The document discusses several routing protocols for mobile ad hoc networks:
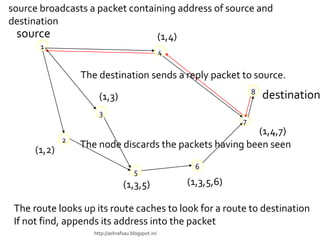
- DSR allows nodes to cache and share routing information for more efficient routing but has larger packet headers due to source routing. AODV uses only next hop information, keeping routing tables smaller.
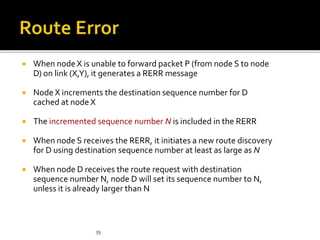
- Both protocols use route discovery and maintenance, but AODV proactively refreshes routes while DSR reacts to failures. AODV also uses sequence numbers to prevent loops and choose fresher routes.
- Overall, DSR is better for networks where routes change infrequently while AODV scales better and maintains only active routes, at the cost of higher routing overhead during route discovery. Security remains a challenge for both protocols.