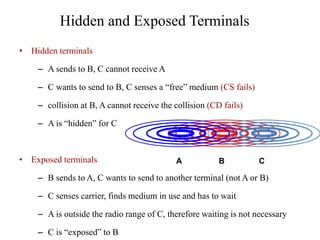
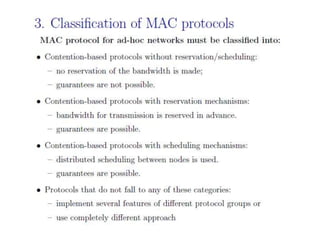
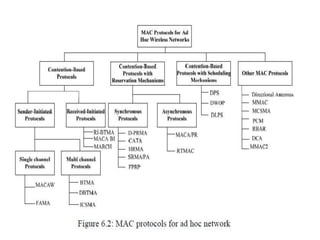
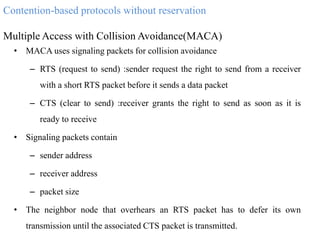
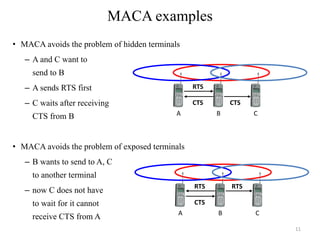
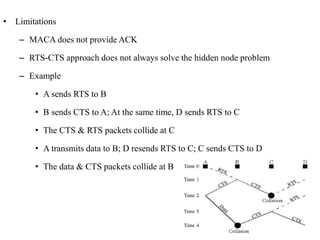
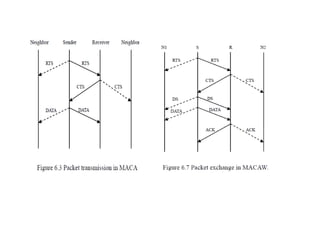
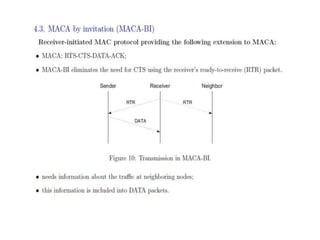
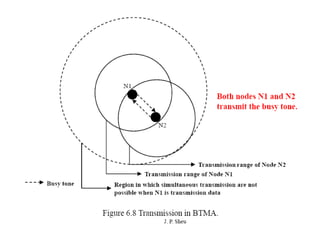
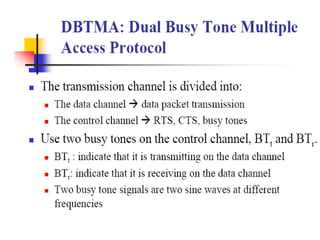
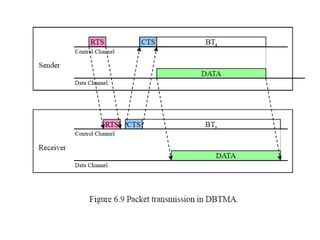
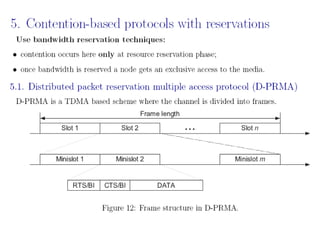
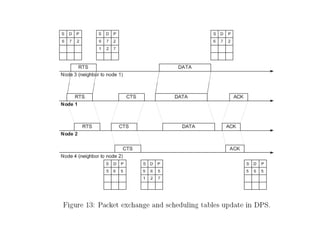
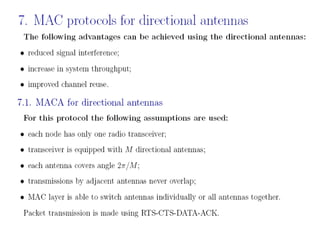
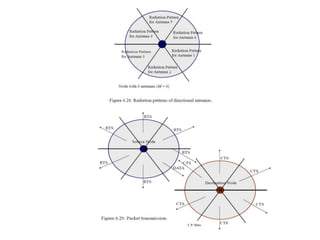
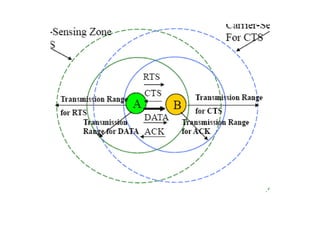
The document discusses several MAC protocols for ad hoc networks including MACA, MACAW, and PAMAS. MACA uses RTS and CTS packets to avoid collisions but does not provide ACK. MACAW is a revision of MACA that includes ACK. It significantly increases throughput but does not fully solve hidden and exposed terminal problems. PAMAS uses a separate signaling channel for RTS-CTS and a data channel. It allows nodes to power down transceivers when not transmitting to save energy.