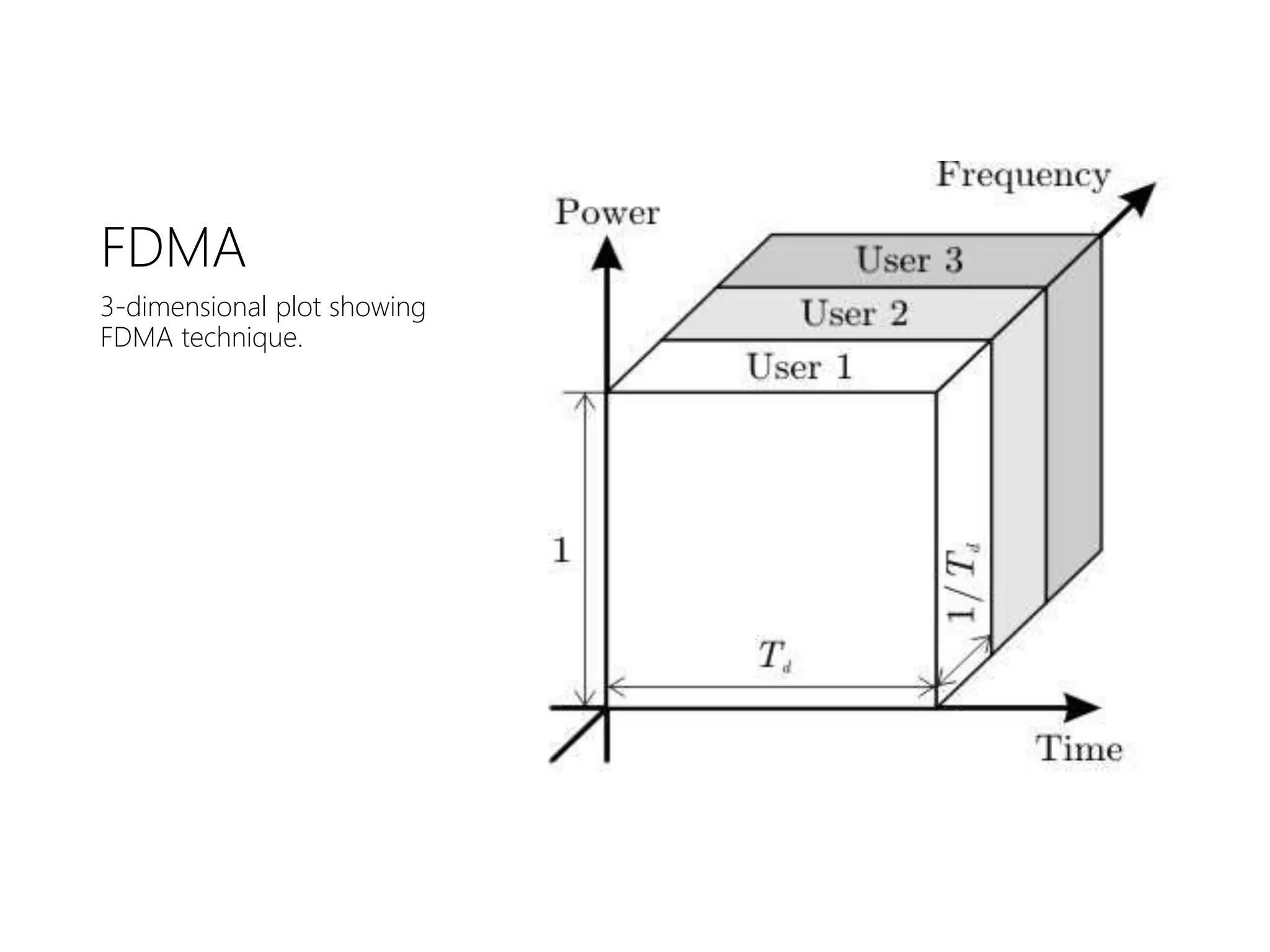
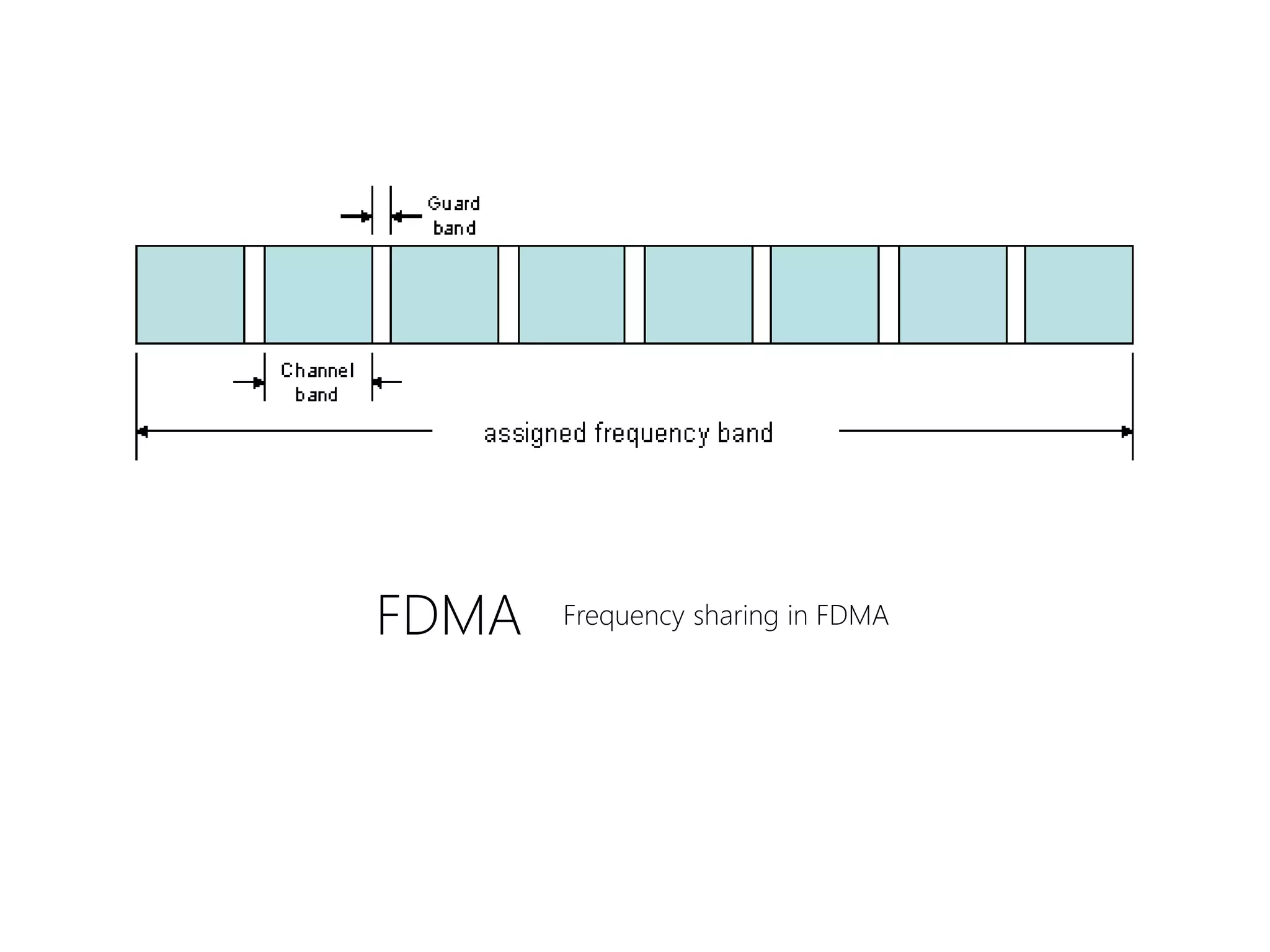
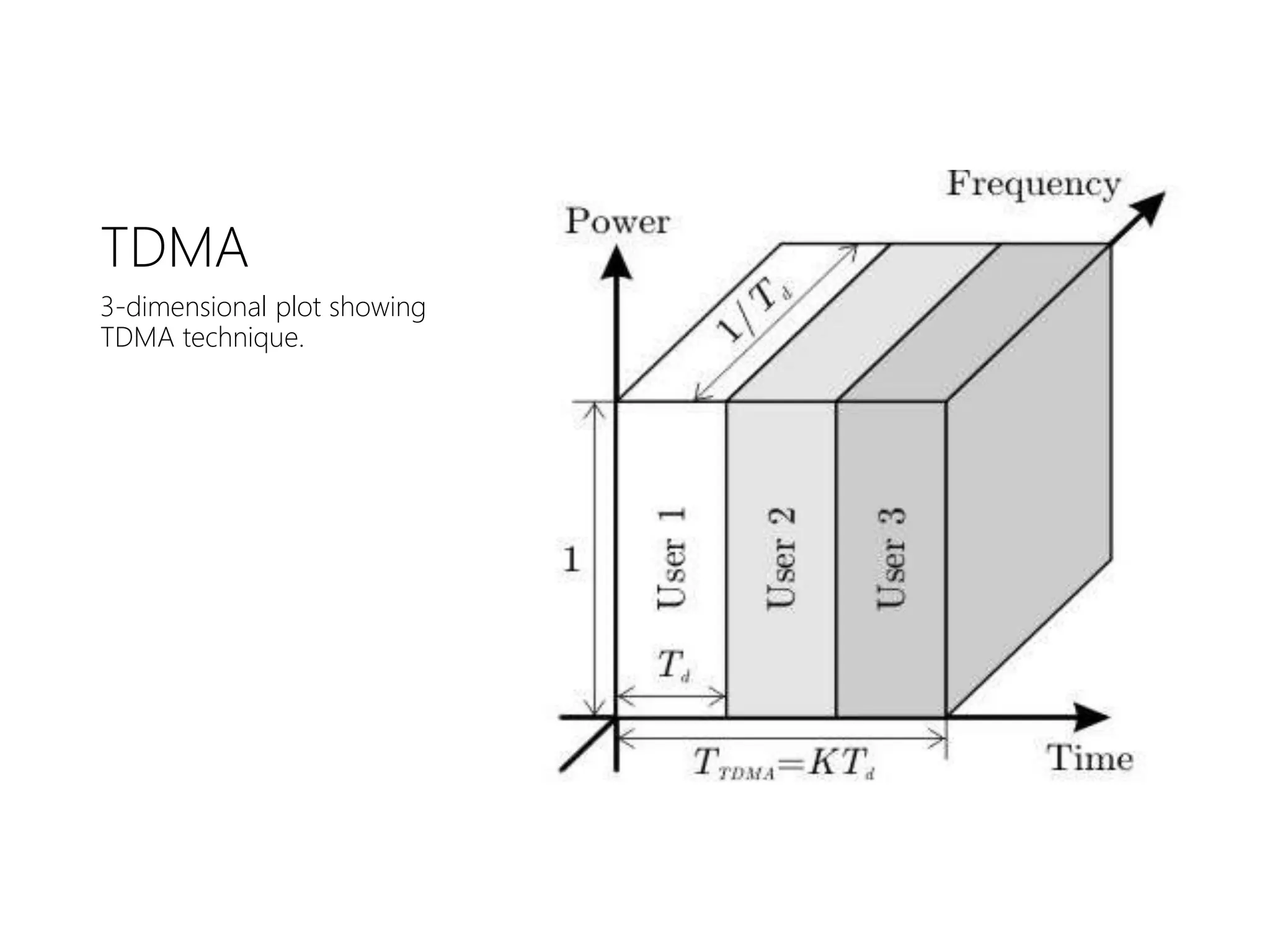
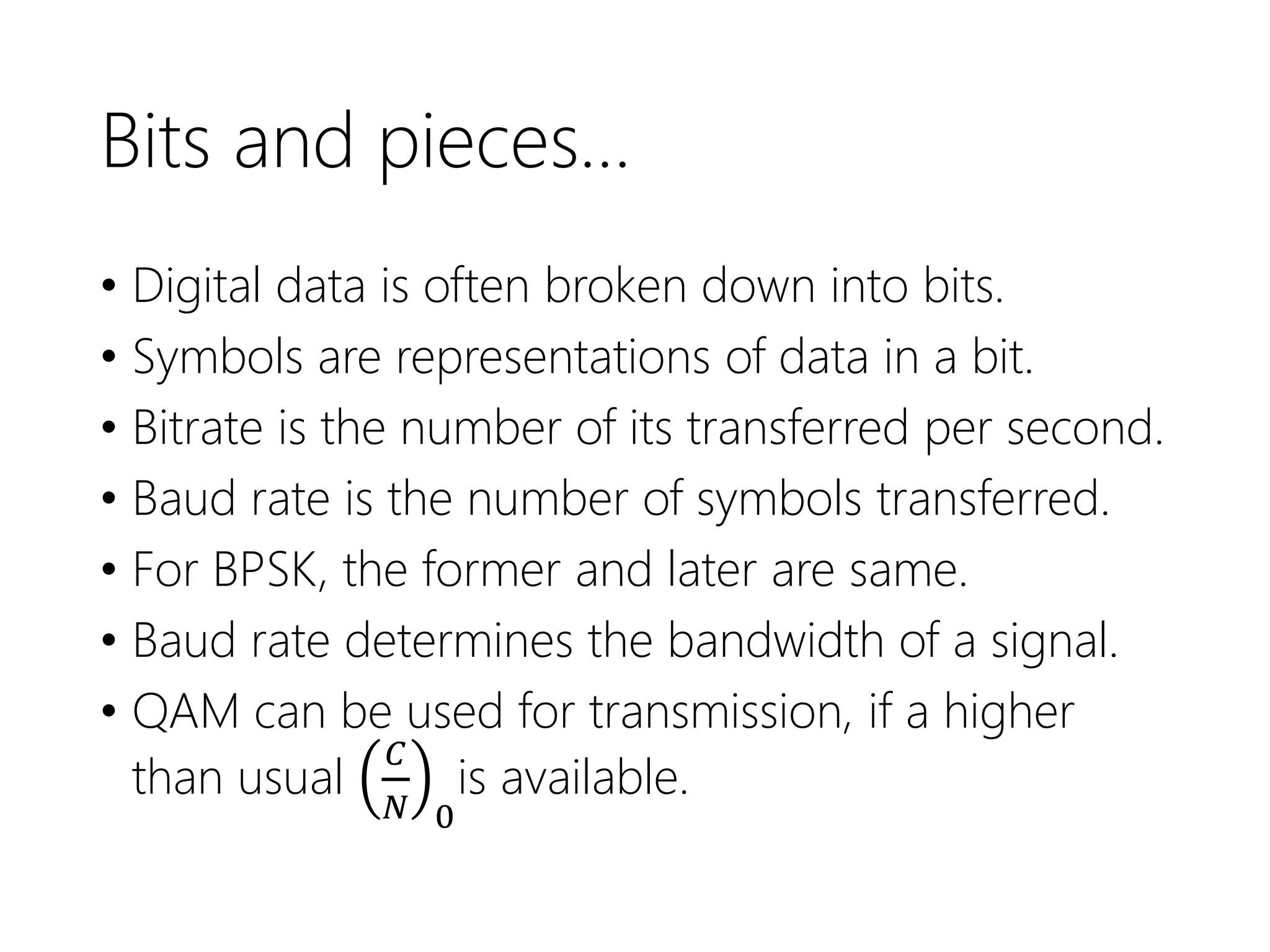
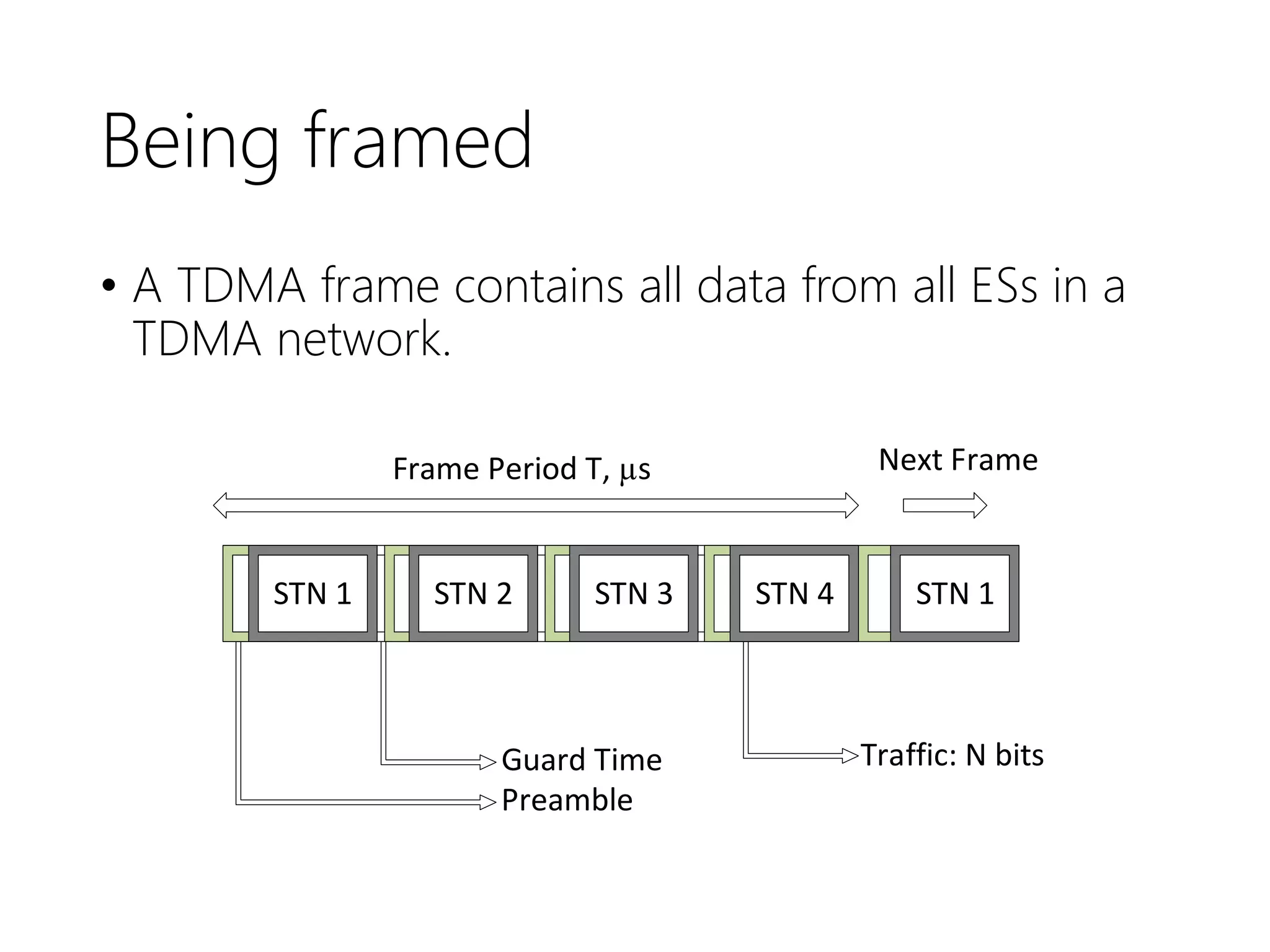
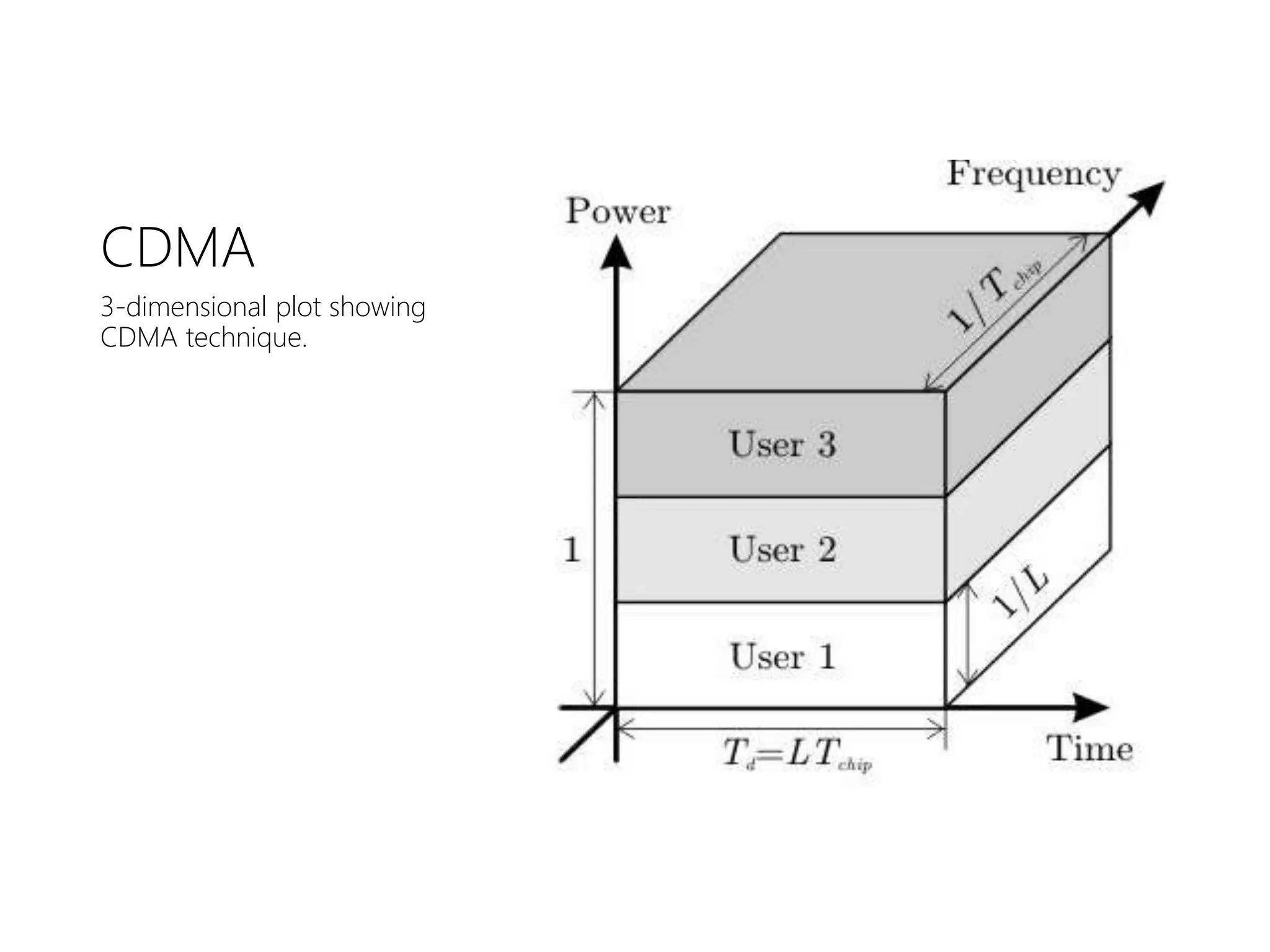
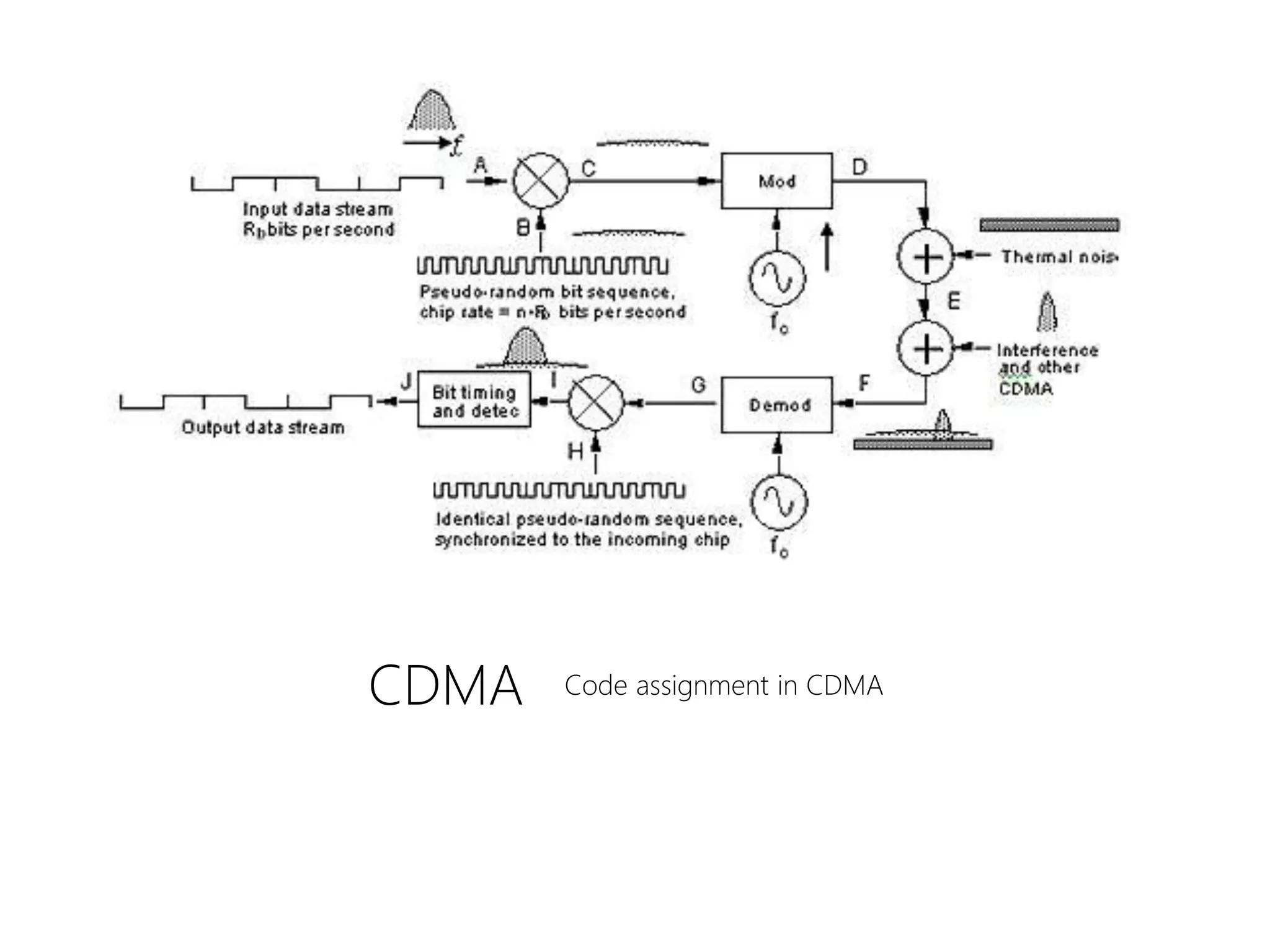
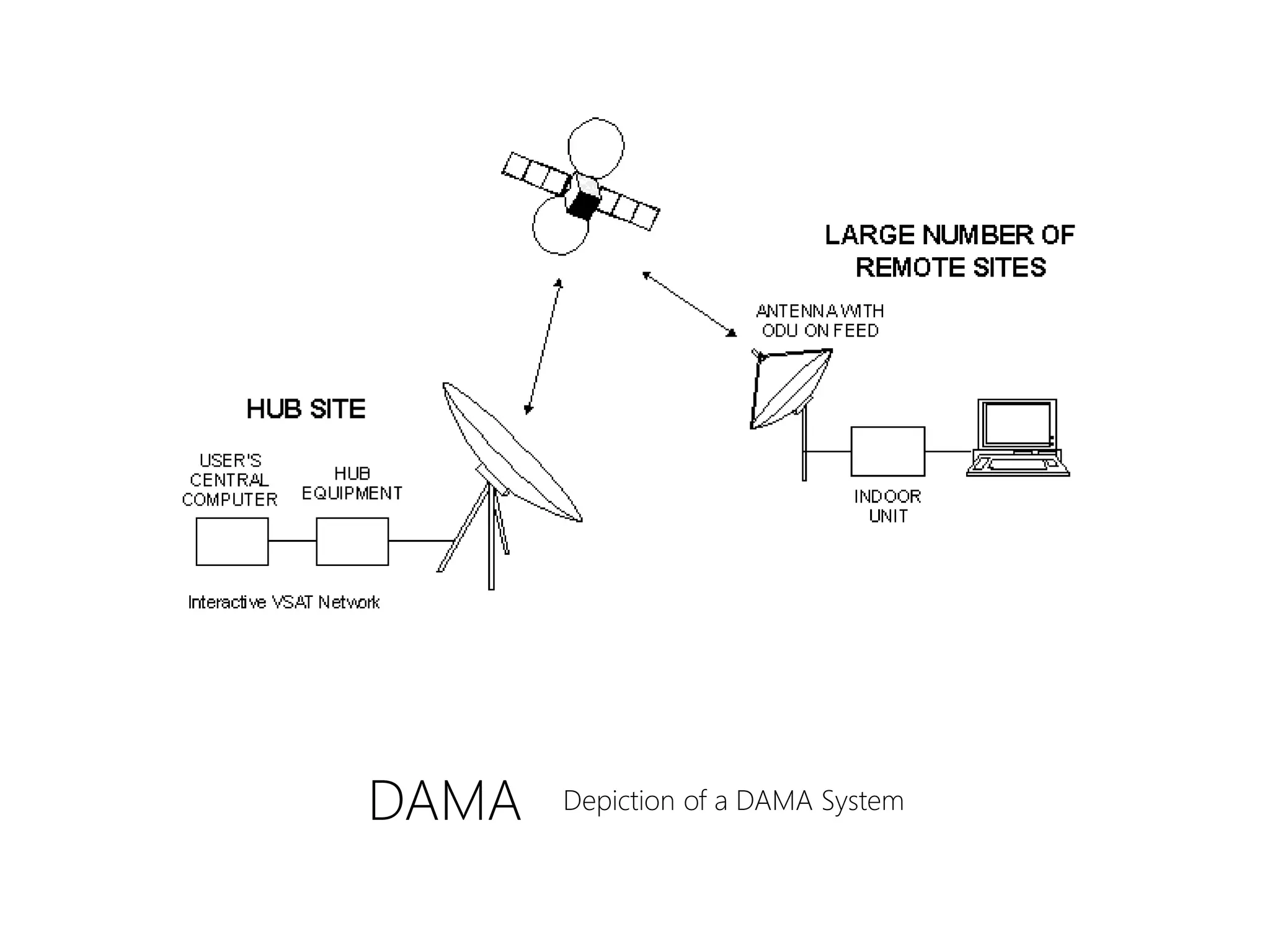
FDMA, TDMA, CDMA, and DAMA are multiple access techniques that allow multiple users to share access to a satellite for communication. FDMA divides the available bandwidth into different frequency channels. TDMA divides the bandwidth into different time slots. CDMA spreads each user's signal over the entire bandwidth using unique codes. DAMA dynamically assigns bandwidth according to demand rather than using pre-assigned blocks of time or frequency. These techniques allow efficient sharing of satellite bandwidth among multiple users.