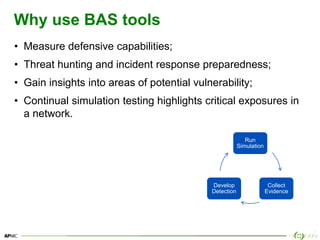
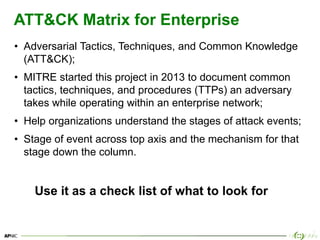
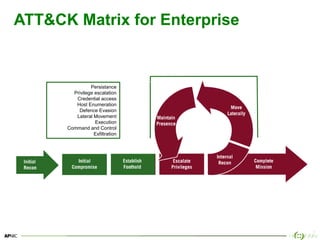
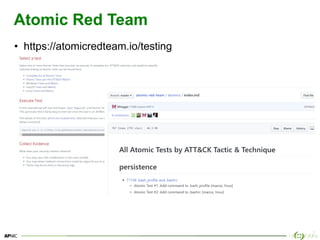
The document provides an overview of breach and attack simulation (BAS) tools, their significance in measuring defensive capabilities, and insights into potential vulnerabilities. It discusses modern defense strategies and highlights open-source tools like Infection Monkey, Metta, and Caldera for simulating adversarial activities. Additionally, it covers the MITRE ATT&CK framework and its relevance in understanding adversarial tactics, techniques, and procedures.




![7
What is Breach and Attack Simulation (BAS)
• Ability to simulate adversarial activities with some degree of
automation. [1]
• May be adversary model based, for example the
Adversarial Tactics, Techniques & Common Knowledge
(ATT&CK™) project. [2]](https://image.slidesharecdn.com/breachandattacksimulationtoolsusingpresentationtemplate4x3green01-190429061218/85/Breach-and-attack-simulation-tools-7-320.jpg)











![23
Metta [Installation]
1. sudo apt-get update && apt-get install -y build-essential
2. sudo apt-get install -y redis-server git python-pip screen python-yaml
libcurl3 dkms wget
3. cd ~/Downloads
4. wget -O https://download.virtualbox.org/virtualbox/6.0.4/virtualbox-
6.0_6.0.4-128413~Ubuntu~xenial_amd64.deb
5. sudo dpkg -i virtualbox-6.0_6.0.4-128413~Ubuntu~xenial_amd64.deb
6. sudo -H pip install --user pipenv
7. git clone https://github.com/uber-common/metta.git /home/apnic/metta
8. cd /home/apnic/metta
9. sudo apt-get install -y virtualenv
10.virtualenv metta
11.source metta/bin/activate
12.pip install -r requirements.txt
https://github.com/uber-common/metta](https://image.slidesharecdn.com/breachandattacksimulationtoolsusingpresentationtemplate4x3green01-190429061218/85/Breach-and-attack-simulation-tools-23-320.jpg)
![24
Metta [Installation]
1. cd ~/Downloads
2. wget -O https://releases.hashicorp.com/vagrant/2.2.3/vagrant_2.2.3_x86_64.deb
3. sudo dpkg -i vagrant_2.0.0_x86_64.deb
4. cd /home/apnic/metta
5. vagrant init StefanScherer/windows_10
6. vagrant up
7. sudo pip install requests
8. pip install celery
9. pip install redis
https://github.com/uber-common/metta](https://image.slidesharecdn.com/breachandattacksimulationtoolsusingpresentationtemplate4x3green01-190429061218/85/Breach-and-attack-simulation-tools-24-320.jpg)
![25
Metta [Starting]
# Open a new terminal and confirm redis is running
cd metta
redis-server
# Open a new terminal and start the celery shell script
cd metta
virtualenv metta
source metta/bin/activate
pip install -r requirements.txt
./start_vagrant_celery.sh
# Open a new terminal and start vagrant
cd metta
vagrant up
# Open a new terminal and start simulation
cd metta
python run_simulation_yaml.py -f MITRE/Adversarial_Simulation/ontarget_recon.yml
https://github.com/uber-common/metta](https://image.slidesharecdn.com/breachandattacksimulationtoolsusingpresentationtemplate4x3green01-190429061218/85/Breach-and-attack-simulation-tools-25-320.jpg)



![33
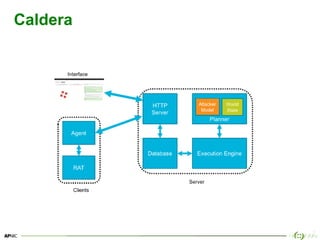
Caldera [Installation]
1. docker-ce --version
2. docker-compose --version
3. sudo apt-get update
4. sudo git clone https://github.com/mitre/caldera
5. cd caldera
6. sudo chown -R `whoami`:docker ./caldera/conf
7. cd caldera
8. sudo docker-compose up
# open a web browser
• https://localhost:8888
https://github.com/mitre/caldera](https://image.slidesharecdn.com/breachandattacksimulationtoolsusingpresentationtemplate4x3green01-190429061218/85/Breach-and-attack-simulation-tools-33-320.jpg)