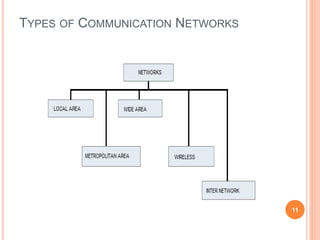
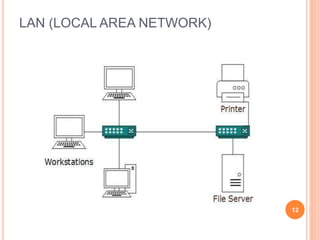
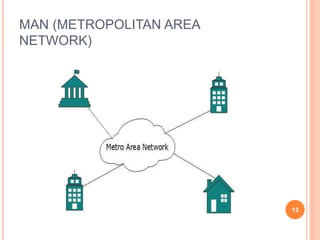
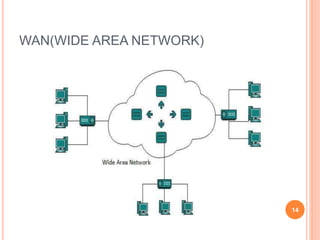
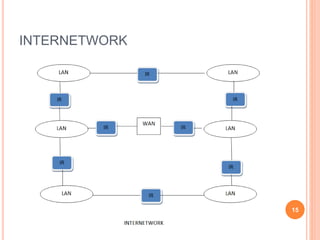
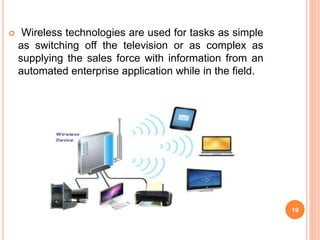
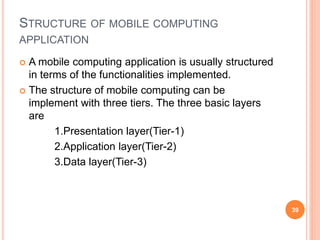
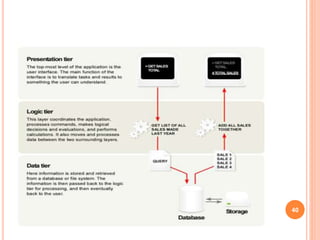
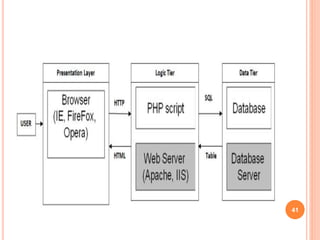
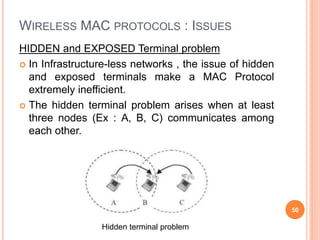
This document provides an introduction to mobile computing. It defines mobile computing as using a computer while on the move, involving mobility, computing, and network connectivity. The key aspects of mobile computing are discussed, including mobile communication infrastructure, software, hardware, and devices. Common network types that enable mobile computing like WLAN, MAN, WAN, and wireless networks are also summarized. The relationship between mobile computing and wireless networking is described, with wireless networking providing the basic communication capabilities. Examples of mobile computing applications are given for various fields.