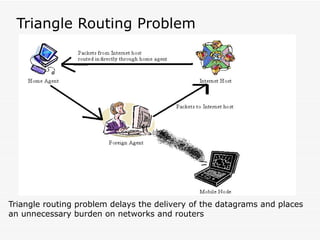
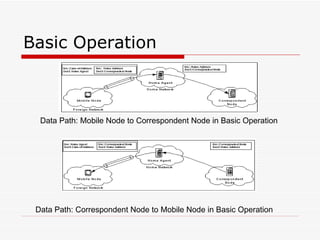
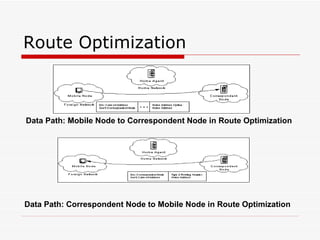
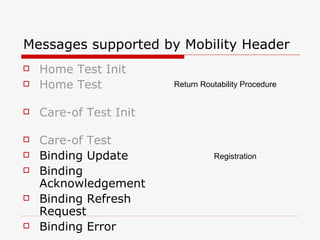
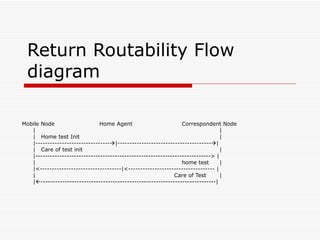
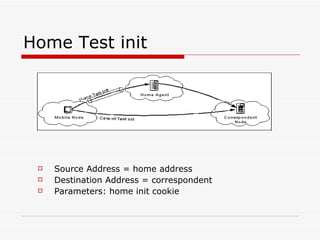
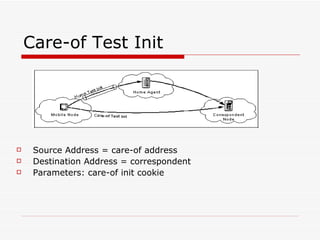
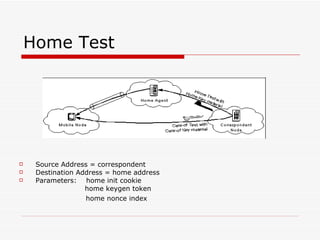
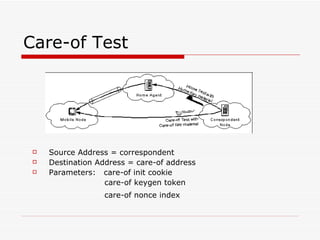
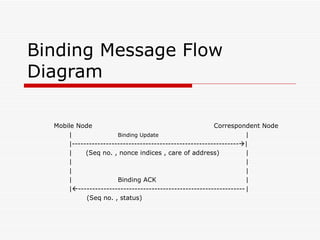
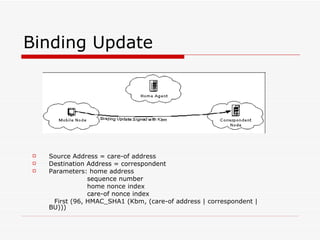
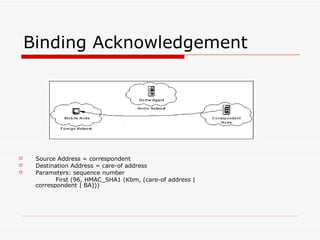
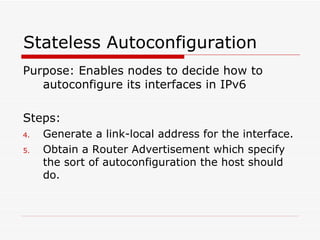
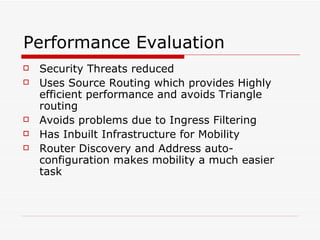
Mobile IPv6 aims to support mobility in IPv6 networks by allowing devices to maintain ongoing connections while moving between different networks. It operates in two modes: basic operation uses bidirectional tunneling between the mobile node and home agent, while route optimization establishes routes directly between the mobile node and correspondent nodes. Route optimization improves performance but introduces security challenges in authenticating binding updates. Evaluations found Mobile IPv6 reduces problems from triangular routing and ingress filtering compared to Mobile IPv4, but securing neighbor discovery and authorizing binding updates remain vulnerabilities.