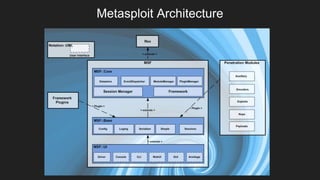
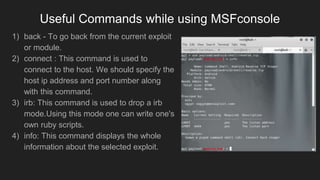
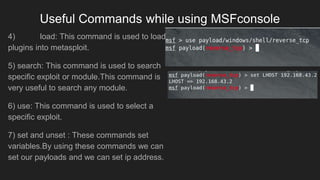
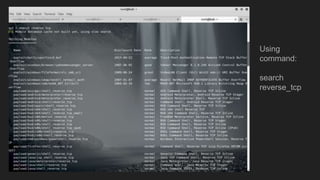
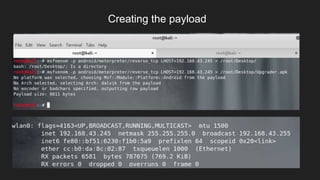
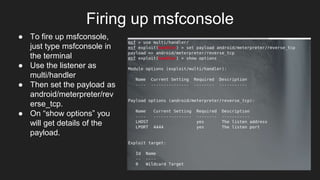
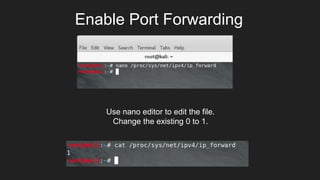
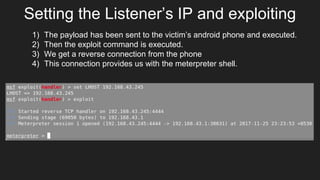
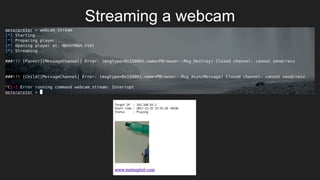
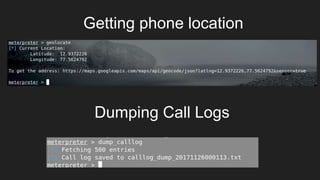
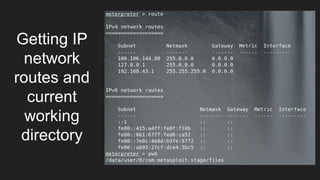
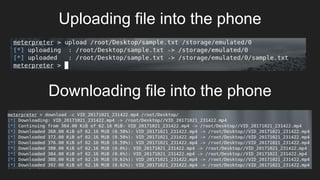
This document provides an overview of Metasploit and how it can be used to perform penetration testing and vulnerability assessments. It defines key Metasploit terminology like exploits, payloads, shellcode, and modules. It describes Metasploit's architecture including its libraries, core, and base components. It also outlines useful MSFconsole commands and provides a step-by-step example of exploiting an Android device with Metasploit that involves generating a payload, setting up a listener, enabling port forwarding, executing the exploit, and using the meterpreter shell for post-exploitation tasks.