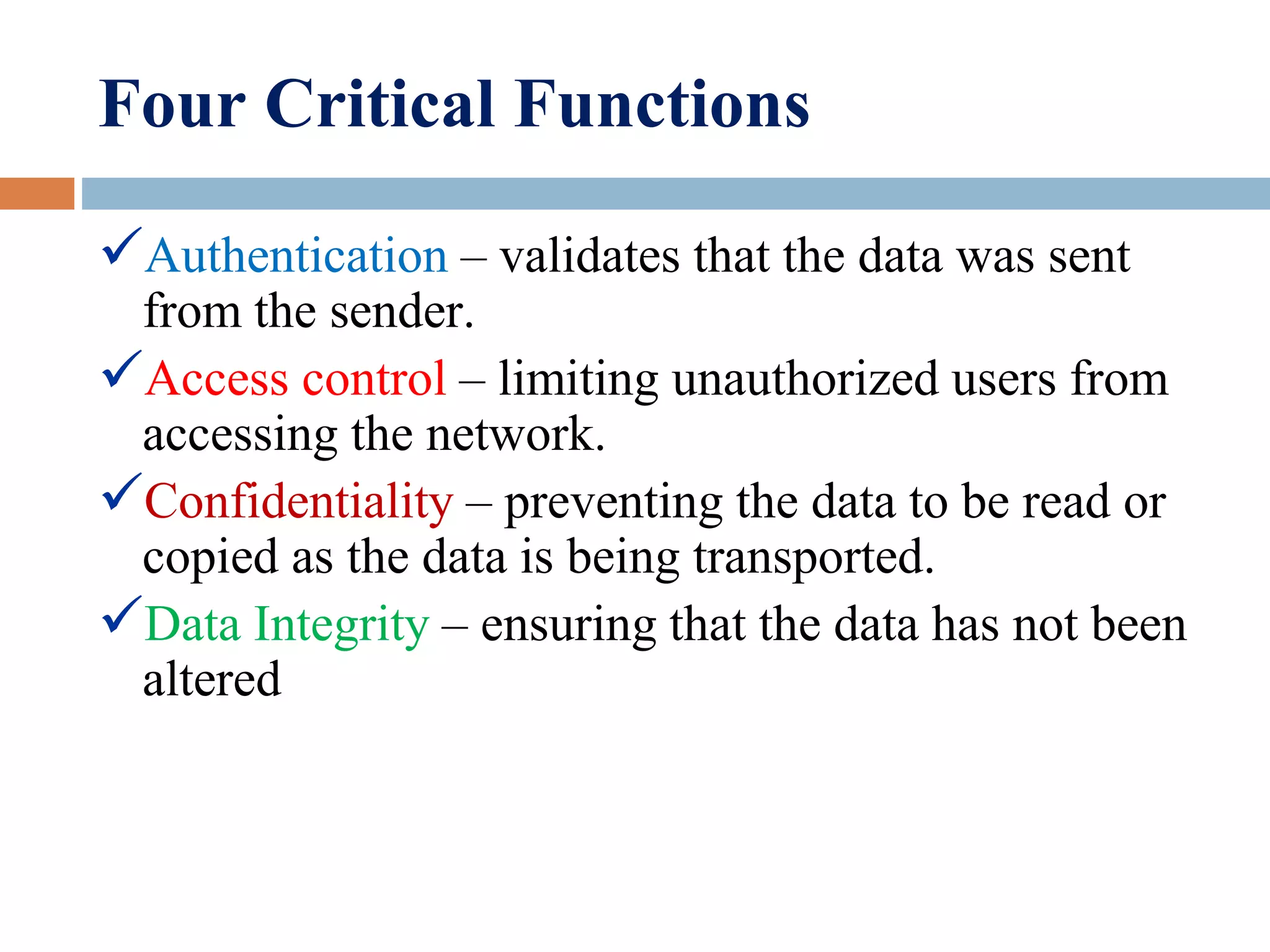
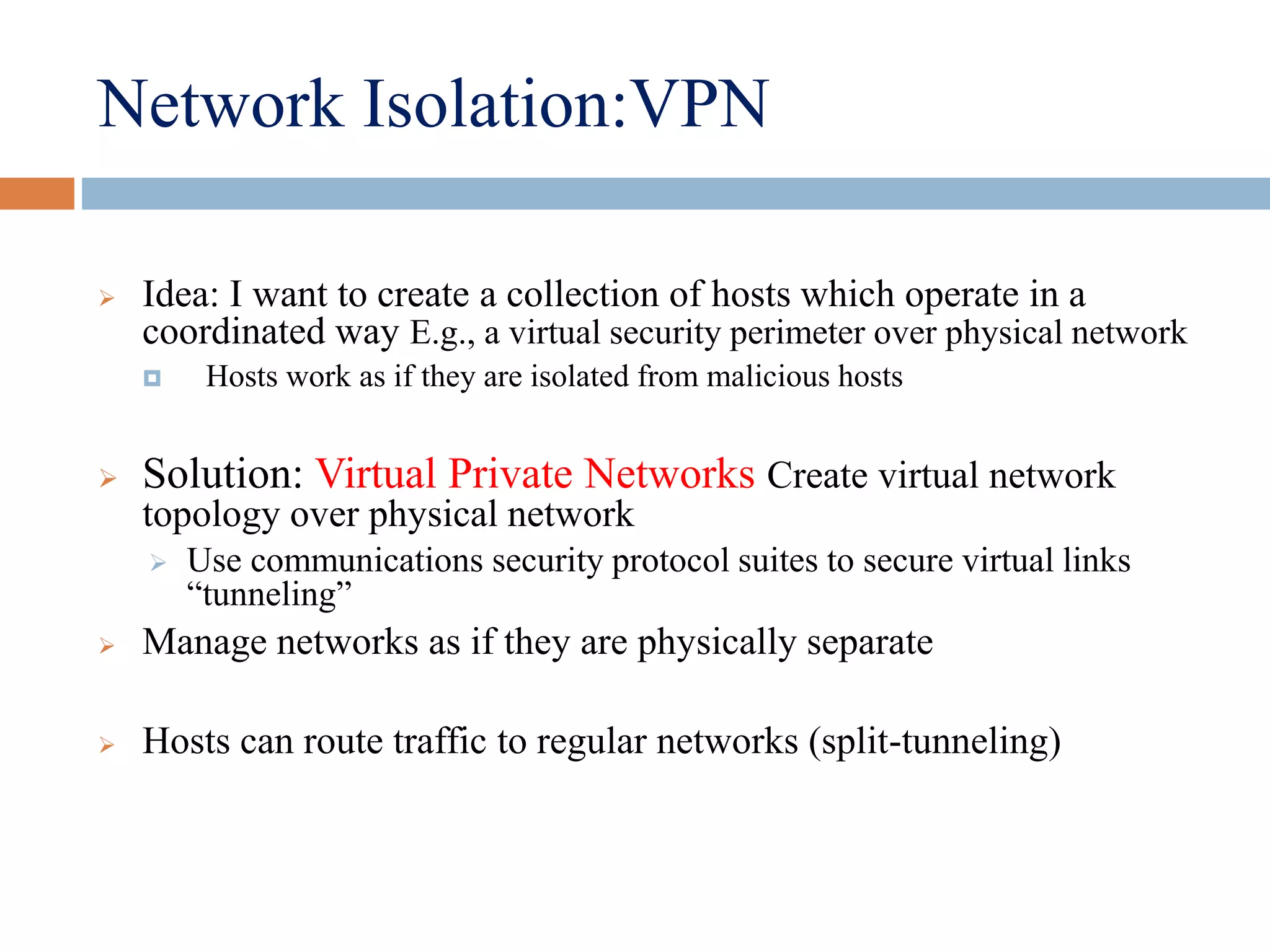
VPN (virtual private network) allows users to connect securely over a public network like the internet. It uses encryption and authentication to provide a secure connection through an otherwise insecure network. The main benefits of VPNs are reduced costs compared to dedicated private networks using leased lines or dial-up. VPNs work by encapsulating packets inside packets of another protocol, called "tunneling", to create and maintain a virtual private circuit between two endpoints.






![Tunneling
A virtual point-to-point connection made through a public
network.It transports encapsulated datagrams
Encrypted Inner Datagram
Original Datagram
Outer Datagram Data AreaDatagram Header
Data Encapsulation [From Comer]
Two types of end points:
Remote Access
Site-to-Site](https://image.slidesharecdn.com/wlan-160503132550/75/WLAN-VPN-Security-10-2048.jpg)