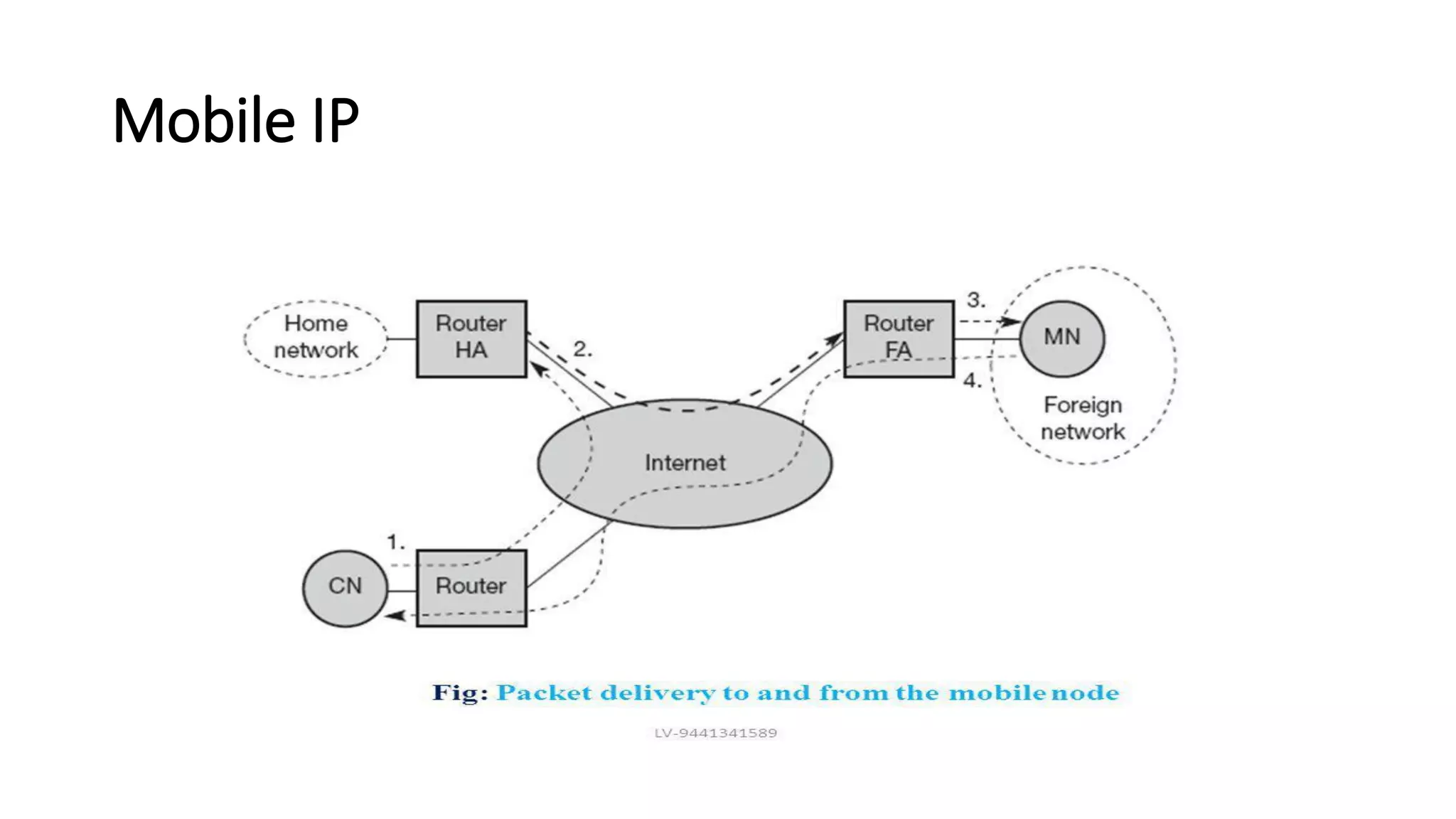
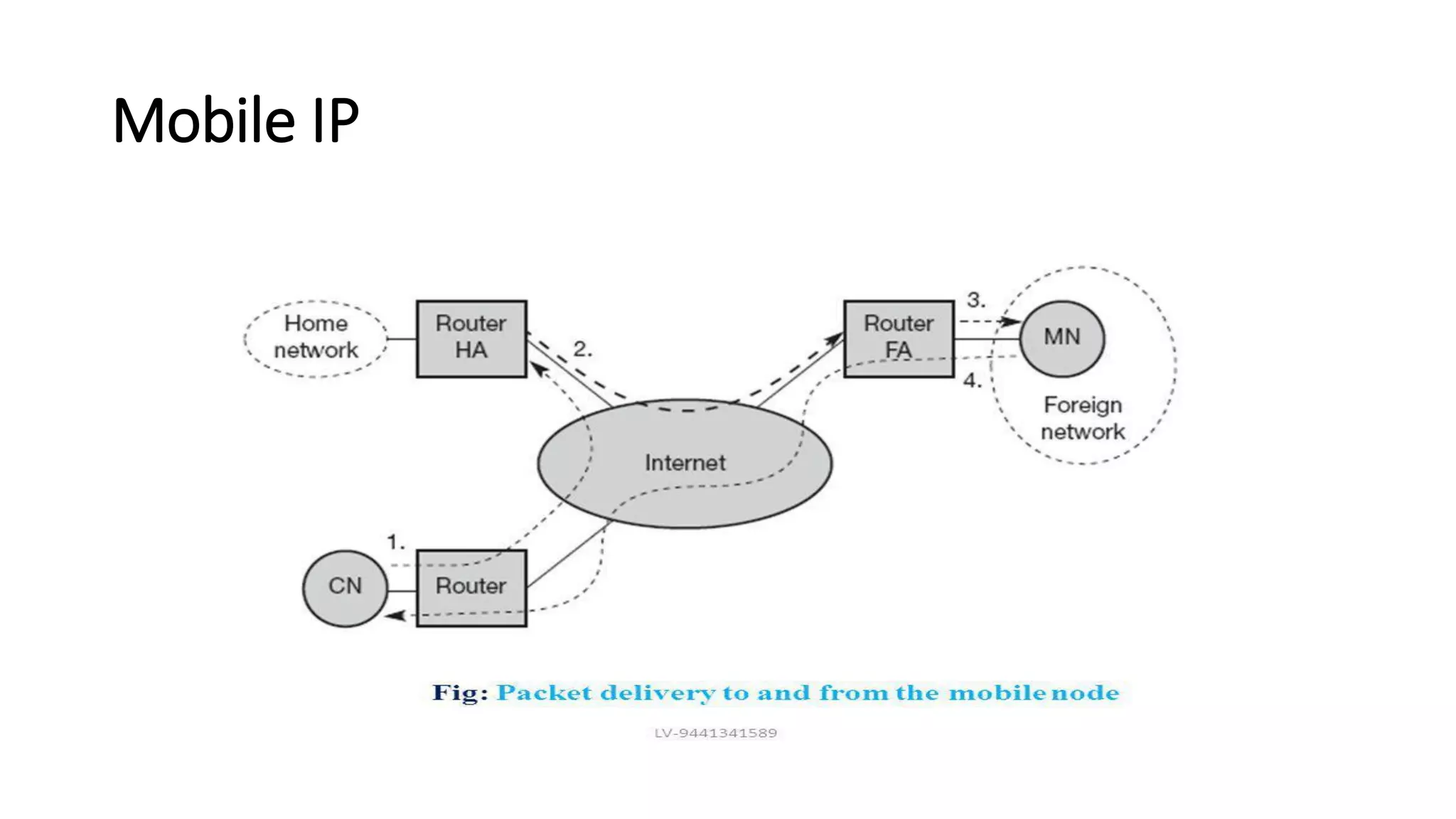
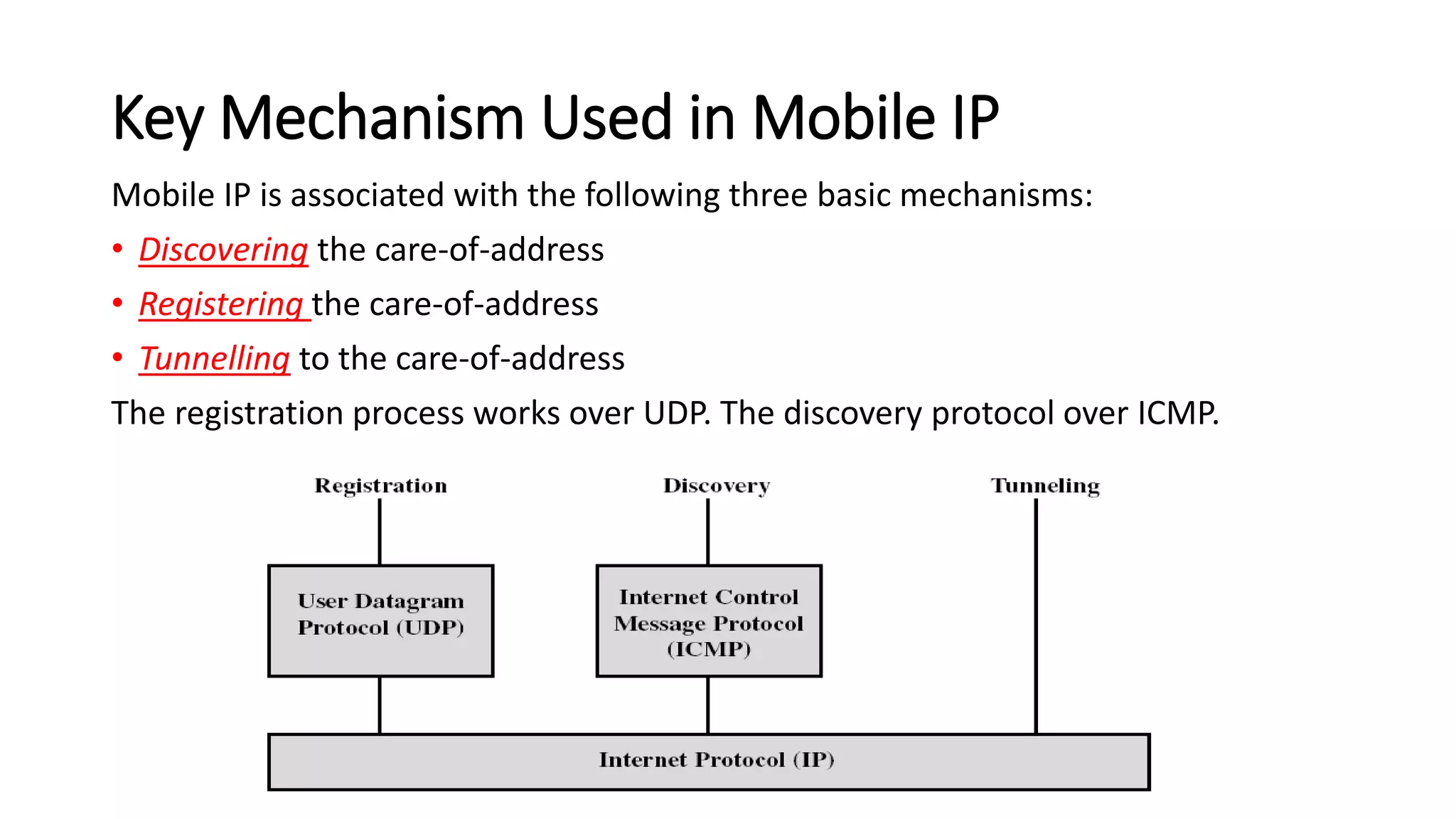
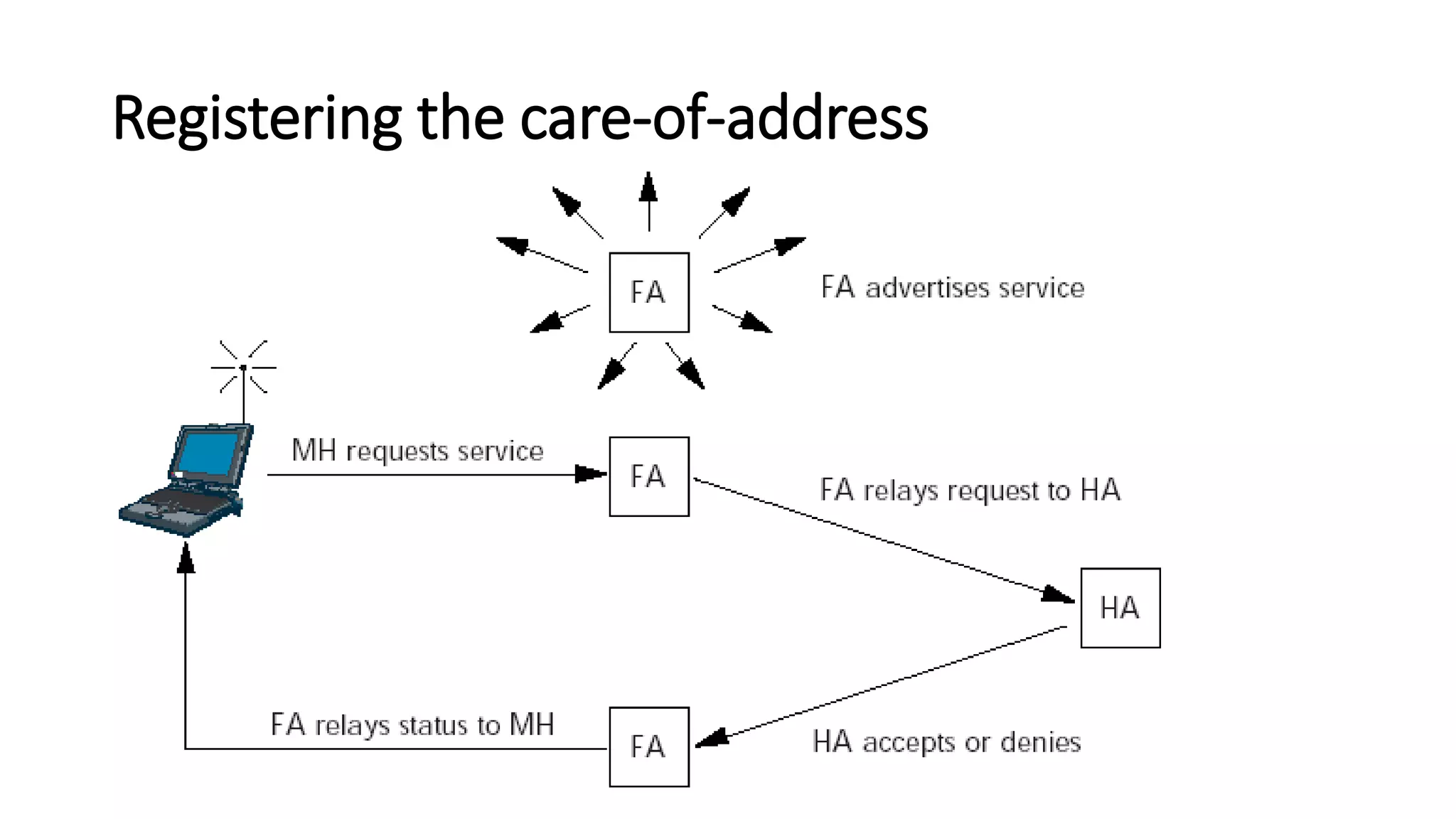
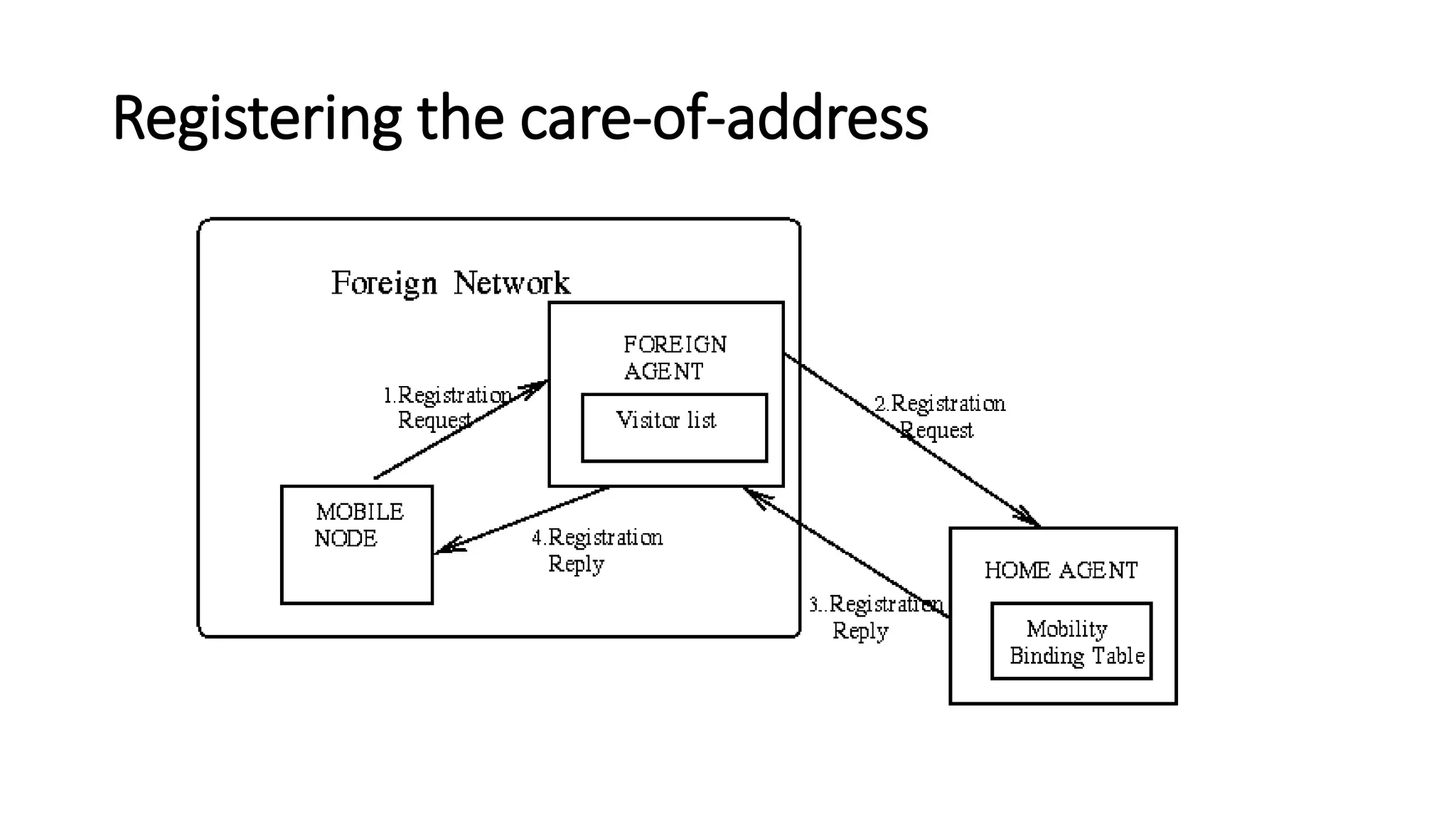
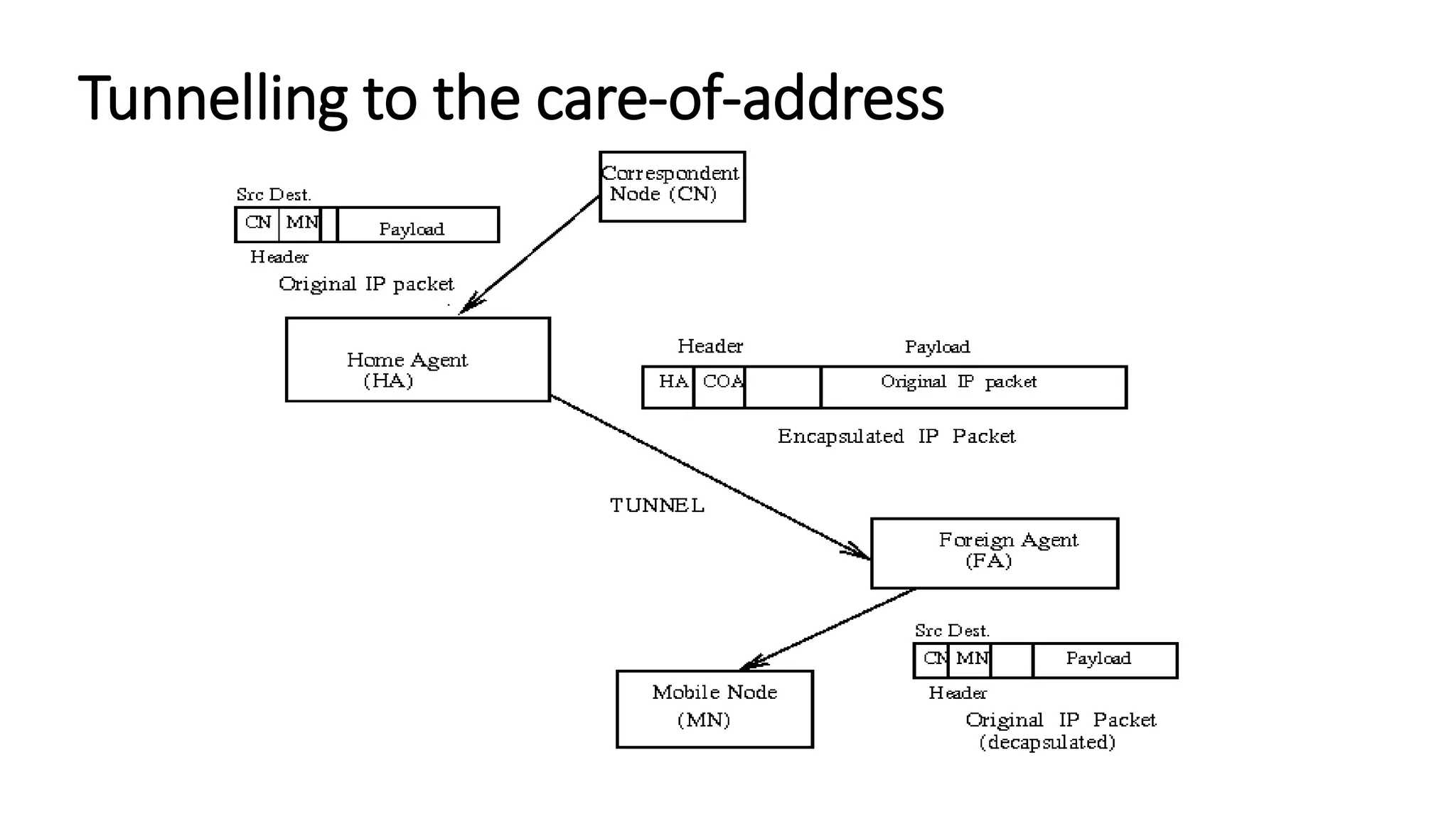
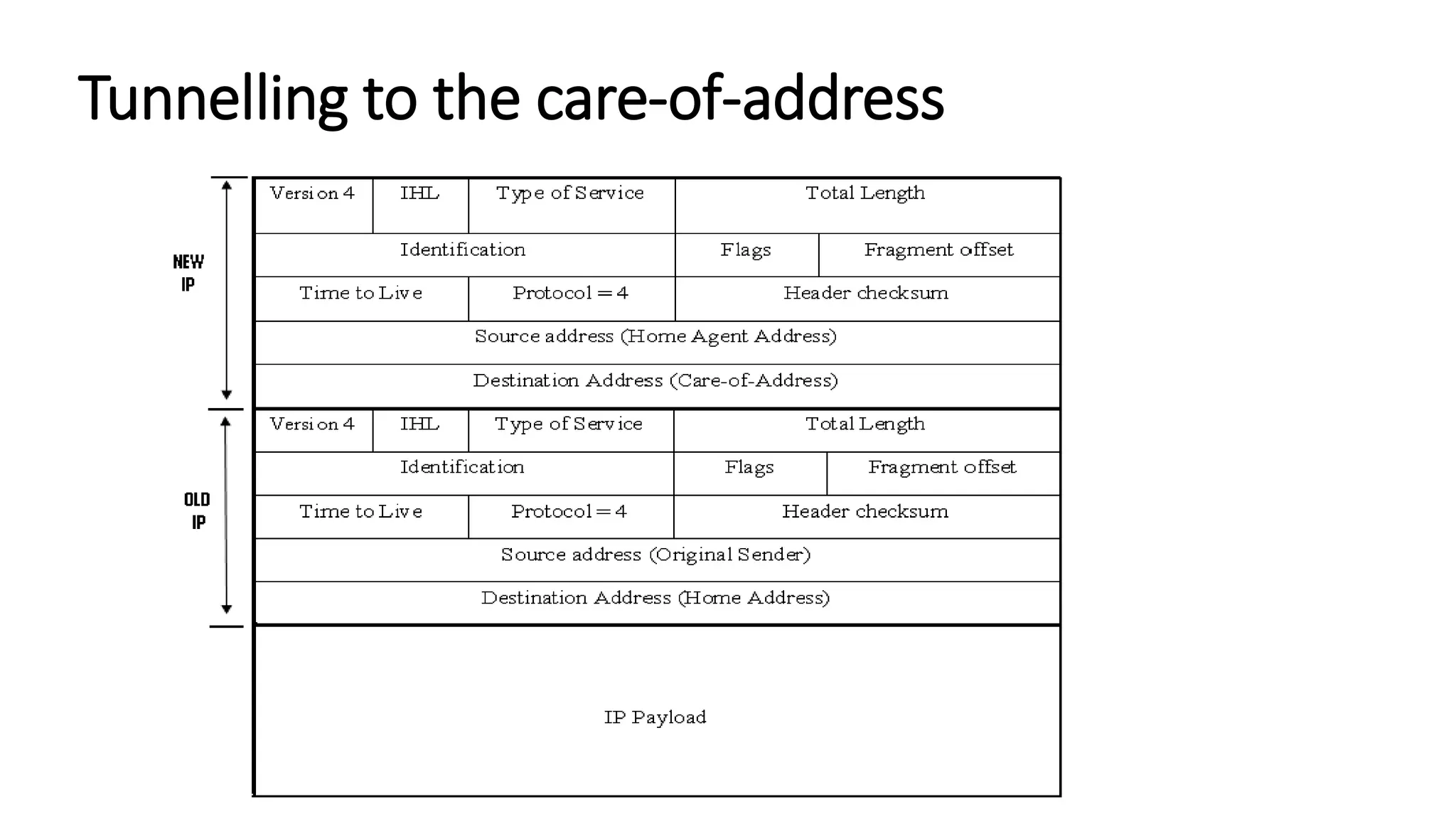
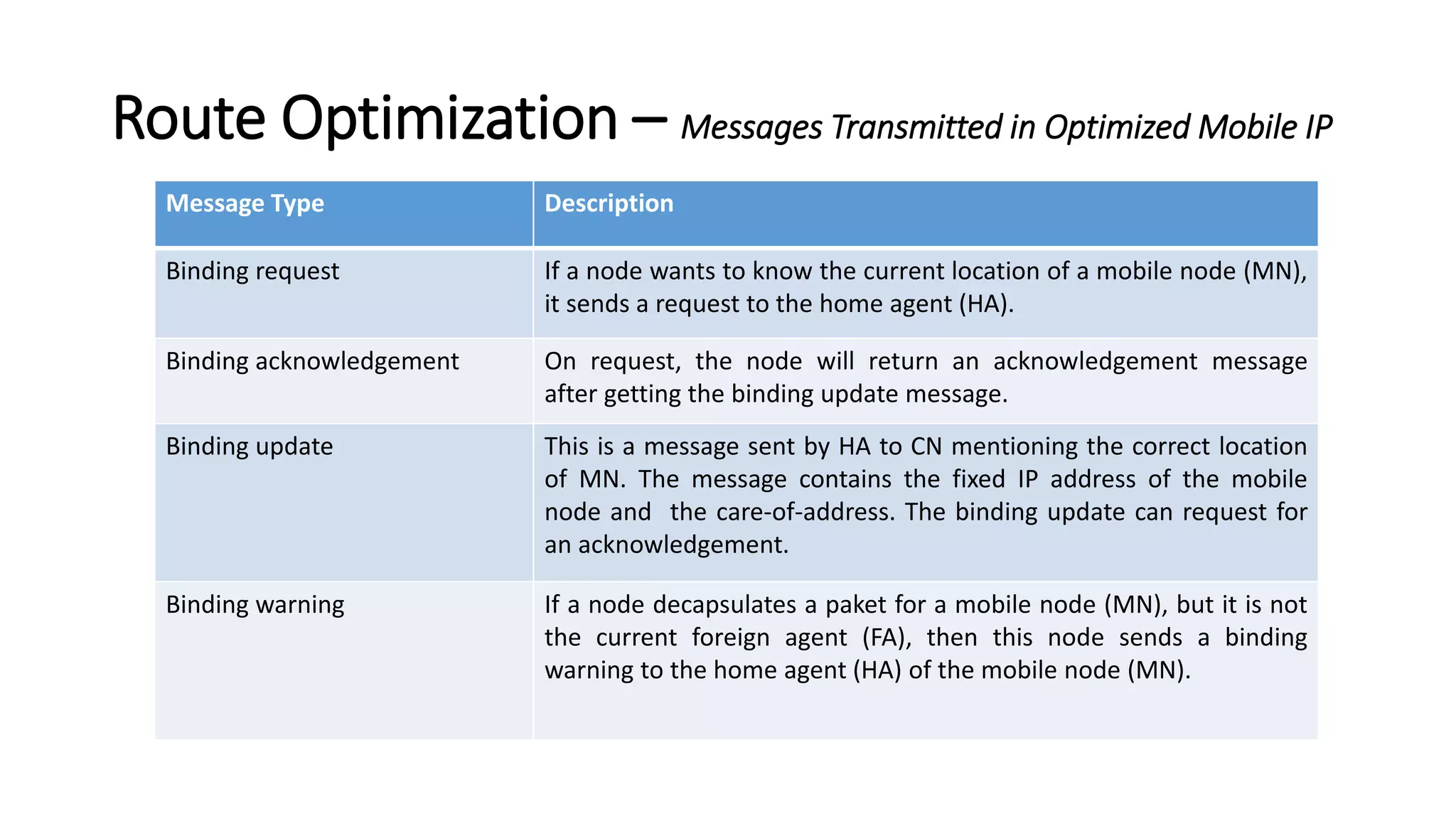
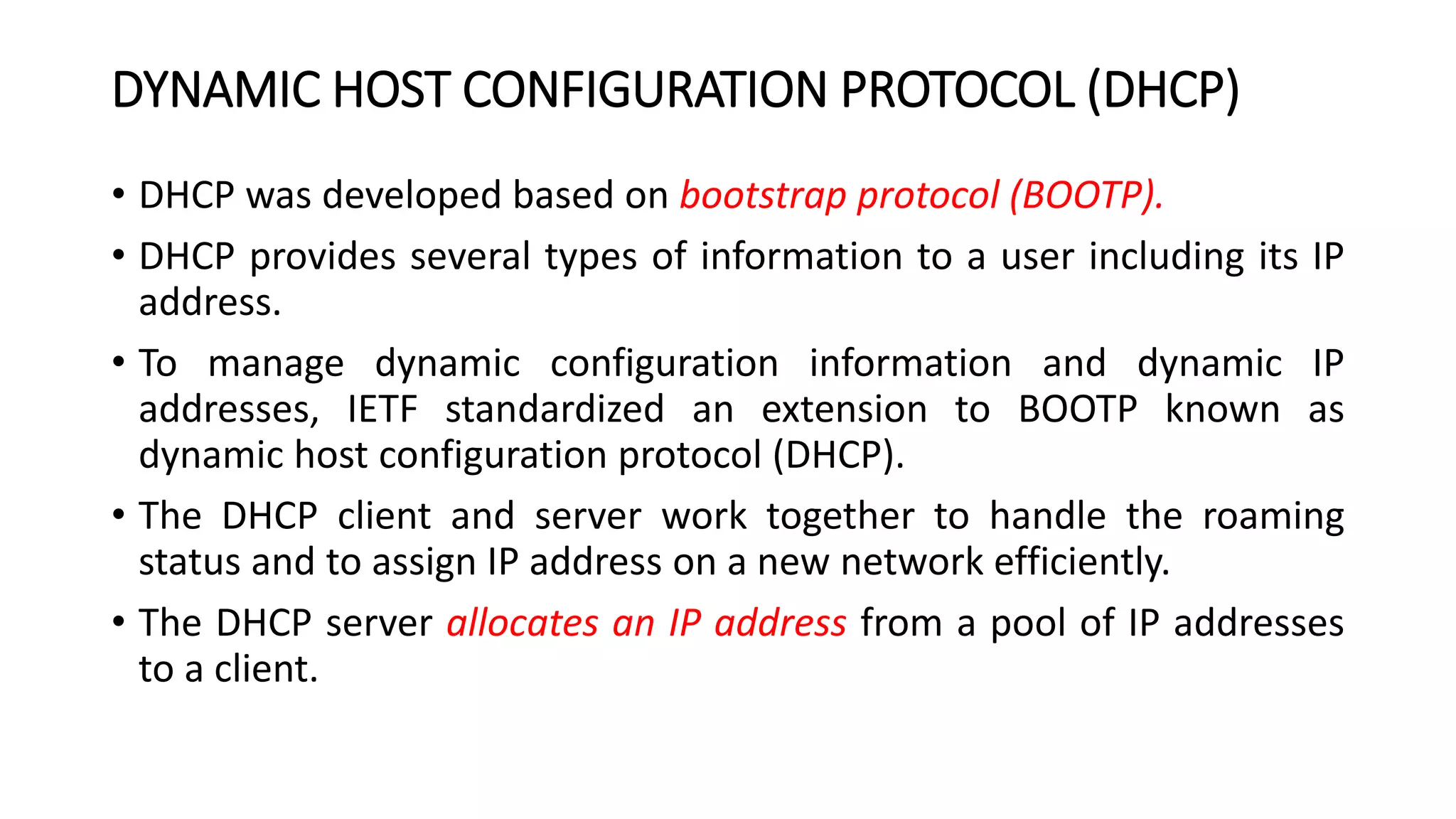
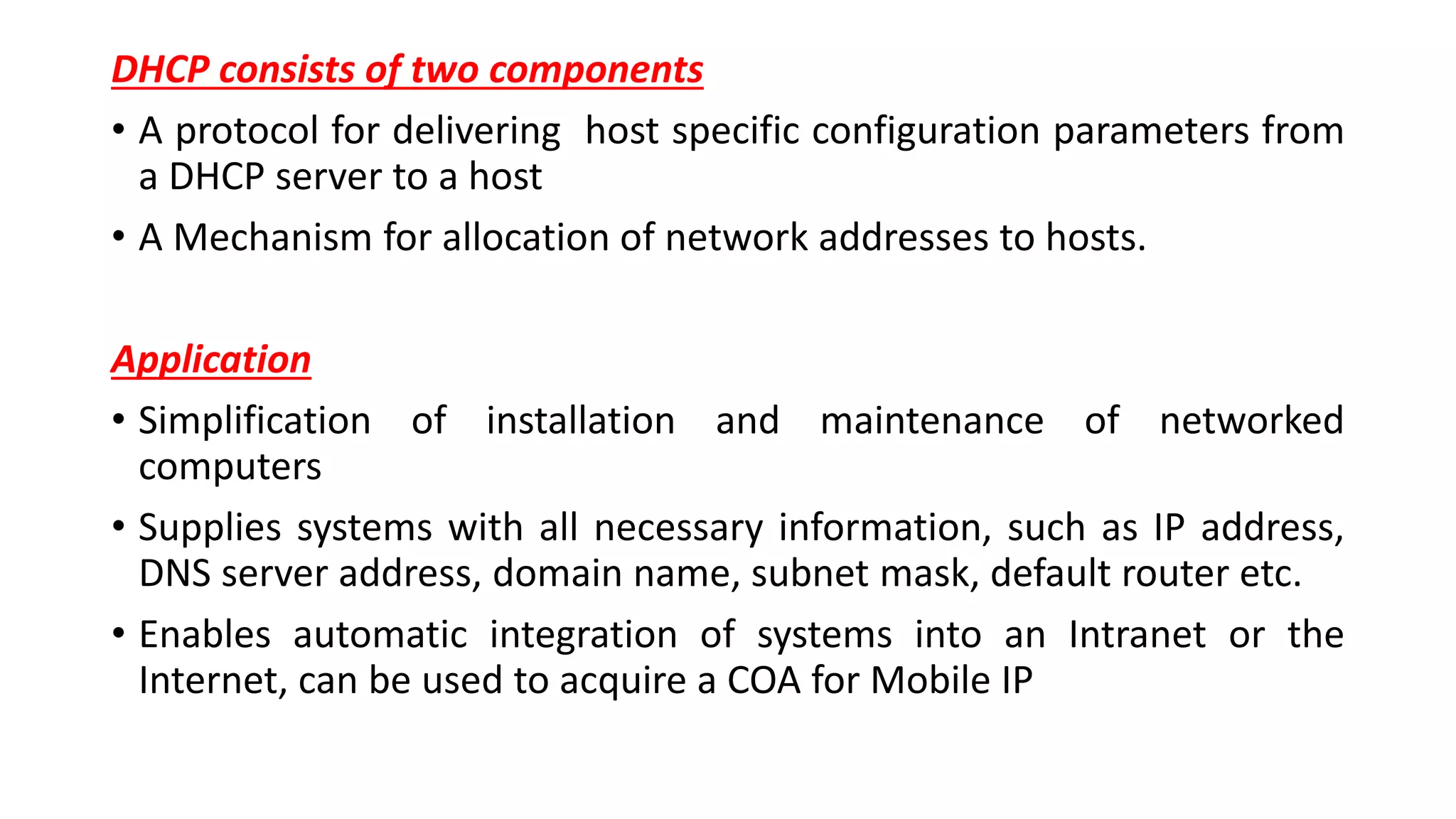
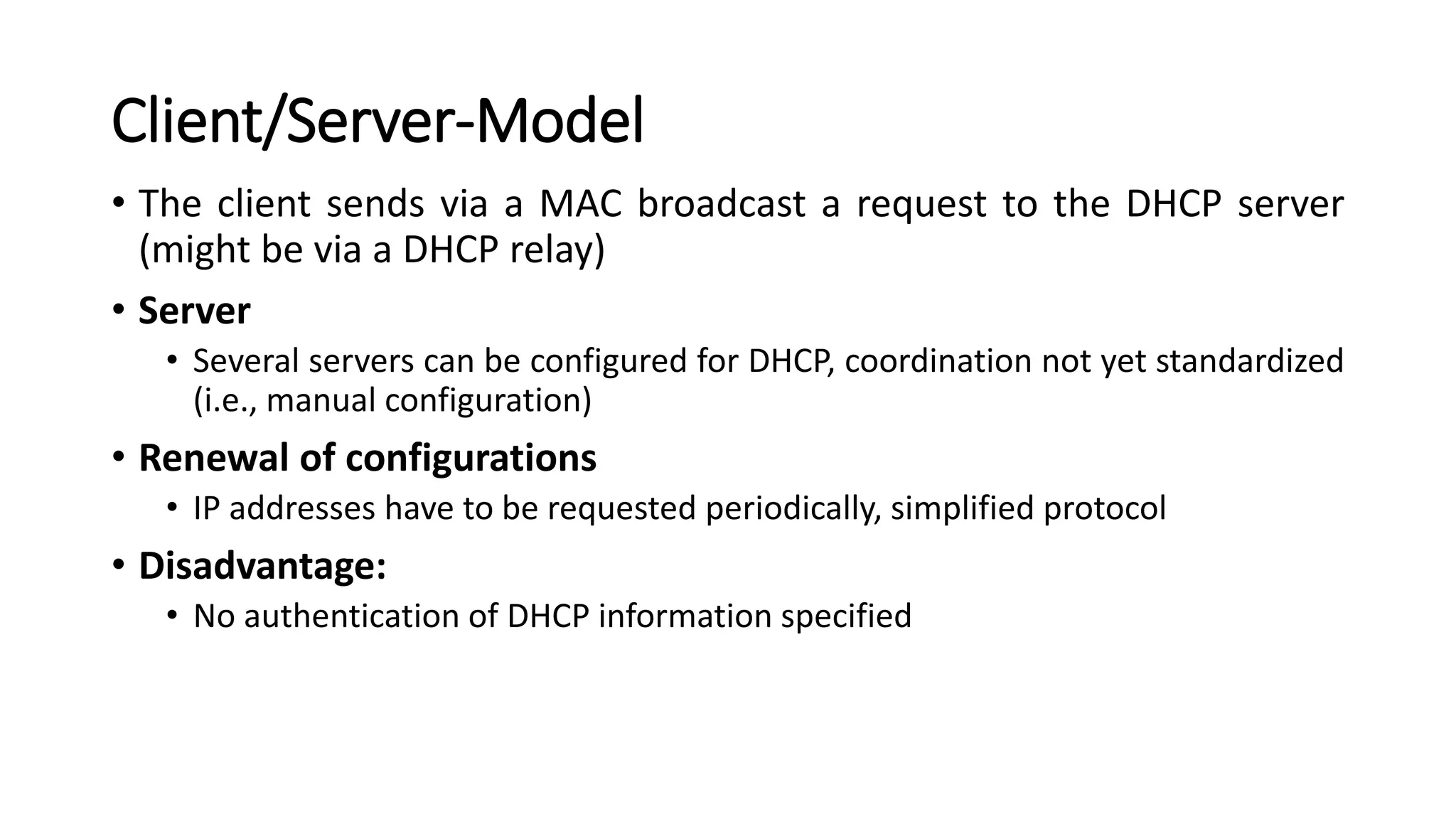
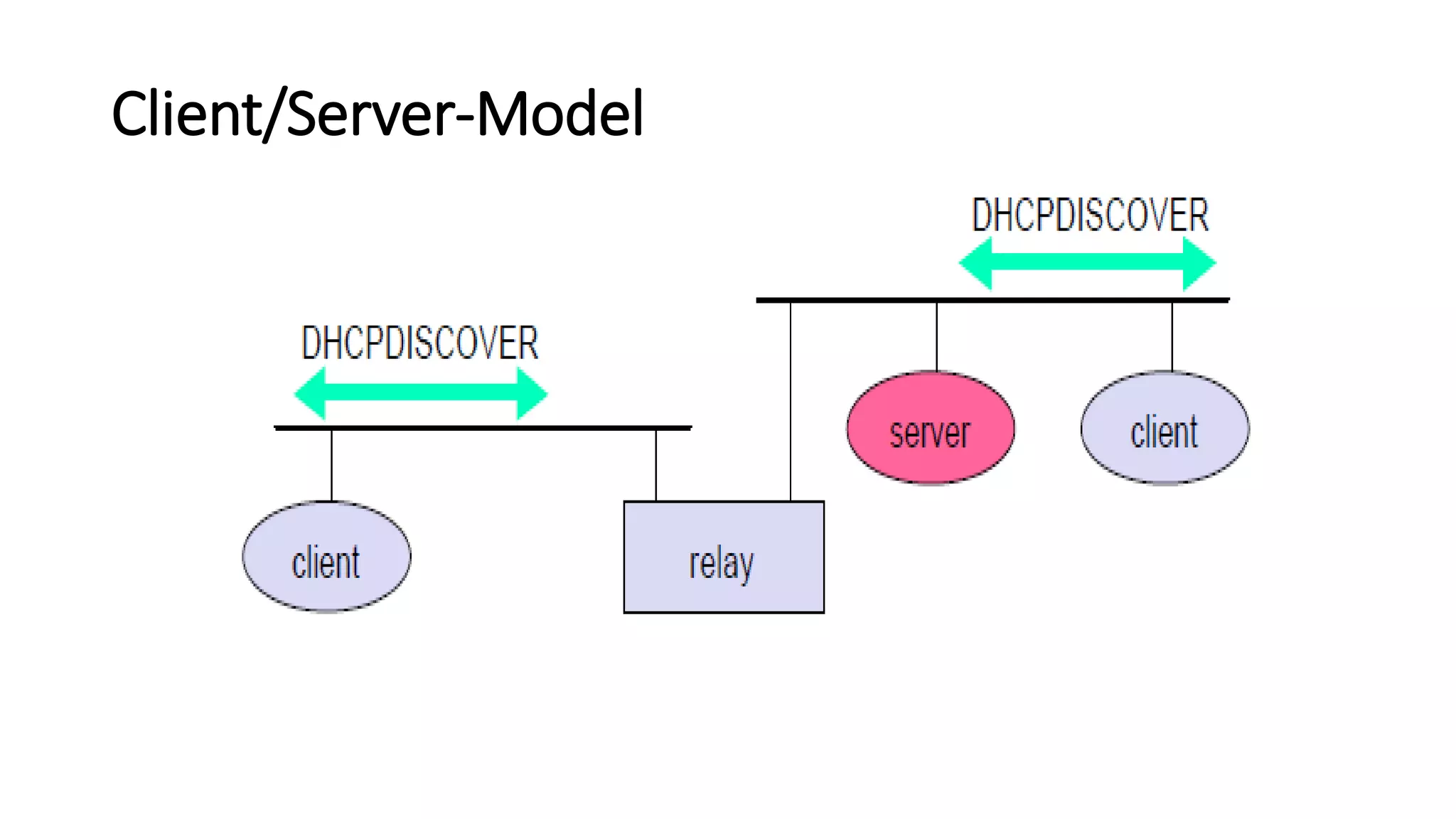
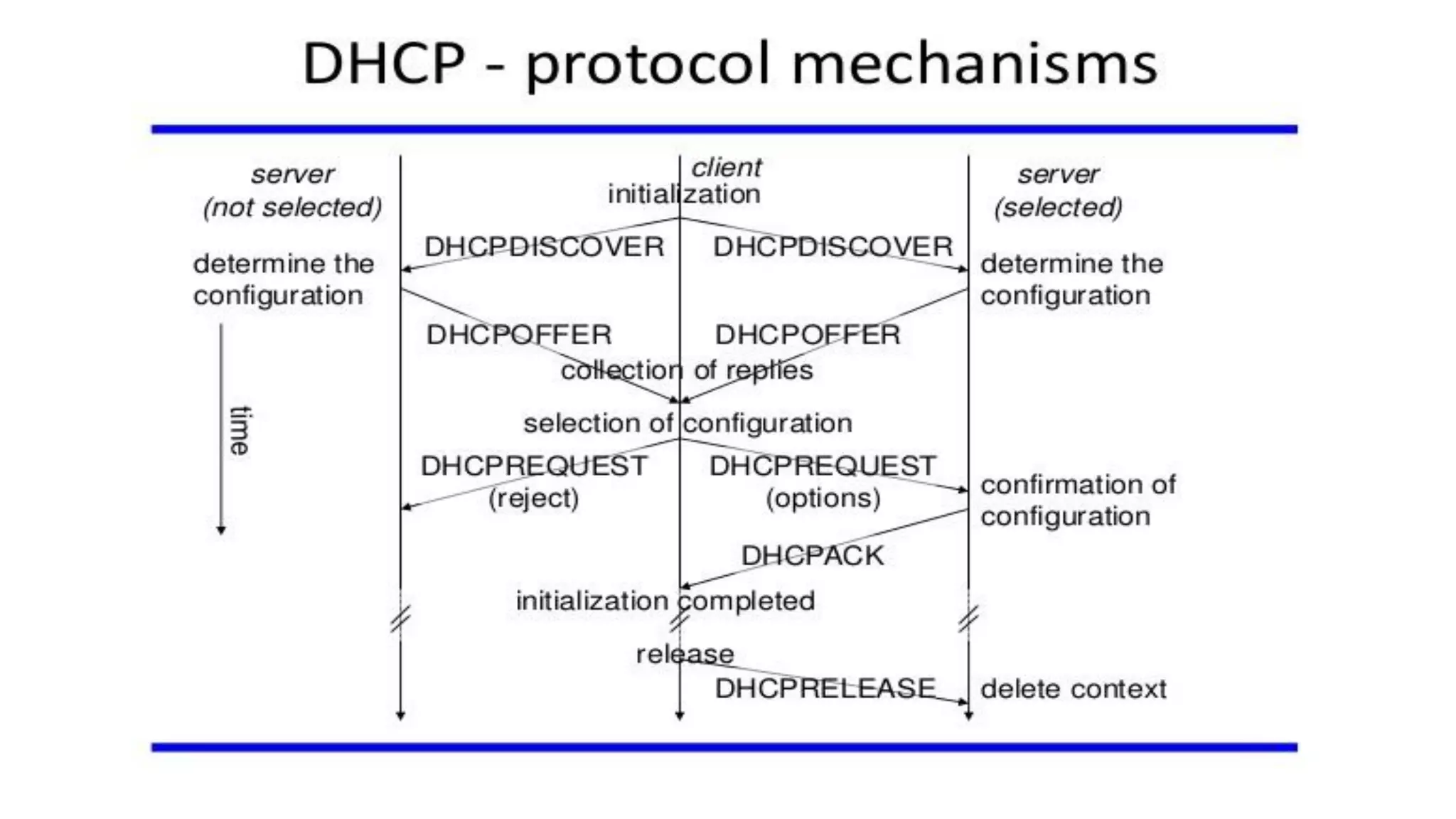
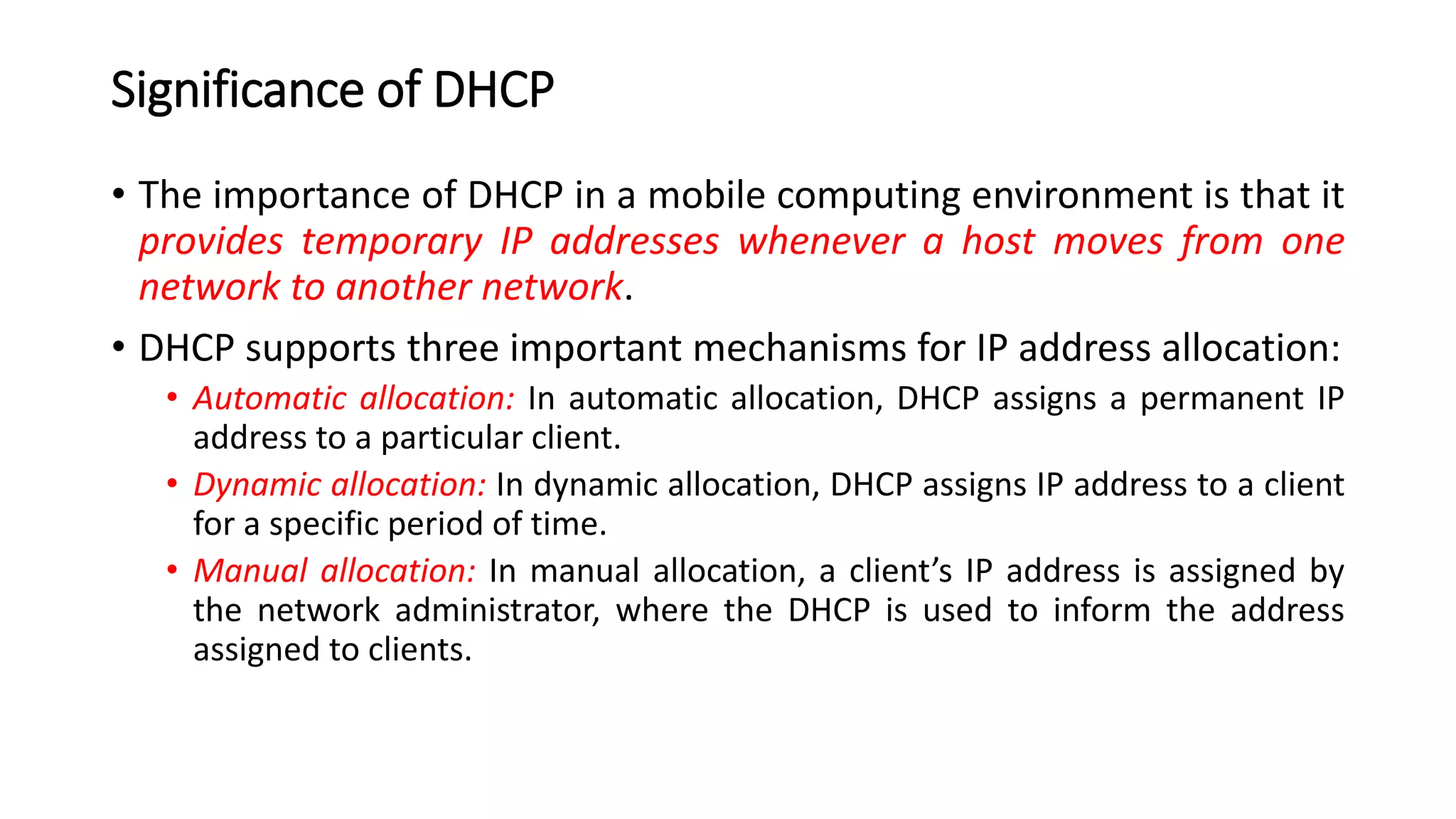
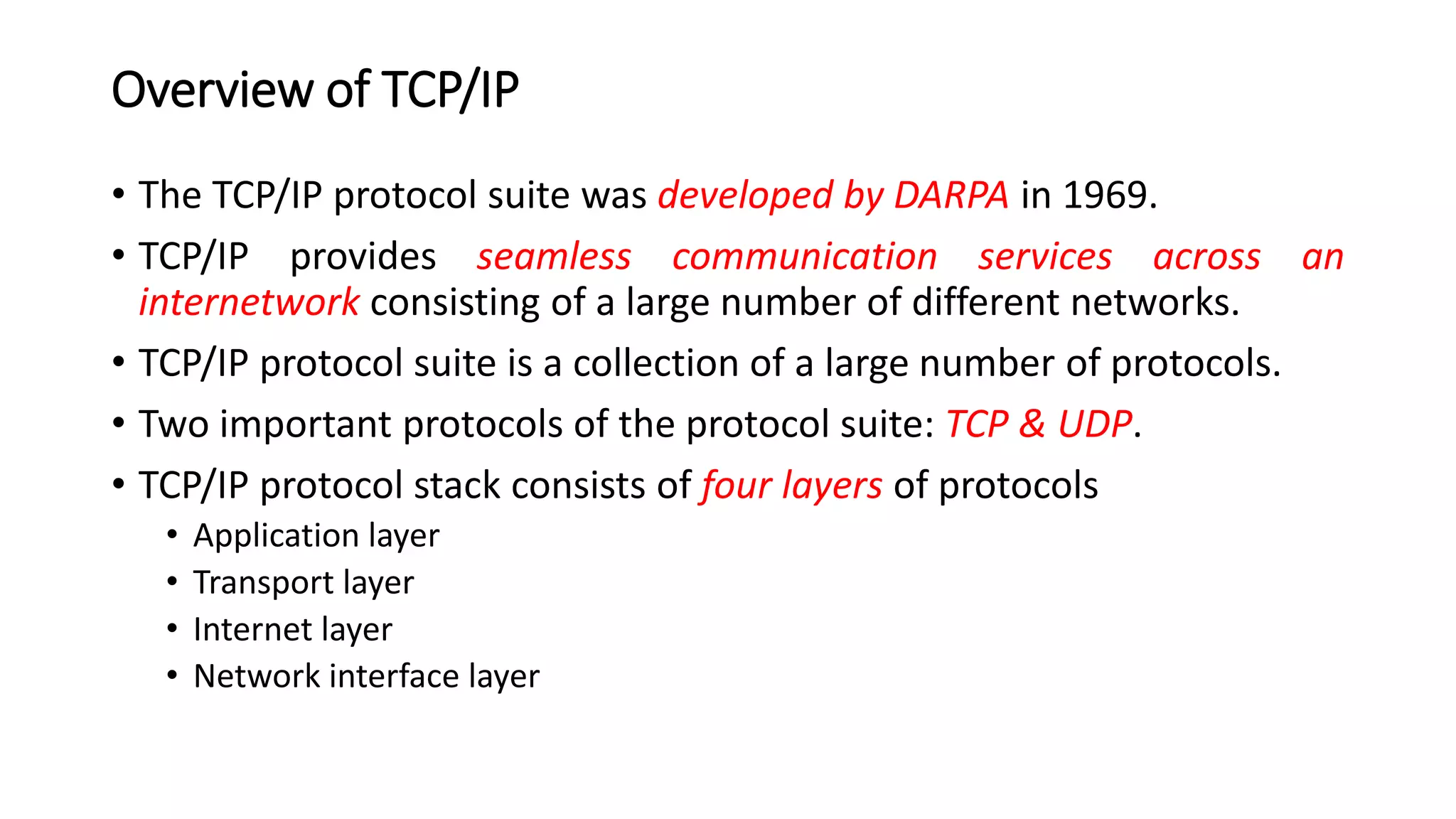
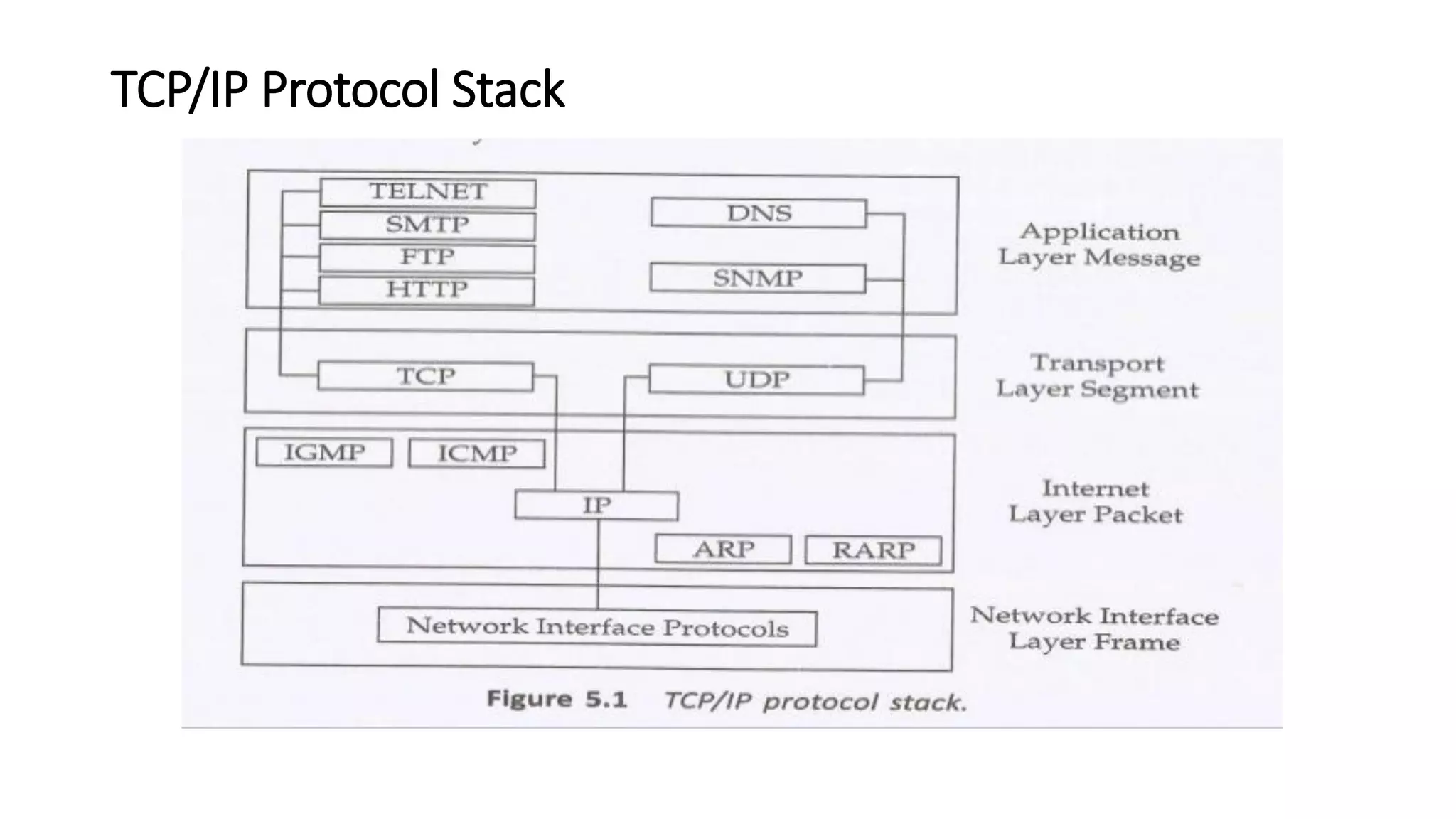
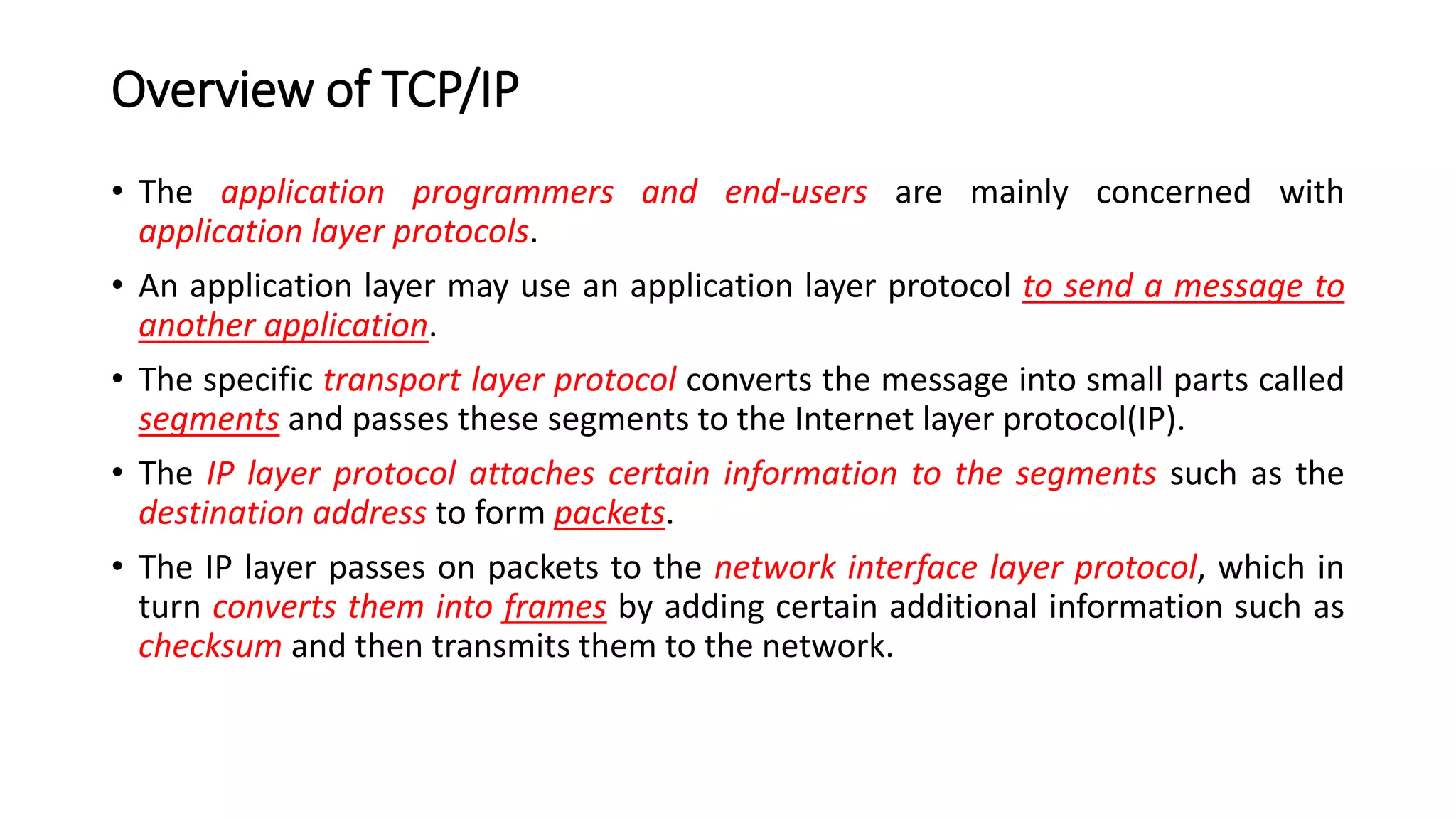
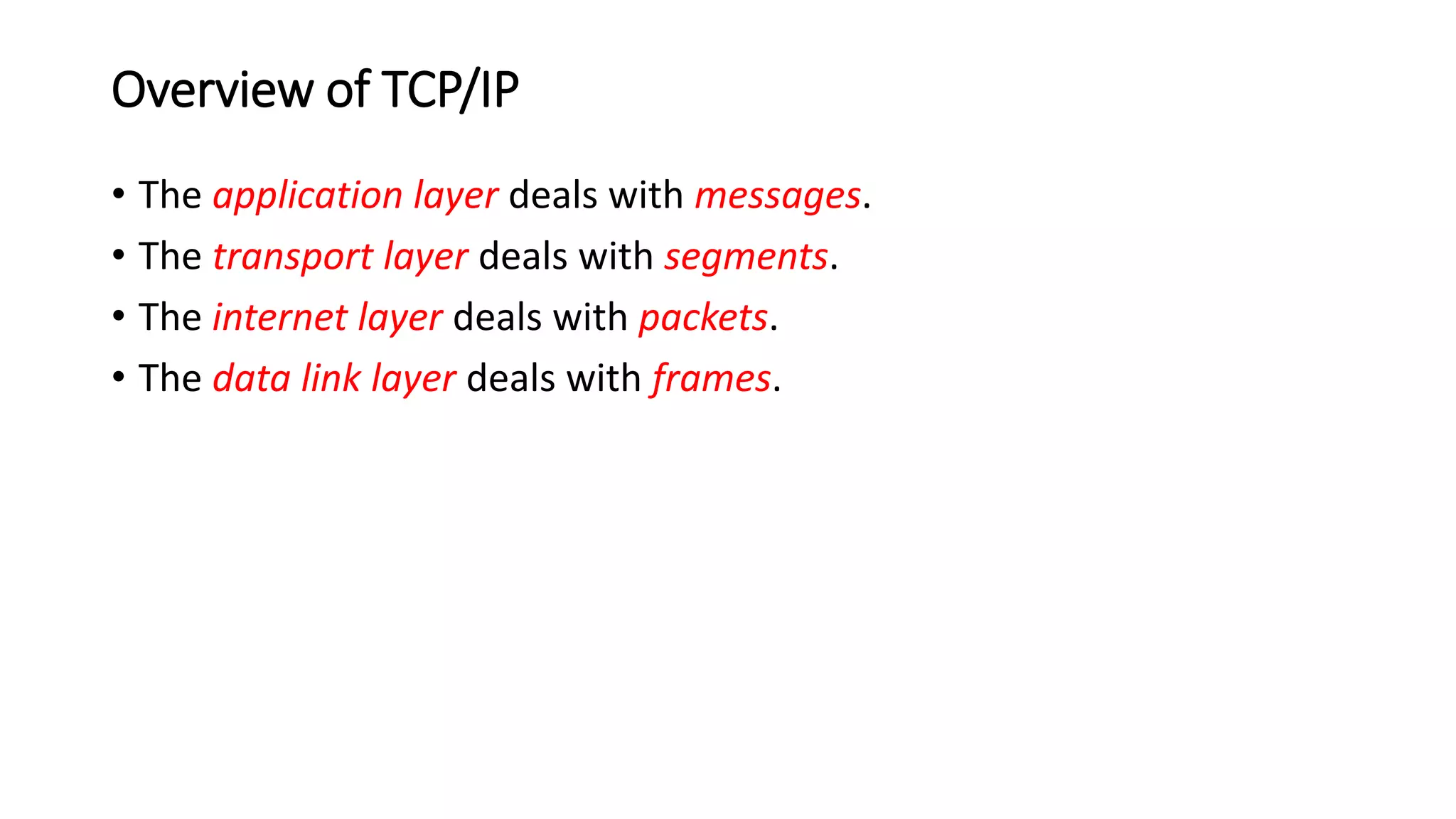
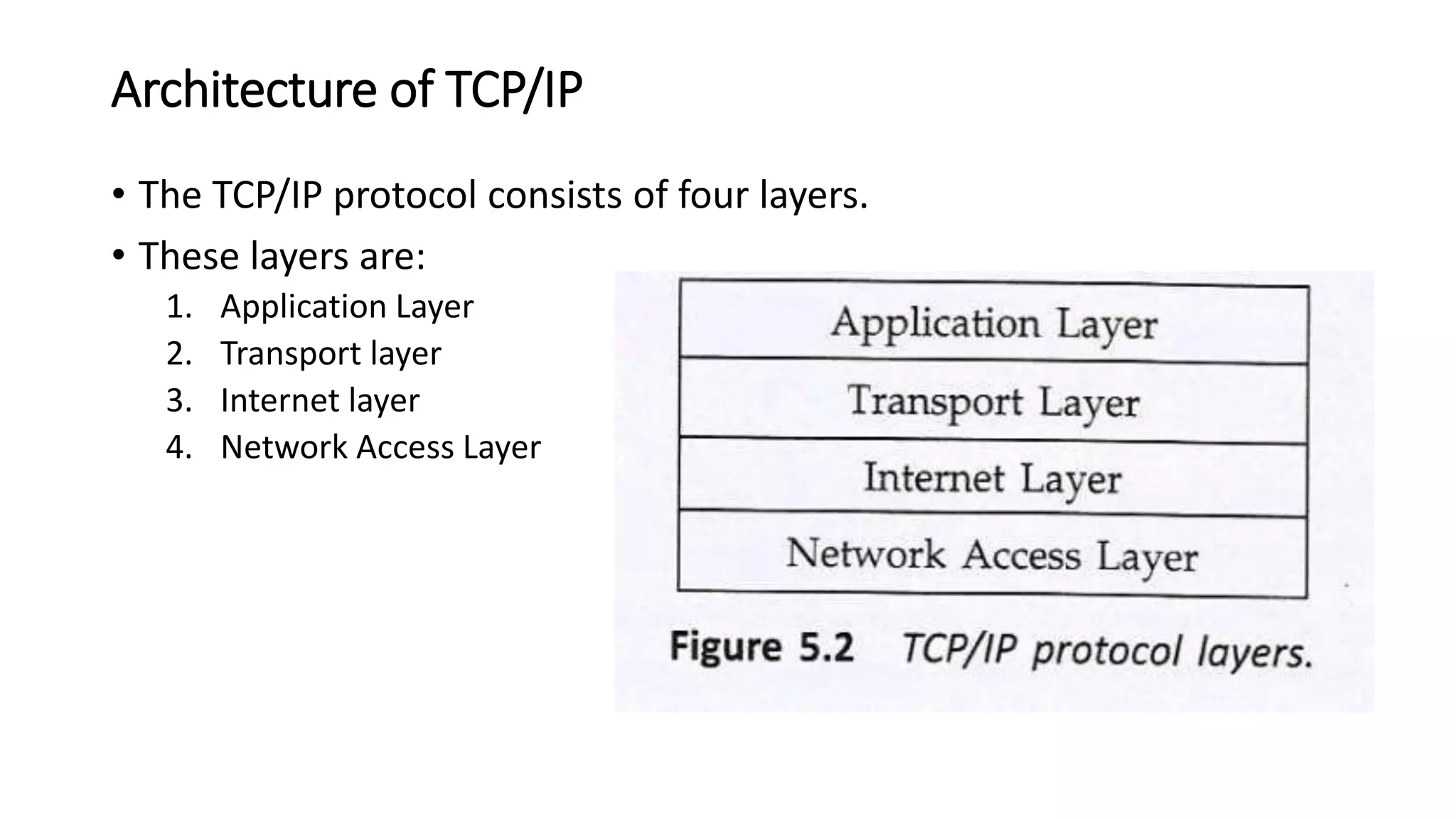
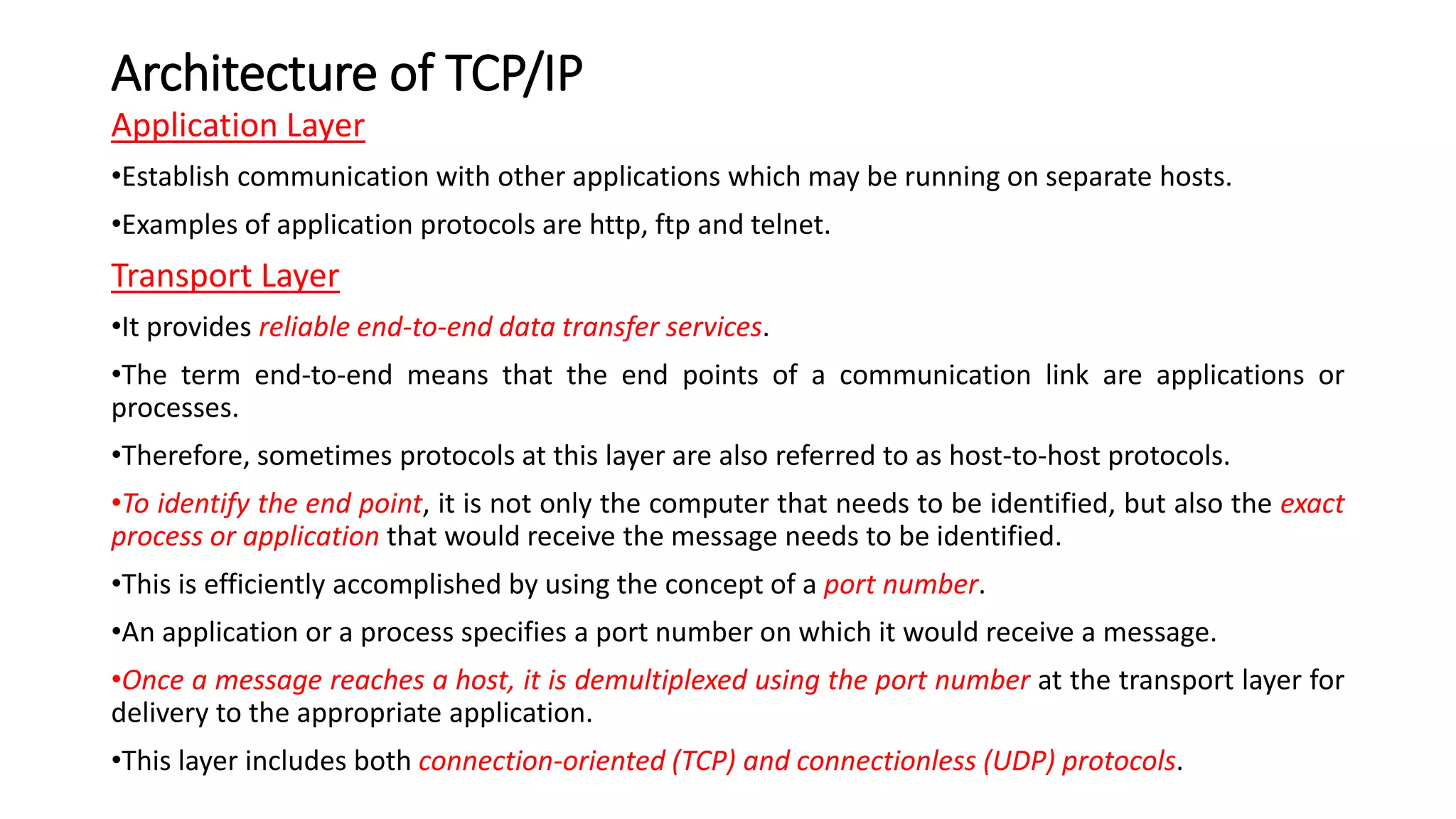
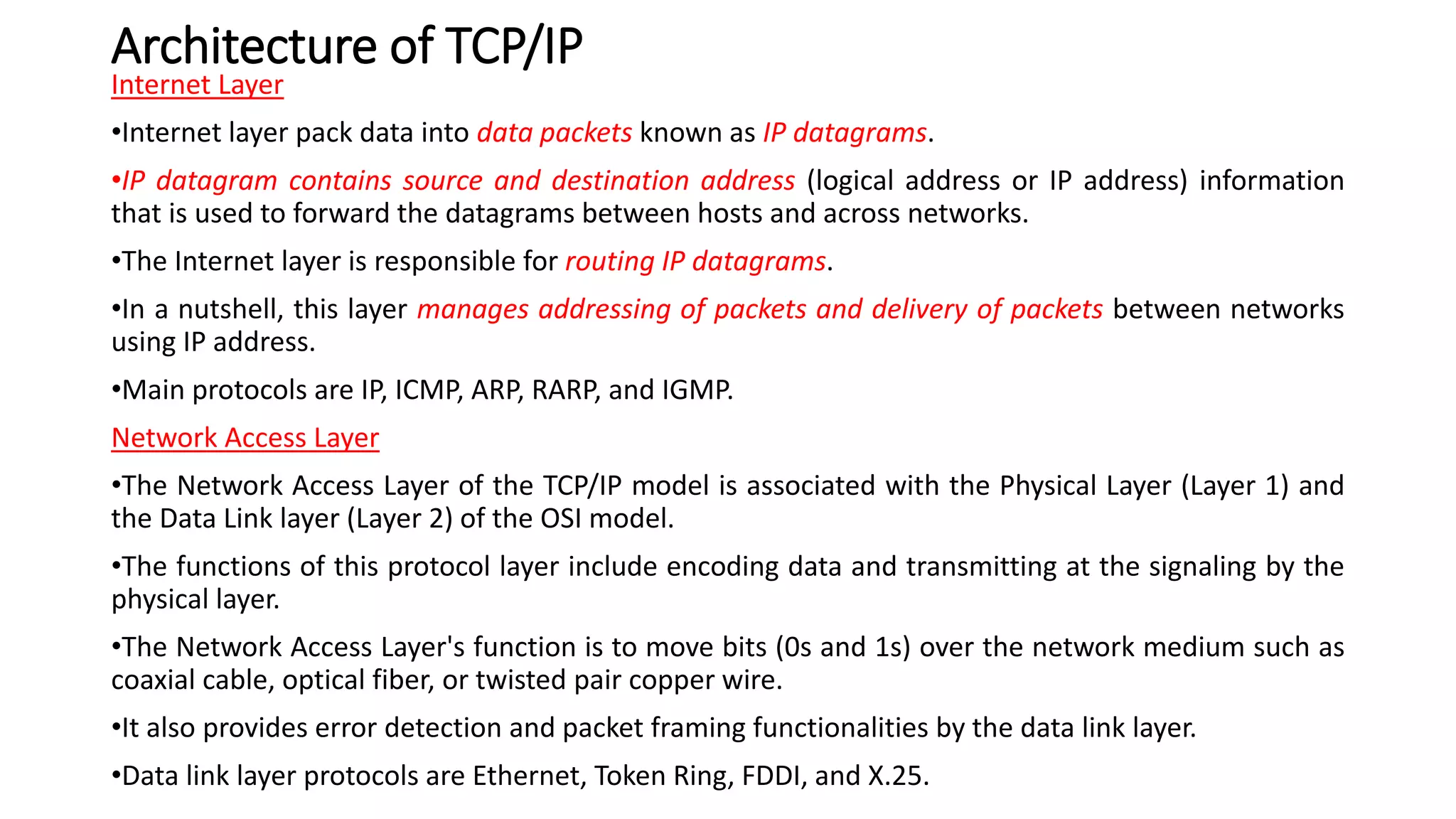
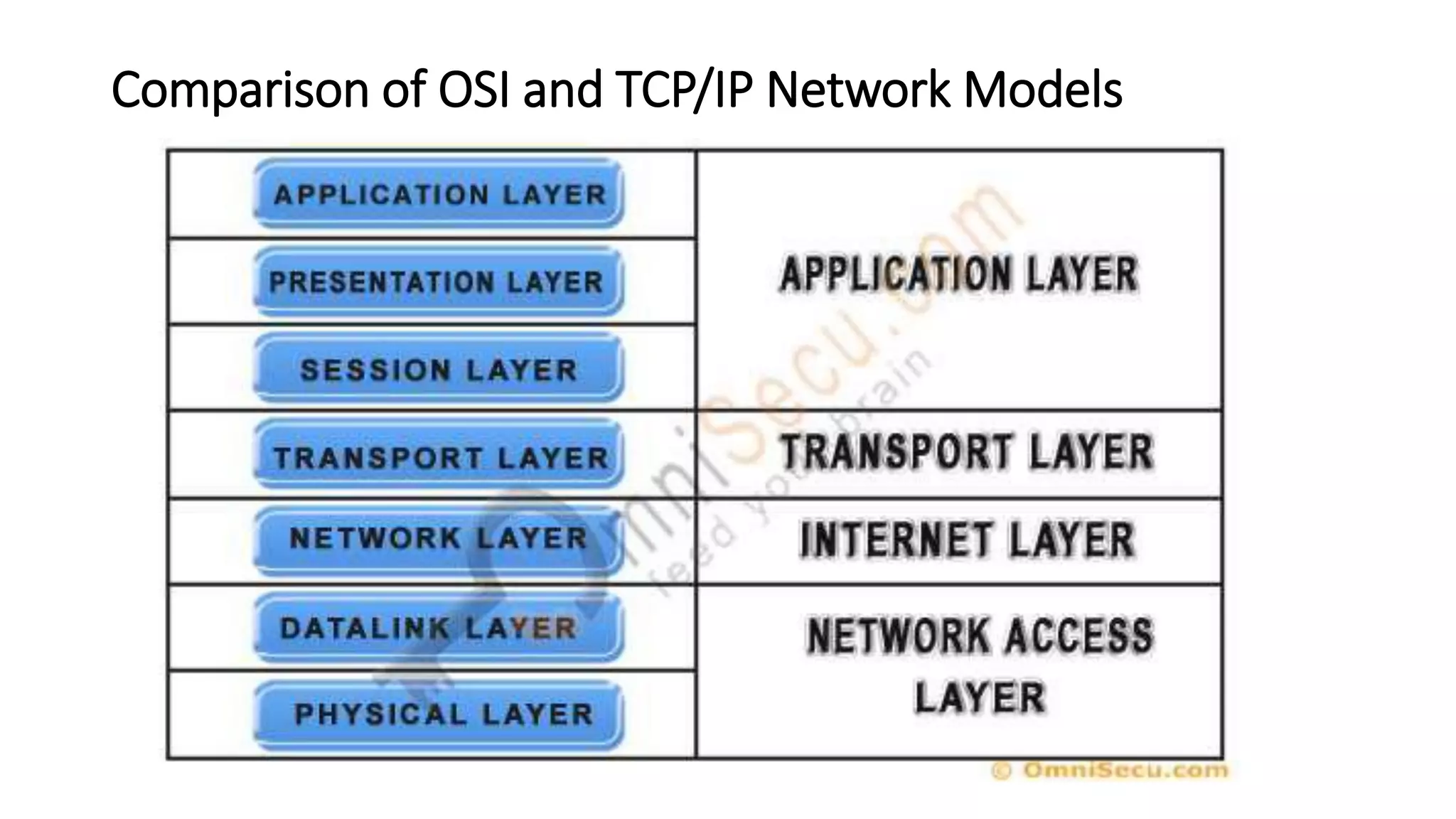
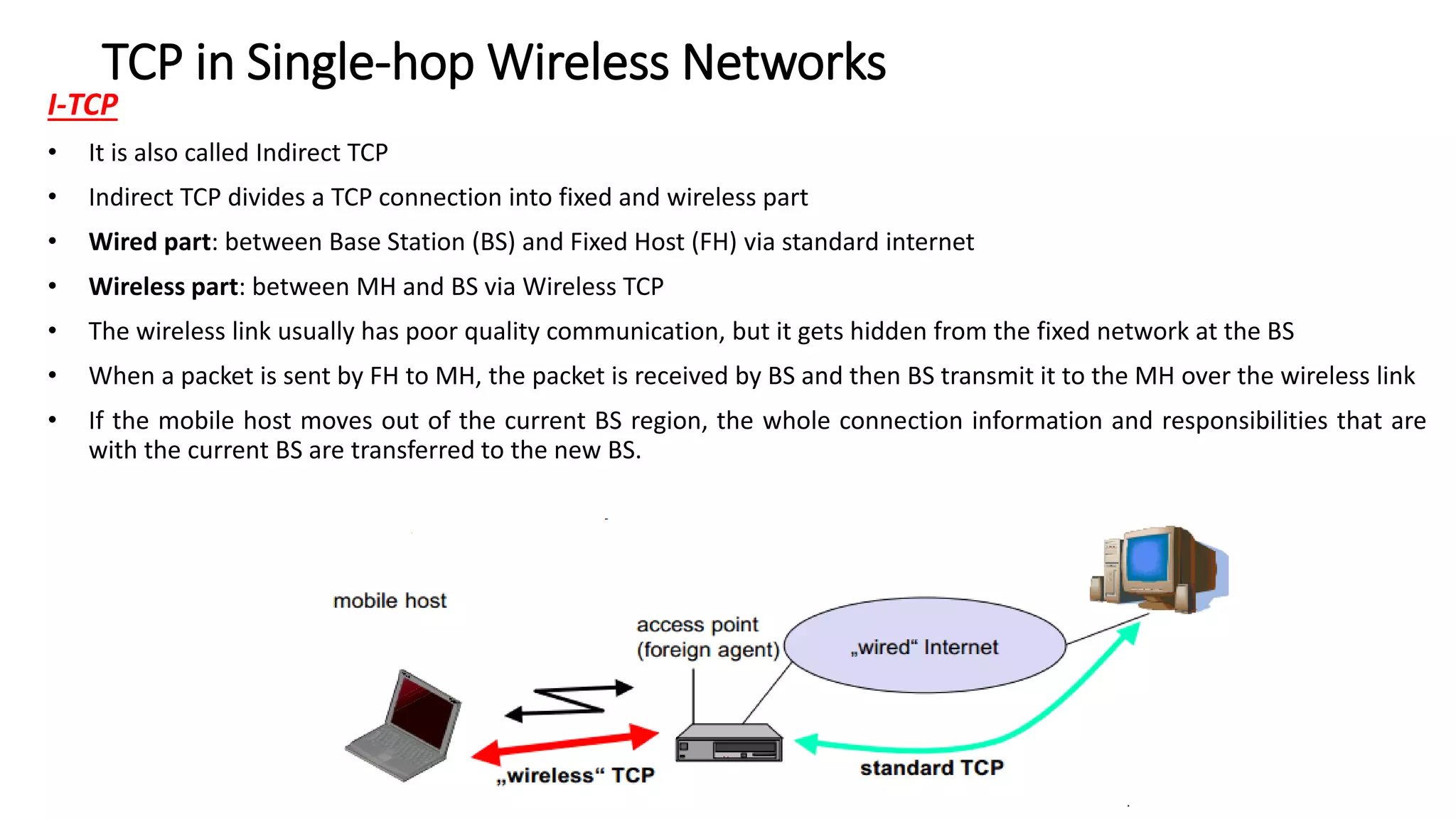
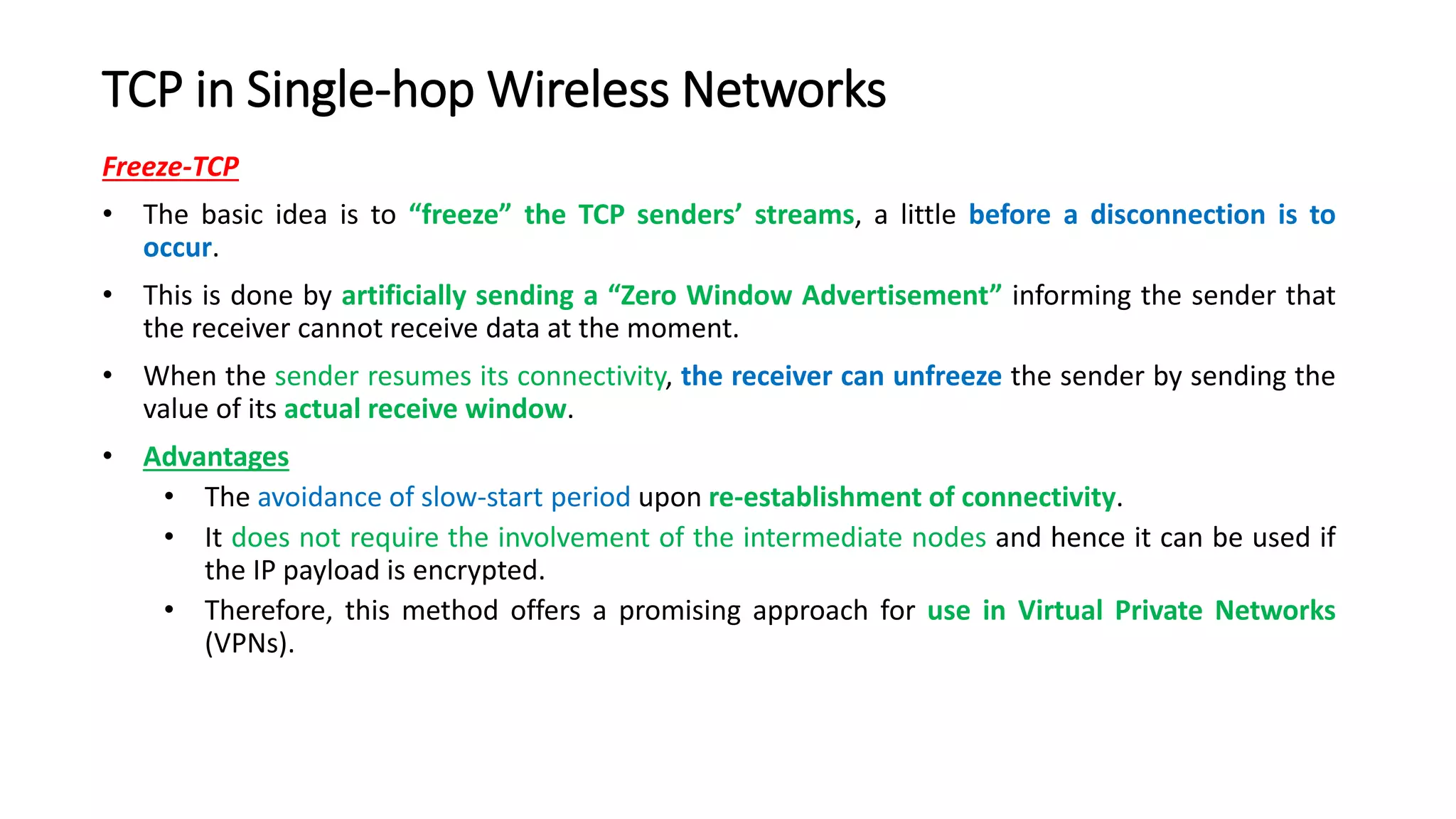
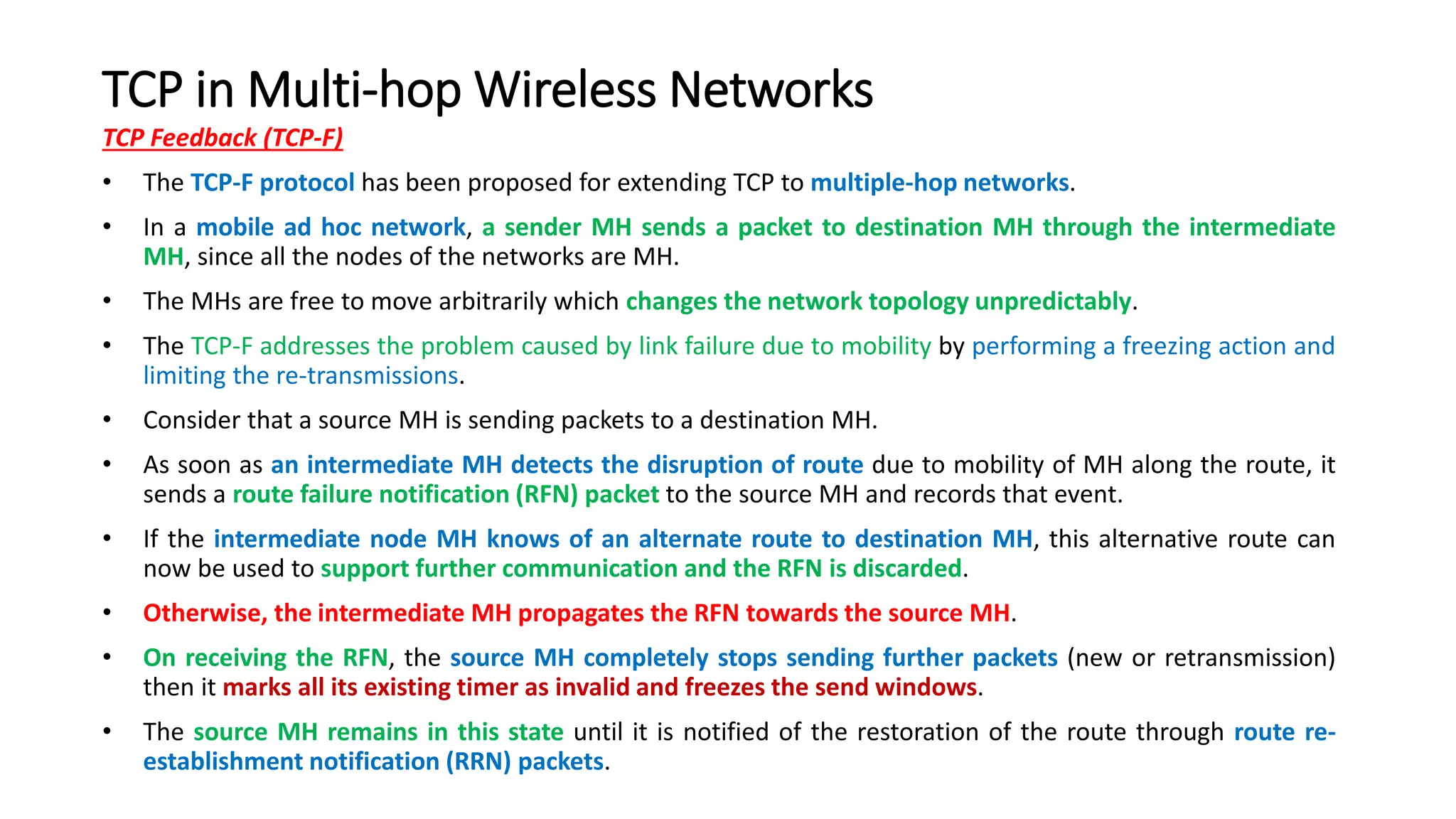
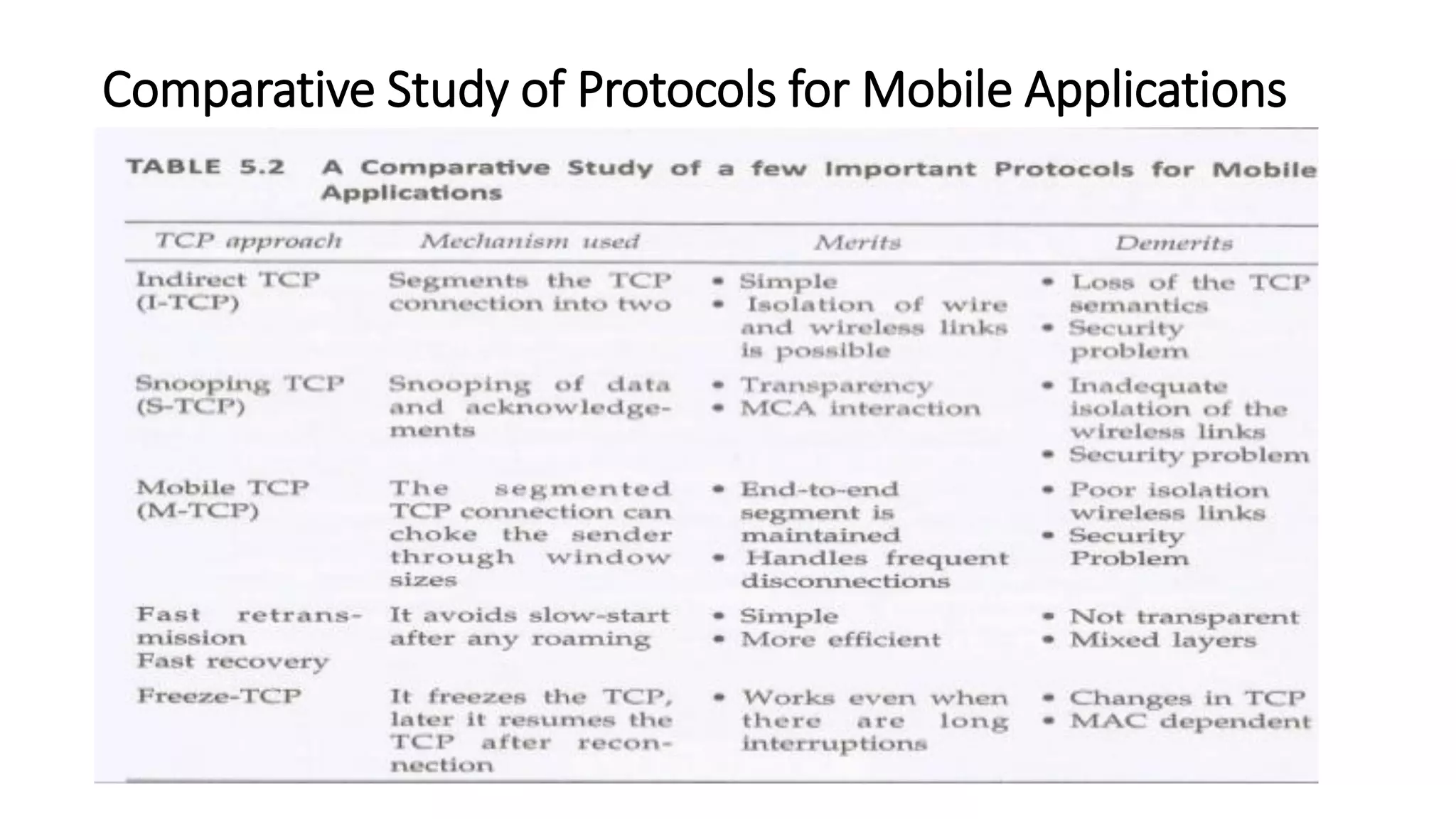
This document discusses Mobile IP and key concepts related to it. Mobile IP allows mobile devices to stay connected to the internet as they move between different networks. It extends the IP protocol to make mobility transparent to applications. The key mechanisms in Mobile IP are discovering a device's care-of-address in a foreign network, registering that address with the home agent, and tunneling packets to the device's current location using that care-of-address.