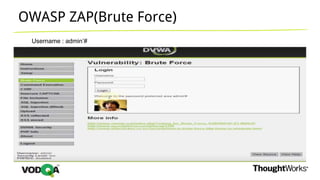
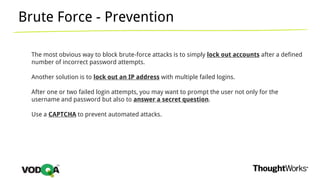
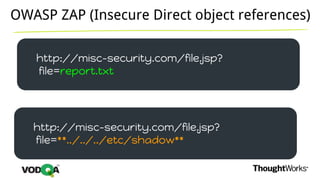
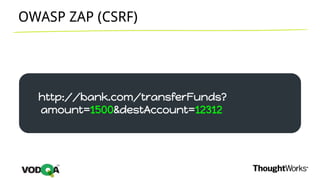
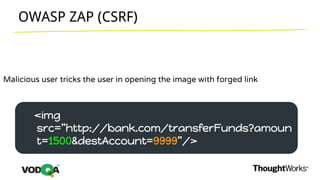
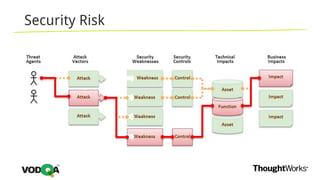
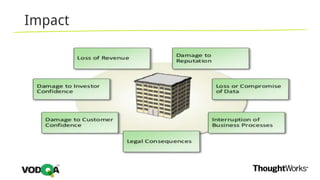
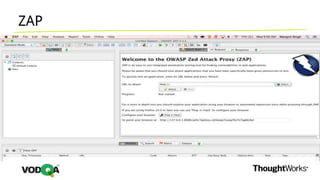
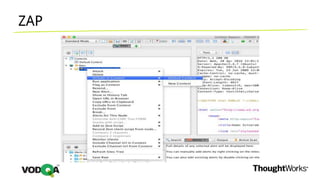
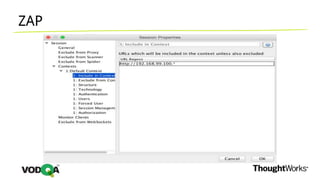
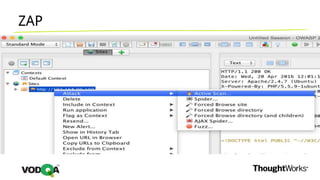
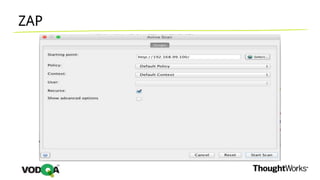
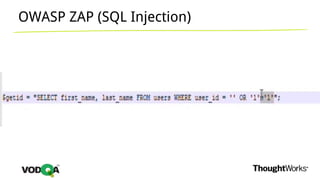
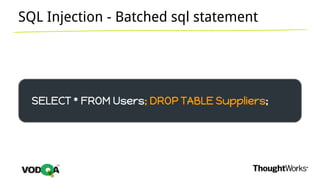
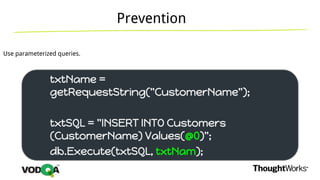
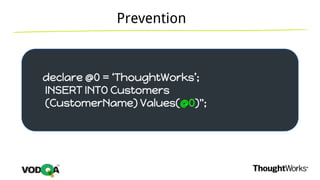
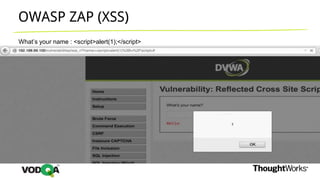
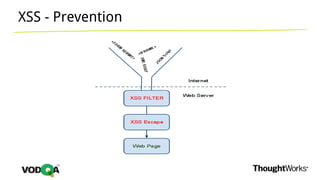
This document introduces security testing using OWASP ZAP (Zed Attack Proxy). It discusses the OWASP Top 10 security risks including injection, XSS, command injection, brute force attacks, insecure direct object references, and CSRF. It demonstrates how ZAP can be used to test for these vulnerabilities on a sample application. Prevention techniques are also provided for each risk, such as parameterized queries, output encoding, access control, account lockouts, and CSRF tokens.












![OWASP ZAP (Command Execution)
int main(char* argc, char** argv) {
char cmd[CMD_MAX] = "/usr/bin/cat ";
strcat(cmd, argv[1]);
system(cmd);
}](https://image.slidesharecdn.com/aaf9f449-3be5-4661-8028-02723bdda1ae-160501085819/85/Security-Testing-Zap-It-29-320.jpg)