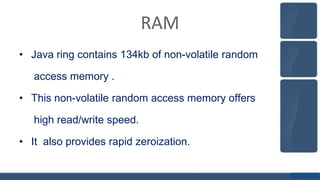
The Java Ring is a stainless steel wearable device that functions as a smartcard with built-in microprocessor capabilities for user authentication and data storage. It includes components like a Java Virtual Machine, memory, and a real-time clock, allowing it to serve applications such as secure financial transactions and access control. Despite its advantages in convenience and security, the Java Ring has high implementation costs and limited processing capacity.