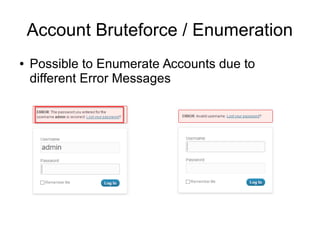
This document discusses securing a WordPress site. It begins with an agenda that includes understanding how WordPress works and its file structure, setting up WordPress, and configuring security settings. It then covers how WordPress functions through index.php and includes other files. It also discusses correlating files and folders. The document outlines setting up WordPress via FTP/SSH or SVN and hardening the server. It details common attack vectors like vulnerabilities in core, plugins, and themes as well as account brute forcing. It recommends customizing .htaccess rules and using child themes to modify functionality securely.















![HTACCESS
● Redirections
– RewriteCond %{REQUEST_URI} robots.txt
– RewriteRule ^abracadabra/ http://google.com
[R=301,L]
● Custom Directives
– DirectoryIndex index.html
– ServerSignature Off
– Header unset Etag](https://image.slidesharecdn.com/secureyourwordpress-140529004000-phpapp01/85/Secure-Your-Wordpress-16-320.jpg)