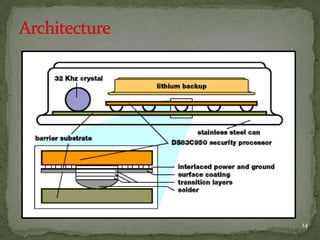
Java Ring is a stainless-steel ring that houses a microprocessor called an iButton, which contains 134KB RAM, 32KB ROM, and a Java virtual machine. It was introduced in 1998 to enable personalized services using information stored on the ring. Examples included a robot making coffee based on a user's preferences. While Java Rings are not widely used, similar wearable devices could be used for applications like automatically adjusting vehicle settings based on the driver's stored preferences.