The document provides an overview of Linux network tools, including foundational theories like the OSI model and device types (modems, routers, switches). It covers configuration settings, essential tools for network analysis (e.g., netstat, nmap, tcpdump), and methods for remote communication (e.g., ssh, ftp). Additionally, it discusses IP and MAC addressing, and various command-line tools to manage and monitor network connections.
![21
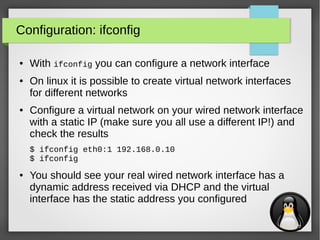
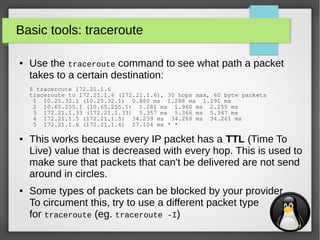
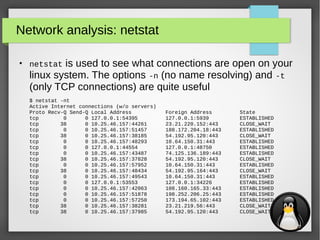
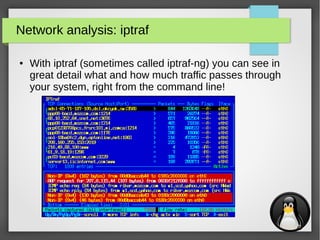
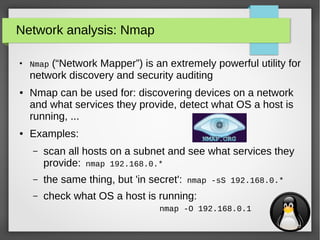
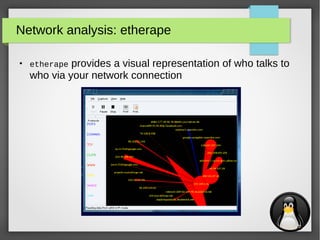
Network analysis: iperf
●
iperf is used to measure the effective network bandwidth for
TCP or UDP traffic between two hosts
● Example:
– Host 1 (192.168.0.1):
$ iperf -s
------------------------------------------------------------
Server listening on TCP port 5001
TCP window size: 85.3 KByte (default)
------------------------------------------------------------
[ 4] local 192.168.0.1 port 5001 connected with 192.168.0.10 port 47693
[ ID] Interval Transfer Bandwidth
[ 4] 0.0-10.1 sec 113 MBytes 93.8 Mbits/sec
– Host 2 (192.168.0.10):
$ iperf -c 192.168.0.1
------------------------------------------------------------
Client connecting to 192.168.0.1, TCP port 5001
TCP window size: 85.0 KByte (default)
------------------------------------------------------------
[ 3] local 192.168.0.10 port 47693 connected with 192.168.0.1 port 5001
[ ID] Interval Transfer Bandwidth
[ 3] 0.0-10.0 sec 113 MBytes 94.7 Mbits/sec](https://image.slidesharecdn.com/networktools-150604094513-lva1-app6891/85/Linux-network-tools-Maarten-Blomme-21-320.jpg)

![30
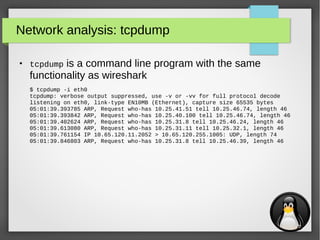
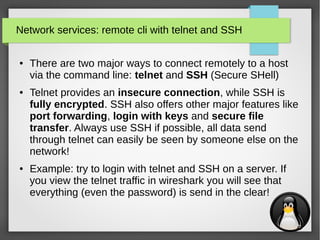
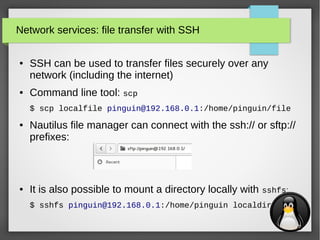
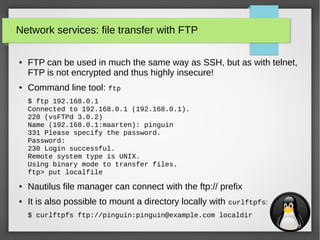
Network services: file transfer with wget & curl
●
wget and curl are both cli utilities that are used to get files
via several protocols (they also support authentication):
– wget: FTP, HTTP & HTTPS
– curl: DICT, FILE, FTP, FTPS, GOPHER, HTTP, HTTPS, IMAP, IMAPS, LDAP, LDAPS,
POP3, POP3S, RTMP, RTSP, SCP, SFTP, SMB, SMBS, SMTP, SMTPS, TELNET and
TFTP
$ wget http://192.168.0.1/index.html
--2015-06-02 17:04:43-- http://192.168.0.1/index.html
Connecting to 192.168.0.1:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 11510 (11K) [text/html]
Saving to: ‘index.html’
index.html 100%[==========================>]
11.24K --.-KB/s in 0.001s
2015-06-02 17:04:43 (16.5 MB/s) - ‘index.html’ saved [11510/11510]
$ curl http://192.168.0.1/index.html -o index.html
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 11510 100 11510 0 0 2126k 0 --:--:-- --:--:-- --:--:-- 2248k](https://image.slidesharecdn.com/networktools-150604094513-lva1-app6891/85/Linux-network-tools-Maarten-Blomme-30-320.jpg)