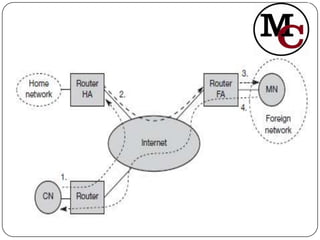
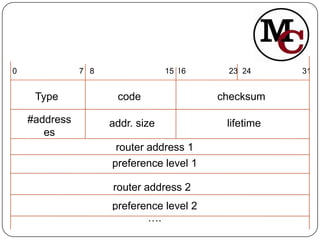
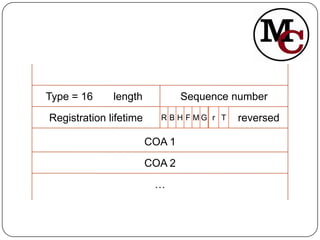
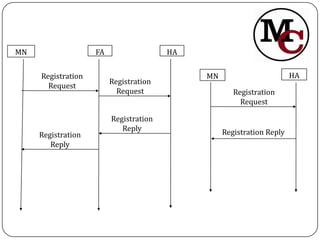
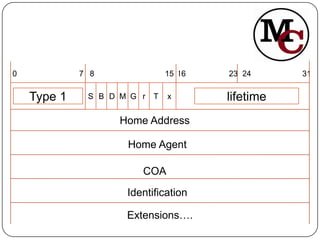
Mobile IP allows mobile nodes to change their point of attachment between IP networks while maintaining ongoing connections. It defines entities like mobile nodes, home agents, and foreign agents to facilitate IP packet delivery to the mobile node's current location. The key operations in Mobile IP are agent discovery, registration of the mobile node's new location with its home agent, and tunneling of packets from the home agent to the foreign agent or mobile node's care-of address.