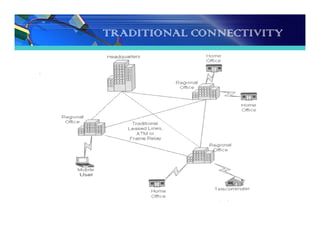
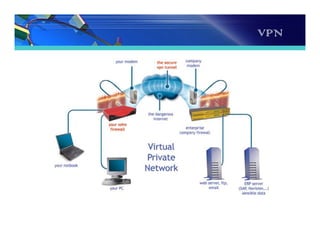
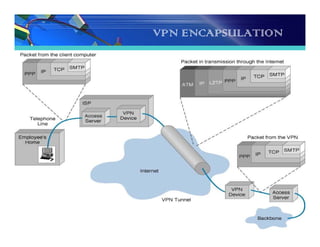
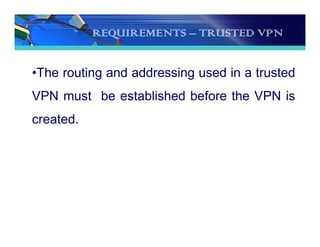
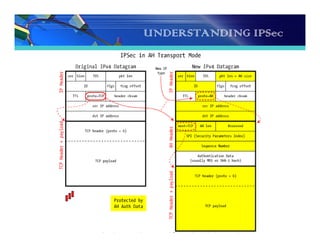
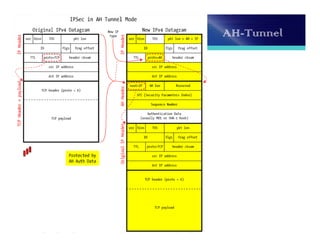
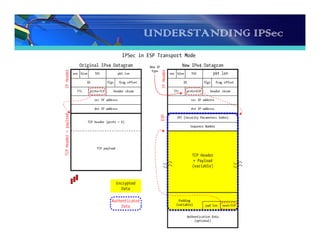
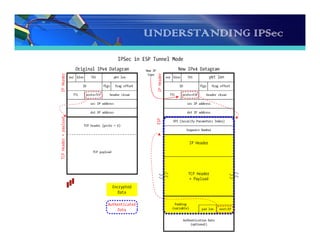
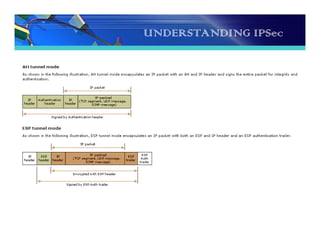
The document discusses the importance and functionality of Virtual Private Networks (VPNs), emphasizing their ability to securely connect geographically separated offices and mobile users over public networks. It outlines the benefits of VPNs, including improved security, cost reduction, and simplified network topology, while detailing the characteristics and different types of VPNs, such as trusted, secure, and hybrid. Additionally, it covers VPN protocols, encapsulation methods, and various technologies supported for implementing VPNs, particularly in Linux environments.