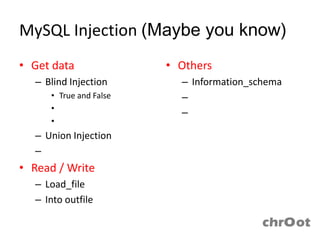
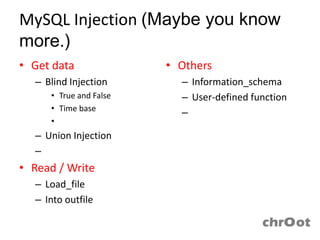
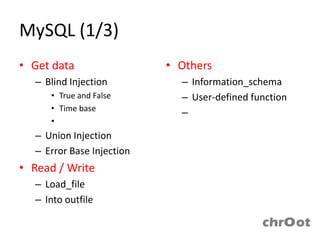
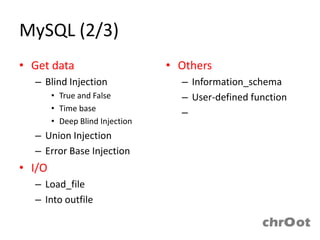
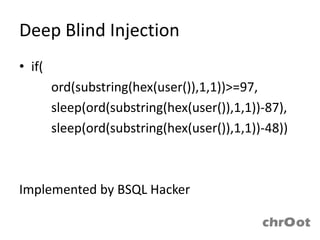
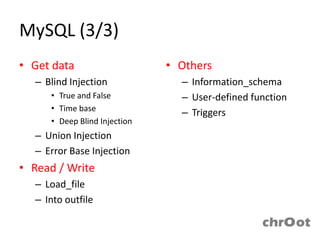
- MySQL injection techniques can be used to extract data through blind injection, union queries, and error-based injection. Time-based blind injection and deep blind injection can extract data character by character.
- Load_file and into outfile functions can be used to read and write files in MySQL. Information from information_schema, user-defined functions, and triggers may also be exploitable.
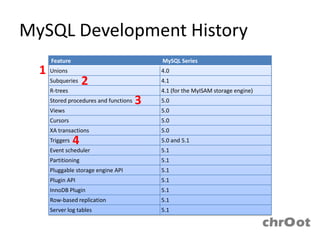
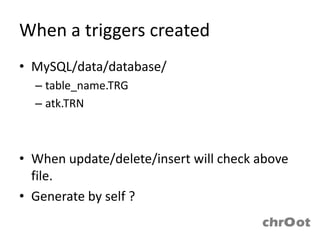
- Triggers are database objects that activate when events like insert, update or delete occur and may potentially be exploited to add new accounts or stop the MySQL server.