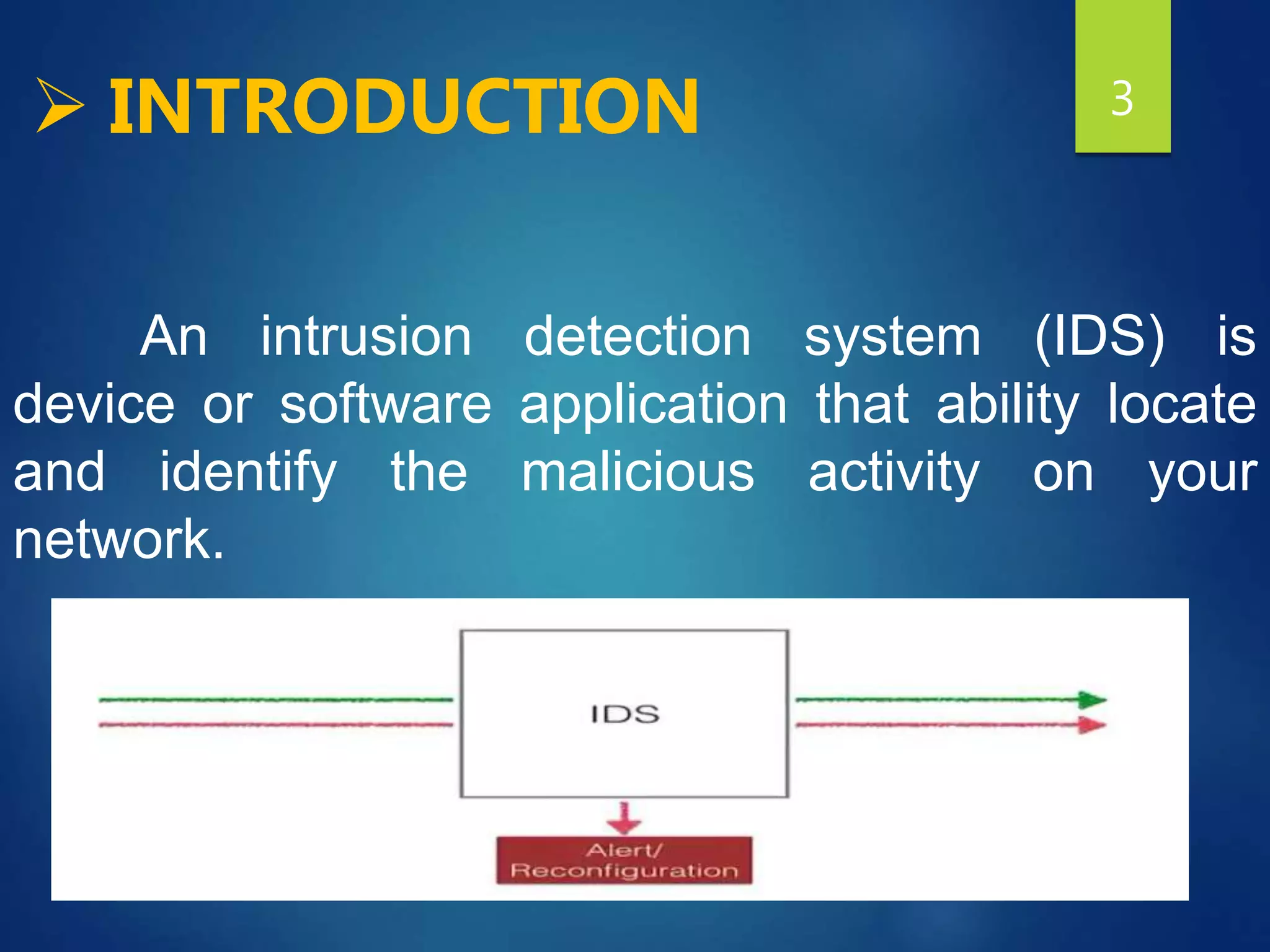
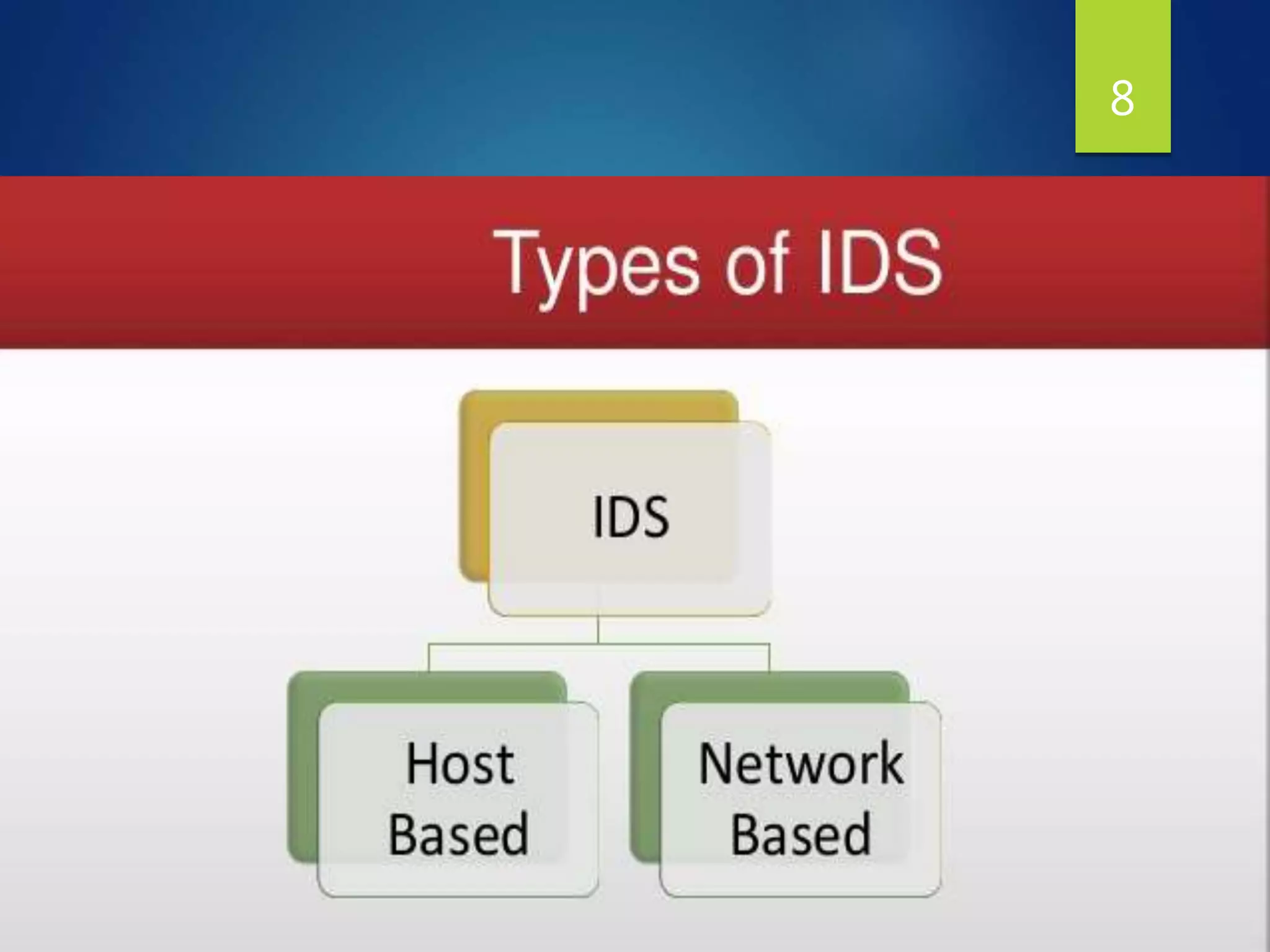
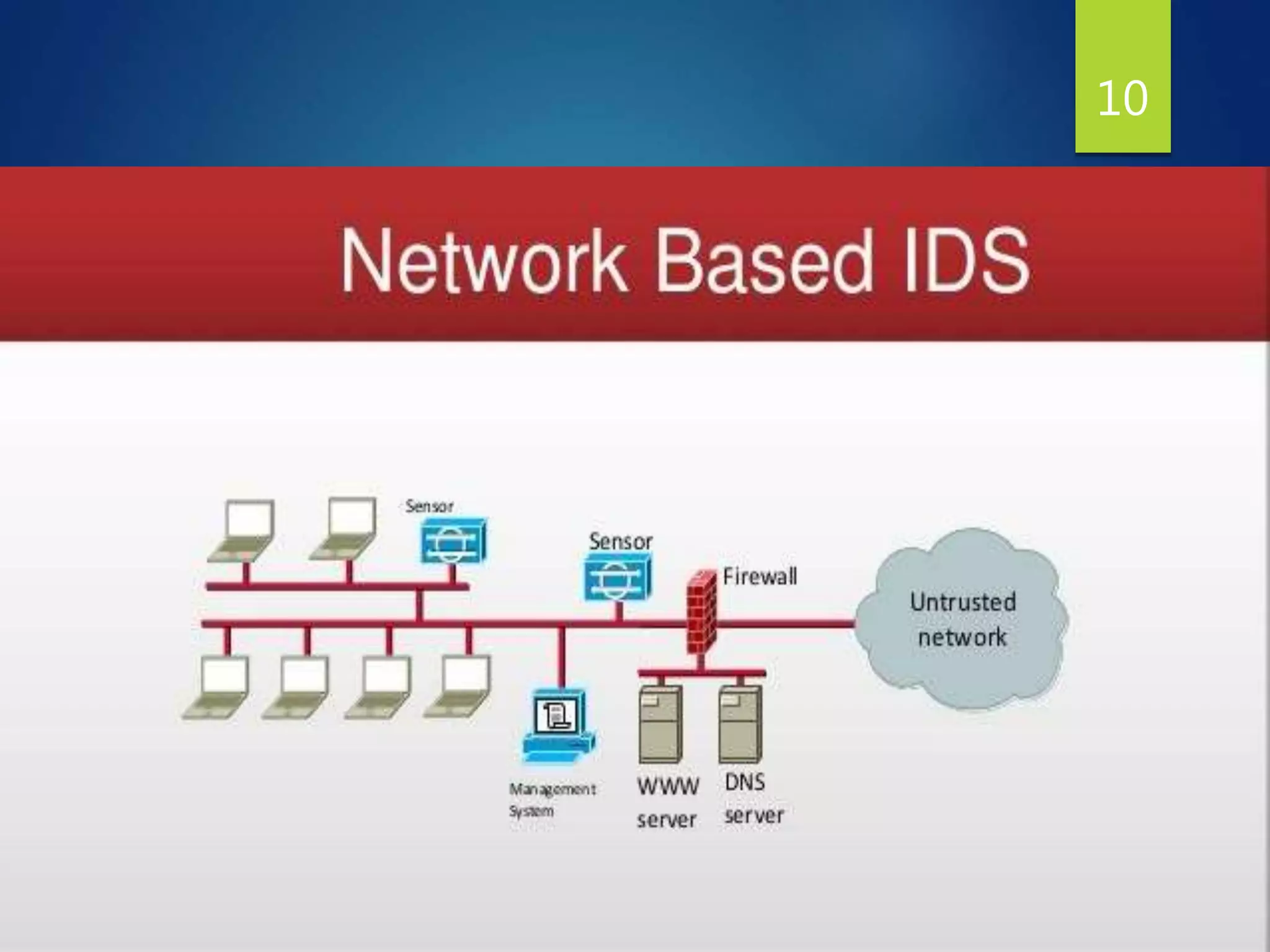
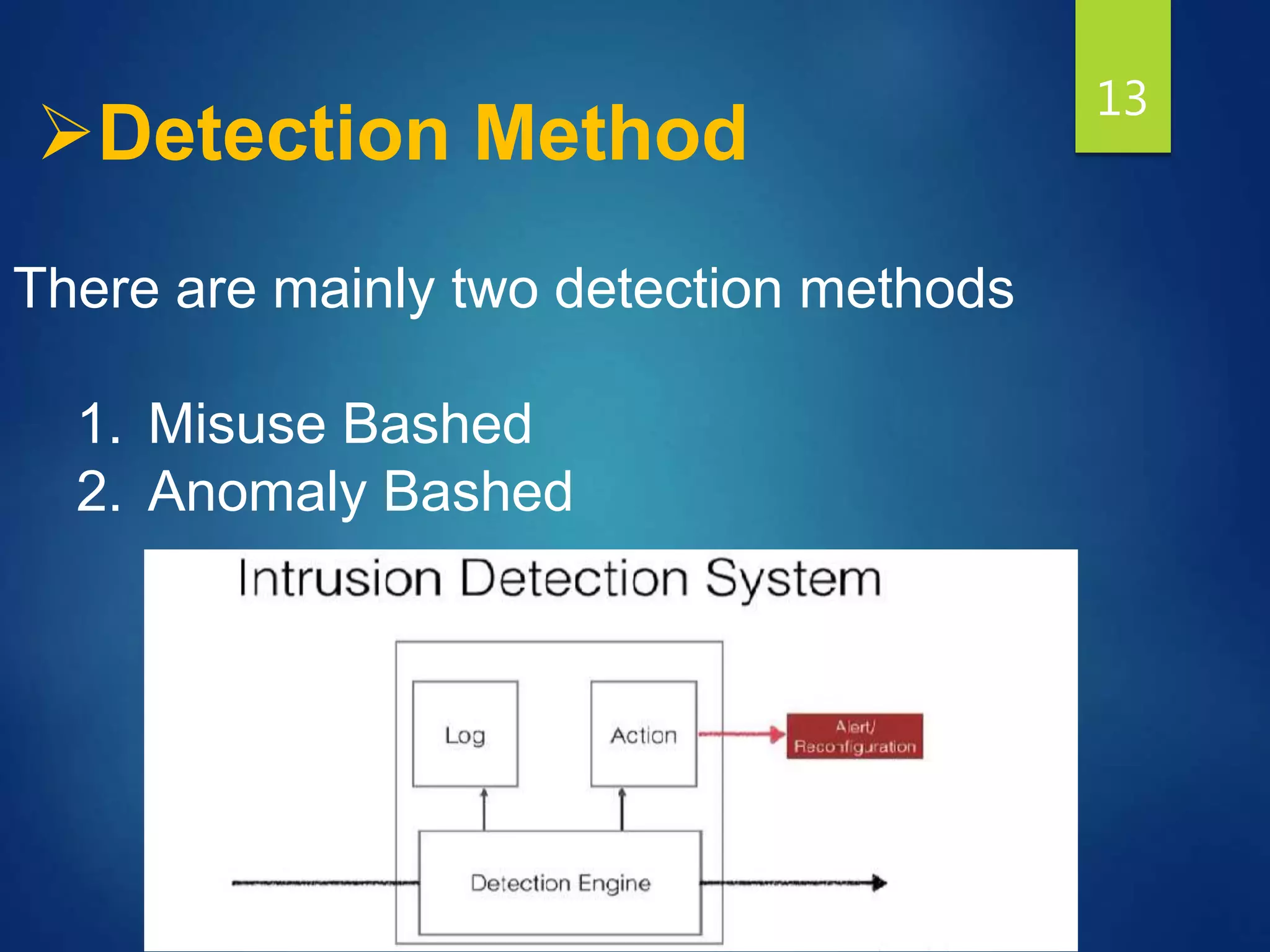
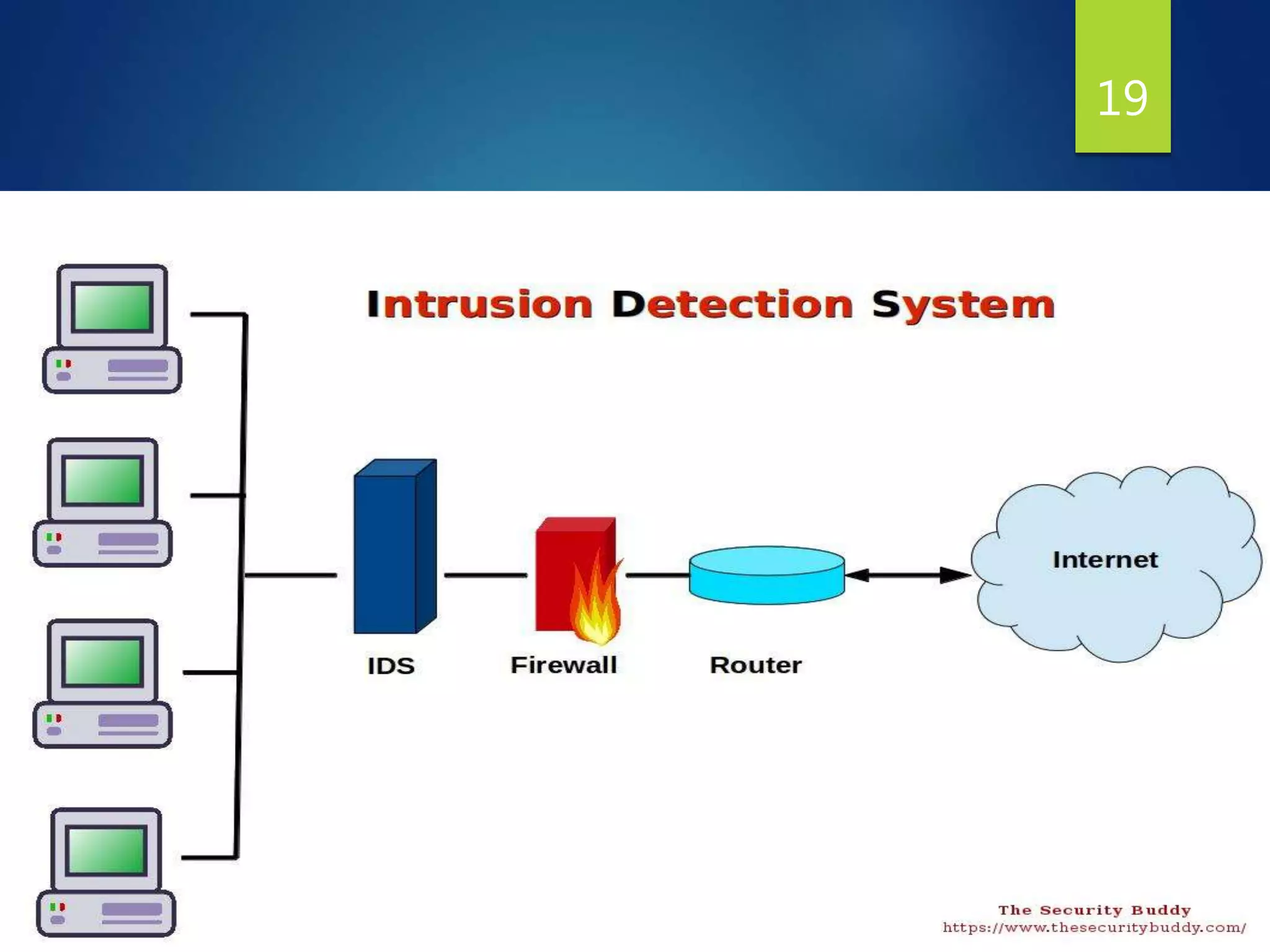
This document provides an overview of intrusion detection systems (IDS). It discusses two main types of IDS - network intrusion detection systems (NIDS) which monitor network traffic to and from all devices, and host-based intrusion detection systems (HIDS) which monitor traffic to and from individual hosts. It also describes two common detection methods - misuse detection which looks for known attack patterns, and anomaly detection which identifies abnormal network traffic.